This module is a part of a larger series of building a security lab in VirtualBox. Click here to be taken back to the series landing page.

Whenever you are building a lab – whether in the cloud or on premise – you should always plan your network first. You should factor in future growth as well. It's much more difficult to change network design later than planning for it now.
Download pfSense
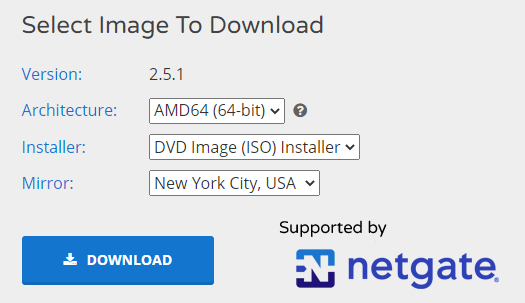
Go to: https://www.pfsense.org/download/ and choose the image with the following specifications:
- AMD64
- ISO installer
- Choose the mirror closest to you
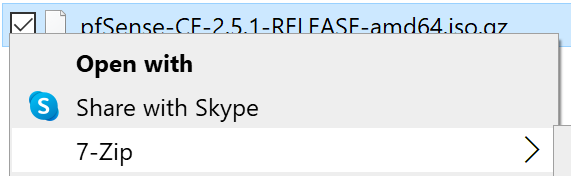
Now, go to the folder where you downloaded pfSense. We need to extract the .iso file form the archive.

Install 7zip or some other archive extraction utility to decompress the .gz archive.
You should now have a pfSense-CE-#.#.#-RELEASE-amd64.iso file in your folder.
Create the VM
Click the New button

The Name and Machine Folder are specific to your computer. Ensure you choose the correct Type and Version as shown here.
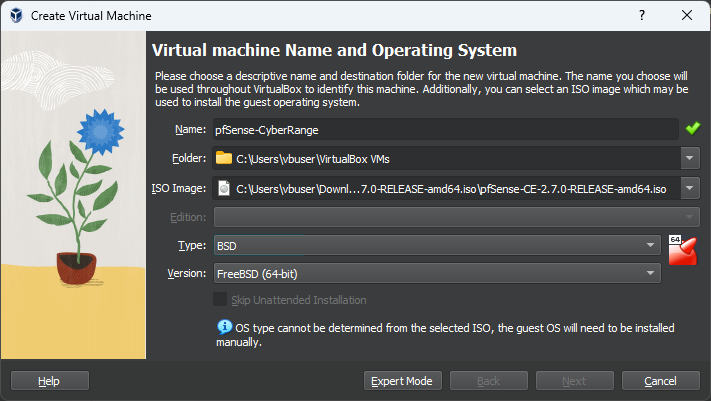
