What is the OSCP?
- https://www.offensive-security.com/pwk-oscp/
- Earned upon completion of:
- Self-paced PEN-200 course
- 23.75 hours simulated penetration test
- You will learn:
- How to think like an attacker
- Tools and methods used by attackers
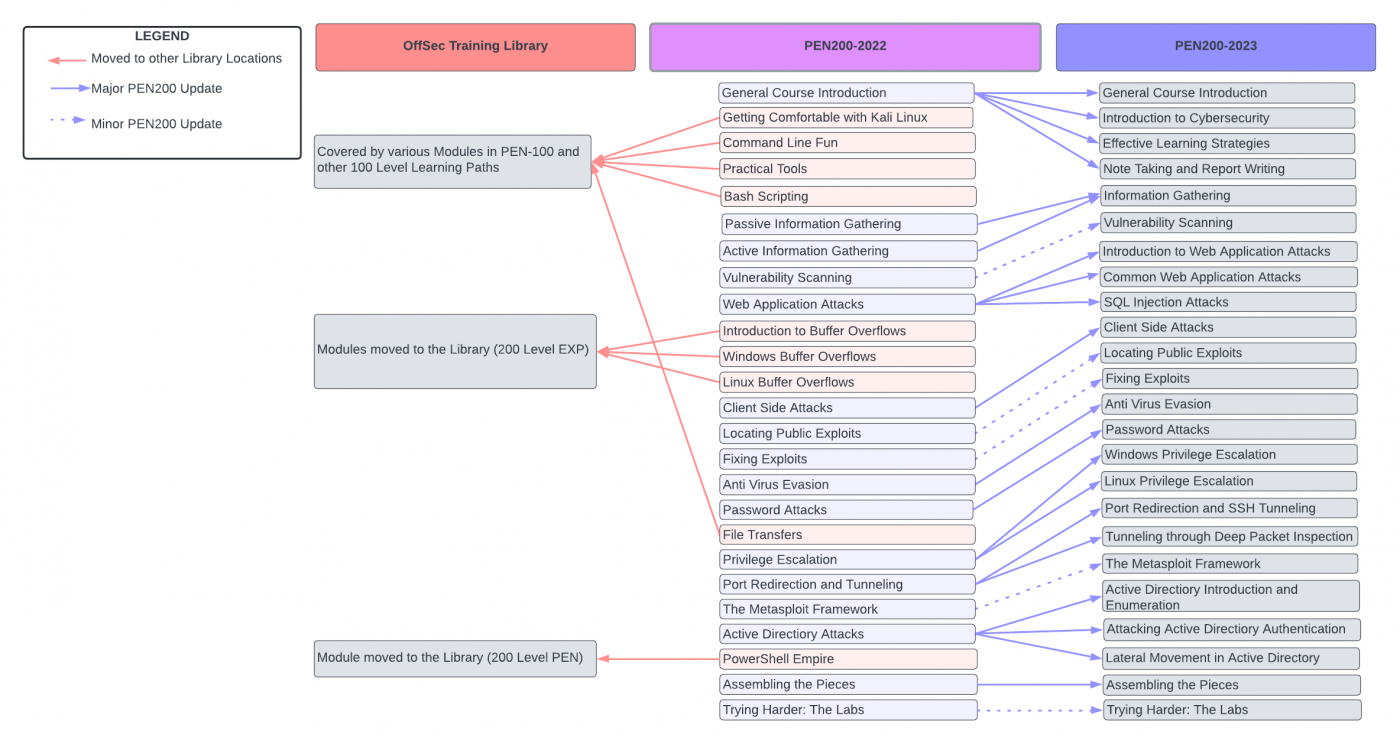
Major Changes
Apr 18, 2023
Official Announcement
You can read the announcement here. The purpose of this change is to make the learning experience and labs more modular. I'll summarize the most important points below:
Course Changes
I'm not going to cover every thing that was added or removed from the course (you can read the announcement), but I will mention the most notable changes:
Removed
- Buffer Overflows — simple overflows not realistic
- Command Line (covered in PEN-100)
- Bash Scripting (covered in PEN-100)
- File Transfers (covered in PEN-100)
Added/Enhanced
- Web App
- Privliege Escalation
- Tunneling
- Active Directory
Lab Changes
- No more shared environment
- Follows PEN-300 and WEB-200 exclusive environment model
- Labs are more challenge-based, progressively more difficult
Exam Changes
- No buffer overflow machines
- Any existing content should be expected in the exam (see diagram above)
- Any new content will be added to the exam six months post-launch
Bonus Points
Please consult the announcement post and carefully read through each scenario.
