Key Points
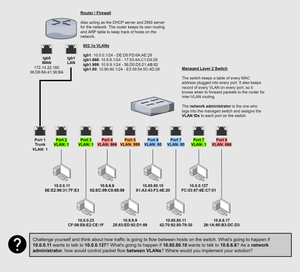
- VLANs are a layer 2 concept. The segmentation is occurring on the switch. The switch needs the assistance of a router – a layer 3 device – to move traffic between VLANs.
Need a refresher on network layers? See my other post here:
- The switch has a database called a CAM table where it keeps track of the following details about every plugged in computer:
- MAC Address
- Port Number
- VLAN ID -- if it's a managed switch
- VLANs require a "managed" switch. That means the switch has an embedded server of some kind where a network administrator will log into and configure each port with the desired VLAN tag number. An "unmanaged" switch – a dumb switch – is much simpler and only serves the purpose of forwarding traffic to the correct MAC address.
- The design in the diagram above is known as "router-on-a-stick" (ROAS), because of the single trunk from the switch to the router. It is a common design in smaller networks.
802.1q Protocol
802.1q – also referred to as Dot1Q – is an open standard developed by the Institute of Electrical and Electronics Engineers (IEEE). In order for VLANs to work, all devices on the network must understand and abide by the 802.1q protocol.
How Does 802.1q Work?
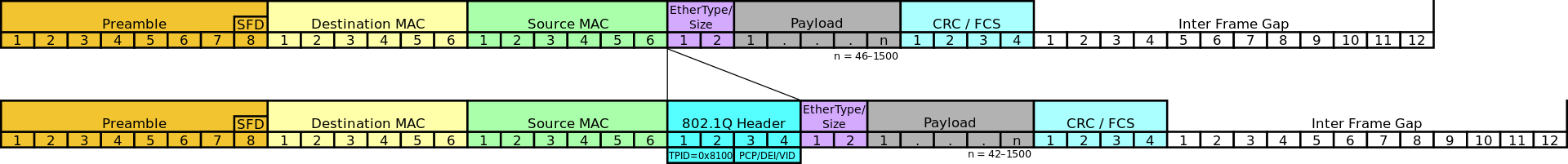
Header Injection
In the picture above, there is a before and after comparison of a layer 2 payload. The top image is the before and the bottom image is the after.
