Change Log
View Change Log
Mar. 19, 2024
- Corrected the interface configuration on Metasploitable 2
- Prefer default route out AD lab interface for Internet access
- Added a route to Kali's subnet through the correct interface
Mar. 14, 2024
- Added a completely new module
- External Pentest Practice in Your VirtualBox AD Lab
Mar. 13, 2024
- Update several screenshots in the AD lab section to bring it up-to-date with the latest user experience
- Update the AD lab firewall rules to correct a logic flaw
- The original ruleset will block traffic to the default gateway of the lab
- Update adds a rule to the top of the ruleset that allows traffic to the default gateway, which will also correct issues with the DNS resolver
January 25, 2024
Updated the Configuring the pfSense Firewall for Our VirtualBox Lab step with new firewall rule creation screenshots and configurations
- Should remove any confusion where rules used to reference
INTERFACE netand now referenceINTERFACE subnets - Moved the steps to create firewall aliases from the Adding Another Interface to pfSense in VirtualBox to the aforementioned step above, as creating the aliases earlier will help readers create better rules
- Also, updated firewall rules for the
AD_LABsubnet, so that they reference the aforementioned aliases, they are a bit more restrictive, and they scale better for labs that add more subnets
December 30, 2023
- Massive upgrade to the Active Directory Lab Step!
- Added a completely new step to help you set up a vulnerable AD lab using this project on GitHub, and also demonstrate some example attacks that are possible
- Added additional steps to help you understand how to roll back your AD lab to clean slate
September 1, 2023
Updated the Building a pfSense VM for Our VirtualBox Cyber Range step, Importing Kali Using the Official VirtualBox Image step, and Adding Vulnhub VMs to Our VirtualBox Cyber Range step
- Lots of screenshot updates!
- Brings the guide up to the VirtualBox 7.x experience, so less guesswork for readers when building their VMs
June 23, 2023
Updated the Adding an Active Directory Forest to Our VirtualBox Lab step
What We'll Build
- Virtualized pfSense firewall as the gateway
- Multiple subnets for different purposes
- LAN
- Isolated
- Active Directory
Usage Scenarios
Desktop
You have a desktop – either your daily-use computer or backup computer – you do not want to reimage it, but would like to run some labs on your computer.
Laptop
Your daily-use computer. You want to run some labs on it and would like a mobile security lab.
Recommended System Specifications
- Multithreaded CPU with Virtualization Support
- At least 16GB RAM – 32GB would be better
- Plenty of free disk space, preferably more than one internal disk
Enabling Virtualization in the BIOS
- Turn on the laptop
- Press the
ESCkey multiple times until you get to the system setup menu.
Warning: you might need to press a different key on your system to get to the BIOS menu. From my HP laptop, ESC is the key to get to the BIOS.
- Choose BIOS Setup
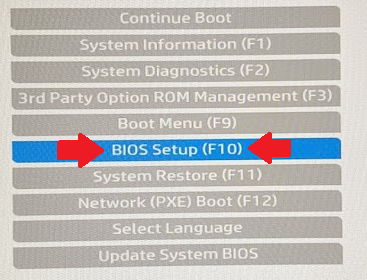
- Go to Advanced > System Options
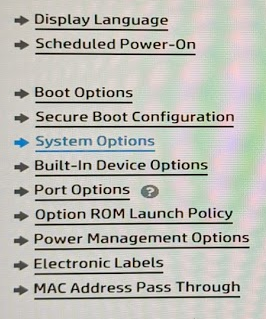
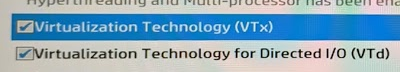
- Enable VTx and VTd (For AMD processors, there is a different name)
- Save changes and exit the BIOS setup
Install VirtualBox
To download the VirtualBox installer for your host OS, navigate to their downloads page here:

You'll see a list of downloads based on host operating system. At the time of writing this guide, the latest version was 6.1.32.
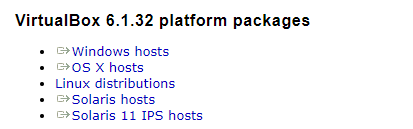
- If downloading for Windows, click
Windows hosts - If downloading for Mac OS, click
OS X hosts - If downloading for Linux, click
Linux distributionsand follow the instructions. You can downloading using an.rpmor.debpackage, or you can install using your package manager such asyumorapt.
Install the VirtualBox Extension Pack
Once you've installed VirtualBox, I'd highly recommend you add the extension pack for better VM support.
You can download the extension pack file. Once you open the file, VirtualBox should be the default file handler and install the extension pack. You must reinstall the extension pack any time you update VirtualBox!
A Note on VirtualBox Guest Additions
What are the VirtualBox Guest Additions? As you continue to experiment with VirtualBox, you may hear this name come up. Put simply, the Guest Additions are drivers (or software) you can install inside the VM, to enable it to run more smoothly with VirtualBox.
For example, sometimes you may have VM that has a poor screen resolution, the screen doesn't resize, or some other strange issues. You may need to install the VirtualBox Guest Additions drivers to help the VM run more smoothly.
Next Steps
Building a pfSense VM for Our Cyber Range