Jan 11, 2022
This announcement revealed a major change to the exam structure — with the introduction of an Active Directory set in addition to three independent targets.
- Points Required to Pass: 70
- Points Possible: 100
- No partial points for Active Directory (AD)
- Must fully compromise the AD set
What Skills Should I Have for the OSCP?
- Most people want to learn how to hack in as little time as possible
- I mean it sincerely when I say this:
- There are no shortcuts, no secrets
- No one is gatekeeping
- Accept that it's going to take time and work
- Learn the key skills now before you form bad habits
- You will thank yourself later when:
- You know how the attacks work at multiple layers
- You know how to detect attacks at multiple layers
Required Skill Areas
- Operating Systems
- Networking
- Web
- Programming
How They Apply to the OSCP
Some sections of the syllabus will fit into multiple columns, while others only fit into one column.
Free Training Resources
I am maintaining a list of free training resources on these topics at this page, and will continue to add to it as I come across more quality links.

Should I Get Other Certs First?
People have asked me about getting certifications such as the A+, Network+, and Security+ in preparation for the OSCP. And the true answer to that question is, "It depends."
Certifications can be expensive and time-consuming and there are often costs to keep them current.
Weighing the Pros and Cons
I've been in this position before. The idea of certifications is appealing, because they give you structure on what to study from start to finish.
However, certifications can be expensive and time-consuming, so I would narrow it down to this if you're trying to decide on whether to pay for a certification or not:
Search for the certification on some job sites like LinkedIn or Indeed.
- Is there high demand for the certification?
- Are the jobs in the results something you'd consider applying to?
- If yes:
- Then, it may be worth obtaining the certification
- If no:
- Then, you could study the certification materials and skip the exam
- If yes:
Curiosity: The Most Important Attribute
This is the single biggest requirement to becoming a successful hacker. You need to have the mentality of:
What if ________ ?What would happen if I ________ ?I wonder what caused ________ to happen.I don't know what ________ is. Let me research it.
To the curious, nothing is inconsequential. Hackers want to understand how things work, how things are controlled, and how those control systems can be manipulated in unintended ways.
Learn to Break the Rules (Ethically)
Imagine you are looking at an application. You see an input box. The input box says that you may only enter alphanumeric characters. Your curiosity should kick in here. What would happen if you input a special character or an emoji? What would happen if you input 1,000 "A" characters?
Learn to Love Research
Your first instinct – when you encounter something you don't know – should be to do some research on Google, Reddit, or other areas of the Internet. There's a good chance someone on the Internet has already asked about it or written about it.
Google Dorks
Google's search has operators that can be used to return very specific results when performing a search.
Some Example Search Operators
"keyword"all results must contain this word"some words"return all results with this exact phrase-keywordresults must not contain this word-"some words"results must not contain this phrasesite:somesite.comreturn results only from a specific sitesite:*.somesite.comreturn results from any subdomain of a sitefiletype:pdfreturn results containing PDF filesbefore:YYYY-MM-DDreturn results before a specific dateafter:YYYY-MM-DDreturn results after a specific dateafter:YYYY-MM-DD before:YYYY-MM-DDreturns results in a date rangecache:somesite.comcheck for cached version of a siteinurl:keywordresults must contain this word in their URLintitle:keywordresults must contain this word in their titlesite:somesite.com file:xlsx inurl:expenseyou can compound operators

Google Hacking Database
This is a list of Google Dorks used by the community to find vulnerabilities or misconfigurations.

Learning How to Hack
Put briefly, two things will make you a better hacker:
- Experience
- Time
This is true for any profession or hobby, really. The more experience you gain related to a particular subject matter, the better at it you will you become.
