This module is a part of a larger series of building a security lab in VirtualBox. Click here to be taken back to the series landing page.

Log into the Web Portal
In Kali, open your web browser and navigate to: https://10.0.0.1

The default credentials are:
- Username:
admin - Password:
pfsense
Click Next
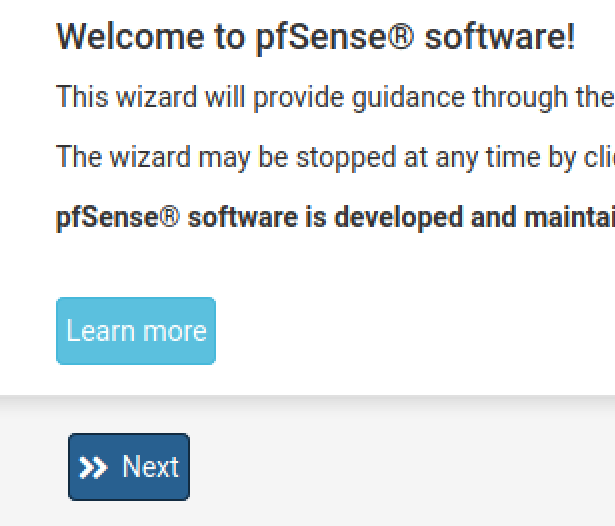
Click Next (again). Fill out the Hostname and Domain. Uncheck Override DNS. Click Next.
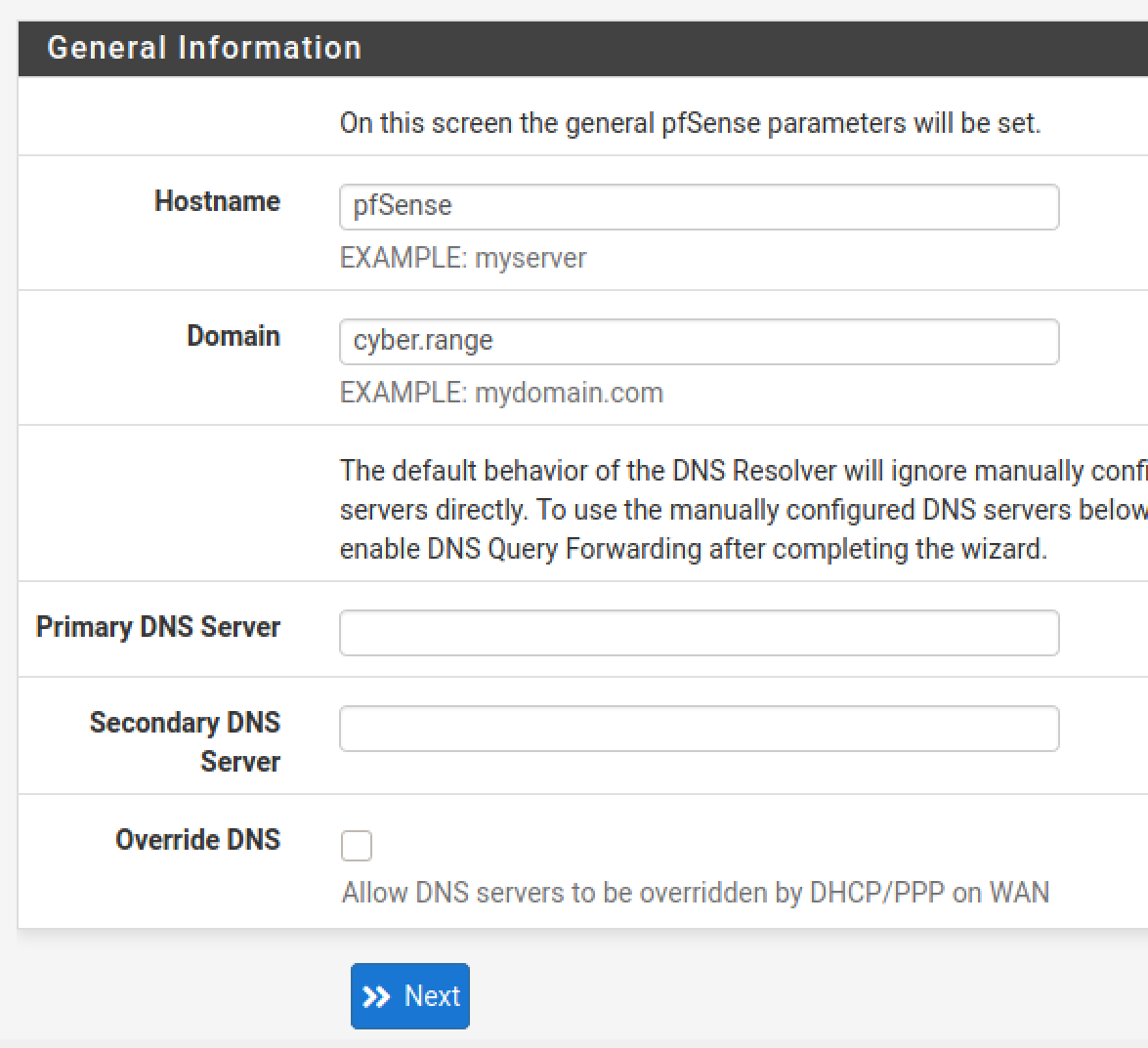
Double check your timezone and click Next.