If you reference the network diagram above, you will remember that the network administrator logs into the managed switch and assigns each port a specific VLAN tag ID.
When a computer plugged into the port sends a frame on the wire, the switch will inject the 802.1q header into the layer 2 header and send it along.
VLAN Segmentation
VLAN segmentation – by itself – is not a security feature. When combined with a firewall, you can create a more robust network security design.
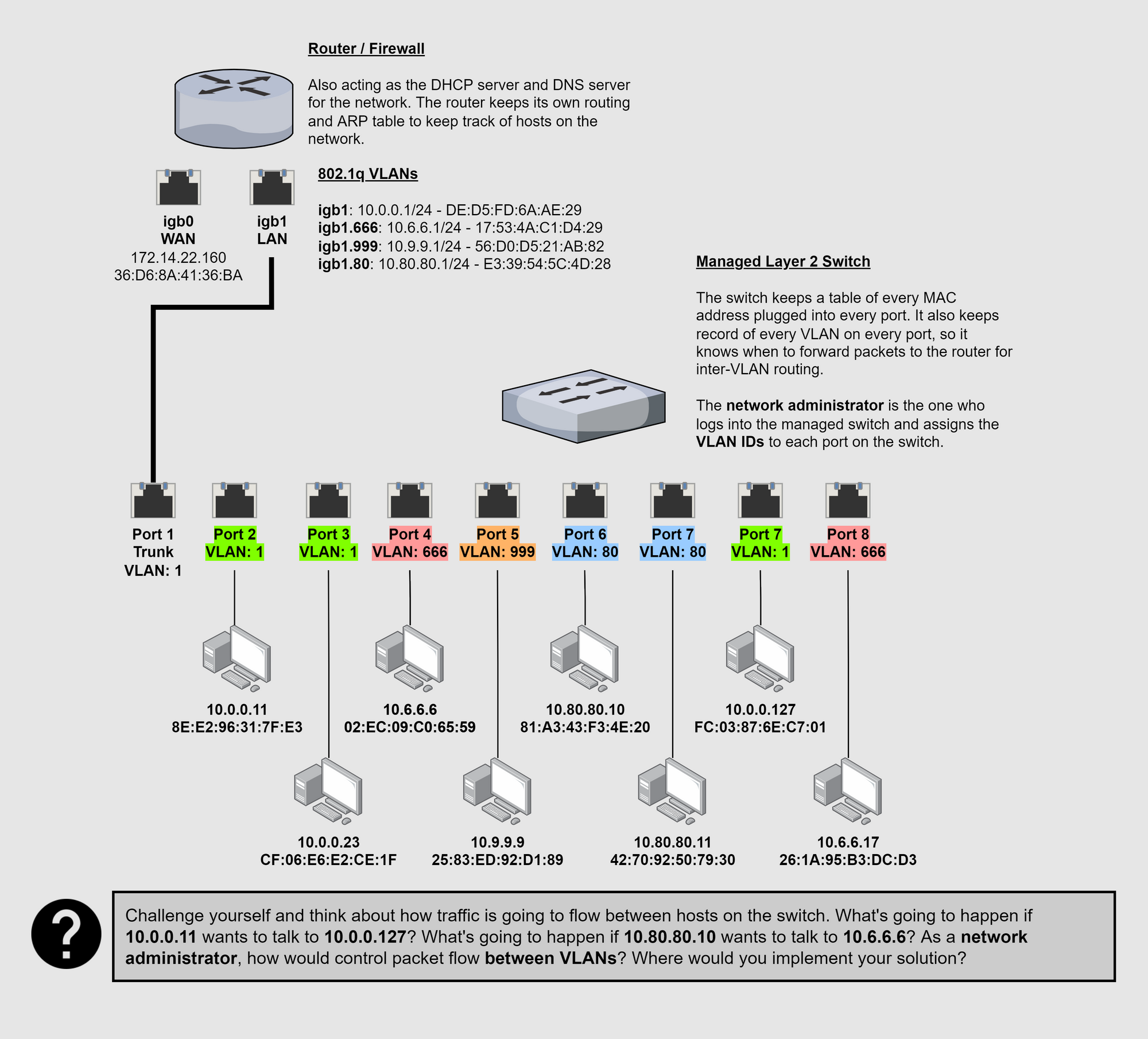
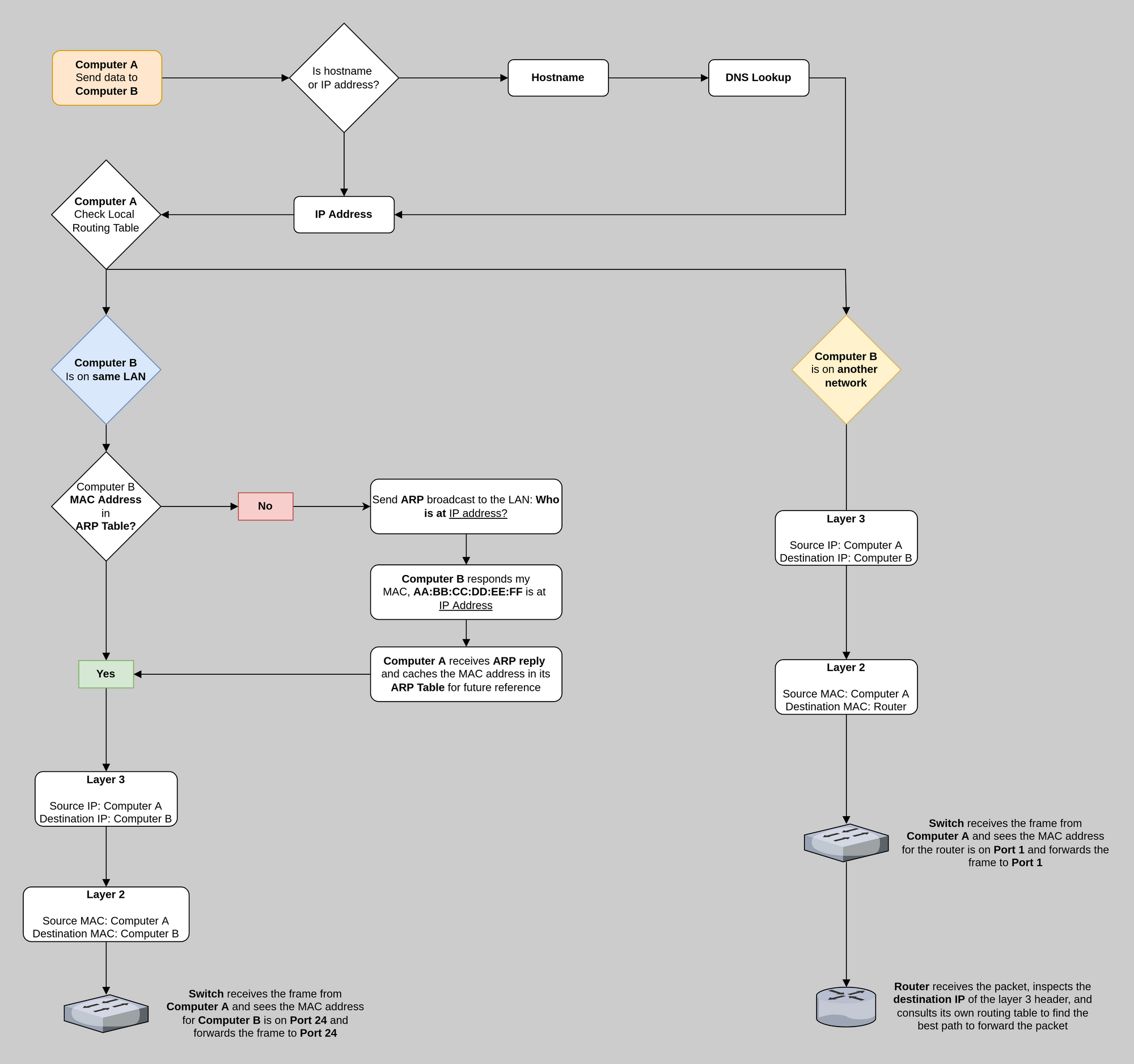
How Does Traffic Flow?
If two hosts are in the same VLAN, then they are in the same layer 2 broadcast domain. Effectively, they are on the same LAN. If a host wants to communicate with another host on the same VLAN, then the switch can move traffic between them.
If two hosts on different VLANs want to communicate, this requires a router. This is because the switch knows that both hosts are on different LANs and forwards the frame up the trunk to the router to complete its journey. The router receives the frame, inspects the 802.1q header in the layer 2 payload, checks its ARP table, and stamps the packet with the recipient's MAC Address.
This works because:
- The router also understands 802.1q
- The router and the switch share knowledge of the same VLAN IDs
- The router is the default gateway for all VLANs
