This page is part of the larger series of converting an old laptop into a bare metal home lab server. Click the link to be taken back to the original post.

What is OWASP Juice Shop?
Juice Shop is a deliberately vulnerable web application where you can practice a wide variety of web attacks.
The application contains a vast number of hacking challenges of varying difficulty where the user is supposed to exploit the underlying vulnerabilities. The hacking progress is tracked on a score board. Finding this score board is actually one of the (easy) challenges!
The official project page can be found here:
Dockerized Installation
When I first wrote this guide, I don't believe Juice Shop was available as a Docker image. Previously, I had shown readers how to get up and running using the packaged distributions and Node.JS.
There is — however — a Docker image available now and this latest iteration of Juice Shop step of my Proxmox security lab guide makes several improvements over the previous version.
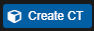
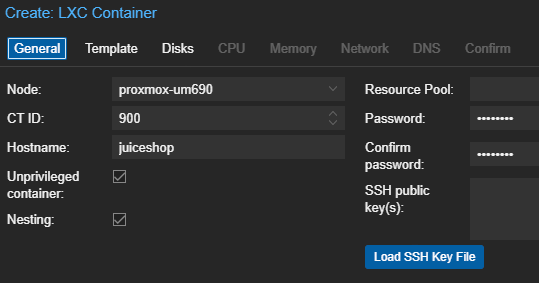
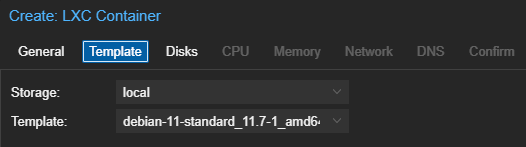
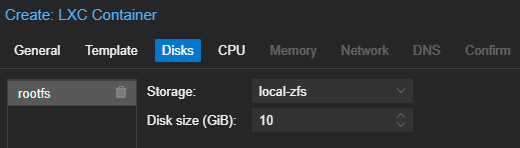
Create the Linux Container
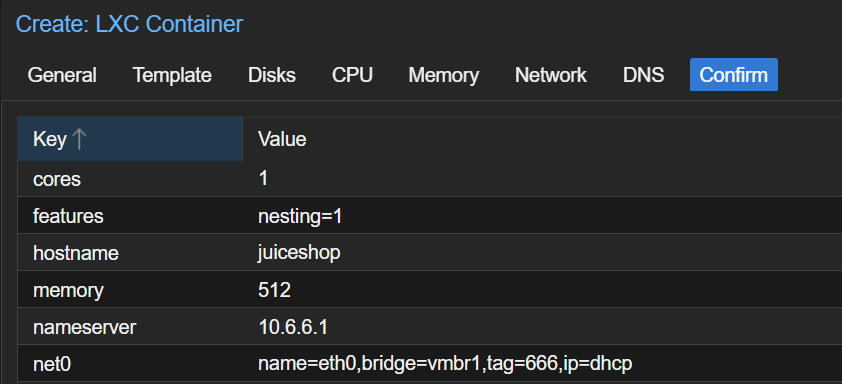
Prepare to Run Docker on LXC
I've already written a post some time ago showing readers how to get Docker Engine up and running on a Linux Container in Proxmox.
Come back here when you've finished getting the Docker environment all set up.

Pull and Run the OWASP Juice Shop Image
If you've successfully followed along with the post linked above, the following should be true:
- FUSE OverlayFS is installed on the PVE hypervisor
- FUSE OverlayFS is installed on the LXC
- Docker Engine is installed on the LXC and the Docker Hello World image was pulled and run, indicating Docker is installed and ready
Now, we're ready to pull the OWASP Juice Shop Docker Image and test. Open a shell on the Linux Container.