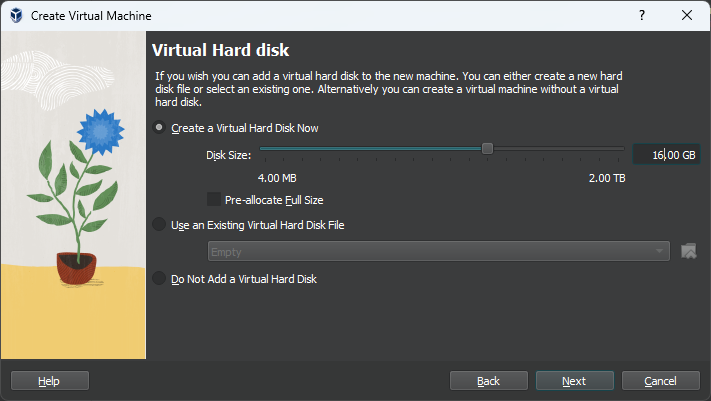
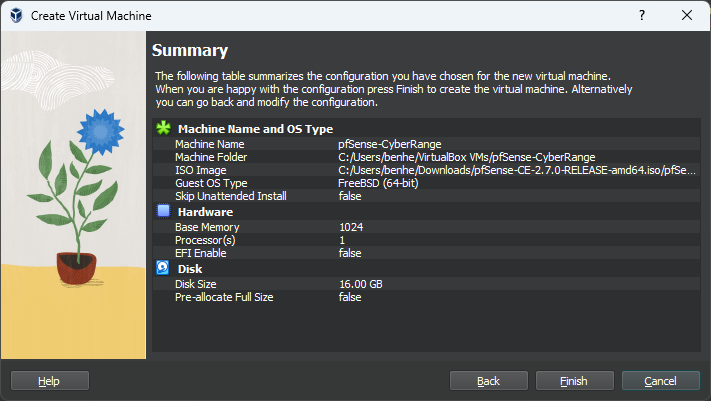
Customize the VM
Right-click the VM and choose Settings
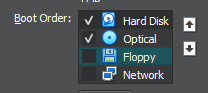
Move Hard Disk above Optical and disable Floppy

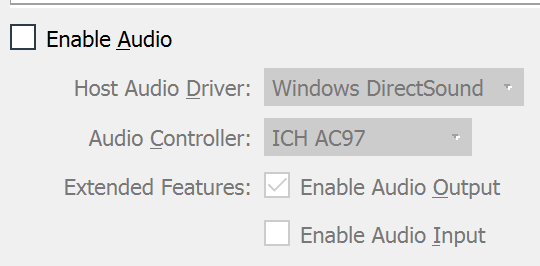
Disable audio
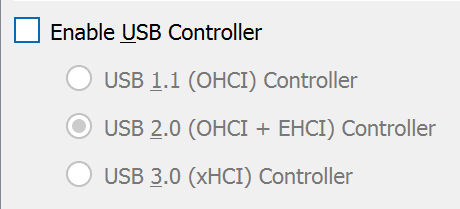
Disable USB
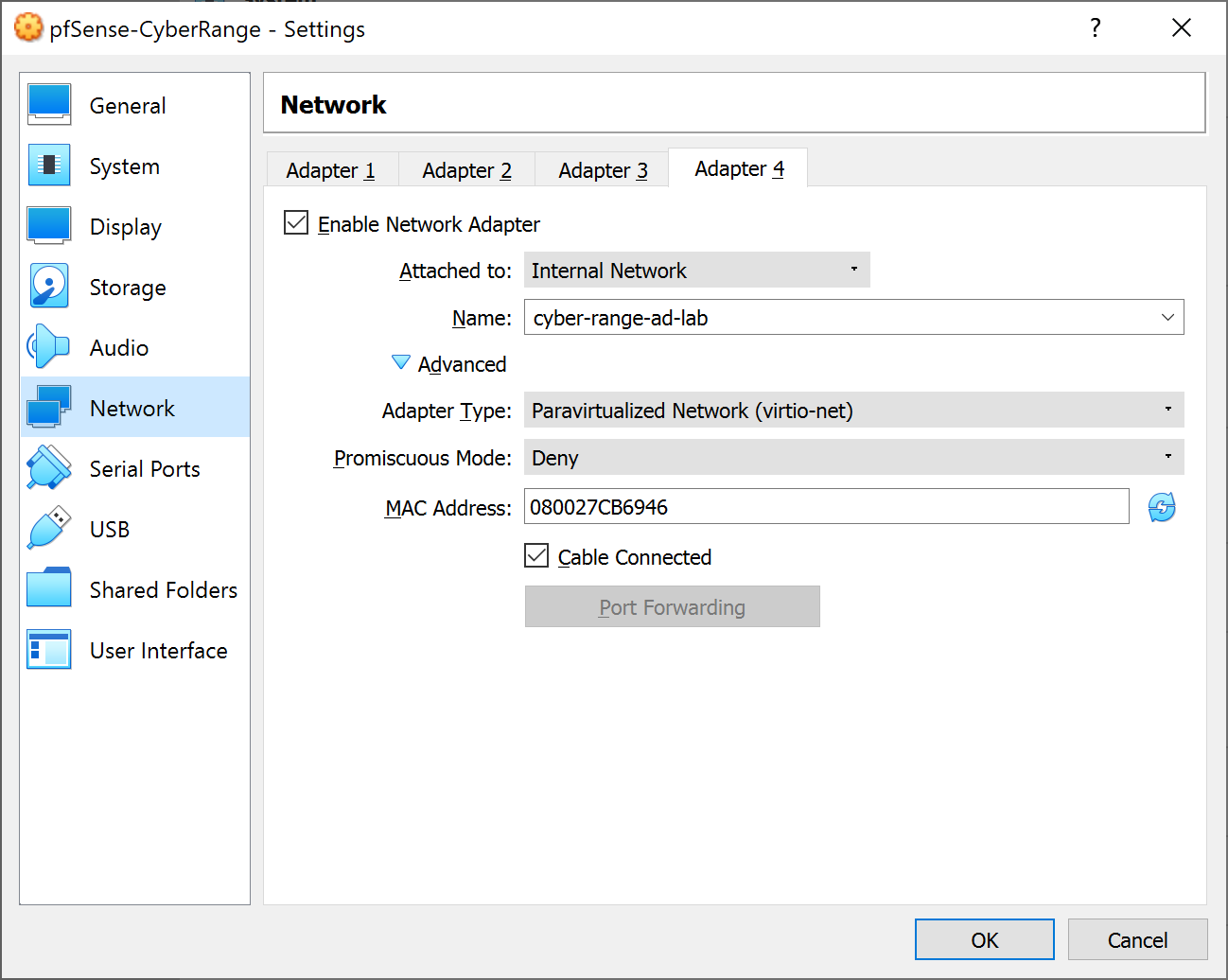
Configure the Network Interfaces
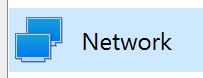
Adapter 1: WAN
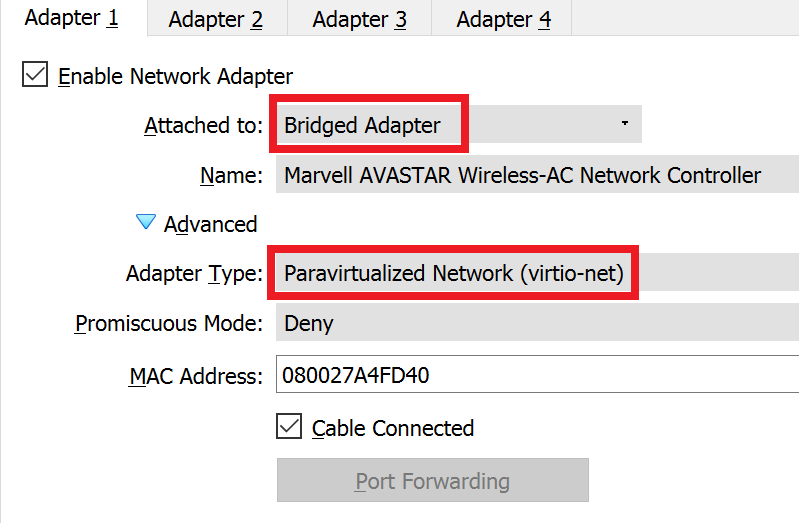
Adapter 2: LAN
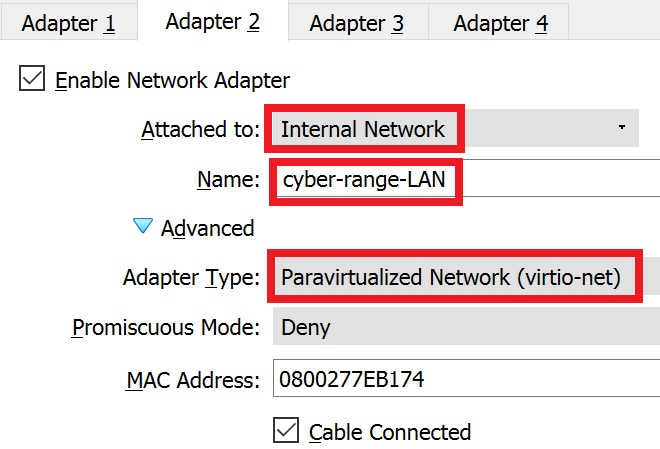
