This page is part of the larger series of converting an old laptop into a bare metal home lab server. Click the link to be taken back to the original post.

pfSense is a modern, easy-to-use, and modular router and firewall. It will act as the gateway and firewall to an internal network that will primarily house our vulnerable infrastructure and security related infrastructure.
System Setup
Download the pfSense ISO file from here: https://www.pfsense.org/download/. Be sure to choose the correct format: DVD Image (ISO).
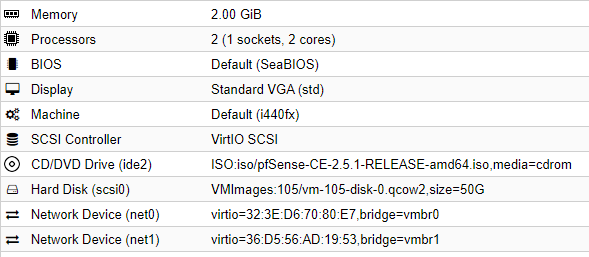
Upload the ISO file to Proxmox and create a VM with this hardware configuration:
Create the VM first then add the second adapter afterward. If you need a refresher on uploading ISOs and creating VMs, refer back to this post:

Give your pfSense VM a Static DHCP Reservation
We want the WAN IP address of the pfSense VM to stay the same every time it reboots.
- Log into your home router and give the pfSense WAN MAC Address a static IP address.
- If your home IP address space is
192.168.1.0/24, give pfSense an IP of192.168.1.2. If your address space is172.16.1.0/24, give pfSense and IP of172.16.1.2. Something llike this.
Double Check the Options
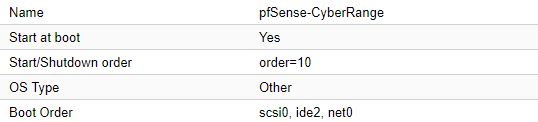
Before you boot up the pfSense VM, check the options in Proxmox and make sure they look like this.
Start the pfSense VM and double click it to open the NoVNC shell.
Install and pfSense Initial Setup
Power on the VM and let the auto-start load the installer.
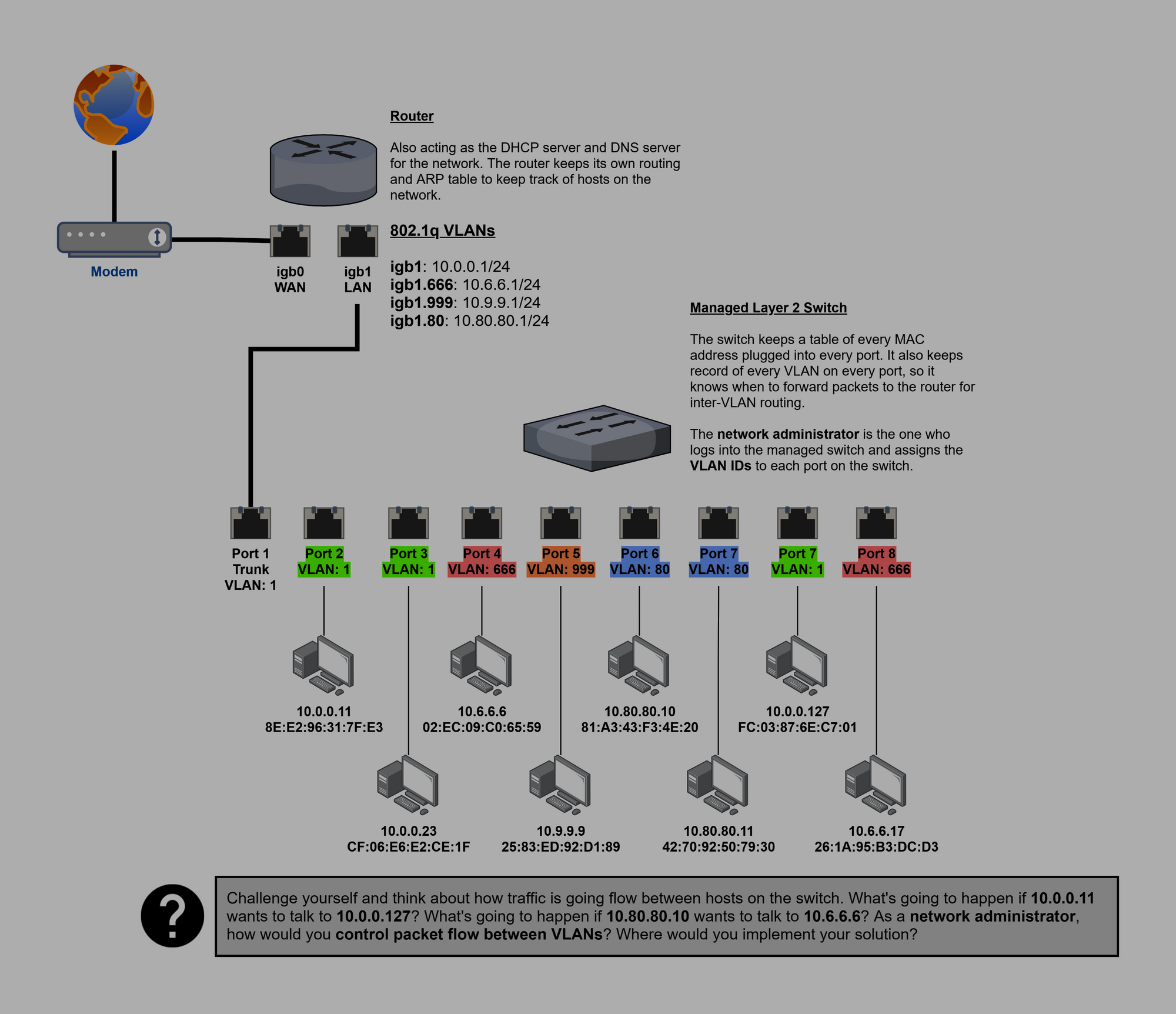
Configure VLANs
At the beginning of the guide, when we first installed Proxmox, we setup some Open vSwitch bridges and defined some VLANs on the vmbr1 bridge. In order for VLANs to function, both the switch and the router need to be aware of the VLANs.