- It has an ARP table of any device it communicates with on each LAN
- It can send an ARP broadcast on a LAN to discover a host
For more detail on packet movement through a network, check out my other post:
Practical Example
Creating VLANs with pfSense
First let's look at the concept of an interface and subinterfaces. An interface is the physical RJ-45 jack on the device. A subinterface is a software-defined interface on the device. The subinterface – in other words – is not a physical interface.

In the network diagram above, the router has two interfaces igb0 and igb1. igb0 is the WAN interface – meaning that all external traffic enters and exits here. igb1 is the LAN interface – meaning that this is the default gateway for all local traffic.
igb1.666, igb1.999, and igb.80 are subinterfaces. They were created by logging into the router and creating these interfaces as subinterfaces of the igb1 interface. In other words, igb1 is the parent interface of these subinterfaces.
Create the VLAN
- Log into pfSense. Then, go to
Interfaces > Assignments.
- Click on
VLANs
- Click
Add
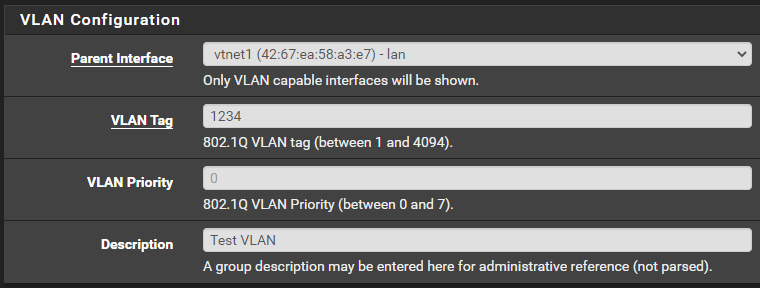
- Configure the VLAN with your details
- Click
Save
Configure the Interface
- Go back to
Interface Assignments
- There is a new interface available to be added
- Click
Add
- Click your interface name,
OPT4in my case - Configure it to your liking. Make sure the interface is enabled.