If you're just starting out, be patient and accept that for you to get better at hacking and security research is just a matter of gaining experience over time.
How to Learn Real Hacking
- There is no one path to becoming a hacker or security professional
- The highly respected LiveOverflow talks about his journey
HTML > VBS > Webdev > PHP > CSS > JS > MySQL > SQLi > Android Dev > Google Wave > Computer Science > Linux > HackerSpace > Arduino > CTFs
How the Best Hackers Learn Their Craft
- A Carnegie Mellon professor discusses how to grow your hacking skills
- DELIBERATE practice, autodidacticism (self-initiated learning), creativity
- Don’t shut down when you don’t understand (Google keywords in the problem)
- CTFs are critical to skill growth (HackTheBox, TryHackMe, etc)
Pentesting Methodology
- It is important to follow proven methodologies when conducting a penetration test, even when doing CTFs
- The Penetration Testing Execution Standard (PTES) and Penetration Testing Framework (PTF) detail the core steps of a penetration test
Applying it to CTFs
1. Client Visit and Scoping
- For a CTF, think platform rules of engagement
- Have an understanding of what you may and may not do
- Be very clear on what your target is
- Never engage out of scope without permission
2. Intelligence Gathering
- Passive
- Finding information about a target in an indirect way
- No interaction with target systems
- Active
- Finding infomration about a target directly
- Query DNS servers
- Visiting target web sites, FTP servers, mail servers, etc
- Finding infomration about a target directly
3. Threat Modeling
- Asses the target type and determine some common weaknesses
- For example, most web applications could use a database, which could lead to SQLi
4. Vulnerability Analysis
- Directly related to the quality of your intel
- Based on your interactions with the target systems
- Check version numbers, inputs, etc
- What do your findings reveal?
5. Exploitation
- Use great care and rely on your intel
- Is there an exploit for the target service?
- Version-specific?
- Architecture-specific (32-bit/64-bit)?
- An incorrect exploit could crash the service
6. Post Exploitation
- Congrats, you got a shell!
- Get a lay of the land
- Privilege escalation, further penetration
- Repeat the enumeration process (steps 2 through 5)
7. Reporting
- For a CTF, this could be a blog write-up
- You'll want to clearly define how you exploited targets
- Describe the vulnerability
- Describe the exploit used and how it works
- Describe any changes you made to an exploit
- Describe how to prevent exploitation
Getting Hands-On Experience
Knowledge without practice is useless. Practice without knowledge is dangerous.
– Confucius
Key Point for the OSCP
OSCP-Like Boxes List
This is a huge list of targets that will give you a similar experience to something you'd see in the OSCP (not identical). You'll see targets in these categories:
- Vulnhub (homelab, self-hosted)
- Proving Grounds (hosted)
- HackTheBox (hosted)
Hosted Services
Pros
- Lab and environment are already set up for you
- Just bring your Kali VM and get to work
- Some services also offer a pre-made Kali attack box for convenience
Cons
- Most will require a fee to use extended features
- If you use the provided attack box, you're going to miss out on valuable experience setting up and maintaining your Kali VM
Some Providers
Home Lab
Guides I've Written
How to Start Your Home Lab

- One of the single greatest way to develop core IT skills
- Systems/Network administration and break-fix are easily some of the best ways to learn the attack surface of IT systems
Building a Security Lab in VirtualBox

- VirtualBox is a free and open-source type 2 hypervisor
- If you're new to virtualization, this is the best place to start
- This guide is great for beginners and you'll get plenty of hands on experience with systems and networking
Building a Security Lab in Proxmox

- Proxmox is a free and open-source type 1 hypervisor
- The Proxmox guide is going to require separate server hardware
- Proxmox has far more advanced capabilities than VirtualBox or VMware Workstation and would be a great logical next step once you've gotten comfortable with something like VirtualBox
Developing an Attack Methodology
First Things First
Building Momentum
Developing an attack methodology is usually the most difficult part for beginners, as it can be overwhelming when you're staring at your first nmap scan and trying to figure out what to pick at first.