- Should VLANs be setup now [y|n]
- Enter Y
- Enter vtnet1 (
vtnet1is the LAN interface)- Enter tag 666
- Enter vtnet1 (again)
- Enter 999
- Press Enter to complete the VLAN setup
- Enter the WAN interface name
- Enter vtnet0
- Enter the LAN interface
- Enter vtnet1
- Enter the Optional 1 interface
- Enter vtnet1.666
- Enter the Optional 2 interface
- Enter vtnet1.999
- Do you want to proceed?
- Enter Y
- Wait for additional setup steps to complete
You can read more about VLANs here:
Configuring Interface IP Address Ranges
Now, we are going to configure each interface and sub-interface with IP address spaces for clients on each LAN. Choose 2) Set interface(s) IP address.
- Enter 2 (LAN)
- Configure IPv4 address LAN interface via DHCP? (y/n)
- Enter N
- Enter the new IPv4 address
- 10.0.0.1
- Enter 24
- Press Enter (for LAN)
- Configure IPv6 address LAN interface via DHCP6? (y/n)
- Enter N
- Enter the new LAN IPv6 address. Press Enter for none:
- Press Enter
- Do you want to enable the DHCP server on LAN? (y/n)
- Enter Y
- Start of range: 10.0.0.11
- End of range: 10.0.0.244
- Do you want to revert to HTTP?
- Enter N
- Press Enter to complete
- Configure IPv4 address LAN interface via DHCP? (y/n)
Choose 2) Set interface(s) IP address again.

- Enter 3 (OPT1)
- Configure IPv4 address OPT1 interface via DHCP? (y/n)
- Enter N
- Enter the new IPv4 address
- 10.6.6.1
- Enter 24
- Press Enter (for LAN)
- Configure IPv6 address OPT1 interface via DHCP6? (y/n)
- Enter N
- Enter the new LAN IPv6 address. Press Enter for none:
- Press Enter
- Do you want to enable the DHCP server on OPT1? (y/n)
- Enter Y
- Start of range: 10.6.6.11
- End of range: 10.6.6.244
- Do you want to revert to HTTP?
- Enter N
- Press Enter to complete
- Configure IPv4 address OPT1 interface via DHCP? (y/n)
Choose 2) Set interface(s) IP address yet again.

- Enter 4 (OPT2)
- Configure IPv4 address OPT2 interface via DHCP? (y/n)
- Enter N
- Enter the new IPv4 address
- 10.9.9.1
- Enter 24
- Press Enter (for LAN)
- Configure IPv6 address OPT2 interface via DHCP6? (y/n)
- Enter N
- Enter the new LAN IPv6 address. Press Enter for none:
- Press Enter
- Do you want to enable the DHCP server on OPT2? (y/n)
- Enter Y
- Start of range: 10.9.9.11
- End of range: 10.9.9.244
- Do you want to revert to HTTP?
- Enter N
- Press Enter to complete
- Configure IPv4 address OPT2 interface via DHCP? (y/n)
Configuring the System Settings
We can now configure the rest of the setup through the GUI. However, if you go try to login to pfSense at the WAN IP address, it's going to fail.
This is because pfSense is blocking WAN access to the web console. This is a good thing if your pfSense router is sitting at the edge of your network. You wouldn't want any body to be able to reach the login page of your home router from the internet.
In reality, the IP address on the WAN port is a private IP address – which is not accessible from the Internet without some workarounds. So, in this case, it's perfectly safe to open the WAN port inside our home network.
Allowing Access to the Web Console from the WAN

Enter option 8 to open a system shell on pfSense. Then, type this command to disable the firewall. We need to do this at first to allow access.
pfctl -dLogging in and Setting Up
Open up your web browser and go to https://pfsense-ip-address. You may get a security warning about an untrusted certificate. Disregard and continue.
The default login for the web console is:
- Username:
admin - Password:
pfsense
Hostname and Domain
Click Next > Next. Set the hostname and domain.
- Hostname:
pfSense-sec - Domain:
cyber.range
DNS Settings
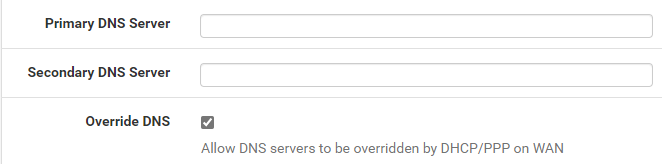
You can specify DNS servers here. The Override DNS box tells pfSense to use DNS settings from your home router. If you want to use the DNS settings from your home router, check this box and leave the DNS server boxes empty.
NTP Server
Click Next. Select an NTP server. Click Next.
Configure the WAN Interface
Select the type to DHCP
- DHCP Hostname:
pfSense-sec
Uncheck the box: Block RFC1918 Private Networks, as we want to allow private IP addresses through to the WAN interface.
Configure the LAN Interface
Skip this part
Wrapping Up
Change the admin password. Click Next > Reload > Finish.
Permanent Access via WAN IP
Disable the Firewall Again
After the initial setup, the firewall re-enables itself. We need to disable it one more time, so we can create some firewall rules in the GUI.
Go back to your pfSense system shell and run this command:
pfctl -dIf the web GUI is stalling, you probably have an asymmetric routes issue (we will cover that later). For now, go to the pfSense system shell and run these commands to restart the WAN network interface:
ifconfig vtnet0 down
ifconfig vtnet0 upYou should now be able to log into pfSense again.