Adapter 3: ISOLATED
Adapter 4: AD_LAB
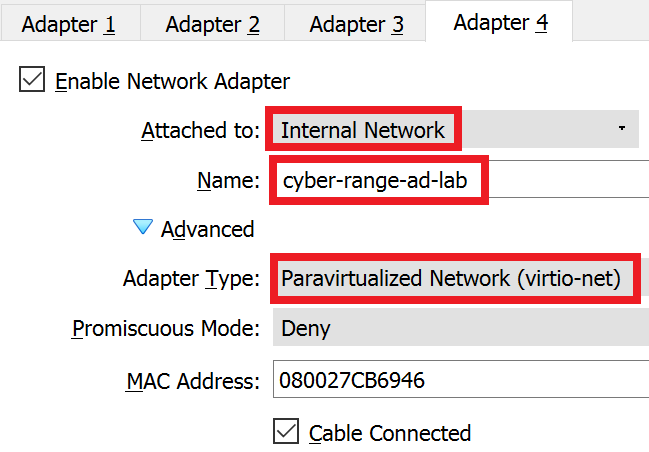
All done. Click OK.
Installing pfSense

If it asks for the startup disk, just choose the .iso disk we downloaded earlier. Press Enter.
Choose Install pfSense
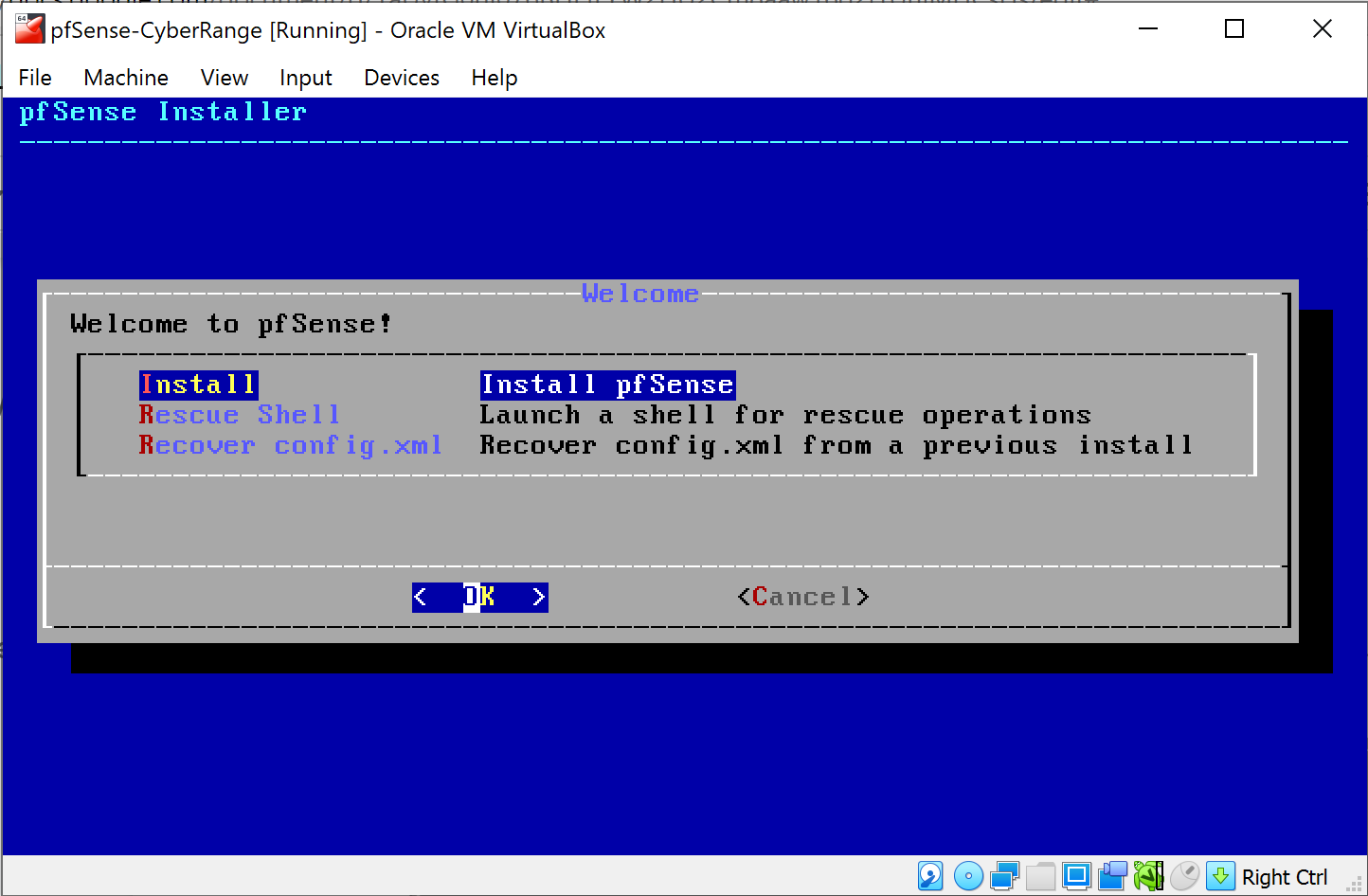
Choose Auto (ZFS)
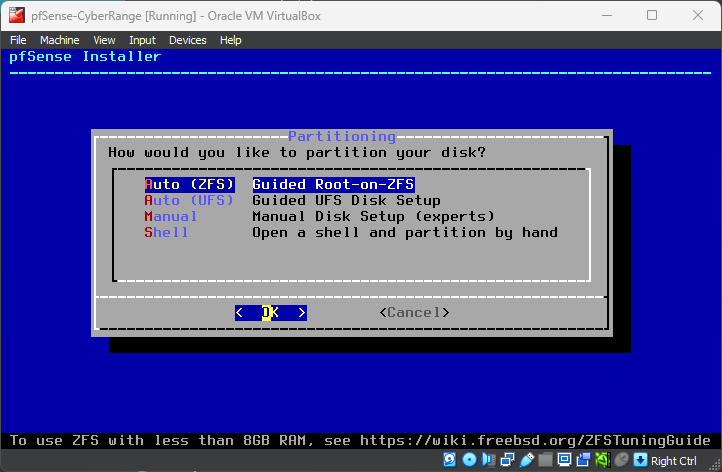
Proceed with Installation using the defaults
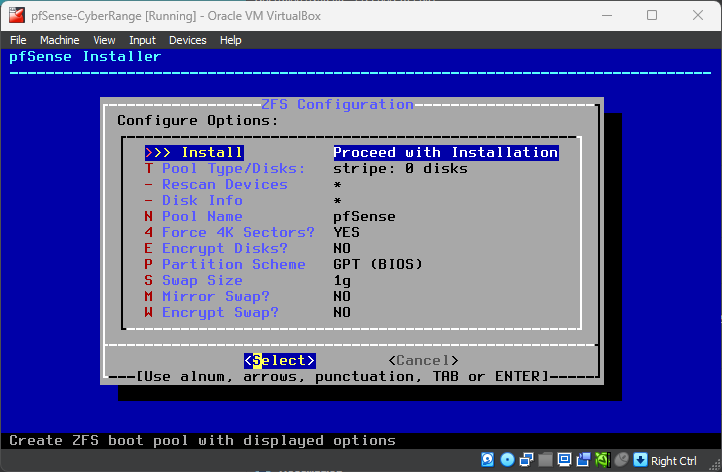
Stripe – No Redundancy
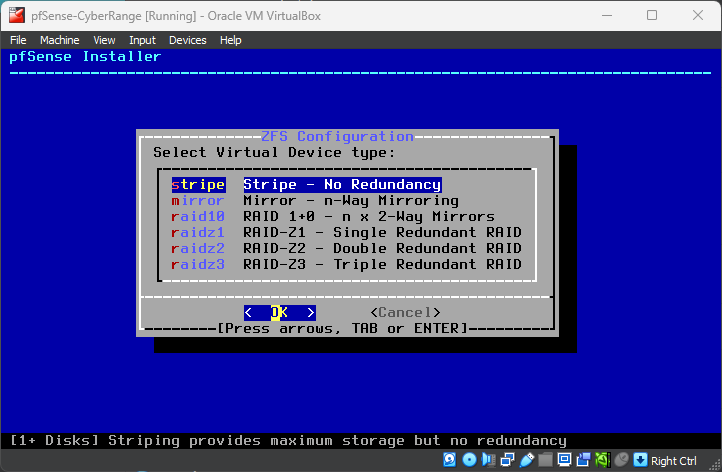
Use your Space Bar such that an * (asterisk) denotes the selected disk.