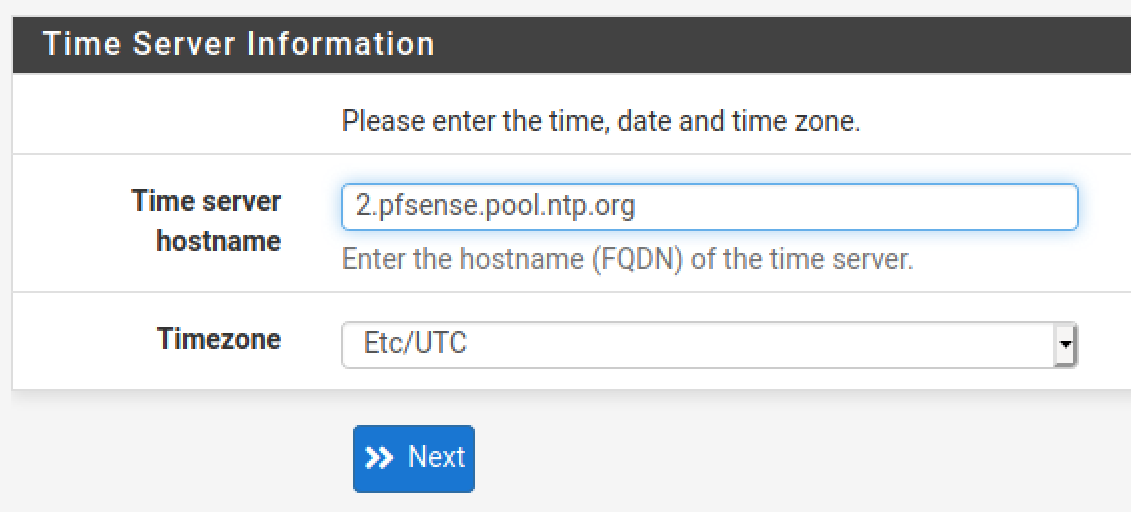
Scroll down and uncheck this box. We’re double-NAT, which means that the WAN network is also a private network, so we want to allow this. Click Next.
Leave this alone. Click Next.
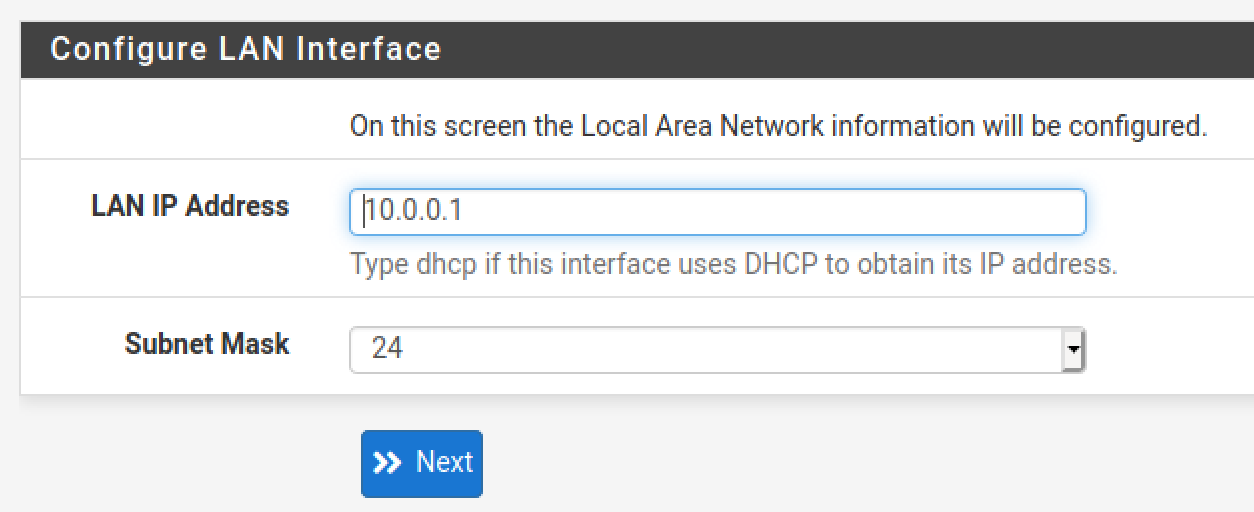
Change the admin password. Save it in a password vault. Click next.