Add a WAN Rule
Go to Firewall > Rules > WAN
Click Add
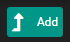
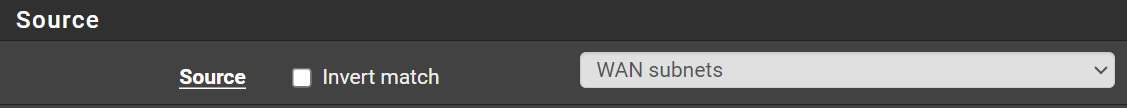
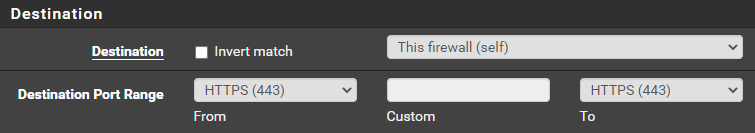
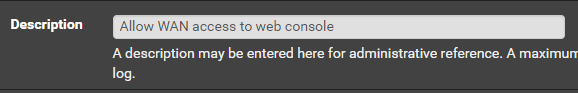
Click Save and Apply Changes
Finalize System Setup
Disable Hardware Checksum Offloading
Go to System > Advanced
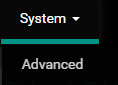
Go to the Networking tab. Check the box: Disable hardware checksum offloading. Reboot the VM when prompted.
Rename the Optional Interfaces
Go to Interface > Assignments
Then, click on each interface shown below and change their descriptions accordingly.
OPT1
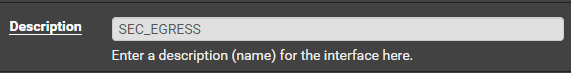
Click Save and Apply Changes
OPT2
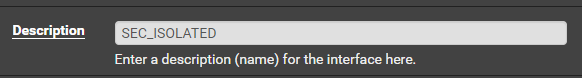
Click Save and Apply Changes
Set up Firewall Rules
Create Firewall Aliases
Go to Firewall > Aliases
Create an Alias for RFC1918
This alias will be used in some future firewall rules to reference all private IPv4 address spaces.
Click Add
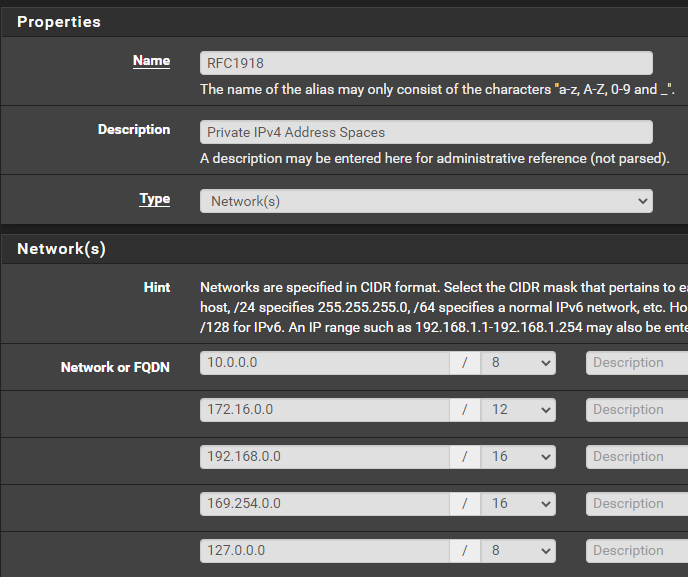
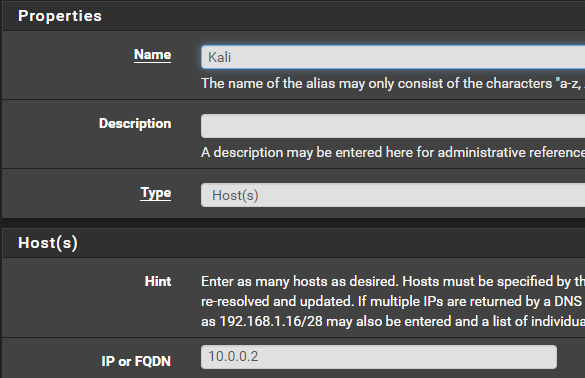
Create an Alias for Kali
Just create this for now even though we haven't create a Kali VM yet. We are going to assign a static DHCP reservation for Kali later.
Click Add
Click Save and Apply Changes
WAN Firewall Rules
Go to Firewall > Rules > WAN
Allow Home Network to Internal LAN
We want to allow our home network to reach the LAN where Kali is going to sit. That way you can ssh or open a remote desktop to your Kali VM.