The key is to get some momentum by starting with the low-hanging fruit. Just start analyzing ports. Look at the service banners in the nmap output and try to figure out what's running on a specific port. Some examples of "easier" services to get started with are:
- File Servers
- Protocols
- FTP
- SMB
- Why they're good starters
- Can sometimes allow anonymous authentication
- Are great places to enumerate more information for later
- Protocols
- HTTP
- Why it's a good starter
- Easy to assess, just open your web browser
- Use a tool like
gobusterto spider the web server - Other directories and files may offer additional avenues
- Why it's a good starter
My CTF Methodology
CTFs are there to teach you about computer vulnerabilities and train you to think like an attacker, like a person trying to bypass control systems.

Notes: Your Key to Success
Taking good notes is your key to success with hacking. Not only from a learning perspective where you're documenting what you're learning, but you also need to take thorough notes while you're assessing a target, so you can keep track of important details and screenshots.
If you ask online, you’re going to get bombarded with all kinds of opinions on the best app. Everyone has their favorite, so find what works best for you!
Note-Taking Products
Local Notes + Sync
- Obsidian + GitHub or other sync solution
- Trillium + Sync Server
- Joplin + Dropbox
- Microsoft Word + OneDrive
Web-Based Notes Platforms
- Notion
- GitBook
- Microsoft OneNote
- Google Docs
- SimpleNote
- BookStack (Self-Hosted)
- Wiki.js (Self-Hosted)
Note-Taking Methodology
Keep your educational notes succinct and searchable, so that the information you need is readily available at a moment’s notice. Your write-ups can be more verbose, since you may want to add more context.
Write-Ups
- Your write-ups for various challenges (Windows, Linux, Web, Binaries, etc.)
- Have a template that you can clone and fill out as you move through the challenge
- Consider having a scratch pad where you can copy/paste before the final draft
- Keep these notes in their own category
- Some concepts may transfer to educational notes
Learning
- Short, concise summaries
- Memorable trivia
- Commands
- Code snippets
- Diagrams – https://draw.io (free)
- Etc.
Roadmap to OSCP
This assumes you're a complete beginner, so you can start at whichever step in the roadmap suits your skill level:
Core Skills Checklist
This is not an exhaustive list of everything you need to know, but it should be a good basis of determining your proficiency.
Systems
- You'll need to know a variety of operating systems for the OSCP
- Windows
- Windows XP
- Windows7
- Windows 10
- Windows Server
- Linux (Debian and RedHat derivatives)
- BSD
- Possibly more
- Windows
- Be comfortable in the terminal
- Bash
- PowerShell (and CMD)
- Know how to list the users and groups on an operating system
- Know the file system hierarchy on various operating systems
- Know how to get the current operating system version and kernel
- Be familiar with the Windows Registry
- Know how to list installed hotfixes on Windows
- Know how to check and modify permissions and ACLs
- Know how to check, create, and modify scheduled tasks
- Know how to list running process and services
- Have a basic understanding of how Active Directory functions
- Know how to work with AD in the shell and GUI
- Know the difference between a local and network user
- Know the difference between a local and network group
- Know the difference between NTLM and Kerberos authentication
- Know how to check various AD policies and configurations
- Know how to query DNS records
- Know how to query LDAP
Networking
- You don't need to be a subnetting wizard
- Given an IP address and network mask: know how to figure out your IP address space
- Know how to query and configure network interfaces on the command line
- Know how to read a routing table on the host
- Know what ARP is and how to read an ARP table
- Know how to list listening ports on a host
- Know how to pivot to internal networks when your target has mutliple interfaces or routes
- Proxying
- Tunneling
- Know how to forward individual ports
- Be familiar with the OSI model
- Understand the fundamentals of TCP/IP networking
Web
- Know the most common HTTP request methods
- Know the most common HTTP response codes
- Know some basic HTTP headers and how they work
- Know the basic functionality of a web server
- Know how to make HTTP requests from the command line