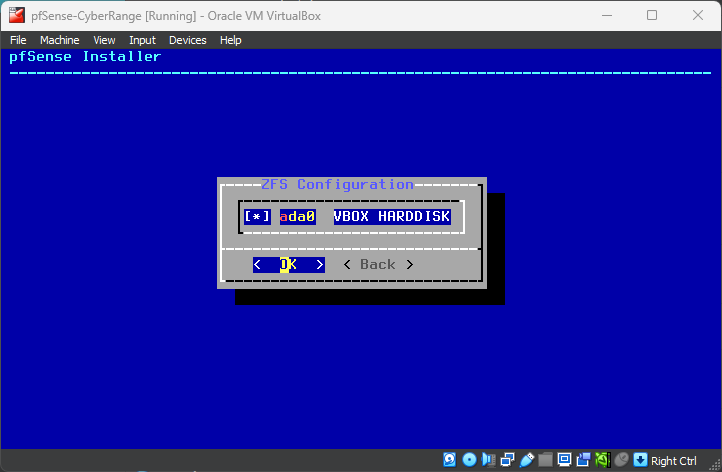
Use your arrow keys to select YES and proceed.
Wait for installation process to complete...
Choose Reboot
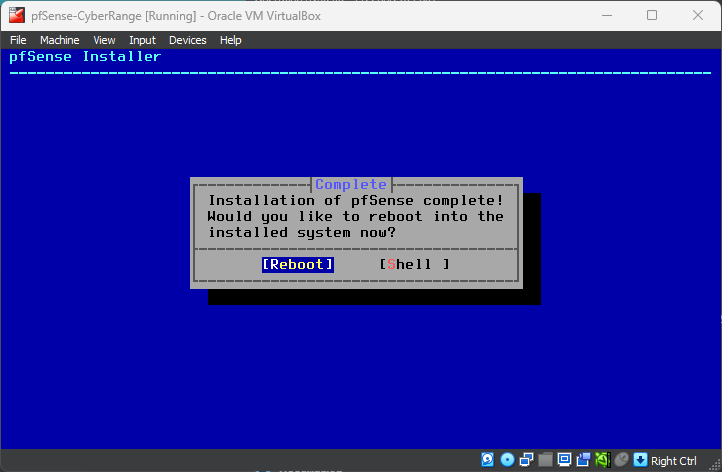
Configuring pfSense

Wait for the VM to finish booting. When asked Should VLANs be set up now [y|n]?, choose n.
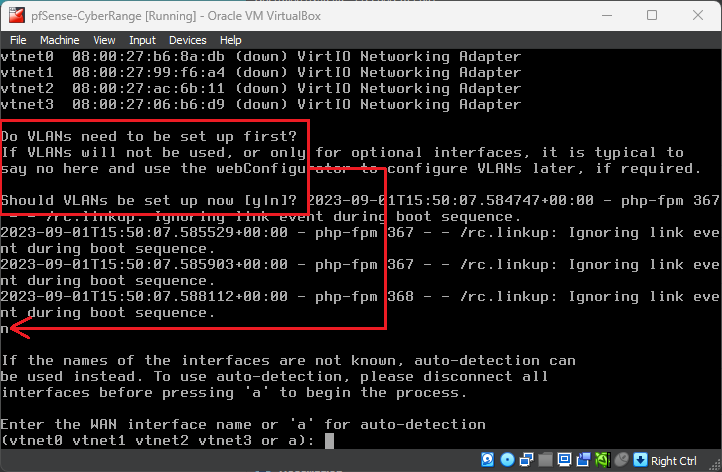
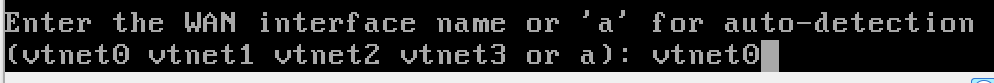
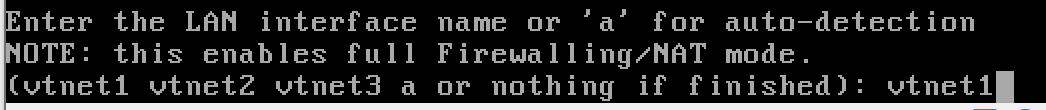
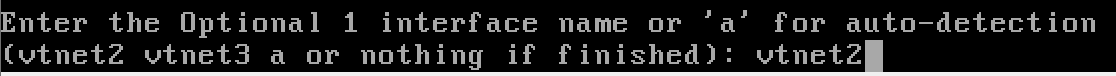
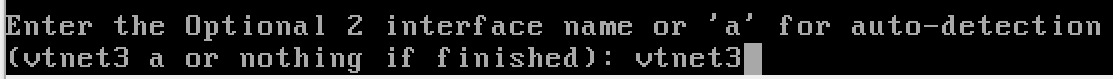
Configuring the Interfaces
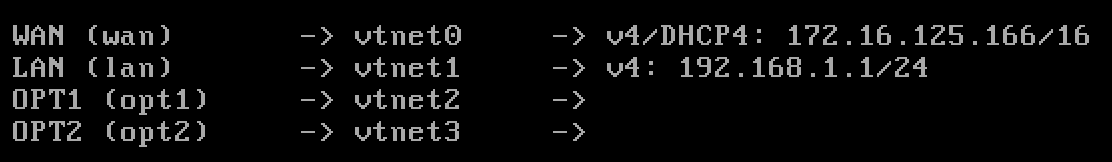
- The WAN interface pulled an IP address from my home network.