Click Add
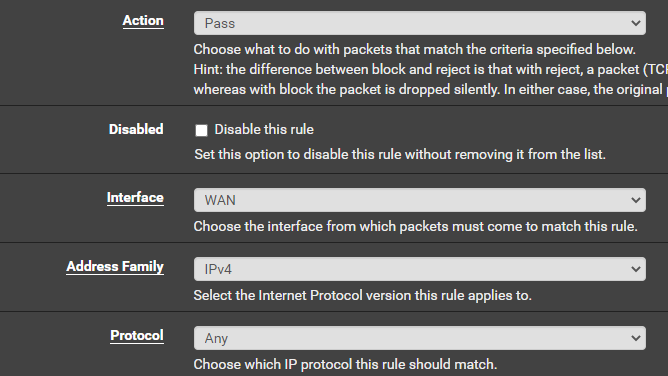
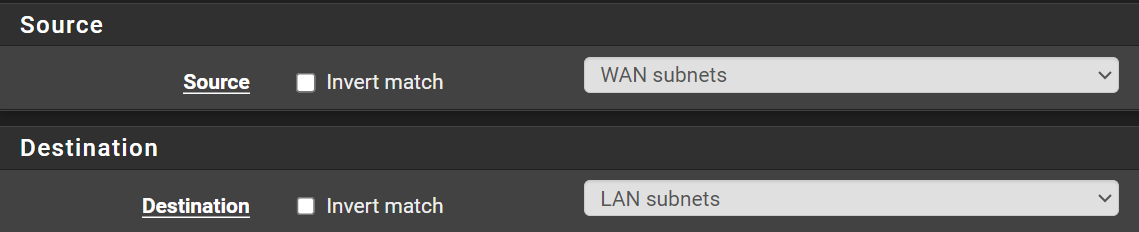
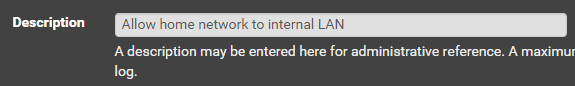
Click Save and Apply Changes
WAN Desired End State
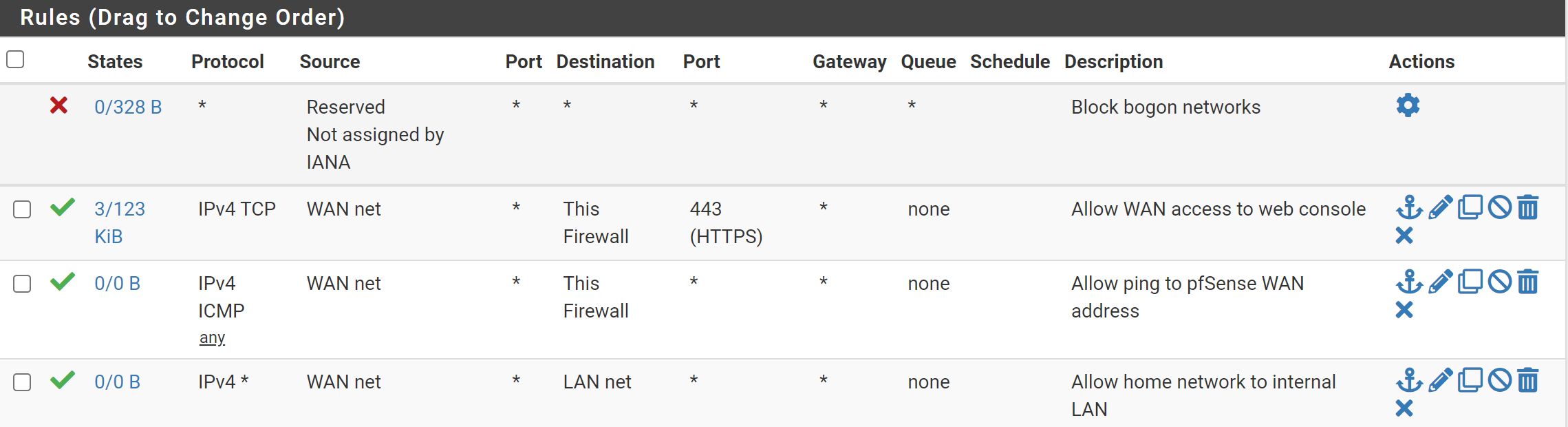
LAN Firewall Rules
No changes necessary. Leave it as-is.
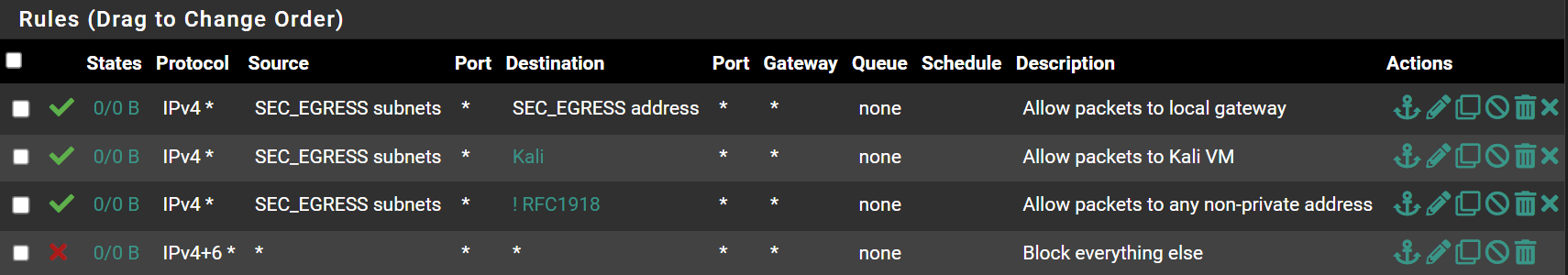
SEC_EGRESS Rules
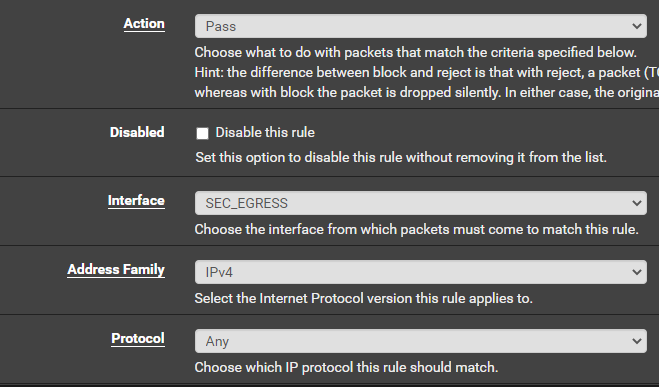
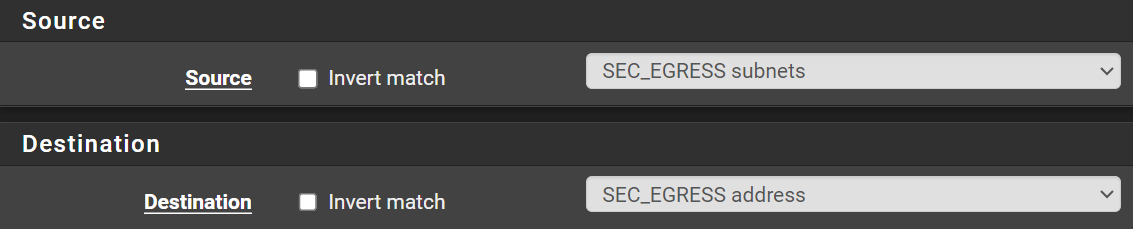
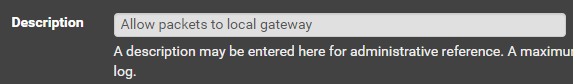
Allow Packets to Local Gateway
Packets need to be able to reach the default gateway in order to reach the Internet. We have to do it this way, because we will be blocking RFC1918 addresses a few rules later.