Click Reload and wait for the web configurator to refresh. Click Finish.
Configure the Interfaces
Isolated Interface
Choose OPT1
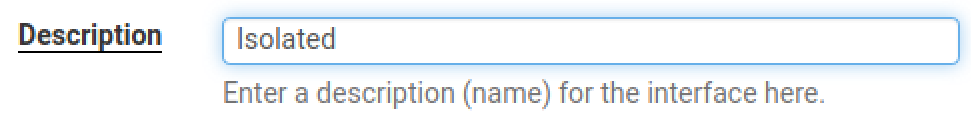
Set the Description to Isolated. Scroll down and click Save and Apply Changes.
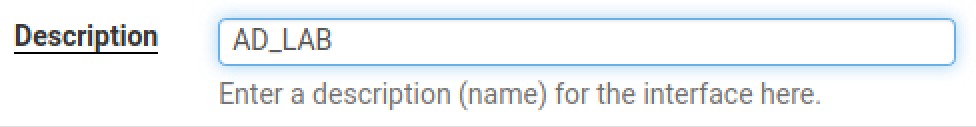
AD_LAB Interface
Choose OPT2
Set the Description to AD_LAB. Scroll down and click Save and Apply Changes.
Optimize the DNS Resolver Service
Go to Services > DNS Resolver
Check these boxes, click save and apply changes.
Netgate is pushing people to the Kea DHCP daemon, as they're deprecating the ISC DHCP daemon. If you opt to move to the Kea DHCP daemon, these options will not be available.
You will need to switch back to ISC DHCP, make your desired selections, then switch back to Kea DHCP.
https://www.reddit.com/r/PFSENSE/comments/17z1u6f/dhcp_registration_on_dns_resolver/

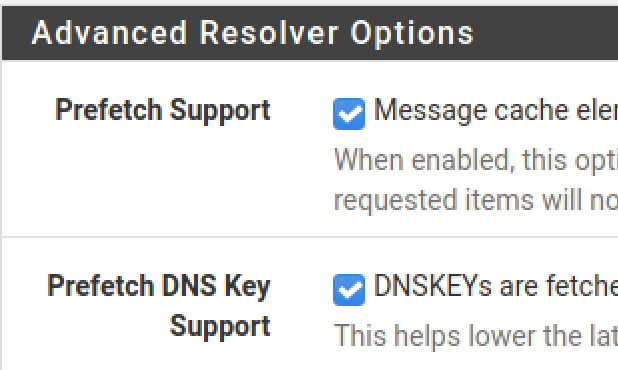
Still under DNS Resolver, go to Advanced Settings. Check both of these boxes. Click save and apply changes.
Give Kali a Static DHCP Lease
Go to Status > DHCP Leases
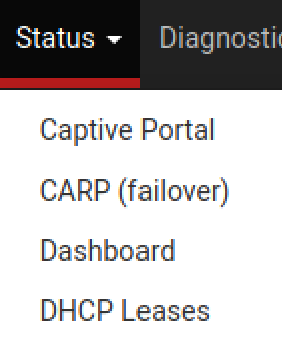
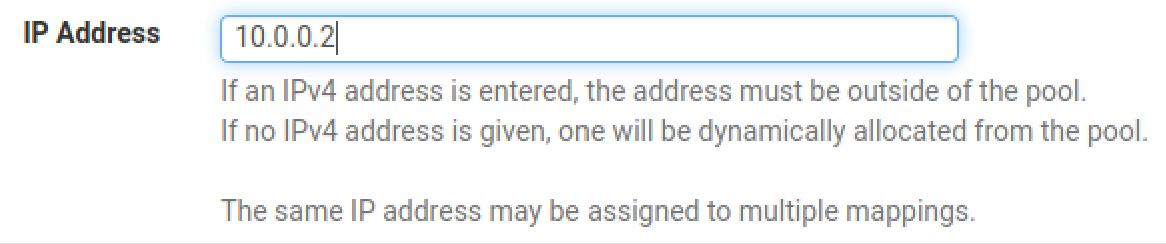
Click Save and Apply Changes.