- The Default LAN IP address space is 192.168.1.1/24
- OPT1 (optional interface 1) – Isolated – is not yet configured.
- OPT2 (optional interface 2) – AD_LAB – is not yet configured.
Configure the LAN
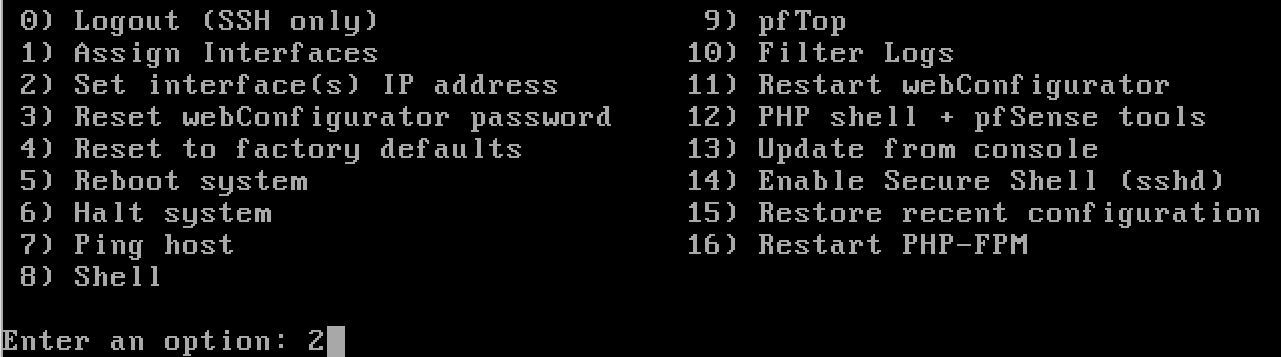
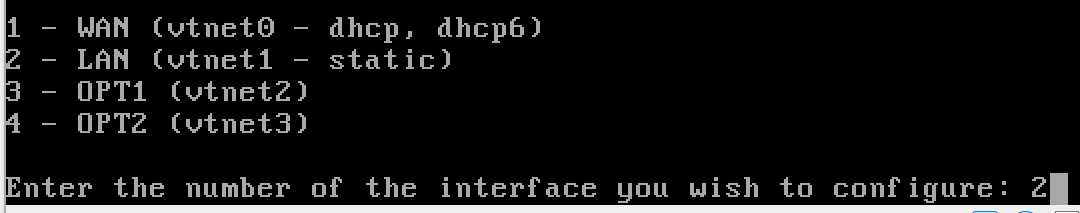
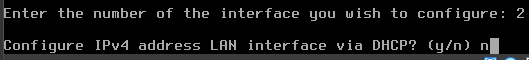
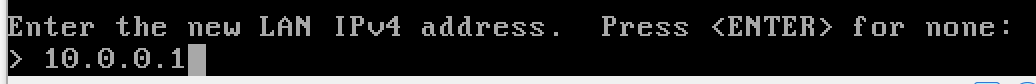
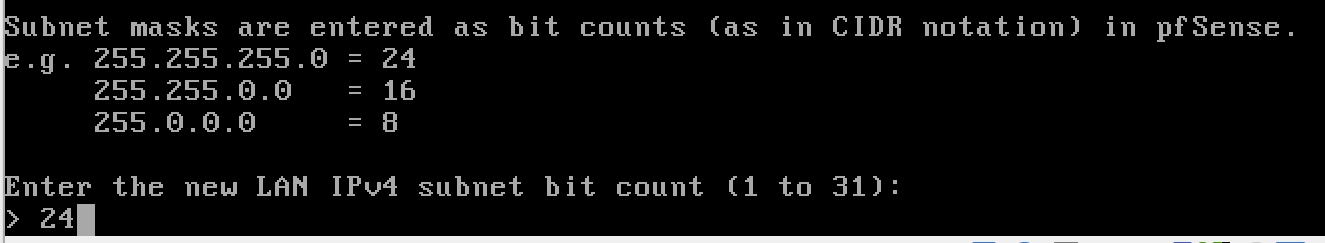
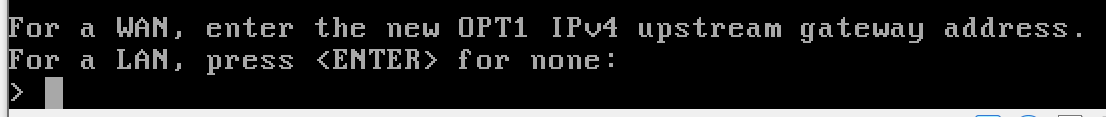
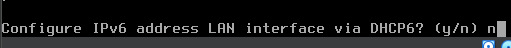
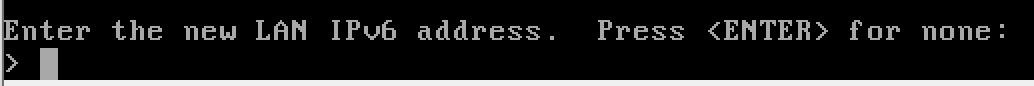

y to enable the DHCP server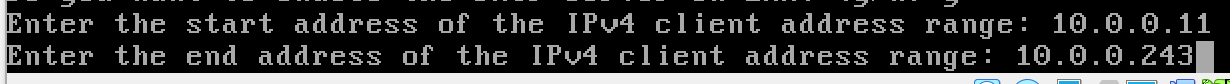
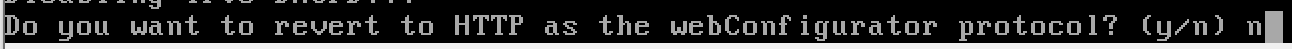
n, we want to keep using TLS on the web portal.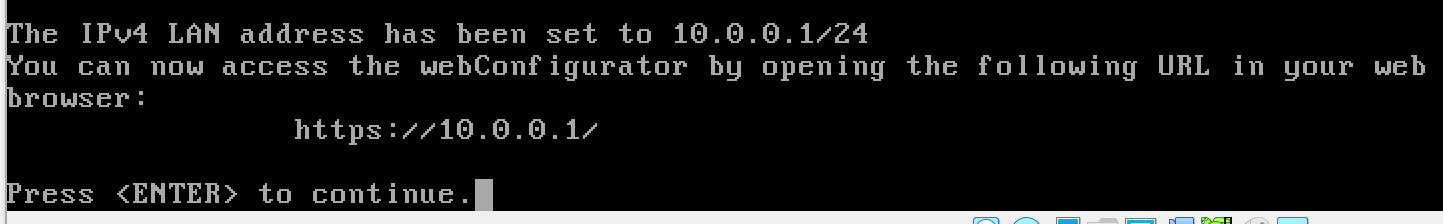
Configure the Isolated LAN
