Why I'm Writing this Post
In some previous posts, I've gone over a few topics that necessitate this post, including:
- Introduced the process of installing and configuring Wazuh
- Covering in detail the OwlH NIDS integration with Wazuh
- Covering the logall_json log archiving option in Wazuh
For anyone who may have followed any of my previous write-ups, I want to have a brief overview that will ensure your upgrades go as smoothly as possible.
Official Upgrade Documentation
My previous write-ups covering installation and integration are written using the Wazuh central components; that is — Wazuh Indexer, Wazuh Manager, and Wazuh Dashboard.

Upgrading with Customizations
I am going to refer you to the official documentation for all of the commands and procedures for upgrading the Wazuh server infrastructure. I will merely be adding context for certain parts in the sections below.
apt or yum commands according to the operating systems you're using on your Wazuh infrastructure.In general, the processes is detailed in four core steps:
- Preparing to upgrade
- Upgrading Wazuh Indexer
- Upgrading Wazuh Manager Server
- Upgrading Wazuh Dashboard
apt install <package-name> or yum install <package-name>, you will be prompted for Y/N input asking if you want to overwrite the existing configuration file. In most cases, choosing the default selection — N — is the best choice.Preparing to Upgrade
If you've followed my installation procedure, this step is run on the Wazuh Manager server, as this is where filebeat is installed.
systemctl stop filebeatIf you've followed my installation procedure, this step is run on the Wazuh Dashboard server.
systemctl stop wazuh-dashboardWazuh Indexer
These steps are to be completed on the server running Wazuh Indexer.
References to the username:password options in the curl commands are the credential you use to log into Wazuh Dashboard. I recommend only providing the username in the command and NOT putting the password on the command line.
Once you've upgraded your Wazuh Indexer(s), be sure to place the package back on hold to ensure that you prevent unplanned upgrades to your infrastructure.
sudo apt-mark hold wazuh-indexerWazuh Manager
These steps are to be completed on the server running Wazuh Manager.
Wazuh Manager Configuration
As noted in the upgrade guide, if /var/ossec/etc/ossec.conf has been modified, the original will not be overwritten. You will have to reconcile any differences between /var/ossec/etc/ossec.conf and /var/ossec/etc/ossec.conf.new.
In my environment — as documented in this guide — I am using the logall_json option and rotate_interval options in ossec.conf, therefore necessitating this step.
diff command to compare the two files and merge the new settings as necessary. I'd recommend a manual review of the differences and then proceed to copy and paste the additions from ossec.conf.new into ossec.conf.Once you've upgraded your Wazuh Manager, be sure to place the package back on hold to ensure that you prevent unplanned upgrades to your infrastructure.
sudo apt-mark hold wazuh-managerFilebeat Configuration
Installing a new version of Wazuh Manager requires the latest wazuh module for Filebeat. This will not overwrite /etc/filebeat/filebeat.conf, but it will overwrite the files in /usr/share/filebeat/modules/wazuh.
logall_json option and using the OwlH integration I want to ensure that I am not duplicating archived logs and alerts.I want to continue to receive custom Zeek alerts in the wazuh-archive-* indices based on custom Wazuh rules I've written. I also want raw Zeek logs to be written to their respective indices, owlh-{proto}-1.x-* — see here for more information.
Add this filebeat processor to the file /usr/share/filebeat/module/wazuh/archives/config/archives.yml:
processors:
- drop_event:
when:
and:
- has_fields: ['bro_engine']
- not:
regexp:
data.description: "^Zeek.*Log:.*"Effectively, we are telling the wazuh module in filebeat to drop any log with the line bro_engine that is not a custom rule alert. This is the job of the owlh module in filebeat to ship those raw logs to their respective indices.
Wazuh Dashboards
These steps are to be completed on the Wazuh Dashboard server.
Once you've upgraded your Wazuh Dashboards server, be sure to place the package back on hold to ensure that you prevent unplanned upgrades to your infrastructure.
sudo apt-mark hold wazuh-dashboardWhen logging back into the Wazuh Dashboard server — https://wazuh-dashboard-ip — the wazuh-alerts-* index pattern will be set as the default index pattern.
In my environment:
- I am using the
logall_jsonoption - Filebeat is reading from
archive.jsonin Wazuh - Filebeat is writing to
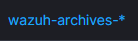
wazuh-archives-*
I'd like to set wazuh-archives-* as the default index pattern after upgrade.

Wazuh Agents
After installing the latest version of the Wazuh Agent package, ensure to take precautions to prevent unplanned upgrades.
Windows
Windows agents are installed via a MSI package and will not be automatically upgraded. Install the target MSI package and restart the service.
Linux
Linux agents — when installed using your distributions package manager (eg. apt, yum) — need to be held back from unintended upgrades. For example, running apt update && apt upgrade -y would upgrade the Wazuh Agent on a Debian-based system if the package was not held.
For Debian-based distributions, you can use the apt-mark command to hold pacakges from being upgraded without specific overrides.
sudo apt-mark hold wazuh-agentHold the 'wazuh-agent' package
When ready to upgrade the package:
- Run the command below
- If prompted to overwrite any configuration files, typically answer,
N
# Install the latest version of the wazuh-agent package
sudo apt install wazuh-agent
# Put the package back on hold
sudo apt-mark hold wazuh-agentInstall the latest version of Wazuh Agent