# Download the latest Juice Shop Docker iamge
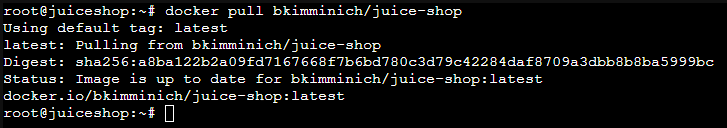
docker pull bkimminich/juice-shop
# The OWASP documentation runs Juice Shop on TCP/3000, I prefer TCP/80
# Also, pass in some options to ensure the container always runs at boot, and always restarts for any reason other than manual stoppage
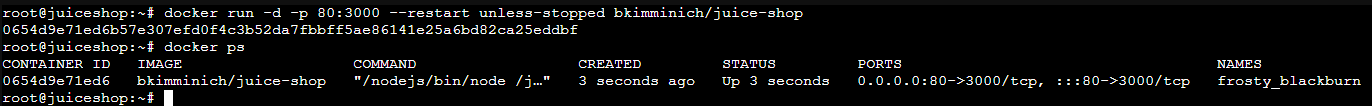
docker run -d -p 80:3000 --restart unless-stopped bkimminich/juice-shopManaging the Docker Process
docker psSee if the container is running
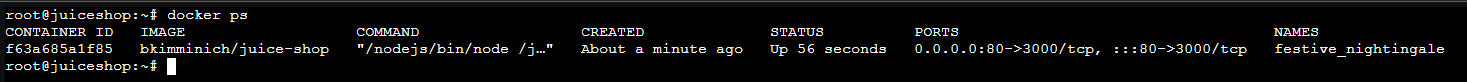
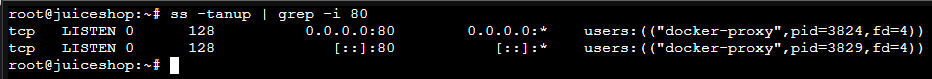
ss -tanup | grep -i 80Make sure it's bound to TCP/80
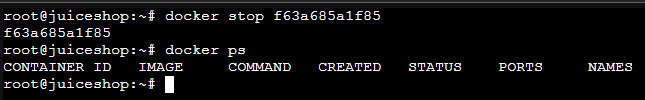
docker stop <container_id>Stop the container
docker run -d -p 80:3000 --restart unless-stopped bkimminich/juice-shopRe-run the container
docker pull bkimminich/juice-shopUpdate the Juice Shop container image to the latest
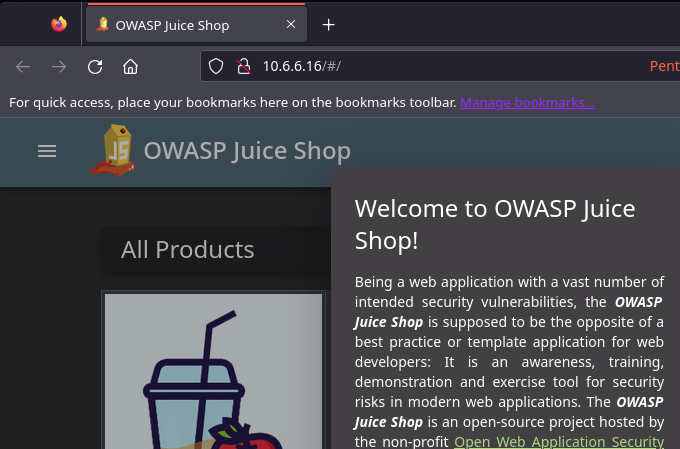
Check Kali Connectivity
Take a Snapshot
Once you've got the Linux Container and the Juice Shop Docker image configured, take a snapshot of the container in its last known good state. That way, you can roll back to this snapshot in case anything breaks during the penetration test.
Optional: Move to Isolated VLAN
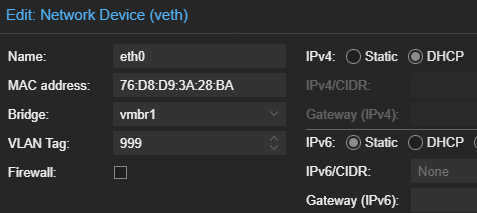
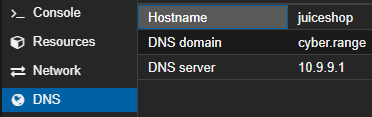
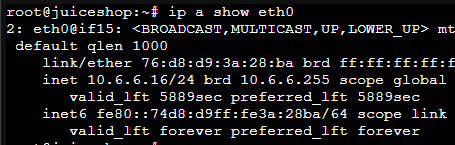
systemctl restart networking.serviceRestart the networking stack on the LXC
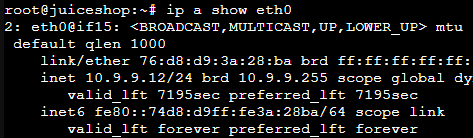
Confirm Kali Connectivity
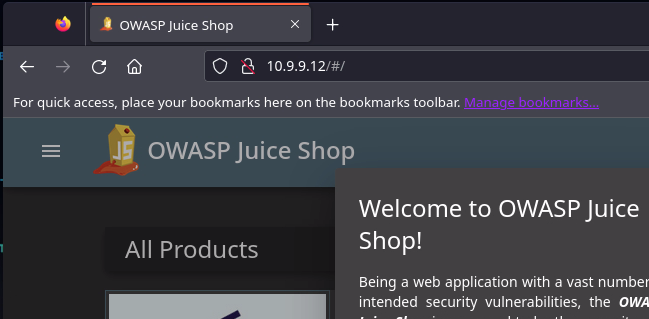
My firewall rules (and yours if you've followed this guide) should be such that you can access the Juice Shop container at its new address on the Isolated VLAN.
Need to Update your Container?
Just reverse the steps above and put your LXC back on VLAN 666 to reallow Internet access while you perform your update activities. When finished, repeat the procedure shown above to place it back on VLAN 999.
Next Step: Adding Vulnhub VMs to the Cyber Range