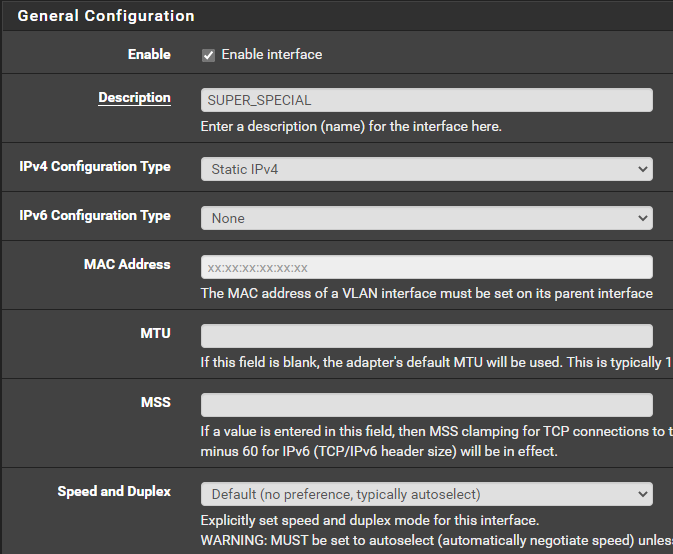
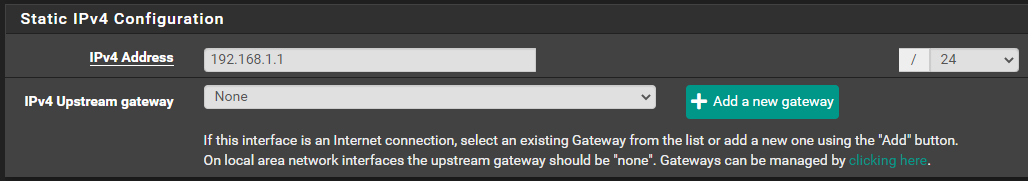
- I have created a
192.168.1.0/24network –/24 = 255.255.255.0. The IPv4 address in this case is the address the default gateway will use. There is no upsteam gateway because this is a LAN. - Click
Save
Configure the DHCP Server
- Go to
Services > DHCP Server
- Select your interface name.
SUPER_SPECIALin my case. - Configure your DHCP settings. Make sure to enable the DHCP server.
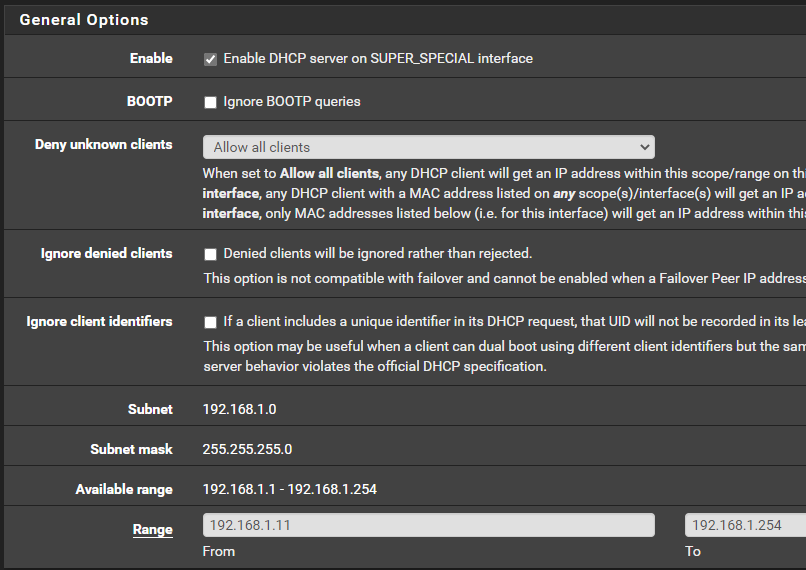
- Click
Saveat the bottom of the screen.