Importing Kali from Offensive Security Images

Configuring the pfSense Firewall

Adding Vulnhub VMs to the Lab

Building the Active Directory Lab

Hack Your Active Directory Lab

Set up a Pivoting Lab
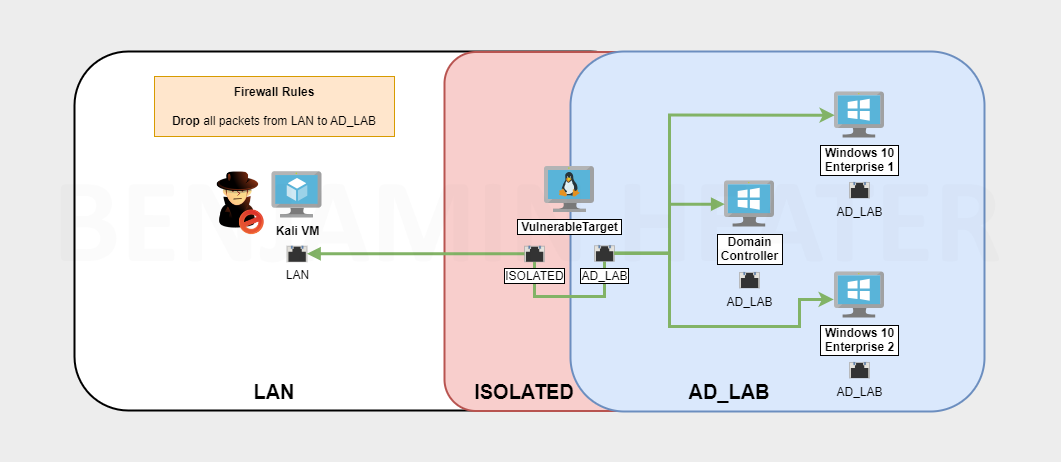
Troubleshooting Your Lab

Creating a Windows 7 Buffer Overflow Practice VM

Adding Another Interface to pfSense

Appendices
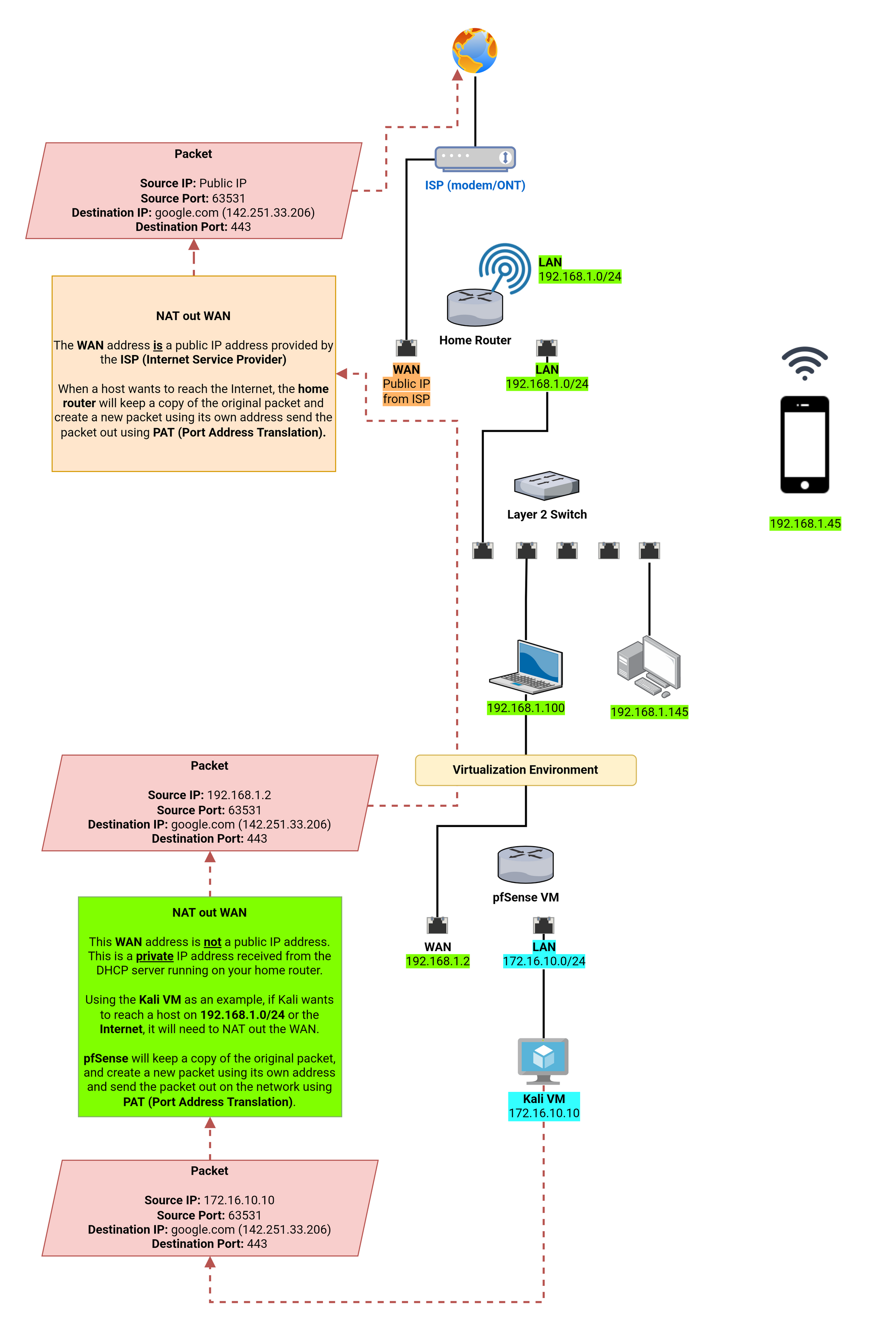
Appendix A: Double NAT Diagram
Learn more about NAT here: https://www.youtube.com/watch?v=wg8Hosr20yw
Other Projects

Honorable Mentions
- Check out @Dewalt’s PimpMyKali script to make your Kali VMs so much better
- gimmesystem in the HackTheBox Discord server for QA testing this guide