Click Add
Click Save
Allow Packets to Kali VM
Click Add

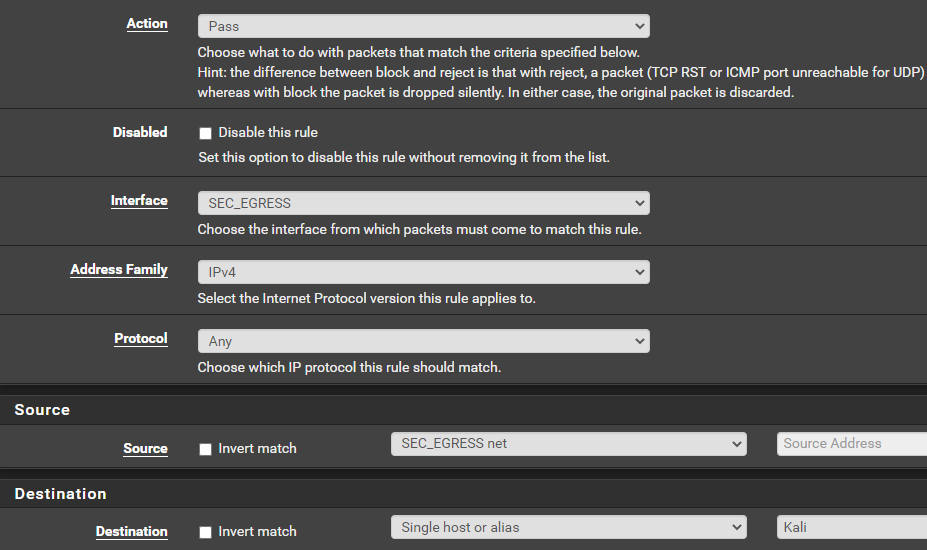
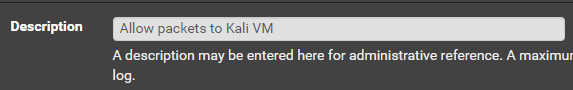
Click Save
Allow Packets to Internet (Non-Private Addresses)
Click Add

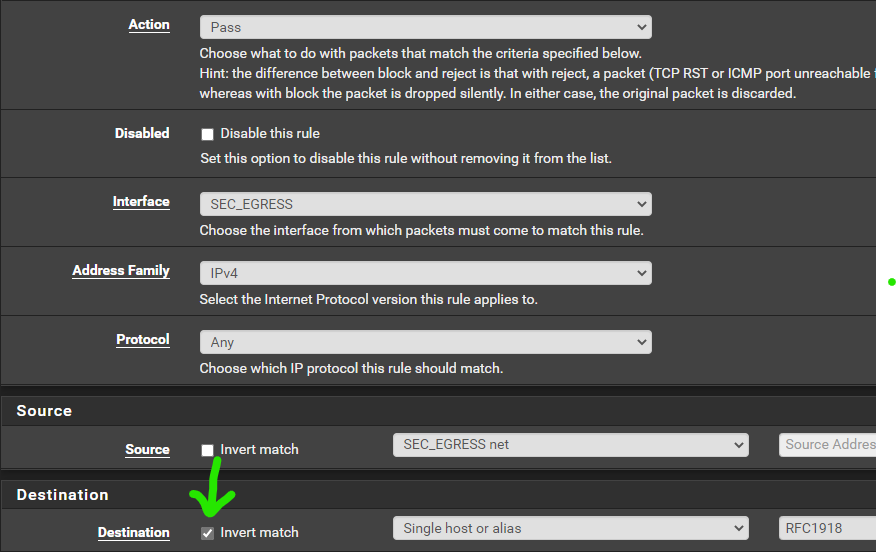
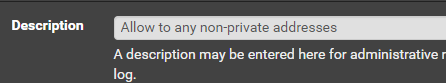
Click Save.