Configure Firewall Rules
- Go to
Firewall > Rules
- Choose your interface.
SUPER_SPECIALin my case - You will notice there are no firewall rules by default
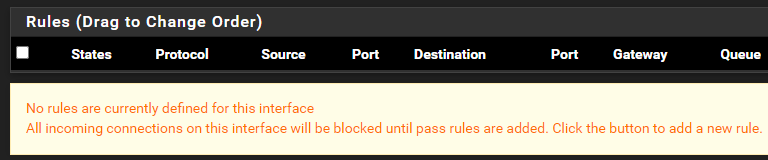
- pfSense is a default deny firewall, so unless you explicitly allow something, it will be blocked.
- Firewall rules are outside the scope of this article, so experiment with it and decide how you want traffic to flow between your networks.
Configure VLANs on the Switch
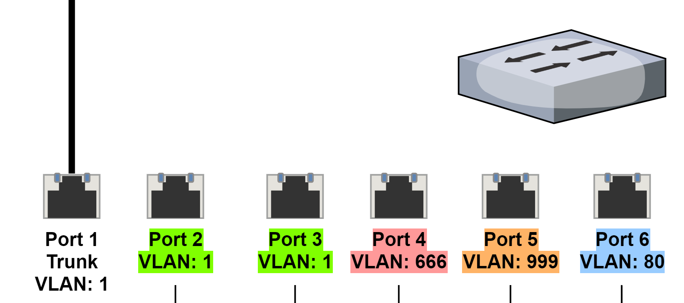
In the case of the managed switch, if you want a host to be on VLAN 1234, you just need to reconfigure the port with the new VLAN ID.
Then, when you turn on the device, the host will request a DHCP address. pfSense will note the 802.1q tag and assign an IP address from the SUPER_SPECIAL address pool.
Additionally, now that the device is on VLAN 1234, any firewall rules you have created will determine how packets may flow. Any other devices on VLAN 1234 will be able on the same LAN, so they can talk freely.
Multi-Switch Architecture
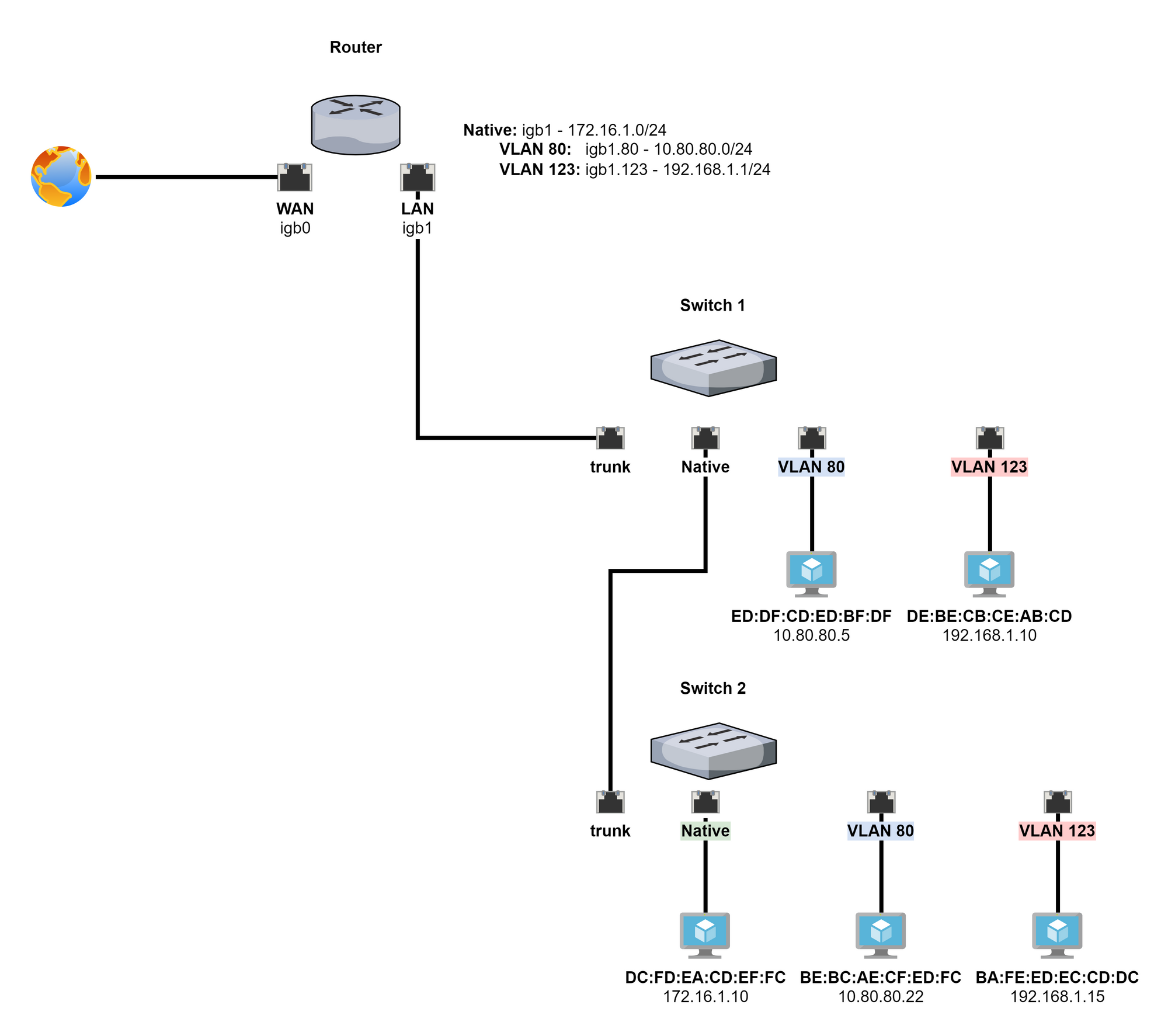
What if you had a multi-switch architecture like this – where switch 1 is the core switch and switch 2 is an access switch? How would hosts communicate?
10.80.80.22 to 10.80.80.5
- They are both on the same logical LAN.
10.80.80.22sends an ARP broadcast toFF:FF:FF:FF:FFto ask for the MAC address of10.80.80.5.- Switch 2 injects the 802.1q payload into the layer 2 headers of the packet.
- The ARP broadcast goes up the trunk to switch 1 and the broadcast is flooded to all ports – on VLAN 80 – on the switch.