Configure the Firewall Rules
Create an Alias for RFC1918
This alias will be used in some future firewall rules to reference all private IPv4 address spaces.
Go to Firewall > Aliases
Click Add
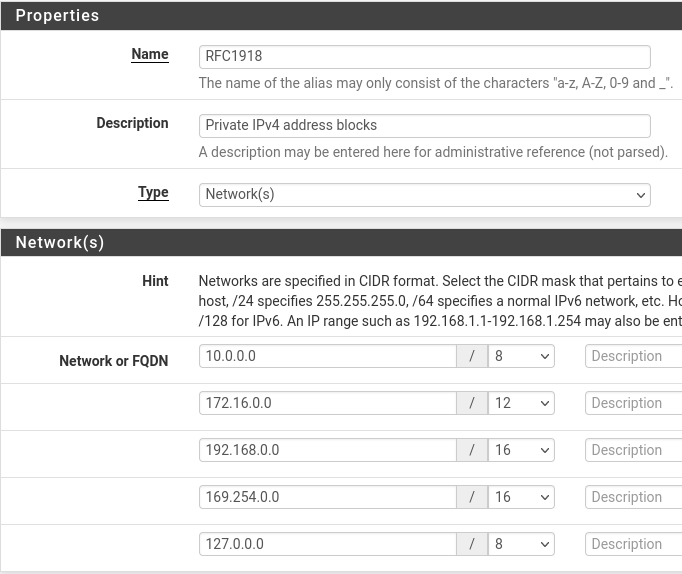
Click Save
Create an Alias for Kali
Click Add
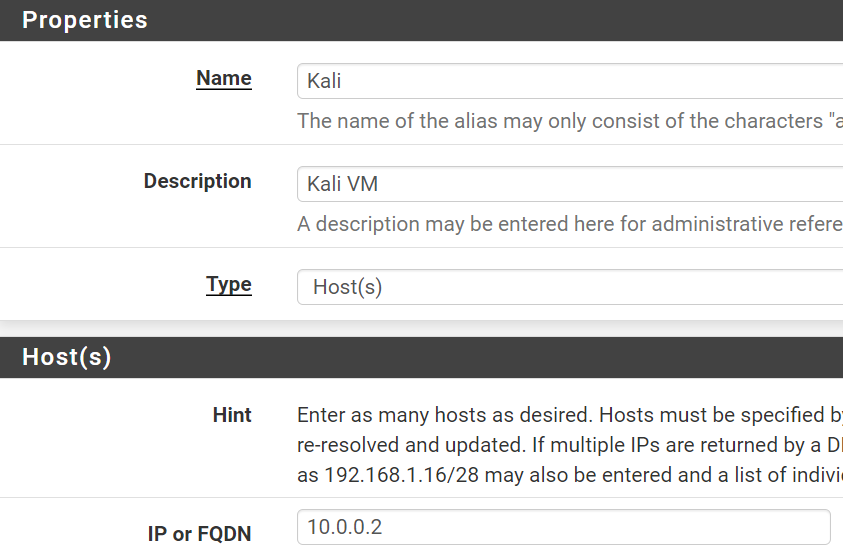
Click Save and Apply Changes
LAN
Click on Firewall > Rules
Click on LAN.