Block Everything Else
Click Add

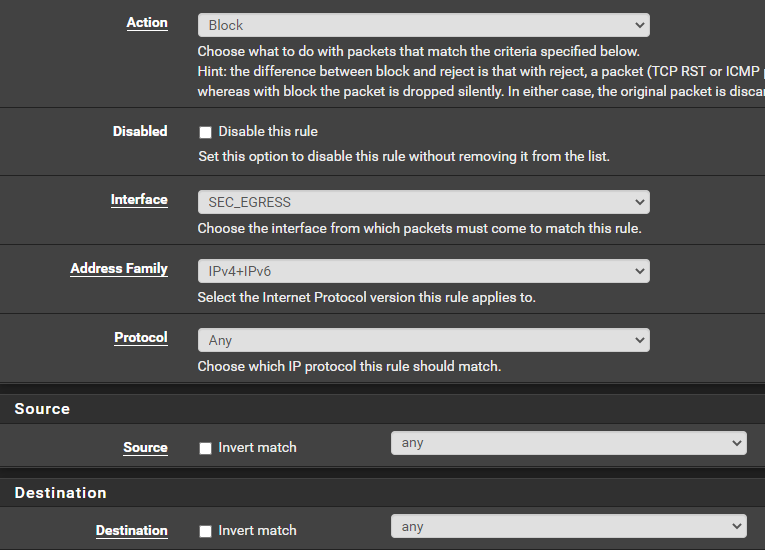
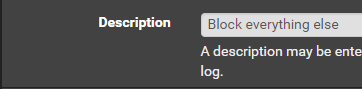
Click Save.
SEC_EGRESS Desired End State
SEC_ISOLATED Rules
Allow SEC_ISOLATED LAN to Kali VM
Click Add

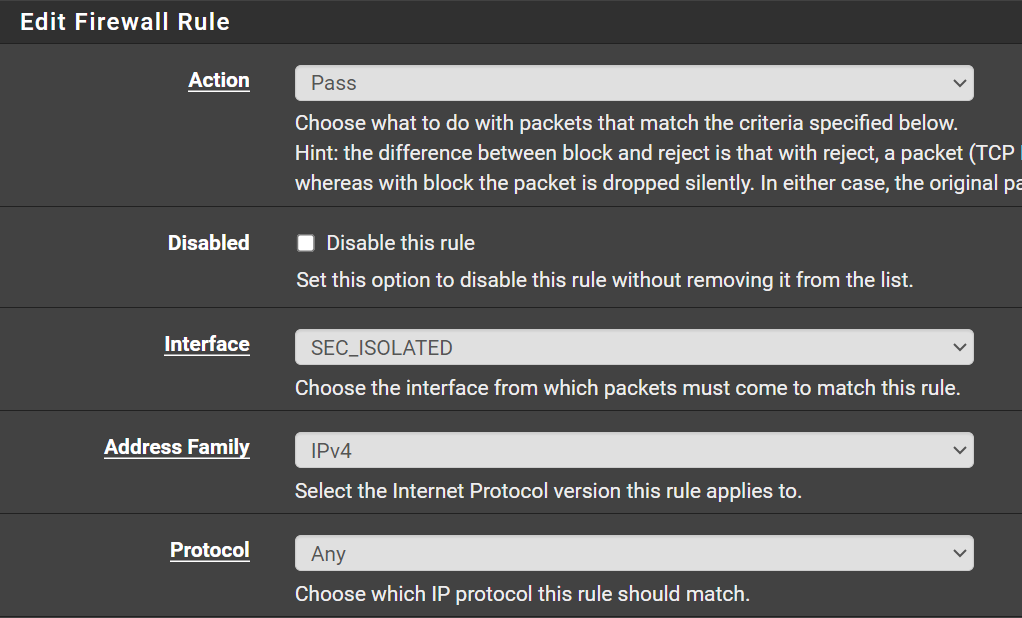
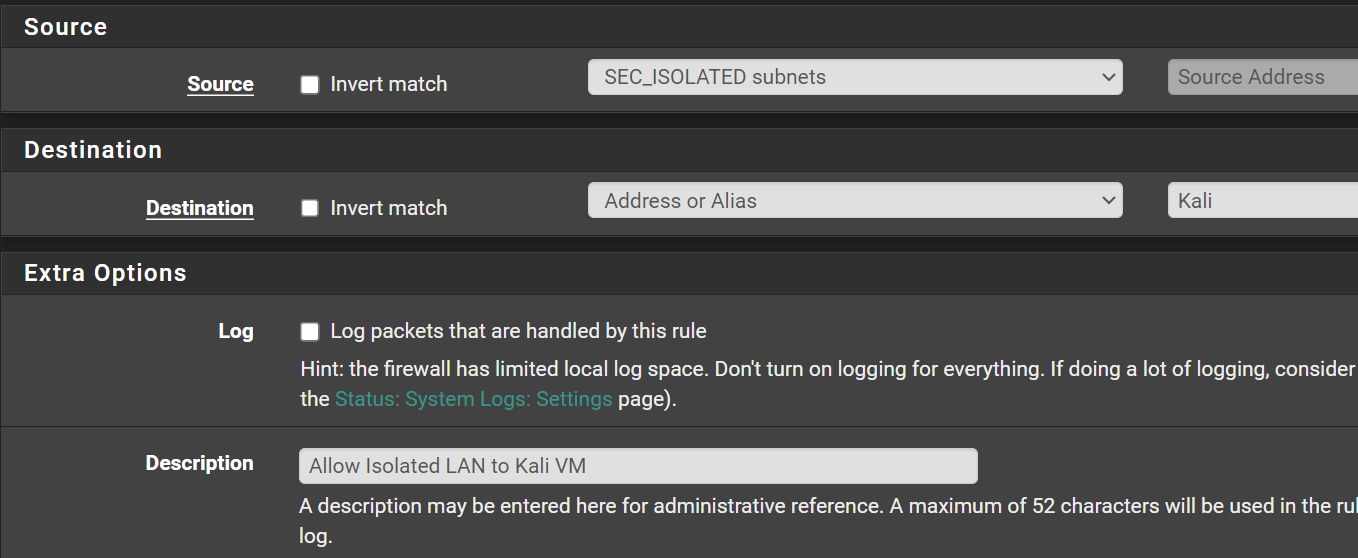
Click Save.