10.80.80.5receives the ARP broadcast and replies toBE:BC:AE:CF:ED:FCwith its MAC address –ED:DF:CD:ED:BF:DF.10.80.80.22– which is atBE:BC:AE:CF:ED:FC– then crafts a packet and sets the destination IP address as10.80.80.5and the destination MAC address asED:DF:CD:ED:BF:DF.10.80.80.22sends the packet on the wire. Again, switch 2 injects the 802.1q payload. Switch 1 receives the packet and inspects the frame. It notes the destination MAC is in its table and that they are both in the same VLAN and forward the packet toED:DF:CD:ED:BF:DF.
172.16.1.10 to 192.168.1.10
- They are both on different subnets. This is going to require a router.
172.16.1.10knows the destination is on a different route. It prepares a packet with the destination address as192.168.1.10and the destination MAC address as the default gateway.- Switch 2 receives the packet and inspects the destination MAC address. It is not in its CAM table. It sends the packet up the trunk. Switch 1 receives the packet and checks its CAM table. The destination MAC is in the CAM table on the trunk port. It forwards the packet to the router.
- The router receives the packet and checks the destination address –
192.168.1.10. It checks its ARP table and routing table.192.168.1.10is atDE:BE:CB:CE:AB:CDand is on sub-interface igb1.123. The router injects the 802.1q payload into the layer 2 headers and sends the packet back down the trunk to switch 1. - Switch 1 receives the packet. It inspects the layer 2 headers and notes the destination MAC address of
DE:BE:CB:CE:AB:CD. That is in the CAM table on VLAN 123. It forwards the packet on to its destination.
Wrapping Up
I hope this has made it easier to understand the concept of VLANs and how the 802.1q protocol can be used to segment devices into smaller LANs. There is much more to explore on this topic, and networking in general.