- Know how to use Burp or some other web proxy
- Know how DNS works to resolve hostnames to IPs
- Know how DNS hostnames correlate to virtual hosts on a web server
- Know how to modify your
hostsfile on your attack box - Know how to modify your DNS settings on your attack box
- Be familiar with SQL and NoSQL databases
- Have basic proficiency in SQL
- Understand SQL injections
Programming
- You don't need to be a full-time engineer or a computer science wizard
- Have some basic proficiency in AT LEAST one of these object-oriented languages:
- PowerShell
- Python
- Have a basic understanding of primitive data types in programming
- Know how to use flow control logic (conditions)
- Know how to use loops
- Know how to read, create, and edit scripts and exploits
- Know how to compile public exploits
- 32-bit
- 64-bit
- Know how to read and understand error messages when your scripts fail
- Google the error messages when you can't figure it out
Hands-On Practice
Develop Your Attack Methodology
TryHackMe
HackTheBox Academy
Develop Your Attack Methodology
Taking the First Step
- Enumerate, enumerate, and enumerate some more
- Look at everything and leave no stone unturned
- Take good notes
- Question everything
- It is OK to look at write-ups and learn from your failures
HackTheBox Academy Resources
- Getting Started with Pentesting on HackTheBox
- Network Enumeration with Nmap
- Footprinting
- Vulnerability Assessment
- Information Gathering - Web Edition
- Attacking Common Applications
- Attacking Common Services
- Linux Privilege Escalation
- Windows Privilege Escalation
TryHackMe Resources
- How to Research
- Hacker Methodology
- Nmap
- Walking an Application
- Vulnversity
- Basic Pentesting
- Intro to Offensive Security
- Vulnerabilities 101
- Post-Exploitation
- Windows Post-Exploitation
My Notes
Target Variety
- Get lots of practice against a wide variety of operating systems
- Windows
- Server 2008, 2012, 2016, etc
- XP, 7, 10, 11
- Linux (Debian and Red Hat derivatives)
- BSD
- Windows
- I'd highly recommend TJ Null's OSCP-like boxes list for both hosted and home lab targets
Hosted Environments
- The OSCP-like boxes list focuses on:
- HackTheBox
- Offensive Security Proving Grounds
- Again, if the goal is variety, I'd try to do targets on both platforms
- Both of these platforms offer Linux and Windows targets
- See below for Active Directory recommendations
Home Lab
- The OSCP-like boxes list focuses on Vulnhub exclusively in this category
- Vulnhub is simply massive, with tons of targets
- Unfortunately, you won't find any Windows targets here
- But, it's still an excellent place to perfect your methodology
- See below for Active Directory recommendations
- My Home Lab Guides will show you how to host Vulnhub targets in a secure way
- The guides also cover how to set up a basic Active Directory lab
Active Directory
- Get comfortable with the Active Directory exploit chain
- Active Directory is just an extension of Windows fundamentals
- You'll need your Windows methodologies
- And, you'll need to understand the core function of Active Directory
Active Directory Fundamentals
HackTheBox Academy Resources
TryHackMe Resources
Attacking Active Directory
Basic Pivoting Practice
Fantastic Comprehensive Module
- TryHackMe - Compromising Active Directory
- Contains paid content, but highly worth it
- Probably overkill for the OSCP, but will really cement the AD exploit chain
- See my write-ups on these rooms:
Practice Active Directory Networks
- HackTheBox
- HackTheBox - Dante Pro Lab - Best for beginners
- HackTheBox - Zephyr Pro Lab - Heavy Active Directory focus
- TryHackMe
Cheat Sheets
Dealing with Impostor Syndrome
When it comes to computer security – and really any other profession – you are always going to encounter people that make you second-guess yourself. It’s important to stay focused on your journey and stay motivated.
- Remember, when you see someone very skilled:
- You're seeing a person at a snapshot in time
- You're not seeing how long it took them to get to this point
- Some people just learn faster than others (and that's OK)
- The only comparison to make is your current self versus your past self
- Do I sometimes feel inadequate when comparing myself with others? Yes!
- Have I made progress more quickly than I thought I would? Also, yes!
- There's a lot to learn and there will always be new things to learn
- Be kind to yourself and remember to give yourself time to relax too
More Pages to Check Out