Block Everything Else
Click Add

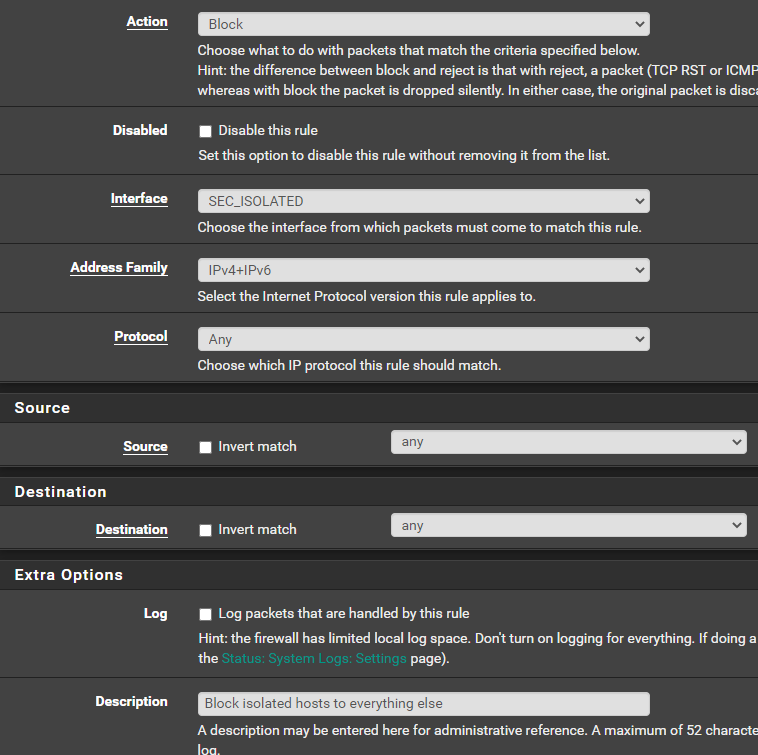
Click Save.
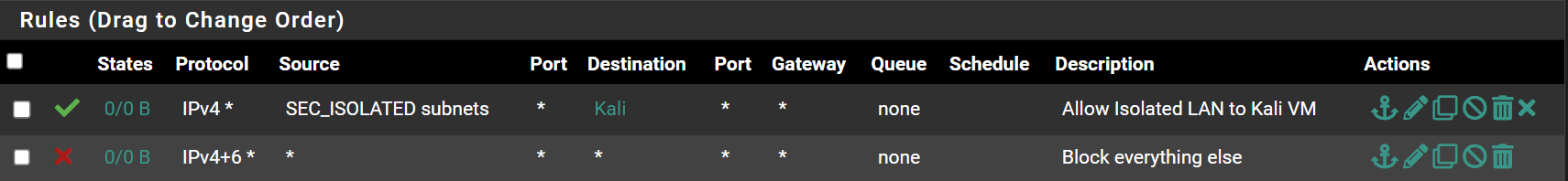
SEC_ISOLATED Desired End State
Configure the DNS Resolver Service
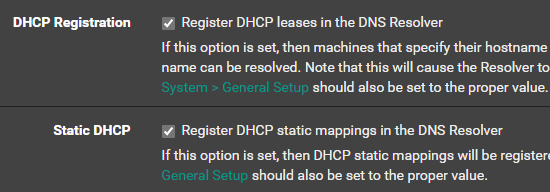
Go to Services > DNS Resolver
Check both of these boxes
Netgate is pushing people to the Kea DHCP daemon, as they're deprecating the ISC DHCP daemon. If you opt to move to the Kea DHCP daemon, these options will not be available.
You will need to switch back to ISC DHCP, make your desired selections, then switch back to Kea DHCP.
https://www.reddit.com/r/PFSENSE/comments/17z1u6f/dhcp_registration_on_dns_resolver/
Go to Advanced Settings
Verify your settings match:
Adding Additional VLANs to the Cyber Range
As you grow your lab, you may find yourself wanting to add additional VLANs to your cyber range network. Fortunately, with pfSense and Open vSwitch, the process couldn’t be easier.
Go to your Proxmox node > Network
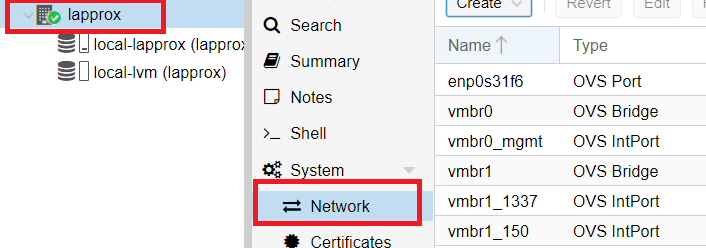
Add a VLAN to VMBR1 in Proxmox
Select vmbr1 and click Create > OVS IntPort. Fill out the fields like this:
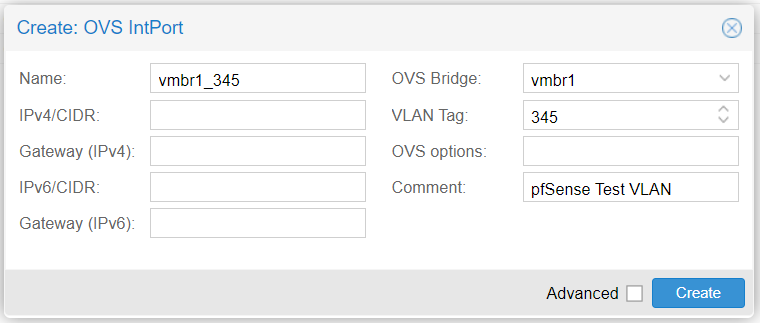
We are indicating that if we attach a container or VM to the switch vmbr1 – and we tag it with the VLAN ID of 345 – pfSense should route it through its intended VLAN.