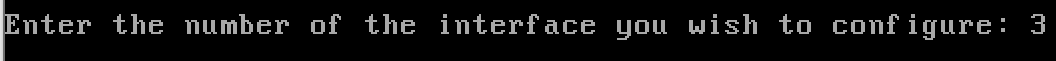
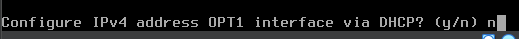
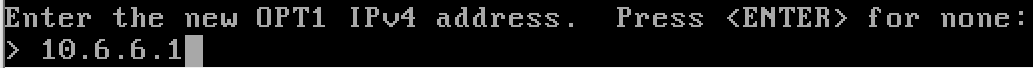
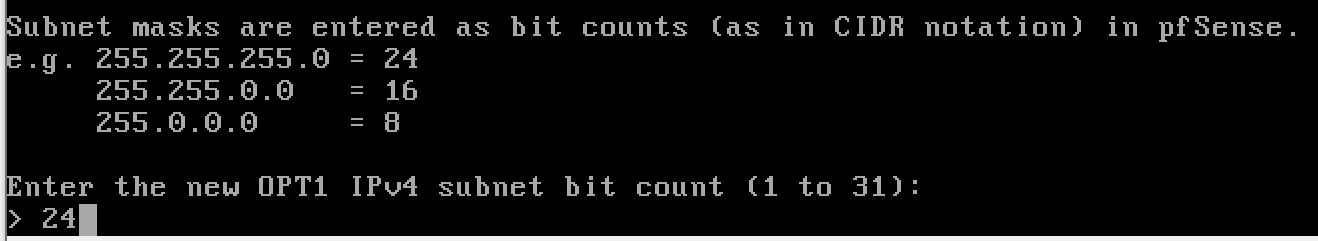
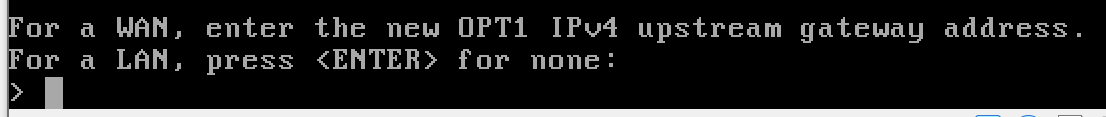
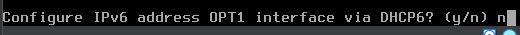
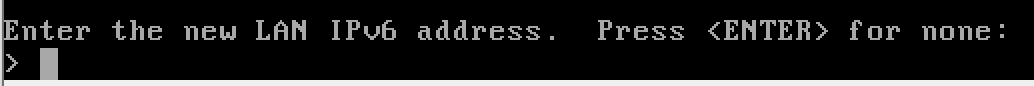
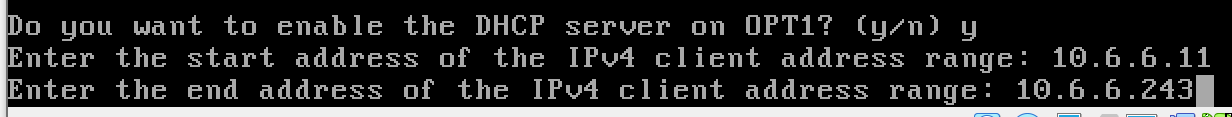
y to enable the DHCP server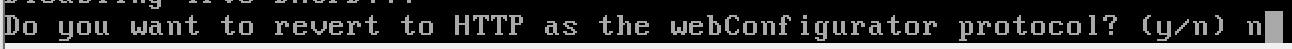
n, we want to keep using TLS on the web portal.All done with the ISOLATED LAN
Configure the AD Lab LAN
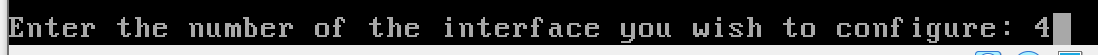
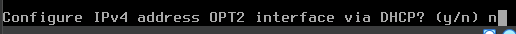
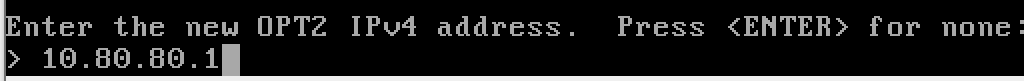
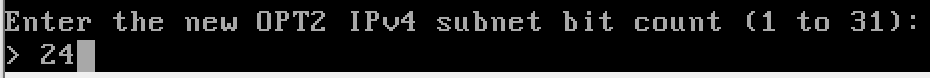
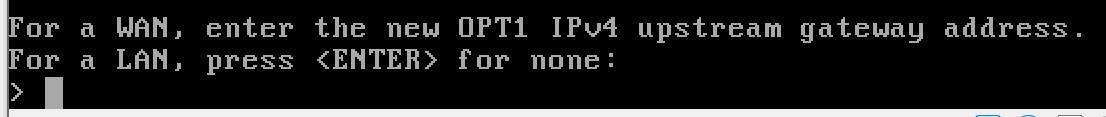
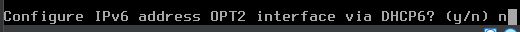
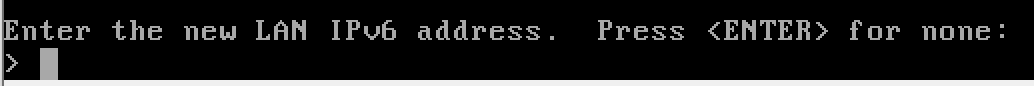