Add a rule
- Action: Block
- Interface: LAN
- Address Family: IPv4 + IPv6
- Protocol: Any
- Source: Any
- Destination: WAN subnets
- Description: Block access to any on same network as host OS
- Click Save
LAN Desired End-State
Block bogon networks rule, it's not entirely necessary on LAN interfaces. But if you wish to enable it, go to Interfaces > LAN, then scroll to the bottom and check the box for Block bogon networks. Then, save and apply your changes and it should automatically be applied to the rules table.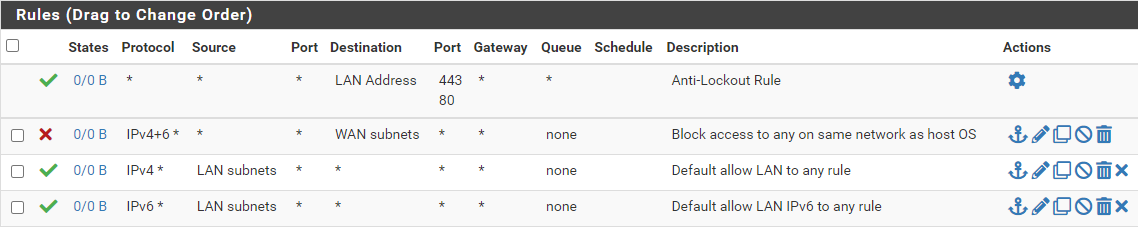
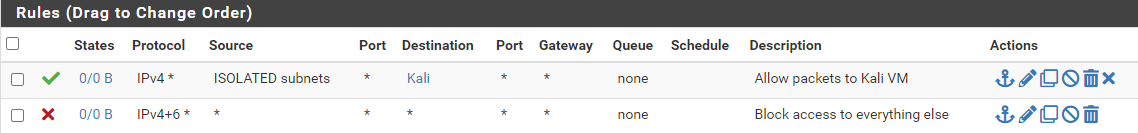
ISOLATED
Click on ISOLATED
Add a rule
- Action: Pass
- Interface: Isolated
- Address Family: IPv4
- Protocol: Any
- Source: ISOLATED subnets
- Destination: Address or alias =
Kali - Description: Allow packets to Kali VM
- Click Save and Apply Changes
Final Isolated rule
- Action: Block
- Interface: Isolated
- Address Family: IPv4 + IPv6
- Protocol: Any
- Source: Any
- Destination: Any
- Description: Block access to everything
- Click Save
ISOLATED Desired End-State
AD_LAB
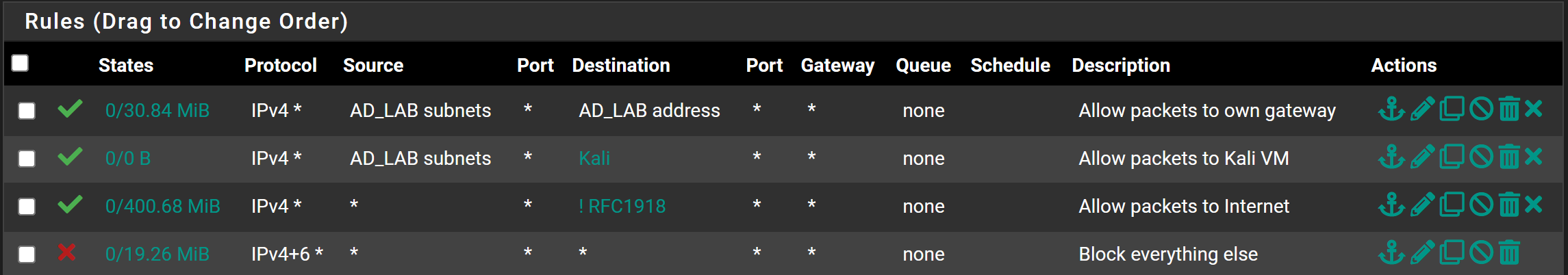
Click on AD_LAB

Add a rule
- Action: Pass
- Interface: AD_LAB
- Address Family: IPv4
- Protocol: Any
- Source: AD_LAB subnets
- Destination: Address or Alias =
RFC1918(✅invert match) - Description: Allow packets to any non-private address
- Click Save
10.0.0.2.Moving forward, if there are additional private IPv4 addresses you want your
AD_LAB hosts to be able to talk to, you'll need to place the firewall rules above this one, as rules are evaluated from top to bottom.Add another rule

- Action: Pass
- Interface: AD_LAB
- Address Family: IPv4
- Protocol: Any
- Source: AD_LAB subnets
- Destination: Address or Alias =
Kali - Description: Allow packets to Kali VM
- Click Save
Add another rule

- Action: Pass
- Interface: AD_LAB
- Address Family: IPv4
- Protocol: Any
- Source: AD_LAB subnets
- Destination: AD_LAB address
- Description: Allow packets to default gateway
- Click Save
Final AD lab rule
- Action: Block
- Interface: AD_LAB
- Address Family: IPv4 + IPv6
- Protocol: Any
- Source: Any
- Destination: Any
- Description: Block everything else
- Click Save and Apply Changes
AD_LAB Desired End-State
Kali rule is above the RFC1918 rule, as having the rule below it would prevent the traffic from reaching Kali.If you put Kali on the same subnet as the rest of the AD hosts, the firewall rules don't really matter, since the packets are switched locally on the same network.