Click Apply Configuration
Add the VLAN to pfSense
Log into pfSense and go to Interfaces > Assignments.
Click on VLANs
Click Add. Fill out the fields like this:
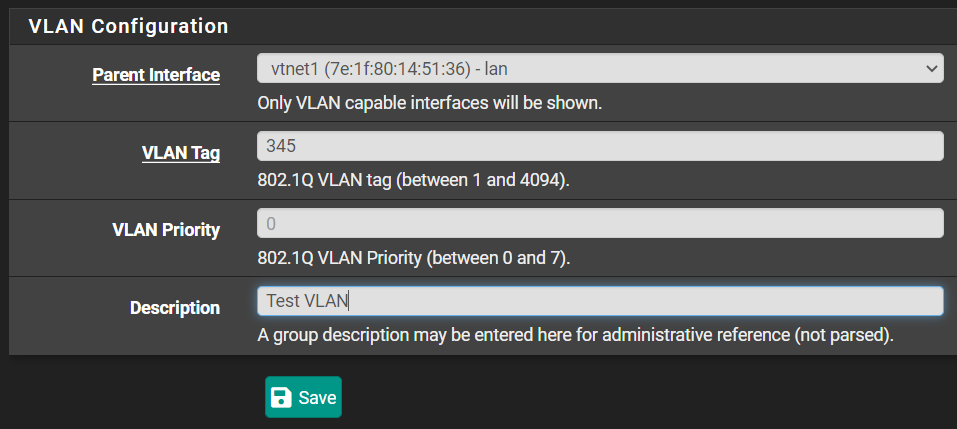
vtnet1 is the LAN interface. We are saying that 345 is a sub-interface of this interface. vtnet1 is the parent. Click Save.
Go to Interface Assignments
Click Add next to the newly added sub-interface.
Click Save. You should now see an OPT# interface. Click on the OPT# interface name.
Configure the Interface
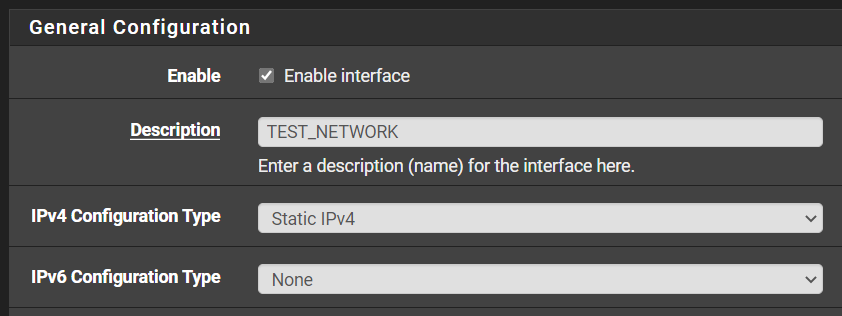
You can use whatever private IP address range you want. This is just an example. You need to specify the IPv4 address of the gateway – not the network. That’s why I entered 192.168.10.1/24 and not 192.168.10.0/24.
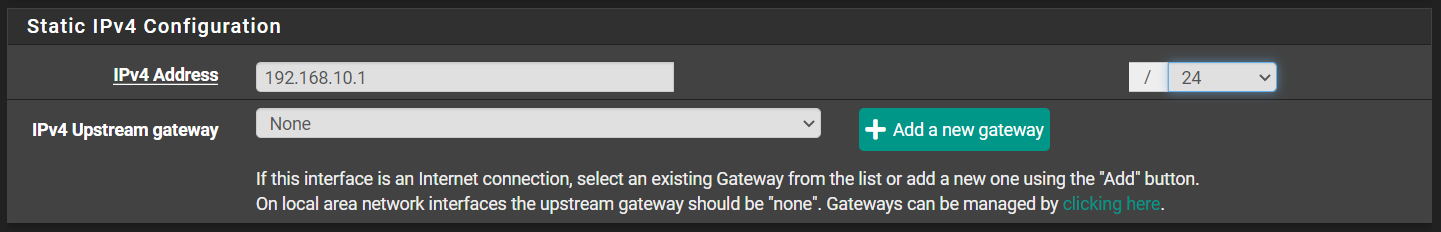
Scroll to the bottom. Check the box Block bogon networks. Click Save and Apply Changes.
Configure the DHCP Server
Go to Services > DHCP Server > TEST_NETWORK
Enable the DHCP server on this interface. Set the range to whatever you wish. I will be entering: 192.168.10.11 -- 192.168.10.244.
Click Save and Apply Changes.
Add Some Firewall Rules
In pfSense, go to Firewall > Rules > TEST_NETWORK
There are not going to be any rules by default (except if you’re blocking bogon nets).
It's up to you how you want to configure your firewall rules and routes.
- Do you want this VLAN to have Internet access?
- Which other LANs should it be allowed to talk to?
- Do you want to route to it from your WAN?
Optional: Configuring Static Routes
I was losing an incredible amount of packets between my personal computer and my Kali VM behind the virtual pfSense as a result of asymmetric routing, due to my home pfSense router not being able to track the TCP state of asymmetric packets and dropping the connection.
If your home router is a stateful firewall — it probably is — you should strongly heed the advice linked in the article just below.

pfSense VM Side
You don’t need a static route on the pfSense side. A route back into your home network already exists in pfSense’s routing table via the WAN interface.
Home Router Side
This is specific to each device! Consult your router’s manual for advice on configuring static routes in your own device
Example:
- Destination:
10.0.0.0/24 - Gateway:
[pfSense WAN IP address] - Description:
Route to pfSense internal LAN
Next Step: Adding a Comprehensive Wazuh SIEM and Network Intrusion Detection System (NIDS) to the Lab