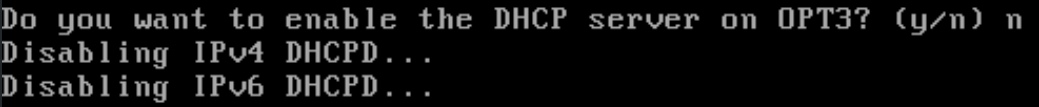
n to disable the DHCP server, as the domain controller will be acting as the DHCP server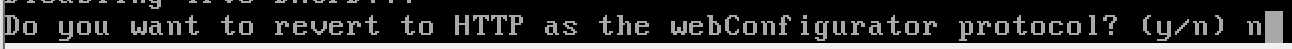
n, we want to keep using TLS on the web portal.All done with the AD_LAB LAN
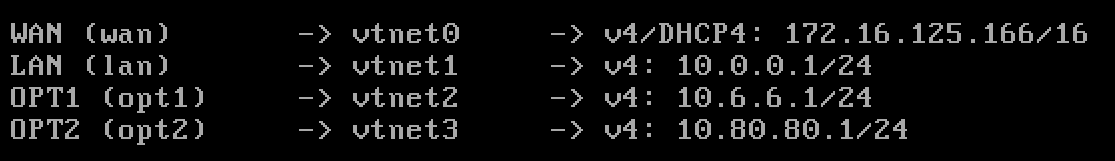
Final Check
You should now see something like this
A Note on Configuring the Firewall
In this guide, we will not be making the pfSense web console available from the WAN.
This is because you may be using a laptop and if you connect to public wireless, then your pfSense web console would be open to the others on that network.
We will be using our Kali VM to configure the pfSense firewall rules in a bit.
Next Step: Importing Kali from Offensive Security Images