Make Some System Tweaks to pfSense
Go to System > Advanced
Go to Networking
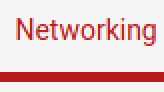
Scroll down and check this box
Click Save and Apply Changes. Click Reboot and reboot now.
Grab Kali's New DHCP Reservation
Log into your Kali VM and open a terminal. Run the command as pictured below.
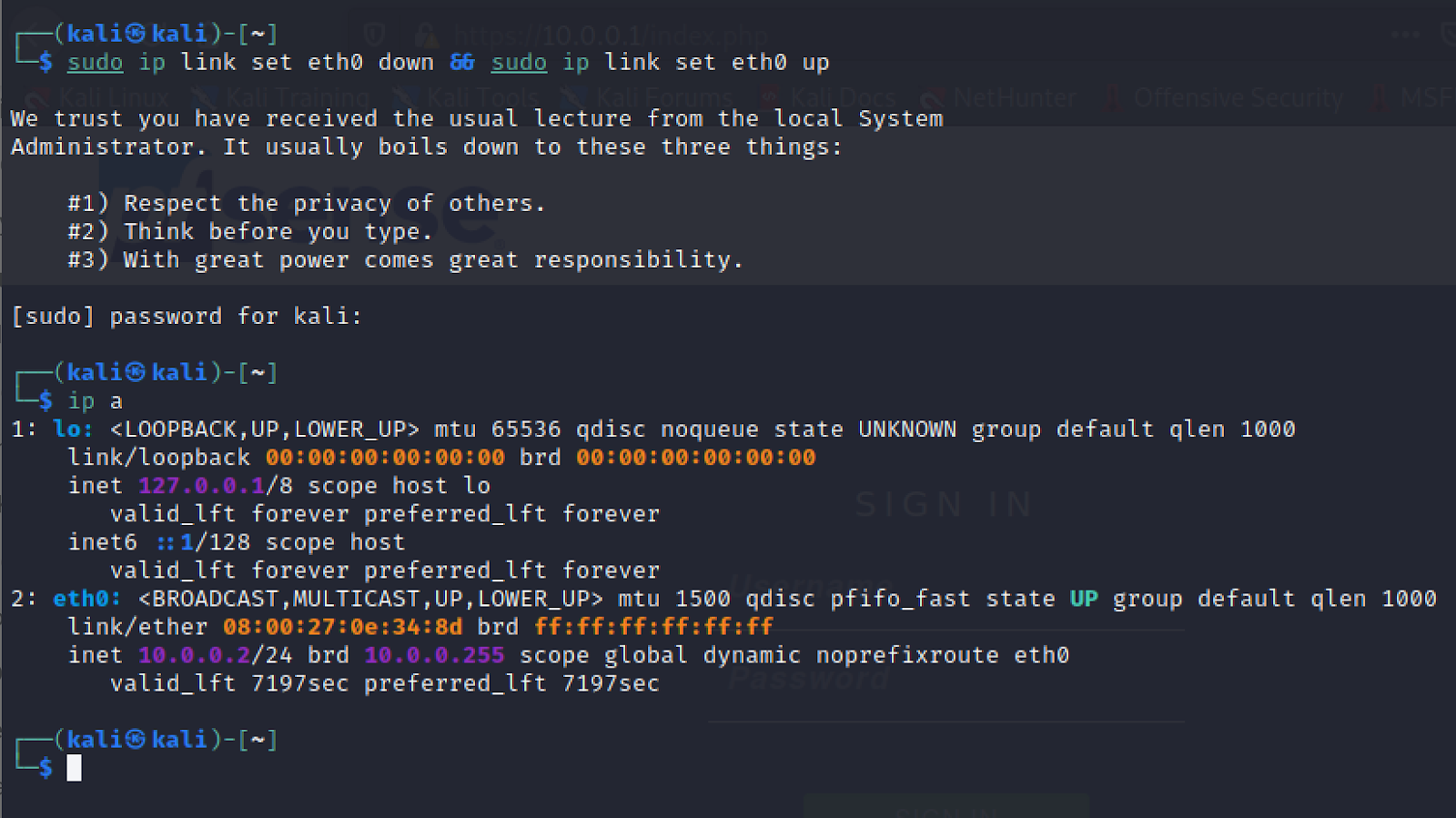
Your IP address should now be 10.0.0.2 as configured.
Next Step: Adding Vulnhub VMs to the Lab



